- Home
- Microsoft Certifications
- 70-744 Securing Windows Server 2016 Dumps
Pass Microsoft MCSE 70-744 Exam in First Attempt Guaranteed!


70-744 Premium File
- Premium File 208 Questions & Answers. Last Update: Mar 09, 2026
Whats Included:
- Latest Questions
- 100% Accurate Answers
- Fast Exam Updates
Last Week Results!
All Microsoft MCSE 70-744 certification exam dumps, study guide, training courses are Prepared by industry experts. PrepAway's ETE files povide the 70-744 Securing Windows Server 2016 practice test questions and answers & exam dumps, study guide and training courses help you study and pass hassle-free!
Unlocking Security Skills for Microsoft 70-744: Windows Server 2016
In today’s technology-driven environments, organizations face increasingly sophisticated threats that target their networks and critical data. Security breaches can result in severe consequences, including operational downtime, financial losses, and damage to reputation. As networks grow in complexity, so does the potential for vulnerabilities. This has created a strong demand for IT professionals who are not only skilled in managing servers and networks but also capable of defending them against evolving threats.
Network security specialists are integral to modern IT operations because they help mitigate risks before they escalate into major incidents. Their responsibilities include monitoring network traffic for anomalies, implementing protective measures, and responding quickly when security events occur. By employing a combination of technical expertise and strategic planning, these professionals minimize the potential damage from breaches and maintain the continuity of business operations.
Advanced Knowledge in Windows Server Security
Securing Windows Server environments requires a deep understanding of both system architecture and security principles. IT professionals must be able to configure, maintain, and monitor servers while anticipating potential threats. Structured training for Windows Server security exposes candidates to practical scenarios where they simulate responding to breaches, learning to analyze vulnerabilities and implement corrective measures.
This type of training emphasizes protecting critical administrative accounts and managing credentials to prevent unauthorized access. It also focuses on best practices in identity management, ensuring that only authorized personnel have access to sensitive data and system controls. Mastery of these concepts is critical for maintaining a robust security posture in enterprise environments.
Understanding Threats and Malware
One of the core responsibilities of a network security professional is recognizing and mitigating threats from malware, spyware, and other malicious software. Even minor vulnerabilities can compromise an entire network, making it essential for professionals to proactively monitor, detect, and neutralize threats. Effective defense strategies require understanding how malware operates, how it spreads, and the methods to contain or eliminate it without impacting legitimate operations.
Windows Server environments offer various tools for monitoring and analyzing potential threats. IT professionals must learn to interpret system logs, deploy security features, and respond appropriately to alerts. This knowledge ensures that they can quickly contain issues, prevent escalation, and maintain the integrity of the network. Developing these skills requires consistent practice and an in-depth understanding of threat behavior and mitigation techniques.
Implementing Advanced Threat Detection
Modern server environments provide features that support proactive security measures. Candidates preparing for the 70-744 exam must understand how to use advanced threat analysis tools to detect anomalies, identify suspicious activity, and respond to potential attacks. Effective threat detection involves both automated monitoring and manual investigation, allowing security professionals to anticipate problems before they compromise systems.
These skills are complemented by learning how to configure security policies, monitoring alerts, and creating procedures for rapid response. IT professionals must be able to distinguish between false positives and genuine threats, applying critical thinking and problem-solving skills to ensure appropriate measures are taken. Advanced threat detection capabilities are essential for maintaining resilience in highly dynamic and complex network environments.
Securing Administrative Privileges
Managing privileged accounts is a critical component of server security. Administrative credentials, if compromised, can provide attackers with complete control over the network. Training emphasizes strategies for limiting access, implementing role-based permissions, and auditing account activity to ensure that administrative rights are used responsibly and securely.
IT professionals must understand how to enforce policies that reduce risk, such as the principle of least privilege, multi-factor authentication, and secure password management. Protecting administrative accounts is not only about controlling access but also about monitoring for suspicious activity and taking corrective actions when anomalies are detected. These measures significantly reduce the potential impact of a security breach.
Securing Virtualized Environments
Virtualization introduces unique challenges to network security, as multiple workloads share the same physical resources. Candidates must learn how to configure virtual machines, isolate critical workloads, and apply security measures that protect both virtual and physical components of the infrastructure. Techniques include controlling network segmentation, configuring firewalls within virtual networks, and monitoring virtual environments for unusual activity.
Understanding how virtualization affects security allows IT professionals to design resilient environments that can withstand attacks while maintaining operational efficiency. Properly secured virtualization ensures that even if one workload is compromised, other resources remain protected, preserving overall network integrity.
Hardening Windows Servers
Server hardening involves applying a combination of policies, configurations, and protective measures to reduce vulnerabilities. Candidates preparing for the exam must understand how to disable unnecessary services, apply security patches, enforce encryption standards, and configure logging and auditing. These measures prevent attackers from exploiting weak points while maintaining operational stability.
Hardening strategies extend to network protocols, access control settings, and administrative tools. IT professionals must be able to evaluate their environment, identify potential risks, and implement solutions that align with security best practices. The ability to harden servers effectively demonstrates expertise in reducing the attack surface and strengthening overall network resilience.
Monitoring and Incident Response
Ongoing monitoring is essential to maintain a secure network. Professionals must be adept at using built-in and third-party monitoring tools to track system performance, log events, and identify potential security incidents. Effective monitoring enables the early detection of anomalies, allowing rapid response to prevent escalation.
Incident response requires a structured approach, including identification, containment, eradication, and recovery. IT professionals must develop protocols that ensure continuity of operations while addressing security threats. This involves coordinating with other teams, documenting actions, and analyzing incidents to improve future response. These skills are critical for managing real-world security challenges and maintaining system integrity.
Practical Experience and Hands-On Labs
Hands-on experience is vital for mastering Windows Server security. Candidates should set up virtual labs to practice configuring servers, implementing security policies, managing administrative accounts, and responding to simulated attacks. These labs provide a safe environment to experiment, make mistakes, and learn from them without risking production systems.
Lab exercises also include scenario-based challenges, allowing candidates to troubleshoot complex security issues and apply best practices under realistic conditions. This approach reinforces theoretical knowledge and develops problem-solving abilities, ensuring candidates are prepared for the practical demands of professional environments.
Threat Mitigation and Recovery
Understanding how to mitigate threats involves both preventive and corrective strategies. Candidates must learn to apply security patches promptly, implement network segmentation, enforce policy compliance, and back up critical data. These measures reduce the risk of attacks and ensure that recovery is possible in the event of a compromise.
Disaster recovery planning and business continuity strategies are integral to maintaining network resilience. IT professionals must design systems that can restore operations quickly, preserving data integrity and minimizing downtime. Training emphasizes the importance of testing recovery procedures to ensure readiness in actual incidents.
Identity Management and Access Control
Effective identity management is crucial to securing Windows Server environments. Candidates must understand how to implement role-based access controls, manage user groups, and enforce authentication policies. These measures ensure that users have appropriate access while reducing the risk of unauthorized activity.
Access control also involves auditing account activity, monitoring for privilege escalation, and applying conditional access policies. IT professionals must be able to analyze security logs and take corrective action when deviations from standard practices occur. This proactive approach strengthens organizational security and minimizes exposure to potential threats.
Continuous Skill Development
Maintaining a secure server environment requires ongoing education and adaptation. Candidates should stay current with evolving threats, emerging security tools, and updated best practices. Regular practice, lab exercises, and scenario simulations help reinforce knowledge and ensure readiness for both exams and real-world challenges.
Developing expertise in advanced server security builds confidence, improves problem-solving capabilities, and prepares IT professionals for senior roles in network administration and security management. Mastery of these skills demonstrates readiness to handle complex, dynamic, and high-stakes environments.
Mastering the principles of securing Windows Server environments is essential for IT professionals aiming to excel in network security. Understanding threat detection, administrative control, virtualization security, server hardening, and incident response provides a strong foundation for both certification and professional practice. Practical experience combined with theoretical knowledge ensures candidates are prepared for real-world challenges and positions them for advancement in IT security roles.
Implementing Privileged Identity Management
A critical aspect of securing Windows Server environments is managing privileged accounts effectively. Privileged identity management ensures that users with elevated access are monitored and that their permissions are granted only when necessary. IT professionals must learn how to create policies that limit the duration and scope of administrative privileges, reducing the likelihood of misuse or exploitation. Techniques include just-in-time access, role-based permissions, and auditing actions performed by privileged accounts. Understanding these methods is essential for preventing unauthorized access and maintaining system integrity.
Proper management of privileged accounts also involves continuous monitoring. IT professionals need to analyze logs to detect unusual behavior and enforce policies that prevent privilege escalation attacks. By implementing a robust identity management strategy, organizations can reduce the risks associated with administrative access and ensure compliance with security standards.
Hardening Workloads and Server Configurations
Securing individual workloads and server configurations is an essential step in minimizing vulnerabilities. Candidates must learn to evaluate servers for unnecessary services and roles, disable features that are not required, and apply appropriate security templates. Workload-specific security ensures that applications and services are protected according to their unique requirements, providing a layered defense against potential threats.
Hardening practices extend to operating system settings, network protocols, and application configurations. IT professionals must be able to apply encryption, enable logging, and enforce access controls to strengthen defenses. Regular review and testing of server configurations help ensure that security measures remain effective against emerging threats.
Securing Network and Virtualization Infrastructure
Modern IT environments rely heavily on virtualization and complex network architectures. Candidates must understand how to protect virtual machines, isolate sensitive workloads, and configure virtual networks to prevent lateral movement by attackers. Network security also involves segmenting traffic, configuring firewalls, and monitoring communications for anomalies.
Securing virtualization infrastructure requires knowledge of hypervisor configurations, virtual switches, and resource pools. IT professionals must be able to implement security policies that apply consistently across both physical and virtual environments. These measures prevent breaches from spreading within the network and protect critical resources from unauthorized access.
Implementing Threat Detection Solutions
Effective threat detection is a cornerstone of network security. Candidates must learn to deploy tools and techniques that identify potential security incidents before they escalate. This includes configuring alerts, analyzing logs, and correlating events from multiple sources to detect patterns of malicious activity.
Threat detection also involves understanding the behavior of attackers and anticipating their tactics. IT professionals need to develop proactive measures, such as intrusion detection systems, anomaly monitoring, and automated response scripts. The ability to detect threats quickly and accurately is essential for maintaining secure and resilient server environments.
Incident Response and Recovery Planning
Preparing for security incidents involves more than detection; it requires a structured response plan. IT professionals must understand how to contain threats, eradicate malicious activity, and restore affected systems efficiently. Incident response planning includes establishing communication protocols, documenting actions, and analyzing events to prevent recurrence.
Recovery strategies are equally important. Candidates must be able to restore servers, data, and services while minimizing operational downtime. Regularly testing recovery procedures ensures that organizations can respond effectively to real-world security incidents. These skills are critical for maintaining business continuity and protecting organizational assets.
Advanced Authentication and Access Controls
Strong authentication methods and access controls are fundamental to securing server environments. Candidates must be proficient in implementing multi-factor authentication, configuring conditional access policies, and managing smart card logon. These measures add layers of security that make it more difficult for attackers to gain unauthorized access.
Access control policies should be regularly reviewed and updated to reflect changes in organizational roles and responsibilities. IT professionals need to monitor account activity, detect anomalies, and enforce least privilege principles. Effective access management reduces the risk of insider threats and external attacks, strengthening overall network security.
Protecting Data and Communication
Data protection is a key responsibility for security professionals. Candidates must understand encryption techniques for data at rest and in transit, configure secure communication protocols, and implement access controls to prevent unauthorized data exposure. This includes using BitLocker, IPsec, and TLS configurations to safeguard sensitive information.
Protecting communication channels involves securing both internal and external traffic. IT professionals need to monitor network traffic for unusual activity, apply security policies to prevent data leakage, and ensure that communication endpoints are properly authenticated and authorized. These practices maintain confidentiality, integrity, and availability of critical data.
Monitoring and Auditing Security Configurations
Continuous monitoring and auditing are essential for maintaining secure server environments. Candidates must learn to use built-in tools and scripts to track changes, detect misconfigurations, and ensure compliance with organizational policies. Auditing provides visibility into user activities, system modifications, and access attempts, allowing proactive identification of potential risks.
Monitoring also involves analyzing trends and correlating events across multiple systems. IT professionals must be able to interpret security logs, generate reports, and take corrective actions when deviations from best practices are identified. This proactive approach ensures that security measures remain effective and that vulnerabilities are addressed promptly.
Security in Hybrid and Cloud Environments
Many organizations operate hybrid environments that combine on-premises servers with cloud services. Candidates must understand how to secure workloads across both environments, manage identity and access consistently, and monitor for threats that span multiple platforms. Security strategies should include policies for cloud integration, identity federation, and secure data transfers.
Hybrid security requires familiarity with cloud-based monitoring tools, encryption standards, and compliance frameworks. IT professionals must be capable of implementing security policies that protect workloads regardless of location, ensuring seamless protection across diverse infrastructure components.
Automating Security Tasks
Automation plays a critical role in maintaining consistent security practices. Candidates must learn to use scripts and automation tools to enforce policies, deploy updates, and respond to security incidents efficiently. Automation reduces the potential for human error and allows security teams to focus on more complex threats.
Effective use of automation includes scheduling security scans, configuring alerts, and executing predefined response actions. IT professionals should be able to design workflows that integrate monitoring, detection, and remediation processes, ensuring rapid and accurate response to security events.
Scenario-Based Problem Solving
Practical problem-solving is a core component of mastering server security. Candidates should engage in scenario-based exercises where they encounter simulated breaches, misconfigurations, and attacks. These exercises enhance critical thinking and decision-making skills, allowing professionals to respond effectively under pressure.
Scenario-based learning also reinforces theoretical knowledge by applying it to realistic situations. Candidates practice analyzing system states, identifying vulnerabilities, and implementing corrective measures. This hands-on experience builds confidence and prepares professionals for both the exam and real-world responsibilities.
Continuous Professional Development
Maintaining expertise in Windows Server security requires ongoing education. IT professionals should stay informed about emerging threats, updates to server platforms, and evolving best practices. Continuous learning ensures that skills remain relevant and effective, allowing professionals to adapt to new challenges and technologies.
Regularly reviewing security documentation, experimenting in test environments, and participating in knowledge-sharing activities strengthens understanding and keeps professionals prepared for complex scenarios. Staying current with trends and tools enhances both exam readiness and professional capability.
Integrating Security Practices Across IT Operations
Security is not a standalone function; it must be integrated into overall IT operations. Candidates must understand how to align security practices with operational procedures, change management, and system maintenance. This ensures that protective measures do not disrupt functionality while maintaining compliance with organizational policies.
Integration also involves collaboration across teams, including network administrators, system engineers, and security analysts. Coordinated efforts improve incident response, streamline monitoring, and enhance overall system resilience. Understanding this integration prepares professionals for leadership roles in IT security.
Building Resilient IT Environments
Ultimately, the goal of securing Windows Server environments is to create resilient systems that can withstand and recover from attacks. Candidates must learn to implement redundant configurations, backup strategies, and failover mechanisms to ensure continuity. This resilience minimizes the impact of disruptions and maintains operational availability.
Resilient environments require careful planning, regular testing, and proactive monitoring. IT professionals must balance security measures with performance and usability, creating systems that are both secure and efficient. Mastery of these principles equips professionals to manage complex infrastructures confidently and effectively.
Developing advanced skills in Windows Server security prepares IT professionals to manage, monitor, and protect complex network infrastructures. Knowledge of privileged identity management, server hardening, threat detection, access control, data protection, and automation ensures that candidates are ready to tackle real-world challenges. Scenario-based learning, continuous monitoring, and proactive threat mitigation further enhance readiness, providing a strong foundation for professional growth in network and server security roles.
Protecting Identity and Credential Information
Securing identity and credential information is one of the most critical aspects of maintaining a secure Windows Server environment. Professionals must understand the processes for safeguarding passwords, service accounts, and cryptographic keys. Best practices include enforcing strong password policies, using secure password vaults, and monitoring for unauthorized access attempts. Understanding how to configure authentication protocols to ensure secure logins is vital. Implementing multi-factor authentication adds an additional layer of security, reducing the risk of compromised accounts.
Regularly auditing account activity is necessary to detect potential misuse of credentials. IT professionals need to establish alerts for unusual login patterns, privilege escalations, and suspicious administrative actions. By actively monitoring identity-related activity, teams can prevent potential breaches and maintain organizational security integrity.
Securing Administrative Roles and Privileges
Administrative privileges provide significant control over servers and systems. If mismanaged, they can become a primary target for attackers. Professionals must learn strategies to limit exposure, such as just-in-time administrative access, separation of duties, and role-based access control. Implementing these techniques ensures that administrative rights are only granted when necessary and revoked promptly after use.
Regular monitoring and auditing of privileged activities help maintain accountability. IT professionals must be able to detect anomalies, enforce policy adherence, and respond to unauthorized actions. Protecting administrative roles is foundational to maintaining a resilient network environment and preventing major breaches.
Implementing Server Hardening
Server hardening involves applying a structured approach to reduce vulnerabilities in the Windows Server infrastructure. Candidates must learn to disable unnecessary services, remove default configurations that pose security risks, and apply security templates and updates. This process also includes configuring encryption, network restrictions, and logging mechanisms to monitor activity and detect potential threats.
Understanding how to harden servers according to workload requirements is crucial. Different services and applications require tailored security configurations to ensure they are protected against exploitation. Professionals must continually evaluate server settings and adapt configurations to address emerging vulnerabilities effectively.
Network Segmentation and Security
Securing network infrastructure is essential for preventing lateral movement by attackers. IT professionals must learn to implement network segmentation, configure firewalls, and enforce traffic restrictions between critical and non-critical systems. Segmentation limits exposure and contains potential threats, preventing an attacker from accessing all resources if one system is compromised.
Advanced network monitoring techniques are also part of this process. Candidates should be proficient in analyzing traffic patterns, detecting anomalies, and responding to suspicious activity. Combining network segmentation with proactive monitoring provides a strong defense against intrusions and helps maintain a secure operational environment.
Securing Virtualized Environments
Virtualization introduces unique security challenges. Candidates must understand how to configure virtual machines, control access to hypervisors, and manage virtual networks securely. Protecting virtual environments involves isolating workloads, enforcing role-based permissions, and monitoring virtual switches for anomalies.
Security policies should extend across both physical and virtual components, ensuring consistent protection regardless of the infrastructure layer. Professionals must also plan for patching and updating virtual environments without disrupting operations. Mastery of virtualized security ensures robust protection in increasingly complex IT environments.
Threat Detection and Analysis
Proactively detecting threats is a critical skill for IT professionals managing Windows Server systems. Candidates must learn to use built-in and third-party tools to identify suspicious activity, correlate logs from multiple sources, and generate actionable alerts. Threat analysis involves understanding attack vectors, recognizing patterns of malicious behavior, and implementing preventative measures.
Automated monitoring and alerting are key components of modern security practices. IT professionals must configure these systems to ensure timely detection while minimizing false positives. Regularly reviewing alerts and investigating incidents allows teams to refine detection strategies and maintain strong defenses against potential breaches.
Incident Response and Recovery
Effective incident response requires a structured approach to contain, investigate, and remediate security events. IT professionals must develop plans for identifying compromised systems, isolating affected workloads, and mitigating damage. Recovery strategies include restoring backups, patching vulnerabilities, and validating system integrity to ensure normal operations resume.
Scenario-based exercises help candidates develop the ability to respond under pressure. These exercises simulate real-world attacks, allowing professionals to practice decision-making, communication, and remediation processes. Preparing for incident response strengthens confidence and ensures readiness to manage actual security incidents.
Data Protection and Encryption
Protecting sensitive data is an essential aspect of securing Windows Server environments. Candidates must understand encryption methods for data at rest and in transit, including configuring secure protocols, encrypting storage, and enforcing access controls. Techniques such as BitLocker, TLS, and IPsec provide essential safeguards against unauthorized access.
Monitoring and auditing data access is equally important. IT professionals must detect anomalies, enforce compliance, and respond to potential breaches promptly. Properly implemented data protection measures help maintain confidentiality, integrity, and availability of critical information.
Automation and Security Management
Automation improves consistency and efficiency in security operations. Candidates must learn to implement automated scripts, policies, and monitoring routines to maintain a secure environment. Automation reduces the risk of human error and allows security teams to focus on complex and high-priority tasks.
Examples include automated patch management, routine compliance checks, and predefined response workflows. IT professionals should design these processes to integrate with monitoring and threat detection systems, ensuring rapid and accurate response to security incidents.
Security in Hybrid Environments
Hybrid environments that combine on-premises servers with cloud services present unique security considerations. Candidates must understand how to manage identities, enforce policies, and monitor workloads across both environments. Protecting hybrid infrastructure requires consistent configurations, secure data transfer, and monitoring of potential vulnerabilities.
IT professionals must also ensure that cloud services adhere to organizational security policies and maintain compliance standards. Coordinating security measures across environments strengthens overall resilience and minimizes potential gaps in defense.
Continuous Monitoring and Auditing
Continuous monitoring ensures that security configurations remain effective over time. Candidates must learn to track changes, detect misconfigurations, and evaluate compliance with established policies. Auditing provides visibility into user activities, system modifications, and access attempts, supporting proactive security management.
Analyzing trends and correlating events across systems allows IT professionals to identify emerging threats and refine security measures. Regular review and reporting ensure that systems remain resilient against evolving risks.
Scenario-Based Learning
Applying theoretical knowledge to realistic scenarios enhances practical skills. Candidates should engage in exercises simulating breaches, misconfigurations, and attacks. Scenario-based learning develops problem-solving abilities, critical thinking, and decision-making under pressure.
These exercises reinforce understanding of security principles while providing opportunities to apply them in controlled environments. Hands-on experience prepares professionals for both the exam and real-world responsibilities.
Security Integration and Best Practices
Security must be integrated into all aspects of IT operations. Candidates must learn to align security measures with operational procedures, change management, and system maintenance. Integration ensures that protective measures are consistent, effective, and do not disrupt business operations.
Collaboration across IT teams is essential for effective security. Coordinated efforts improve monitoring, incident response, and policy enforcement. Understanding how security fits into broader IT operations positions professionals to lead initiatives and maintain resilient systems.
Resilience and Business Continuity
Building resilient IT environments is crucial for maintaining operational stability during attacks. Candidates must learn to implement redundancy, backup strategies, and failover mechanisms. Resilient systems can continue operating during incidents, minimizing downtime and preserving data integrity.
Regular testing of recovery procedures ensures readiness for actual events. IT professionals must balance security measures with usability and performance, maintaining both protection and efficiency. Mastery of resilience principles prepares professionals for advanced roles in network and server security.
Continuous Professional Growth
Maintaining expertise in server security requires ongoing learning. IT professionals should stay informed about emerging threats, updates to platforms, and new security tools. Continuous practice, lab exercises, and scenario simulations reinforce knowledge and improve readiness.
Engaging in knowledge-sharing, evaluating case studies, and exploring new security technologies ensures professionals remain capable of addressing complex and evolving challenges. Continuous growth strengthens both certification preparedness and professional competency.
Securing Windows Server environments demands expertise across multiple domains, including identity management, administrative control, workload hardening, network and virtualization security, threat detection, incident response, and data protection. Developing practical skills through hands-on labs, scenario-based exercises, and continuous monitoring equips IT professionals to protect complex infrastructures effectively. Mastery of these areas prepares candidates for the 70-744 exam and positions them for leadership roles in server security and network administration.
Advanced Threat Mitigation Strategies
Understanding and implementing advanced threat mitigation is crucial for managing secure server environments. Candidates must learn to recognize potential attack vectors, assess risks, and apply appropriate countermeasures. This includes the use of intrusion detection systems, anomaly detection, and behavioral analysis tools to monitor network traffic and server activity. Proactive identification of threats allows IT professionals to neutralize risks before they escalate into serious incidents.
Professionals must also develop strategies for dealing with zero-day vulnerabilities, ransomware, and other sophisticated attacks. This involves continuous evaluation of system configurations, patch management, and implementing layered security measures. By combining detection, prevention, and response strategies, candidates ensure the resilience of Windows Server environments.
Policy Implementation and Governance
Security governance involves creating and enforcing policies that define acceptable use, access permissions, and operational procedures. Candidates must be skilled in designing policies that align with organizational objectives while minimizing security risks. These policies should cover user management, system configurations, patching schedules, and incident response protocols.
Effective governance requires consistent monitoring and enforcement. IT professionals must evaluate compliance, detect deviations, and implement corrective actions promptly. Understanding governance frameworks and their application in Windows Server environments prepares candidates for structured security management and reduces vulnerabilities.
Patch Management and Vulnerability Remediation
Timely patch management is a cornerstone of secure IT operations. Candidates must learn to identify, test, and deploy patches for operating systems, applications, and virtualization platforms. Proper patching prevents exploitation of known vulnerabilities and reduces the likelihood of security incidents.
Vulnerability remediation involves conducting regular assessments, prioritizing risks, and implementing fixes systematically. IT professionals must also maintain records of applied updates and ensure that remediation strategies do not disrupt business operations. This proactive approach strengthens overall system integrity and prepares candidates for security-focused responsibilities.
Endpoint Security and Device Management
Securing endpoints, including desktops, laptops, and servers, is essential for comprehensive network protection. Candidates must understand how to configure endpoint protection solutions, manage antivirus and antimalware tools, and enforce security policies on connected devices. Regular updates and monitoring ensure that endpoints remain resilient against emerging threats.
Device management includes controlling access to network resources, applying encryption, and monitoring for unauthorized devices. IT professionals must be able to respond to potential endpoint compromises quickly to prevent wider system exposure. Effective endpoint security practices are fundamental to reducing organizational risk.
Security Monitoring and Reporting
Monitoring systems for security events provides visibility into potential risks and operational issues. Candidates must learn to configure logs, alerts, and dashboards that track critical activities across servers and network infrastructure. Analysis of these logs helps identify anomalies, suspicious behaviors, and potential breaches.
Reporting mechanisms are equally important, providing documentation for management, compliance audits, and incident investigations. IT professionals should be able to generate detailed reports on security posture, actions taken, and recommendations for improvements. Continuous monitoring and reporting create a proactive security culture within the organization.
Encryption and Key Management
Encryption protects sensitive data from unauthorized access. Candidates must understand how to implement encryption for data at rest, data in transit, and communications between systems. Proper key management ensures that encryption remains effective and that keys are protected from misuse.
Best practices include rotating keys regularly, storing them securely, and monitoring their usage. IT professionals must also understand how to integrate encryption with backup processes and virtualized environments. Strong encryption practices maintain data confidentiality and integrity across all layers of the infrastructure.
Disaster Recovery and Business Continuity Planning
Preparing for potential disruptions is essential in maintaining secure operations. Candidates must develop disaster recovery plans that include backup strategies, system restoration procedures, and failover mechanisms. Business continuity planning ensures that critical operations can continue even during security incidents or infrastructure failures.
Testing recovery procedures is crucial to ensure effectiveness. IT professionals must simulate various scenarios, identify weaknesses, and refine processes to improve resilience. A well-planned disaster recovery and continuity strategy reduces downtime, protects data, and strengthens organizational readiness.
Security for Cloud and Hybrid Environments
Many organizations operate in hybrid environments combining on-premises and cloud infrastructure. Candidates must understand how to implement consistent security policies, manage access, and monitor threats across these environments. This includes securing cloud storage, virtual machines, and remote access connections.
Effective hybrid security involves integrating monitoring tools, encryption protocols, and identity management across platforms. IT professionals must ensure that workloads remain protected regardless of their location. Understanding these dynamics prepares candidates to manage complex infrastructures while minimizing security gaps.
Threat Intelligence and Risk Assessment
Analyzing threat intelligence helps IT professionals anticipate potential attacks and adjust defenses accordingly. Candidates must be able to gather information about emerging threats, evaluate the impact, and implement mitigation strategies. Risk assessment involves identifying vulnerabilities, quantifying potential losses, and prioritizing security actions based on organizational priorities.
By combining threat intelligence with proactive risk management, IT professionals can maintain a dynamic and responsive security posture. Regular assessments and updates to security strategies help organizations stay ahead of evolving threats and ensure compliance with best practices.
Security Automation and Orchestration
Automation streamlines repetitive security tasks, allowing professionals to focus on complex incidents. Candidates must learn to deploy scripts, configure automated monitoring, and integrate security workflows across systems. Automation reduces human error, accelerates response times, and ensures consistent enforcement of security policies.
Orchestration involves coordinating multiple security tools and processes to provide a cohesive defense strategy. IT professionals should design automated responses to common incidents, such as malware detection or unauthorized access attempts. Effective automation and orchestration improve overall efficiency and resilience.
Security Auditing and Compliance
Ensuring compliance with organizational and regulatory standards is a key responsibility. Candidates must understand how to conduct security audits, evaluate adherence to policies, and document findings. Compliance auditing provides accountability and identifies areas requiring improvement.
Auditing should be integrated with continuous monitoring to provide real-time insights. IT professionals must maintain detailed records of configurations, user activity, and system changes. This process supports transparency, accountability, and informed decision-making within the organization.
Practical Scenario Exercises
Hands-on exercises simulate real-world security incidents, allowing candidates to apply theoretical knowledge in practical situations. These scenarios may involve analyzing breaches, mitigating threats, or configuring secure systems under pressure. Scenario-based learning develops critical thinking, problem-solving, and operational skills.
Repeated exposure to practical scenarios builds confidence and prepares IT professionals for actual challenges they may encounter in server security roles. This approach enhances both exam readiness and professional competence in securing Windows Server environments.
Continuous Learning and Professional Development
Staying current with technological advancements, emerging threats, and security methodologies is essential for IT professionals. Continuous learning involves experimenting in lab environments, reviewing case studies, and participating in discussions with peers.
Professionals must remain adaptable and update their skills regularly to maintain proficiency in Windows Server security. Ongoing development ensures they can address complex threats effectively and remain prepared for evolving challenges in network and server security.
Integrating Security Into IT Operations
Security must be an integral part of overall IT operations. Candidates should understand how to align security strategies with system administration, network management, and operational workflows. Integration ensures that security practices are consistently applied without disrupting organizational processes.
Collaboration between security, network, and system teams enhances threat detection, incident response, and policy enforcement. Effective integration strengthens overall IT resilience and prepares professionals to lead security initiatives within complex infrastructures.
Advanced skills in securing Windows Server environments involve managing privileged accounts, hardening systems, protecting data, monitoring threats, and responding to incidents. Candidates must master automation, auditing, hybrid security, and disaster recovery planning. Practical scenario exercises and continuous learning reinforce expertise, ensuring IT professionals are prepared to manage complex infrastructures confidently. Developing proficiency across these areas equips candidates for the 70-744 exam and establishes a strong foundation for leadership roles in server security and network administration.
Implementing Multi-Layered Security
Effective Windows Server security requires a multi-layered approach to protect against a variety of threats. Candidates must understand how to apply multiple defensive measures simultaneously, including perimeter security, endpoint protection, encryption, and access controls. Combining these layers ensures that if one defense is bypassed, additional protections remain active to prevent or mitigate damage.
Understanding the interaction between layers is critical. IT professionals need to know how network firewalls, intrusion detection systems, and host-based protections work together. They must also evaluate the effectiveness of each layer regularly and adjust configurations based on evolving threats. A layered security approach strengthens resilience and reduces the likelihood of successful attacks.
Identity and Access Management
Managing identities and access permissions is central to securing Windows Server environments. Candidates must learn to implement policies that restrict access based on roles, responsibilities, and security clearance. This includes enforcing principle of least privilege, managing service accounts, and configuring group policies effectively.
Monitoring and auditing access activity is equally important. IT professionals should detect abnormal login attempts, unauthorized privilege escalations, and unusual account behavior. Implementing robust identity management practices prevents unauthorized access and helps maintain compliance with organizational security policies.
Securing Administrative Operations
Administrative operations can present significant security risks if not properly managed. Candidates must understand how to protect administrator accounts, monitor privileged actions, and enforce just-in-time access policies. Restricting administrative access reduces the attack surface and limits potential damage in case of compromise.
Regularly reviewing administrative activity, logging changes, and validating security configurations ensures ongoing protection. IT professionals must also be prepared to respond to incidents involving privileged accounts, maintaining system integrity and continuity. Securing administrative operations is critical for maintaining control and preventing internal and external breaches.
Hardening Servers and Workloads
Server hardening involves systematically reducing vulnerabilities across operating systems, applications, and workloads. Candidates must learn to disable unnecessary services, remove default accounts, enforce strong configurations, and apply security templates consistently. Each workload may require specific hardening measures depending on its function and exposure.
Ongoing maintenance, patching, and monitoring are essential to maintain hardened configurations. IT professionals should regularly test servers for compliance with security standards and apply corrective actions when deviations occur. Hardening reduces exploit opportunities and strengthens the overall security posture.
Virtualization and Hyper-V Security
Securing virtualized environments introduces unique considerations for IT professionals. Candidates must understand how to protect virtual machines, manage hypervisors securely, and isolate virtual networks. Access control, encryption, and monitoring for anomalies are key components of virtualization security.
Properly configuring virtual switches, controlling administrative access to hypervisors, and segmenting workloads minimizes the risk of attacks spreading across virtual environments. IT professionals must also maintain security practices for templates, snapshots, and backups. Mastery of virtualization security ensures protection for increasingly complex server infrastructures.
Threat Detection and Advanced Monitoring
Proactive threat detection is crucial for maintaining secure server environments. Candidates must learn to configure monitoring tools, analyze system logs, and correlate events to detect suspicious activity. Understanding attack patterns, anomalous behavior, and unusual access attempts allows professionals to respond before serious damage occurs.
Advanced monitoring includes automated alerts, event correlation, and integration with incident response workflows. IT professionals should also leverage threat intelligence to anticipate potential attacks. Continuous monitoring and advanced analysis strengthen defense capabilities and improve response times.
Incident Response Planning
An effective incident response plan prepares organizations to handle security breaches with minimal disruption. Candidates must understand how to identify compromised systems, isolate affected workloads, and remediate threats systematically. Plans should include communication protocols, documentation, and post-incident reviews to improve future responses.
Scenario-based exercises help candidates develop decision-making skills under pressure. Practicing incident response in simulated environments reinforces problem-solving techniques and ensures readiness for real-world challenges. A well-prepared IT professional can contain threats quickly and restore normal operations efficiently.
Data Protection and Encryption Techniques
Protecting sensitive data is a critical aspect of server security. Candidates must understand encryption technologies for data at rest, data in transit, and communications between servers. Secure key management ensures that encryption remains effective and prevents unauthorized access.
Implementing strong access controls, auditing data usage, and regularly reviewing encryption policies maintains data confidentiality and integrity. IT professionals must also integrate encryption with backup and disaster recovery procedures to ensure comprehensive protection across all environments.
Securing Network Infrastructure
Network security is essential to prevent unauthorized access, lateral movement, and data exfiltration. Candidates must learn to segment networks, configure firewalls, enforce secure protocols, and monitor traffic for anomalies. Advanced network protections include intrusion detection systems, threat intelligence integration, and proactive traffic analysis.
Regular auditing of network devices, reviewing configuration changes, and testing for vulnerabilities ensure ongoing protection. IT professionals must maintain consistent policies across all network components to prevent misconfigurations and reduce attack surfaces.
Cloud and Hybrid Environment Security
Modern IT infrastructures often involve hybrid deployments, combining on-premises and cloud resources. Candidates must understand how to enforce consistent security policies, manage identities, and monitor threats across hybrid environments. Cloud security involves protecting workloads, data, and communications while ensuring compliance with organizational policies.
IT professionals must coordinate security measures across platforms, integrate monitoring systems, and implement secure access protocols. Ensuring consistent protection across both environments reduces risk and maintains operational integrity.
Continuous Auditing and Compliance
Ongoing auditing ensures that security measures remain effective and compliant with policies. Candidates must learn to review user activity, configuration changes, and system events systematically. Auditing also provides documentation for reporting, compliance verification, and incident investigations.
Analyzing trends and correlating multiple data sources allows IT professionals to detect deviations and emerging threats. Maintaining detailed records and continuous auditing strengthens organizational accountability and improves decision-making.
Automation of Security Processes
Automation improves efficiency and reduces errors in security management. Candidates should be familiar with automating monitoring, patch management, threat detection, and incident response workflows. Automated processes enforce consistency, accelerate responses, and allow IT professionals to focus on high-priority tasks.
Orchestration of multiple security tools ensures cohesive defense strategies. By integrating automated responses with monitoring systems, professionals can rapidly mitigate threats and maintain robust protection across all systems.
Practical Scenario-Based Training
Scenario-based exercises simulate real-world incidents, allowing candidates to apply theoretical knowledge in controlled environments. Exercises may include system compromises, malware outbreaks, or configuration errors, requiring immediate response and problem-solving.
This approach develops critical thinking, operational decision-making, and technical proficiency. Regular practice enhances confidence and prepares professionals for both the 70-744 exam and real-world server security responsibilities.
Continuous Learning and Skill Enhancement
Maintaining expertise in Windows Server security requires continuous learning. IT professionals should engage in ongoing study, lab experimentation, and review of emerging threats. Staying informed about new security tools, updates, and attack techniques ensures readiness for evolving challenges.
Developing and refining skills through practice, case studies, and simulations strengthens professional competency. Continuous growth positions candidates to handle complex server environments and take on advanced security roles effectively.
Integration of Security Into Organizational Operations
Security must be seamlessly integrated into daily IT operations. Candidates should understand how to embed security practices into system administration, network management, and operational workflows. Integration ensures that protective measures are consistently applied without disrupting organizational functions.
Collaboration across security, operations, and management teams improves visibility, monitoring, and incident response. Coordinated efforts strengthen defense strategies and create a resilient IT environment capable of withstanding sophisticated attacks.
Mastering Windows Server security involves a comprehensive understanding of identity management, administrative control, server hardening, virtualization security, threat detection, incident response, and data protection. Candidates must also focus on network security, hybrid environments, continuous auditing, automation, and scenario-based learning. Developing expertise in these areas equips IT professionals to handle complex infrastructure challenges, prepares them for the 70-744 exam, and establishes a foundation for advanced roles in network and server security management.
Advanced Identity Protection
Securing administrative and user accounts is fundamental to protecting Windows Server environments. Candidates must learn to implement identity protection strategies, including multi-factor authentication, conditional access policies, and privileged identity management. Controlling access based on risk factors, monitoring user behavior, and applying just-in-time access principles ensures that sensitive accounts are not easily compromised.
Managing service accounts, administrative privileges, and role-based access requires consistent auditing and oversight. IT professionals must be able to respond quickly to potential compromise, revoke access where necessary, and maintain detailed records for accountability. Strong identity protection reduces the likelihood of unauthorized actions and strengthens overall server security.
Implementing Advanced Threat Detection
Advanced threat detection involves using multiple tools and techniques to identify suspicious behavior and potential attacks. Candidates should understand how to configure system and network monitoring, analyze logs, and correlate events to detect anomalies. Knowledge of attack patterns and tactics allows IT professionals to anticipate threats and respond proactively.
Integrating threat intelligence feeds into monitoring solutions provides additional context for detecting sophisticated attacks. Automation and alerts enable faster incident response and reduce the impact of breaches. Mastery of advanced threat detection ensures that Windows Server environments remain secure and resilient.
Server Hardening and Security Baselines
Server hardening involves applying security configurations that reduce the risk of compromise. Candidates must learn to disable unnecessary services, enforce strong password policies, apply system updates, and configure security templates consistently. Security baselines provide standardized configurations that help maintain compliance and protect against common vulnerabilities.
Periodic review of hardening measures is necessary to ensure continued effectiveness. IT professionals must test servers for configuration drift, apply corrective measures, and adapt baselines as threats evolve. Server hardening is a continuous process that strengthens defenses and reduces attack surfaces.
Securing Virtualization Platforms
Virtualized environments present unique security challenges. Candidates should understand how to protect virtual machines, manage hypervisors, and isolate virtual networks. Access control, monitoring, and encryption are essential components of virtualization security.
IT professionals must also implement secure templates, control snapshot usage, and manage virtual machine lifecycle securely. Protecting virtual workloads ensures that threats do not propagate across the environment and that sensitive data remains safe.
Network Segmentation and Perimeter Security
Segmenting networks and implementing perimeter defenses reduces exposure to potential attacks. Candidates must learn to configure firewalls, VLANs, and network access controls to separate critical systems from less sensitive areas. Monitoring network traffic and analyzing anomalies enables early detection of intrusions.
Maintaining consistent configurations and policies across network devices is crucial. IT professionals must regularly audit firewall rules, test segmentation effectiveness, and update defenses to counter emerging threats. Strong perimeter security enhances resilience and limits the impact of potential breaches.
Data Protection and Encryption Management
Protecting sensitive data is essential for server security. Candidates should learn how to implement encryption for data at rest and in transit, manage cryptographic keys, and monitor access to protected information. Integrating encryption with backup and recovery processes ensures that data remains secure even during system restoration.
IT professionals must also enforce strict access controls, monitor data usage, and review policies regularly. Effective data protection safeguards organizational assets and supports compliance with security standards.
Incident Response and Recovery
An effective incident response strategy minimizes the impact of security breaches. Candidates must understand how to identify compromised systems, contain threats, and remediate vulnerabilities. Incident response plans should include roles, responsibilities, communication protocols, and documentation procedures.
Simulation exercises prepare candidates to act quickly under pressure. Reviewing incidents post-event helps refine strategies and improve organizational readiness. Skilled IT professionals can restore normal operations efficiently and reduce the likelihood of repeated incidents.
Automation and Orchestration in Security
Automation streamlines routine security tasks and reduces the potential for human error. Candidates should learn to deploy scripts, configure automated alerts, and integrate responses into workflows. Automation allows IT professionals to focus on complex threats while maintaining consistent enforcement of security policies.
Orchestration coordinates multiple tools and processes to provide cohesive defense strategies. Automating common incident responses accelerates mitigation and ensures standardized handling across systems. Effective automation and orchestration improve security posture and operational efficiency.
Continuous Monitoring and Reporting
Ongoing monitoring is critical for maintaining secure server environments. Candidates must understand how to collect logs, configure alerts, and analyze events for signs of suspicious activity. Regular reporting provides visibility into security posture and supports compliance and decision-making.
IT professionals must be able to generate detailed reports on configurations, incidents, and user activity. Continuous monitoring enables proactive threat identification and timely response, reducing the risk of prolonged exposure to attacks.
Cloud and Hybrid Environment Security
Many organizations use hybrid environments that combine on-premises servers with cloud resources. Candidates should learn to enforce consistent security policies, monitor activity, and manage access across all platforms. Cloud security requires protecting workloads, data, and communications while maintaining compliance with organizational requirements.
Integration of monitoring and access controls ensures that hybrid environments remain secure. IT professionals must manage identities, enforce encryption, and apply consistent policies to protect sensitive information across platforms. Understanding hybrid security enables professionals to manage complex infrastructures effectively.
Compliance and Regulatory Considerations
Adhering to compliance standards and regulations is essential for organizational accountability. Candidates must learn to conduct audits, evaluate policy adherence, and document findings systematically. Compliance ensures that security practices meet internal and external expectations.
Regular audits, continuous monitoring, and detailed reporting help identify weaknesses and enforce corrective measures. IT professionals must maintain records of configurations, activities, and incidents to support transparency and accountability. Compliance-focused practices improve overall security posture and organizational trust.
Hands-On Scenario Training
Practical exercises provide candidates with experience in handling real-world security incidents. Scenarios may include responding to malware outbreaks, unauthorized access, or system misconfigurations. Hands-on practice develops problem-solving, decision-making, and technical proficiency.
Repetition of scenario-based exercises builds confidence and prepares candidates for both the 70-744 exam and actual security challenges in professional environments. Practical experience reinforces theoretical knowledge and enhances operational readiness.
Skill Development and Continuous Learning
Continuous learning is essential to maintain expertise in Windows Server security. Candidates should engage in labs, case studies, and peer discussions to stay informed about emerging threats and evolving technologies. Experimentation and review of new tools help professionals adapt to changing security landscapes.
Ongoing skill enhancement ensures that IT professionals remain capable of addressing complex challenges and implementing best practices. Continuous learning supports career growth and prepares candidates for advanced responsibilities in server security management.
Security Integration Across IT Operations
Security must be integrated into all IT operations to be effective. Candidates should understand how to embed protective measures into system administration, network management, and operational workflows. Integration ensures consistent application of security practices without disrupting business processes.
Collaboration between security teams, network administrators, and system operators enhances detection, response, and enforcement. A cohesive approach creates a resilient environment capable of withstanding sophisticated attacks while maintaining operational continuity.
Advanced knowledge in server security encompasses identity management, administrative protection, server hardening, virtualization security, threat detection, incident response, and data protection. Candidates must also master network security, hybrid environments, continuous monitoring, automation, and scenario-based training. Developing expertise in these areas prepares IT professionals for the 70-744 exam and positions them to manage complex Windows Server infrastructures effectively, ensuring resilience, compliance, and operational security.
Implementing Advanced Access Controls
Access control is a fundamental component of securing Windows Server environments. Candidates must understand how to configure permissions effectively, manage group memberships, and enforce principle of least privilege. Controlling access to sensitive data, administrative functions, and critical applications ensures that only authorized users can perform essential operations.
IT professionals must be able to monitor account activity, detect privilege escalations, and respond to unauthorized attempts. Implementing tiered administrative models and just-in-time access policies reduces exposure and mitigates potential risks. Advanced access control strengthens overall security by limiting the impact of compromised accounts.
Security Monitoring and Threat Analysis
Continuous monitoring is essential to detect security incidents promptly. Candidates should learn to configure monitoring tools, collect logs, and analyze system events for signs of suspicious activity. Understanding attack vectors and anomaly detection allows IT professionals to anticipate potential threats.
Threat analysis involves correlating data from multiple sources, evaluating system behavior, and identifying deviations from expected patterns. Integrating automated alerts and threat intelligence improves response times and reduces the likelihood of prolonged breaches. Effective monitoring and analysis create a proactive security posture.
System Hardening Techniques
System hardening reduces vulnerabilities by applying consistent security configurations across servers. Candidates must understand how to disable unnecessary services, enforce strong authentication methods, and implement security templates for standardization. Hardening measures should be tested regularly to ensure compliance and effectiveness.
Applying patches promptly, configuring audit policies, and reviewing system settings are essential parts of hardening. IT professionals must also validate that critical configurations remain intact over time, preventing unauthorized changes that could compromise security. System hardening minimizes exposure to common attack methods.
Virtualization Security Practices
Virtualized environments require specialized security approaches. Candidates should learn to secure hypervisors, manage virtual machines, and segment virtual networks. Controlling access to virtual resources, encrypting virtual disks, and monitoring activity are essential practices.
Managing snapshots, templates, and virtual machine lifecycles securely prevents the spread of vulnerabilities. IT professionals must ensure that virtualized workloads maintain the same level of security as physical systems, providing consistent protection across the environment.
Network Defense and Segmentation
Protecting network infrastructure is a critical element of server security. Candidates should understand how to implement firewalls, configure network segmentation, and enforce secure communication protocols. Monitoring traffic for unusual patterns enables early detection of intrusion attempts.
Regular auditing of network configurations, reviewing firewall rules, and verifying access controls maintain effective defense mechanisms. IT professionals must ensure that segmentation isolates sensitive resources, limiting potential damage in case of compromise. Strong network defenses reduce the overall risk to Windows Server environments.
Data Security and Encryption Management
Safeguarding data involves implementing robust encryption and access control measures. Candidates must learn to encrypt data at rest, in transit, and across backups. Proper management of encryption keys ensures that only authorized users can access sensitive information.
Auditing data access, reviewing permissions, and applying strict policies help maintain data confidentiality and integrity. Integrating encryption into backup and recovery processes ensures that information remains protected during restoration or migration. Data security is a critical aspect of overall server protection.
Incident Response and Remediation
Incident response prepares organizations to address security breaches efficiently. Candidates must understand how to identify compromised systems, isolate affected components, and remediate threats systematically. Effective response plans include communication protocols, documentation procedures, and post-incident analysis.
Simulated exercises develop problem-solving and decision-making skills under pressure. IT professionals must be able to restore normal operations quickly, minimizing disruption and preventing recurrence. Strong incident response capabilities ensure resilience against evolving threats.
Automation and Orchestration in Security
Automating routine security processes improves efficiency and reduces the potential for human error. Candidates should be familiar with scripting, automated alerting, and integration of incident response workflows. Orchestration allows multiple security tools to work together, providing a coordinated defense.
Automation ensures consistent enforcement of policies, accelerates responses to incidents, and allows IT professionals to focus on complex threats. Proper implementation of automated systems enhances the reliability and effectiveness of server security practices.
Continuous Compliance and Auditing
Maintaining compliance requires continuous monitoring and auditing of system configurations, user activity, and security events. Candidates must learn to document findings, evaluate adherence to policies, and implement corrective actions where necessary. Auditing supports organizational accountability and ensures that security measures meet required standards.
Analyzing trends and correlating information from multiple sources allows for early detection of weaknesses. Detailed records provide transparency and enable verification of security controls. Compliance-focused practices strengthen protection and reduce potential regulatory risks.
Cloud and Hybrid Security Considerations
Hybrid environments that combine on-premises servers with cloud services introduce additional security challenges. Candidates should learn to manage identities, enforce policies, and monitor activity across both platforms. Cloud security involves protecting workloads, data, and communications while ensuring consistent access control.
Integrating monitoring systems, applying encryption, and standardizing configurations maintain secure hybrid operations. IT professionals must understand how to extend on-premises security practices to cloud resources, ensuring comprehensive protection and operational continuity.
Security Policy Development and Implementation
Developing clear and enforceable security policies is critical for effective server protection. Candidates must learn to define acceptable use, access permissions, incident response procedures, and configuration standards. Policies should be practical, enforceable, and regularly reviewed to adapt to evolving threats.
IT professionals play a key role in implementing policies, monitoring compliance, and training users. Consistent policy enforcement ensures that security practices are applied uniformly across the organization, reducing vulnerabilities and strengthening defenses.
Hands-On Scenario Practice
Practical experience reinforces theoretical knowledge and prepares candidates for real-world challenges. Scenario-based exercises simulate breaches, malware outbreaks, and configuration errors, requiring immediate response. Hands-on practice builds technical proficiency, decision-making skills, and confidence.
Repeated exercises allow IT professionals to refine their approach to threat mitigation, incident handling, and operational recovery. This experiential learning is essential for success on the 70-744 exam and in professional server security roles.
Continuous Skill Enhancement
Security in Windows Server environments evolves rapidly, requiring ongoing learning. Candidates should engage in regular study, lab work, and review of emerging threats. Experimentation with new tools, configurations, and monitoring techniques strengthens expertise.
Continuous development ensures that IT professionals can adapt to changing attack vectors and maintain high levels of protection. Skill enhancement positions candidates for advanced responsibilities and effective management of complex server infrastructures.
Security Integration Across IT Operations
Embedding security practices into daily IT operations ensures consistent protection. Candidates must understand how to integrate monitoring, access control, configuration management, and incident response into standard workflows. Coordinated efforts enhance detection, response, and overall system resilience.
Collaboration between IT teams, security professionals, and management ensures that security is considered in all operational decisions. Integrated practices reduce risks, maintain compliance, and support organizational continuity, establishing a robust defense against threats.
Comprehensive mastery of Windows Server security encompasses access control, monitoring, server hardening, virtualization security, network protection, data encryption, incident response, automation, compliance, hybrid security, policy development, hands-on practice, skill enhancement, and operational integration. Developing expertise in these areas equips IT professionals to manage complex environments, address evolving threats, and succeed on the 70-744 exam, ensuring they can protect organizational infrastructure effectively and maintain operational resilience.
Conclusion
Securing Windows Server environments requires a multifaceted approach that combines technical knowledge, practical skills, and strategic thinking. Mastery of access control, monitoring, threat detection, server hardening, and virtualization security is essential for protecting critical infrastructure from evolving threats. IT professionals must understand how to safeguard sensitive data, implement encryption, and manage administrative privileges effectively.
Equally important is the ability to respond to incidents promptly and systematically. Developing and following incident response plans, conducting simulations, and continuously refining processes ensures that security breaches are contained and mitigated efficiently. Automation and orchestration further enhance these capabilities by streamlining routine tasks and coordinating responses across multiple systems.
Continuous monitoring, auditing, and compliance management provide visibility into system activity and ensure that security policies are enforced consistently. Hybrid and cloud environments add complexity to security management, requiring IT professionals to maintain consistent policies, protect workloads, and monitor access across platforms. Developing expertise in these areas ensures that organizations can operate securely while leveraging modern technologies.
Practical, scenario-based training is invaluable in preparing candidates for real-world challenges. By engaging in hands-on exercises, IT professionals develop problem-solving skills, technical proficiency, and confidence in handling complex security situations. Continuous skill enhancement, staying informed about emerging threats, and experimenting with new tools and techniques are crucial for maintaining expertise and adaptability in a dynamic security landscape.
Integrating security into daily IT operations and collaborating across teams strengthens organizational resilience. Security practices must be embedded in configuration management, network monitoring, access control, and incident response workflows to create a cohesive and effective defense. This comprehensive approach enables IT professionals to manage risks proactively, protect critical assets, and ensure operational continuity.
Achieving mastery in Windows Server security and successfully completing the 70-744 exam validates an individual’s ability to implement advanced protection measures, respond effectively to threats, and maintain a secure IT environment. The knowledge, skills, and experience gained through this preparation empower IT professionals to safeguard organizational infrastructure, contribute to strategic security initiatives, and advance in their careers while meeting the evolving demands of the field.
Microsoft MCSE 70-744 practice test questions and answers, training course, study guide are uploaded in ETE Files format by real users. Study and Pass 70-744 Securing Windows Server 2016 certification exam dumps & practice test questions and answers are to help students.
Exam Comments * The most recent comment are on top
- AZ-104 - Microsoft Azure Administrator
- AI-900 - Microsoft Azure AI Fundamentals
- AI-102 - Designing and Implementing a Microsoft Azure AI Solution
- AZ-305 - Designing Microsoft Azure Infrastructure Solutions
- DP-700 - Implementing Data Engineering Solutions Using Microsoft Fabric
- MD-102 - Endpoint Administrator
- AZ-900 - Microsoft Azure Fundamentals
- PL-300 - Microsoft Power BI Data Analyst
- MS-102 - Microsoft 365 Administrator
- SC-300 - Microsoft Identity and Access Administrator
- AZ-500 - Microsoft Azure Security Technologies
- SC-200 - Microsoft Security Operations Analyst
- SC-401 - Administering Information Security in Microsoft 365
- AZ-700 - Designing and Implementing Microsoft Azure Networking Solutions
- DP-600 - Implementing Analytics Solutions Using Microsoft Fabric
- AZ-204 - Developing Solutions for Microsoft Azure
- SC-100 - Microsoft Cybersecurity Architect
- PL-200 - Microsoft Power Platform Functional Consultant
- AZ-400 - Designing and Implementing Microsoft DevOps Solutions
- AZ-140 - Configuring and Operating Microsoft Azure Virtual Desktop
- PL-400 - Microsoft Power Platform Developer
- AZ-800 - Administering Windows Server Hybrid Core Infrastructure
- SC-900 - Microsoft Security, Compliance, and Identity Fundamentals
- GH-300 - GitHub Copilot
- DP-300 - Administering Microsoft Azure SQL Solutions
- PL-600 - Microsoft Power Platform Solution Architect
- MS-900 - Microsoft 365 Fundamentals
- AZ-801 - Configuring Windows Server Hybrid Advanced Services
- MS-700 - Managing Microsoft Teams
- MB-280 - Microsoft Dynamics 365 Customer Experience Analyst
- PL-900 - Microsoft Power Platform Fundamentals
- MB-330 - Microsoft Dynamics 365 Supply Chain Management
- MB-800 - Microsoft Dynamics 365 Business Central Functional Consultant
- AB-730 - AI Business Professional
- DP-900 - Microsoft Azure Data Fundamentals
- MB-310 - Microsoft Dynamics 365 Finance Functional Consultant
- DP-100 - Designing and Implementing a Data Science Solution on Azure
- MB-820 - Microsoft Dynamics 365 Business Central Developer
- MB-230 - Microsoft Dynamics 365 Customer Service Functional Consultant
- AB-100 - Agentic AI Business Solutions Architect
- AB-731 - AI Transformation Leader
- MS-721 - Collaboration Communications Systems Engineer
- PL-500 - Microsoft Power Automate RPA Developer
- GH-900 - GitHub Foundations
- MB-500 - Microsoft Dynamics 365: Finance and Operations Apps Developer
- MB-700 - Microsoft Dynamics 365: Finance and Operations Apps Solution Architect
- MB-335 - Microsoft Dynamics 365 Supply Chain Management Functional Consultant Expert
- GH-200 - GitHub Actions
- DP-420 - Designing and Implementing Cloud-Native Applications Using Microsoft Azure Cosmos DB
- GH-500 - GitHub Advanced Security
- MB-240 - Microsoft Dynamics 365 for Field Service
- GH-100 - GitHub Administration
- AZ-120 - Planning and Administering Microsoft Azure for SAP Workloads
- AZ-303 - Microsoft Azure Architect Technologies
- DP-203 - Data Engineering on Microsoft Azure
- SC-400 - Microsoft Information Protection Administrator
- MB-910 - Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM)
- MB-920 - Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP)
- 62-193 - Technology Literacy for Educators
- 98-383 - Introduction to Programming Using HTML and CSS
- MO-100 - Microsoft Word (Word and Word 2019)
- MO-300 - Microsoft PowerPoint (PowerPoint and PowerPoint 2019)
- MB-210 - Microsoft Dynamics 365 for Sales
Why customers love us?
What do our customers say?
The resources provided for the Microsoft certification exam were exceptional. The exam dumps and video courses offered clear and concise explanations of each topic. I felt thoroughly prepared for the 70-744 test and passed with ease.
Studying for the Microsoft certification exam was a breeze with the comprehensive materials from this site. The detailed study guides and accurate exam dumps helped me understand every concept. I aced the 70-744 exam on my first try!
I was impressed with the quality of the 70-744 preparation materials for the Microsoft certification exam. The video courses were engaging, and the study guides covered all the essential topics. These resources made a significant difference in my study routine and overall performance. I went into the exam feeling confident and well-prepared.
The 70-744 materials for the Microsoft certification exam were invaluable. They provided detailed, concise explanations for each topic, helping me grasp the entire syllabus. After studying with these resources, I was able to tackle the final test questions confidently and successfully.
Thanks to the comprehensive study guides and video courses, I aced the 70-744 exam. The exam dumps were spot on and helped me understand the types of questions to expect. The certification exam was much less intimidating thanks to their excellent prep materials. So, I highly recommend their services for anyone preparing for this certification exam.
Achieving my Microsoft certification was a seamless experience. The detailed study guide and practice questions ensured I was fully prepared for 70-744. The customer support was responsive and helpful throughout my journey. Highly recommend their services for anyone preparing for their certification test.
I couldn't be happier with my certification results! The study materials were comprehensive and easy to understand, making my preparation for the 70-744 stress-free. Using these resources, I was able to pass my exam on the first attempt. They are a must-have for anyone serious about advancing their career.
The practice exams were incredibly helpful in familiarizing me with the actual test format. I felt confident and well-prepared going into my 70-744 certification exam. The support and guidance provided were top-notch. I couldn't have obtained my Microsoft certification without these amazing tools!
The materials provided for the 70-744 were comprehensive and very well-structured. The practice tests were particularly useful in building my confidence and understanding the exam format. After using these materials, I felt well-prepared and was able to solve all the questions on the final test with ease. Passing the certification exam was a huge relief! I feel much more competent in my role. Thank you!
The certification prep was excellent. The content was up-to-date and aligned perfectly with the exam requirements. I appreciated the clear explanations and real-world examples that made complex topics easier to grasp. I passed 70-744 successfully. It was a game-changer for my career in IT!

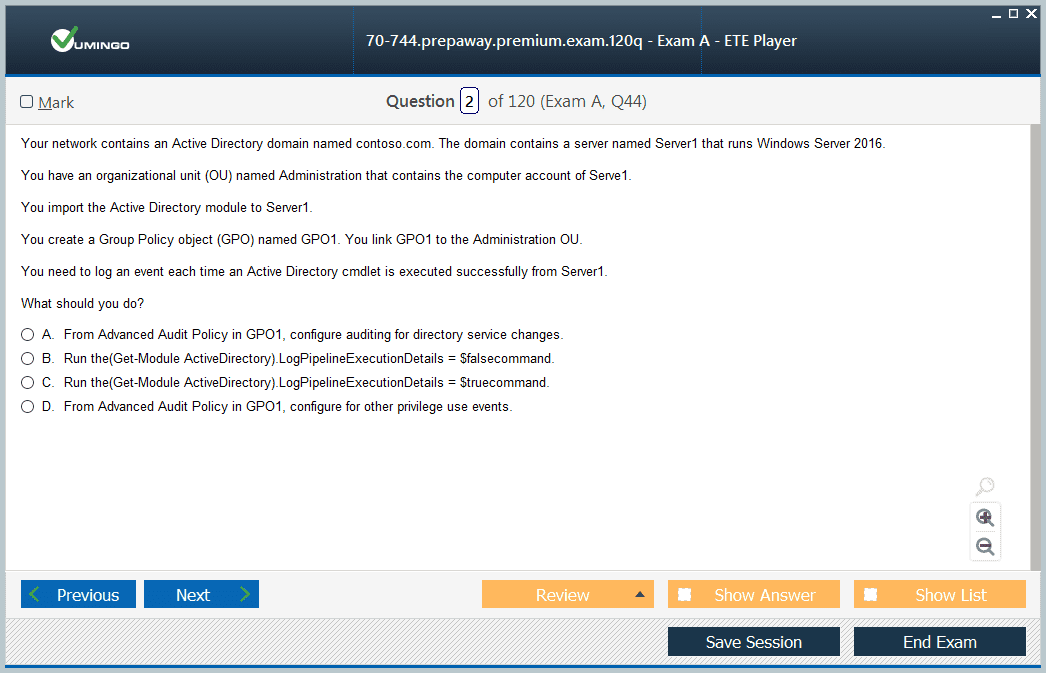
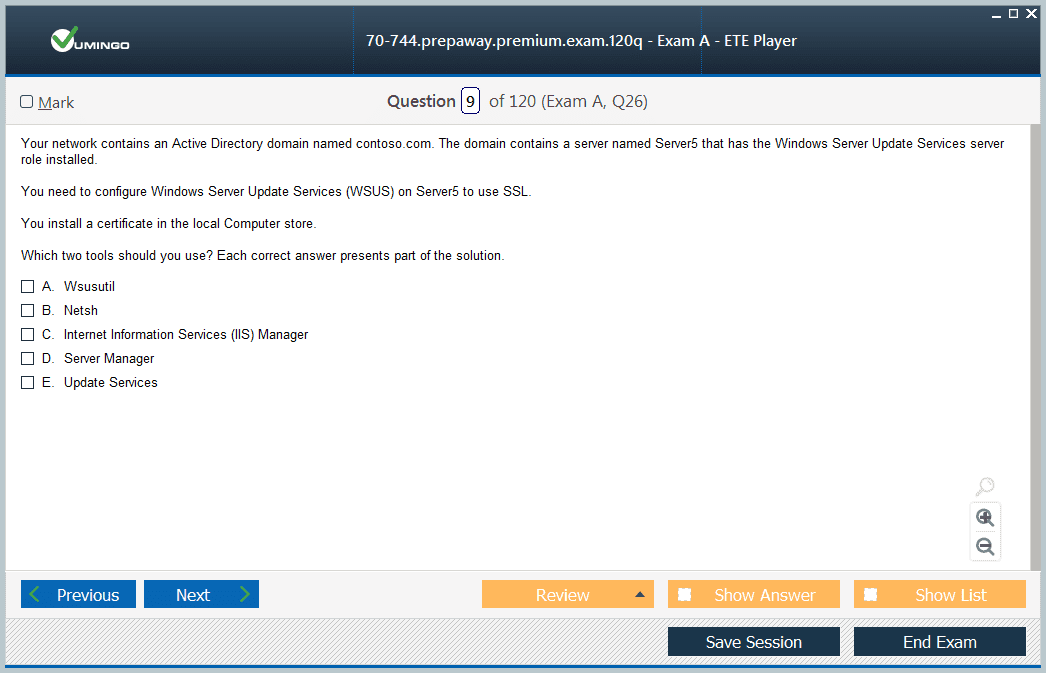
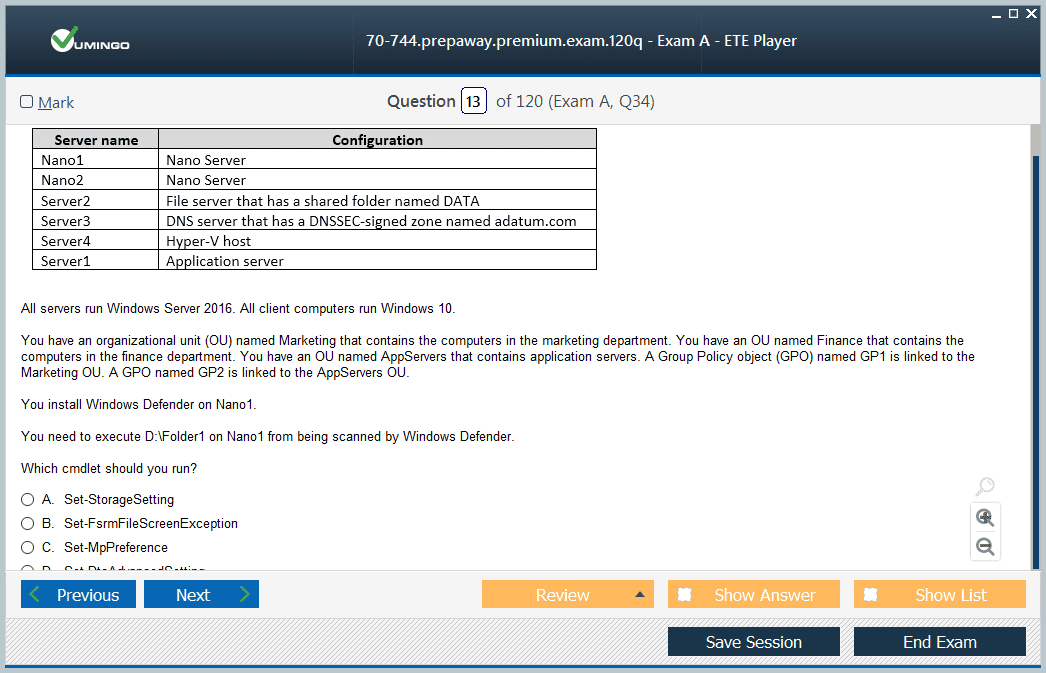
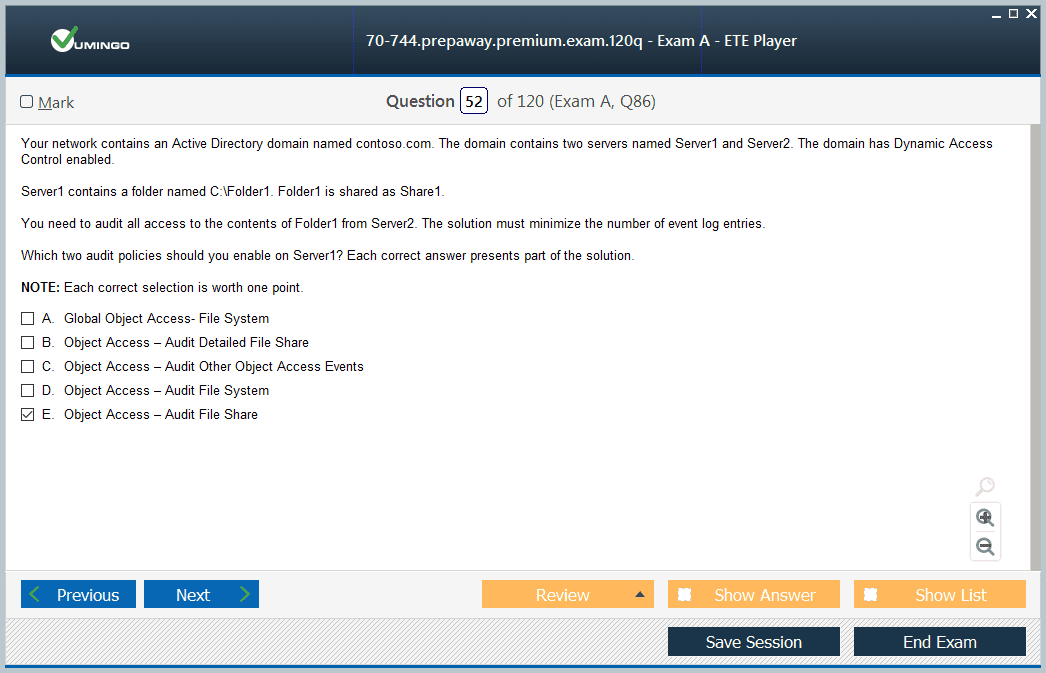




I start learning from this and I am courious how valid this dumps are.
I plan go to exam in next month.
I passed exam using premium dumps - only 4 new question in exam.
Choosing premium is good choice for pass.