- Home
- Microsoft Certifications
- AZ-303 Microsoft Azure Architect Technologies Dumps
Pass Microsoft Azure Architect AZ-303 Exam in First Attempt Guaranteed!
Get 100% Latest Exam Questions, Accurate & Verified Answers to Pass the Actual Exam!
30 Days Free Updates, Instant Download!


AZ-303 Premium Bundle
- Premium File 213 Questions & Answers. Last update: Feb 04, 2026
- Training Course 93 Video Lectures
- Study Guide 926 Pages
Last Week Results!

Includes question types found on the actual exam such as drag and drop, simulation, type-in and fill-in-the-blank.

Based on real-life scenarios similar to those encountered in the exam, allowing you to learn by working with real equipment.

Developed by IT experts who have passed the exam in the past. Covers in-depth knowledge required for exam preparation.
All Microsoft Azure Architect AZ-303 certification exam dumps, study guide, training courses are Prepared by industry experts. PrepAway's ETE files povide the AZ-303 Microsoft Azure Architect Technologies practice test questions and answers & exam dumps, study guide and training courses help you study and pass hassle-free!
AZ-303 Microsoft Azure Architect Technologies Exam Preparation: Complete Professional Certification Guide
The Azure ecosystem encompasses diverse professional roles requiring distinct skill sets and certifications, with data engineering and data science representing two critical but fundamentally different career paths. Data engineers focus on building robust data pipelines, managing data infrastructure, and ensuring data quality and availability across enterprise systems. They work extensively with Azure Data Factory, Azure Synapse Analytics, and Azure Databricks to create scalable data architectures. Data scientists, conversely, leverage statistical analysis, machine learning algorithms, and predictive modeling to extract actionable insights from processed data. Understanding these role distinctions helps aspiring Azure professionals choose appropriate certification pathways aligned with their career aspirations and technical interests.
Azure architects preparing for the AZ-303 examination must comprehend how data engineering and data science roles integrate within broader cloud architecture frameworks. Architects design infrastructure supporting both disciplines, ensuring data engineers have appropriate tools for ETL processes while data scientists access necessary computational resources for model training. Professionals exploring Azure data roles comprehensively gain clarity on career trajectory options. The AZ-303 certification validates architectural expertise encompassing compute, storage, networking, and security domains, providing foundational knowledge applicable across various Azure specializations. Successful Azure architects understand how different technical roles collaborate within cloud environments, enabling them to design holistic solutions meeting diverse organizational requirements.
Professional Career Advancement Through Azure Certification Pathways
Microsoft Azure certifications offer structured pathways for IT professionals seeking career advancement in cloud computing. The certification framework progresses from fundamental to expert levels, allowing professionals to demonstrate increasing expertise systematically. Entry-level certifications like Azure Fundamentals establish cloud computing basics, while role-based certifications validate specialized skills in administration, development, or architecture. The AZ-303 examination represents an advanced certification requiring comprehensive knowledge of Azure services, architectural patterns, and best practices. Professionals earning Azure architect certifications position themselves for senior technical roles, solution architecture positions, and cloud consulting opportunities.
Career advancement through Azure certifications extends beyond technical knowledge validation to include salary improvements, job mobility, and professional credibility. Employers increasingly prioritize certified professionals when staffing cloud initiatives, recognizing certifications as objective competency indicators. Professionals considering Azure career elevation opportunities understand certification strategic value. The AZ-303 certification demonstrates capability to design and implement solutions running on Microsoft Azure, covering compute, network, storage, and security aspects. This credential opens doors to enterprise architecture roles, cloud migration projects, and strategic technology planning positions. Continuous certification maintenance through renewal requirements ensures professionals maintain current knowledge as Azure services evolve.
AZ-400 Certification Investment and Value Proposition Analysis
The AZ-400 DevOps Engineer Expert certification represents significant investment in professional development, requiring examination fees, study materials, and preparation time. Understanding the complete cost structure helps candidates budget appropriately and assess return on investment. Direct costs include examination fees, practice tests, training courses, and potentially bootcamps or instructor-led training. Indirect costs encompass study time opportunity costs, lab environment expenses, and potential examination retake fees. However, certified DevOps professionals typically command premium salaries justifying the initial investment through enhanced earning potential and expanded career opportunities.
Financial considerations for certification pursuit extend beyond monetary costs to include time commitment and preparation intensity. DevOps certification preparation requires mastering Azure DevOps Services, CI/CD pipelines, infrastructure as code, and monitoring strategies. Candidates researching AZ-400 certification expenses thoroughly make informed decisions about certification timing. The AZ-303 certification similarly requires substantial preparation investment, though it focuses on architectural design rather than DevOps practices. Both certifications provide long-term career value exceeding initial costs, particularly as organizations accelerate cloud adoption. Strategic certification planning considers current role requirements, career goals, and organizational needs when prioritizing certification pursuits.
DevOps Practices Implementation on Azure Platform Infrastructure
DevOps methodologies fundamentally transform how organizations develop, deploy, and maintain software systems. Azure provides comprehensive tooling supporting DevOps practices through Azure DevOps Services, GitHub integration, and Azure Pipeline capabilities. Successful DevOps implementation requires cultural shifts emphasizing collaboration, automation, and continuous improvement alongside technical tool adoption. Azure architects must design infrastructure supporting DevOps workflows, including automated deployment pipelines, infrastructure as code implementations, and comprehensive monitoring solutions. The integration of development and operations practices reduces deployment cycles, improves software quality, and enhances organizational agility.
Azure DevOps practices encompass continuous integration, continuous deployment, infrastructure automation, and feedback loops enabling rapid iteration. Organizations implementing DevOps on Azure leverage services like Azure Repos for source control, Azure Pipelines for CI/CD, Azure Boards for project management, and Azure Test Plans for quality assurance. Professionals examining AZ-400 DevOps elevation strategies understand comprehensive DevOps implementation. Azure architects designing DevOps-enabled environments ensure infrastructure supports automated testing, staged deployments, rollback capabilities, and environment consistency. Container technologies including Azure Kubernetes Service facilitate microservices architectures complementing DevOps practices. Monitoring and logging implementations provide visibility necessary for continuous improvement and rapid issue resolution.
Dynamics 365 Business Consultant Career Preparation Framework
Microsoft Dynamics 365 certifications validate expertise in business application implementation, configuration, and optimization. Dynamics 365 consultants bridge business requirements and technical implementation, requiring both functional business knowledge and technical configuration skills. The MB-800 certification pathway prepares professionals for consultant roles focusing on business application deployment, user training, and process optimization. Dynamics 365 encompasses various modules including Sales, Customer Service, Finance, and Supply Chain Management, requiring consultants to develop specialized expertise in relevant business domains.
Business application consulting requires understanding organizational processes, change management principles, and technical configuration capabilities. Successful consultants translate business requirements into system configurations, customize applications meeting unique organizational needs, and train users ensuring effective system adoption. Candidates exploring MB-800 consultant preparation approaches understand business application career pathways. While AZ-303 focuses on infrastructure architecture, understanding business applications like Dynamics 365 helps architects design appropriate supporting infrastructure. Integration between Dynamics 365 and Azure services creates comprehensive business solutions leveraging both platforms' strengths. Azure architects supporting Dynamics 365 deployments ensure adequate compute resources, appropriate networking configurations, and robust security implementations.
Data Science Certification Pathway Navigation Strategies
Azure data science certifications validate machine learning expertise, statistical analysis capabilities, and AI solution implementation skills. The DP-100 certification focuses on designing and implementing data science solutions on Azure, covering machine learning model development, deployment, and management. Data scientists leverage Azure Machine Learning, Azure Databricks, and Azure Cognitive Services to build intelligent applications. Successful data scientists combine mathematical foundations, programming proficiency, and domain knowledge to solve complex business problems through data-driven approaches.
Machine learning implementation on Azure requires understanding algorithm selection, feature engineering, model training, and deployment strategies. Data scientists work with large datasets, train predictive models, and deploy solutions providing business value through automation or enhanced decision-making. Professionals pursuing DP-100 certification successfully develop comprehensive data science competencies. Azure architects supporting data science initiatives design infrastructure providing necessary computational resources, managing large-scale data storage, and ensuring secure access to sensitive datasets. Integration between data engineering pipelines and data science workflows creates end-to-end analytical solutions. Understanding data science requirements helps architects design appropriate Azure environments supporting machine learning workloads efficiently.
Azure Fundamentals Mastery for Cloud Computing Foundations
The AZ-900 Azure Fundamentals certification establishes foundational cloud computing knowledge essential for all Azure professionals. This entry-level certification covers cloud concepts, Azure services, security, privacy, compliance, and pricing models. Fundamental understanding of cloud computing paradigms including infrastructure as a service, platform as a service, and software as a service provides context for advanced certifications. The AZ-900 certification serves as stepping stone toward role-based certifications like AZ-303, ensuring candidates possess necessary prerequisite knowledge.
Cloud fundamentals encompass understanding virtualization, elasticity, scalability, and pay-as-you-go consumption models distinguishing cloud computing from traditional infrastructure. Azure fundamental services include compute options like virtual machines and app services, storage solutions including blob and file storage, and networking components like virtual networks and load balancers. Candidates achieving AZ-900 certification proficiency establish solid cloud foundations. For AZ-303 candidates, fundamental concepts provide essential context for architectural decisions. Understanding service categories, pricing models, and service level agreements informs architecture design ensuring solutions meet business requirements while managing costs effectively. Fundamental knowledge prevents common misconceptions and supports informed decision-making throughout architectural design processes.
Cybersecurity Enhancement Through MS-500 Security Administration
The MS-500 certification validates expertise in implementing and managing security and compliance solutions within Microsoft 365 environments. Security administrators protect organizational data, manage identity and access, implement threat protection, and ensure regulatory compliance. Microsoft 365 security spans identity management through Azure Active Directory, information protection through encryption and rights management, threat protection through Microsoft Defender, and compliance management through retention policies. Security administration requires understanding threat landscapes, security best practices, and compliance frameworks relevant to various industries.
Comprehensive security implementations protect against diverse threats including malware, phishing, data exfiltration, and unauthorized access. Security administrators configure multi-factor authentication, conditional access policies, and privileged identity management protecting organizational resources. Professionals advancing MS-500 cybersecurity proficiency develop essential security competencies. Azure architects incorporate security considerations throughout infrastructure design, implementing defense-in-depth strategies protecting resources at network, host, application, and data layers. Security group configurations, network security groups, application security groups, and Azure Firewall implementations create layered security architectures. Understanding security administration principles helps architects design secure Azure environments meeting organizational security requirements and regulatory compliance obligations.
Agentic AI Applications in Business Intelligence Analytics
Agentic artificial intelligence represents autonomous AI systems capable of independent decision-making and action-taking based on defined objectives and constraints. These advanced AI implementations transform business intelligence by automating complex analytical workflows, identifying patterns humans might overlook, and providing proactive recommendations. Agentic AI systems in business intelligence autonomously gather data, perform analyses, generate insights, and trigger actions based on findings. This automation enables organizations to respond rapidly to market changes, optimize operations continuously, and make data-driven decisions at unprecedented speed.
Business intelligence evolution through agentic AI creates opportunities for more sophisticated analytical capabilities. Traditional business intelligence requires manual report creation and human interpretation, while agentic systems automatically identify significant trends, anomalies, and opportunities. Organizations leveraging agentic AI business intelligence gain competitive analytical advantages. Azure architects designing AI-powered business intelligence solutions ensure infrastructure provides necessary computational resources, manages large datasets efficiently, and maintains security protecting sensitive business data. Integration between Azure Synapse Analytics for data warehousing, Azure Machine Learning for model training, and Power BI for visualization creates comprehensive analytical environments. Understanding agentic AI capabilities helps architects design infrastructure supporting advanced analytical workloads.
AI-Driven Data Interpretation Transformation Mechanisms
Artificial intelligence revolutionizes data interpretation by automating pattern recognition, identifying correlations, and generating insights from complex datasets. Traditional data analysis requires manual hypothesis formation and testing, while AI-driven approaches automatically identify significant patterns and relationships. Machine learning algorithms process vast datasets identifying trends invisible to human analysts. Natural language generation capabilities transform statistical findings into human-readable narratives, making complex analyses accessible to non-technical stakeholders. AI-driven interpretation accelerates decision-making by providing timely, accurate insights from organizational data.
Data interpretation automation through AI encompasses anomaly detection, predictive analytics, and prescriptive recommendations. Anomaly detection identifies unusual patterns suggesting problems or opportunities requiring attention. Predictive analytics forecast future trends based on historical patterns, enabling proactive planning. Prescriptive analytics recommend specific actions optimizing desired outcomes. Organizations implementing AI data interpretation solutions enhance analytical capabilities significantly. Azure architects supporting AI-driven interpretation design infrastructure providing necessary computational resources, implementing appropriate data storage solutions, and ensuring low-latency access to analytical results. Azure Cognitive Services offer pre-built AI capabilities for text analytics, image recognition, and language understanding, accelerating AI implementation without requiring extensive machine learning expertise.
Artificial Intelligence Classification and Application Taxonomy
Artificial intelligence encompasses diverse technologies and approaches categorized by capability levels and application domains. Narrow AI or weak AI performs specific tasks within defined domains, representing most current AI implementations. General AI or strong AI would match human cognitive abilities across all domains, remaining theoretical rather than realized. Superintelligent AI would exceed human intelligence across all domains, representing speculative future possibility rather than current reality. Understanding AI classification helps organizations set realistic expectations about current AI capabilities and limitations.
AI technologies categorize by approach including rule-based systems, machine learning, deep learning, and neural networks. Rule-based systems follow explicitly programmed logic, while machine learning systems learn patterns from data. Deep learning uses multi-layered neural networks identifying complex patterns in large datasets. Organizations exploring AI type spectrum comprehensively understand technology options. Azure provides diverse AI services supporting various implementation approaches. Azure Cognitive Services offer pre-built AI capabilities, Azure Machine Learning enables custom model development, and Azure Bot Service facilitates conversational AI implementations. Architects selecting appropriate AI technologies for specific use cases ensure solutions effectively address business requirements while managing implementation complexity and costs.
AI Learning Complexity and Certification Pathway Selection
Artificial intelligence learning encompasses diverse knowledge areas including mathematics, programming, machine learning algorithms, and domain expertise. Mathematical foundations span linear algebra, calculus, probability, and statistics necessary for understanding algorithmic behavior. Programming skills in Python or R enable AI implementation, with proficiency in libraries like TensorFlow, PyTorch, or Scikit-learn. Machine learning algorithm understanding covers supervised learning, unsupervised learning, and reinforcement learning approaches. Domain expertise ensures AI applications address real business problems effectively.
AI learning complexity varies based on career goals and current knowledge foundations. Professionals with strong mathematical backgrounds may find theoretical concepts accessible while requiring programming skill development. Conversely, experienced programmers may grasp implementation quickly while requiring mathematical concept reinforcement. Candidates researching AI learning difficulty honestly make informed education decisions. Azure AI certifications like AI-900 and AI-102 provide structured learning pathways focusing on Azure-specific AI implementation rather than theoretical foundations exclusively. Microsoft Learn offers free training resources covering AI concepts, Azure AI services, and hands-on labs enabling practical experience. Strategic AI learning combines theoretical understanding with practical implementation experience, gradually building comprehensive AI competencies.
Reinforcement Learning Engineering Career Development Roadmap
Reinforcement learning represents machine learning paradigm where agents learn optimal behaviors through trial and error interactions with environments. Unlike supervised learning requiring labeled training data, reinforcement learning agents discover successful strategies through reward signals. Applications include robotics, game playing, autonomous vehicles, and resource optimization. Reinforcement learning engineers design agent architectures, define reward functions, implement training algorithms, and deploy learned policies. This specialized field requires strong mathematical foundations, programming expertise, and understanding of specific application domains.
Career pathways into reinforcement learning engineering typically require advanced education in computer science, mathematics, or related fields. Practical experience implementing reinforcement learning algorithms using frameworks like OpenAI Gym, TensorFlow, or PyTorch proves essential. Engineers pursuing reinforcement learning careers methodically understand specialization requirements. While Azure doesn't offer specific reinforcement learning certifications, the platform supports reinforcement learning implementation through Azure Machine Learning and Azure Databricks. Azure architects supporting reinforcement learning workloads ensure infrastructure provides necessary computational resources, particularly GPU capabilities for intensive training processes. Understanding reinforcement learning requirements helps architects design appropriate Azure environments supporting this computationally demanding machine learning approach.
Computer Vision Specialist Career Progression Framework
Computer vision enables machines to interpret and understand visual information from images and videos. Applications span facial recognition, object detection, image classification, autonomous vehicles, and medical imaging analysis. Computer vision specialists develop and deploy models performing visual recognition tasks, requiring expertise in image processing, deep learning, and convolutional neural networks. Specialization areas include object detection, semantic segmentation, image generation, and video analysis. Career success requires combining theoretical knowledge with practical implementation experience across diverse application domains.
Professional development pathways for computer vision specialists emphasize deep learning frameworks, particularly convolutional neural network architectures. Hands-on experience with datasets like ImageNet, COCO, or domain-specific collections provides essential practical exposure. Professionals becoming computer vision specialists successfully develop specialized AI expertise. Azure Computer Vision Service offers pre-built capabilities for image analysis, optical character recognition, and face detection. Azure Custom Vision enables training custom image classification models without extensive machine learning expertise. Architects supporting computer vision applications ensure adequate storage for image datasets, sufficient computational resources for model training, and optimized inference pipelines for production deployments.
Professional Qualification Skills Acquisition Strategies
Professional qualification in IT fields requires systematic skill acquisition across technical, business, and soft skill domains. Technical skills encompass specific technologies, programming languages, and tools relevant to chosen career paths. Business skills include understanding organizational processes, financial principles, and strategic thinking enabling technology professionals to align technical solutions with business objectives. Soft skills like communication, collaboration, and problem-solving prove essential for career advancement beyond purely technical roles. Comprehensive skill development creates well-rounded professionals capable of contributing across diverse organizational contexts.
Skill acquisition strategies combine formal education, professional certifications, hands-on experience, and continuous learning. Formal education provides theoretical foundations and structured learning pathways. Certifications validate specific competencies and demonstrate commitment to professional development. Practical experience through projects, labs, and real-world implementations reinforces theoretical knowledge. Professionals exploring qualification skill requirements understand development pathways. Azure architects require diverse skills including infrastructure design, security implementation, networking configuration, and cost optimization. AZ-303 preparation encompasses these areas systematically, ensuring candidates develop comprehensive architectural competencies. Continuous learning through Microsoft Learn, community engagement, and hands-on practice ensures professionals maintain current knowledge as Azure services evolve.
CISSP Domain Four Network Security Fundamentals
The CISSP Domain 4 addresses communication and network security, covering networking fundamentals, network protocols, secure network architecture, and network security controls. Network security protects data during transmission, prevents unauthorized access, and ensures communication confidentiality, integrity, and availability. Core concepts include network topologies, TCP/IP protocol suite, OSI model, routing and switching, and wireless network security. Security professionals must understand both networking fundamentals and security controls applicable to network environments.
Network security implementations encompass firewalls, intrusion detection systems, virtual private networks, and network segmentation. Defense-in-depth strategies implement multiple security layers protecting against various attack vectors. Security professionals mastering CISSP Domain 4 thoroughly develop comprehensive network security expertise. Azure network security implements through network security groups, application security groups, Azure Firewall, and Azure DDoS Protection. Network segmentation using virtual networks and subnets isolates workloads, limiting lateral movement potential during security incidents. Azure architects implementing network security ensure appropriate controls protect organizational resources while enabling necessary connectivity for business operations.
CISSP Domain Three Security Architecture Principles
CISSP Domain 3 covers security architecture and engineering, emphasizing secure design principles, security models, and security architecture frameworks. Security architecture establishes organizational security foundations, defining security requirements, controls, and processes protecting information assets. Core principles include defense-in-depth, least privilege, separation of duties, and fail-safe defaults. Security models like Bell-LaPadula for confidentiality and Biba for integrity provide theoretical frameworks guiding security implementations.
Security engineering encompasses cryptography, physical security, and secure system design throughout lifecycle phases. Cryptographic implementations protect data confidentiality, ensure integrity, and enable authentication. Physical security controls protect facilities, equipment, and infrastructure supporting information systems. Candidates studying CISSP Domain 3 comprehensively develop security architecture expertise. Azure security architecture implements through Azure Security Center for security posture management, Azure Policy for governance enforcement, and Azure Blueprints for repeatable deployments. Encryption implementations protect data at rest using Azure Storage Service Encryption and data in transit using TLS. Azure architects designing secure solutions apply security architecture principles ensuring comprehensive protection meeting organizational requirements.
Security Certification Comparison and Selection Guidance
Security certifications validate diverse expertise levels and specialization areas, requiring careful selection aligned with career goals and current experience. CISSP represents broad security management certification requiring extensive experience and demonstrating comprehensive security knowledge across multiple domains. CCSP focuses specifically on cloud security, validating expertise in cloud architecture, governance, operations, and legal considerations. CEH emphasizes offensive security skills, validating penetration testing and ethical hacking capabilities. Each certification serves different career pathways and requires distinct knowledge foundations.
Certification selection considers current role requirements, career aspirations, and organizational needs. Security managers benefit from CISSP's broad coverage and management focus. Cloud security specialists find CCSP directly applicable to cloud-specific challenges. Penetration testers require CEH's offensive security focus. Professionals comparing CISSP CCSP CEH options make strategic certification decisions. Azure architects benefit from understanding security certifications contextualizing security requirements within cloud architectures. While AZ-303 covers Azure security services, security certifications provide deeper security expertise applicable across platforms. Combined Azure architecture and security certifications create powerful credential combinations demonstrating comprehensive cloud security design capabilities.
Backward Elimination Regression Feature Selection Method
Backward elimination represents feature selection technique in machine learning removing least significant variables iteratively until model contains only statistically significant predictors. The process begins with all available features, then systematically removes variables with highest p-values exceeding significance thresholds. After each removal, model retraining and statistical evaluation determine if additional features require elimination. This iterative process continues until all remaining features demonstrate statistical significance below defined thresholds. Backward elimination helps prevent overfitting by reducing model complexity while maintaining predictive accuracy.
Feature selection proves essential for building interpretable, efficient machine learning models. Excessive features increase computational requirements, complicate model interpretation, and risk overfitting to training data. Backward elimination systematically identifies and removes features contributing minimally to predictions. Data scientists understanding backward elimination comprehensively implement effective feature selection. Azure Machine Learning supports feature selection during model training through automated machine learning capabilities. Architects supporting machine learning workloads ensure adequate computational resources for iterative model training required by feature selection processes. Understanding machine learning concepts helps architects design appropriate Azure environments supporting data science activities effectively.
Simple Linear Regression Machine Learning Fundamentals
Simple linear regression models relationships between single independent variables and dependent variables using straight-line equations. This fundamental statistical technique predicts dependent variable values based on independent variable inputs by finding best-fit lines minimizing prediction errors. Linear regression applications include sales forecasting, risk assessment, trend analysis, and various prediction scenarios. Understanding linear regression provides foundations for more complex machine learning algorithms. Key concepts include slope, intercept, residuals, and goodness-of-fit measures like R-squared.
Regression analysis implementation requires training data containing paired observations of independent and dependent variables. Algorithm training identifies optimal slope and intercept values minimizing squared differences between predicted and actual values. Trained models predict new outcomes for previously unseen independent variable values. Professionals learning linear regression fundamentals develop essential machine learning foundations. Azure Machine Learning supports regression model development through designer interfaces and code-based approaches. Architects supporting machine learning initiatives ensure infrastructure provides necessary data access, computational resources, and deployment capabilities. Understanding basic machine learning concepts helps architects communicate effectively with data science teams and design appropriate supporting infrastructure.
Financial Services Professional Certification Pathways
Financial services certifications validate expertise in investment management, financial analysis, and wealth management practices. The Chartered Institute for Securities and Investment offers certifications covering securities operations, investment advice, and wealth management competencies. Financial professionals pursue certifications demonstrating knowledge of financial markets, investment products, regulatory requirements, and client relationship management. These credentials enhance professional credibility, meet regulatory requirements, and demonstrate commitment to ethical standards. Financial services certifications require rigorous examination preparation, continuing education, and adherence to professional codes of conduct.
While financial certifications differ fundamentally from IT credentials, understanding professional certification value transcends specific industries. Both domains recognize certifications as competency validation mechanisms benefiting career advancement. Professionals exploring CISI certification programs understand financial services credentialing. IT professionals can learn from financial services' mature certification frameworks emphasizing ethics, continuing education, and professional standards. Azure architects supporting financial services clients must understand industry regulatory requirements affecting cloud implementations. Compliance considerations including data residency, encryption requirements, and audit capabilities significantly influence Azure architecture designs for financial sector clients. Understanding client industry contexts enables architects to design solutions meeting both technical and regulatory requirements effectively.
Virtual Desktop Infrastructure and Application Delivery
Citrix certifications validate expertise in virtual desktop infrastructure, application virtualization, and digital workspace solutions. Citrix technologies enable organizations to deliver desktops and applications to users regardless of device or location. Virtual desktop infrastructure centralizes desktop management, improves security through data centralization, and enables flexible work arrangements. Application virtualization decouples applications from operating systems, simplifying deployment and management. Citrix professionals implement, configure, and optimize virtual desktop environments ensuring optimal user experiences while managing infrastructure efficiently.
Virtual desktop infrastructure implementations on Azure leverage Azure Virtual Desktop providing managed desktop virtualization services. Citrix Virtual Apps and Desktops deploy on Azure infrastructure combining Citrix management capabilities with Azure scalability. Professionals pursuing Citrix technology certifications develop desktop virtualization expertise. Azure architects designing virtual desktop solutions consider user experience requirements, network latency, storage performance, and licensing models. Integration with Azure Active Directory provides identity management, while Azure Files or Azure NetApp Files deliver user profile storage. Understanding virtual desktop requirements helps architects design Azure environments supporting remote workforce needs effectively. Network optimization through Azure Virtual WAN and ExpressRoute ensures acceptable user experiences for geographically distributed users.
Web Development and Digital Marketing Credentials
CIW certifications validate web development, design, and digital marketing competencies. Web development certifications cover HTML, CSS, JavaScript, and responsive design techniques. Web design certifications emphasize user experience, visual design principles, and accessibility standards. Digital marketing certifications address SEO, social media marketing, and web analytics. These credentials demonstrate proficiency in creating, designing, and promoting web presences supporting organizational objectives. Web professionals use CIW certifications differentiating themselves in competitive markets requiring demonstrated competency.
Modern web applications increasingly deploy on cloud platforms leveraging scalability, global reach, and managed services. Azure App Service provides platform-as-a-service for web application hosting supporting various frameworks and languages. Teams earning CIW web certifications demonstrate web expertise. Azure architects supporting web applications design solutions ensuring high availability, acceptable performance, and appropriate scaling. Azure CDN improves global content delivery performance, while Azure Front Door provides application acceleration and security. Integration with Azure DevOps enables continuous deployment updating applications rapidly. Understanding web application requirements helps architects design Azure environments supporting diverse web workloads from simple websites to complex web applications.
Big Data Processing and Analytics Platform Expertise
Cloudera certifications validate big data platform administration, development, and data science competencies. Cloudera platforms process and analyze massive datasets using distributed computing frameworks. Big data administrators manage cluster infrastructure ensuring reliability, performance, and security. Big data developers build data processing applications using frameworks like Apache Spark, Apache Hive, and Apache Kafka. Data scientists leverage big data platforms for advanced analytics and machine learning on large-scale datasets.
Azure provides multiple big data services complementing or replacing traditional on-premises big data platforms. Azure Synapse Analytics offers unified analytics platform combining big data and data warehousing. Azure Databricks provides managed Apache Spark environment for big data processing and machine learning. Professionals holding Cloudera platform certifications demonstrate big data expertise. Azure architects designing big data solutions select appropriate services based on workload characteristics, data volumes, and analytical requirements. Azure Data Lake Storage provides scalable storage for big data analytics, while Azure HDInsight offers managed Hadoop, Spark, and Kafka clusters. Understanding big data technology landscape helps architects design solutions meeting organizational analytical needs while managing costs through appropriate service selection.
California Basic Educational Skills Test Preparation
CBEST assesses basic reading, mathematics, and writing skills required for teaching credentials in California. This examination validates foundational academic competencies necessary for effective teaching. Reading sections evaluate comprehension and analysis of written materials. Mathematics sections cover arithmetic, statistics, algebra, and measurement. Writing sections assess composition abilities through essay responses. Prospective teachers prepare through practice tests, study guides, and review courses ensuring readiness for credential requirements.
While CBEST differs completely from IT certifications, examination preparation principles apply across domains. Effective preparation requires understanding examination formats, identifying knowledge gaps, focused study, and practice testing. Candidates preparing for CBEST successfully develop test-taking strategies applicable broadly. AZ-303 preparation similarly benefits from understanding examination structure, comprehensive topic coverage, hands-on practice, and simulated testing. Both examinations require time management, question interpretation skills, and ability to demonstrate knowledge under testing conditions. Strategic preparation approaches combining content mastery with test-taking skill development improve success probability across examination types.
Neonatal Critical Care Nursing Certification Requirements
Neonatal critical care certifications validate specialized nursing competencies caring for critically ill newborns. These advanced certifications require extensive clinical experience, specialized knowledge, and examination success. Neonatal nurses provide complex care to premature infants and newborns with critical conditions requiring intensive monitoring and intervention. Certification demonstrates expertise in neonatal assessment, respiratory support, medication administration, and family-centered care. Continuing education requirements ensure certified professionals maintain current clinical knowledge.
Professional certification programs across healthcare and technology share common elements including rigorous examination requirements, experience prerequisites, and continuing education mandates. Examining neonatal critical care credentials illustrates healthcare certification frameworks. Though unrelated to Azure, understanding healthcare certifications provides perspective on professional credentialing importance across industries. Healthcare regulations requiring certified professionals parallel IT industry preferences for certified cloud professionals. Both fields recognize certifications as quality indicators ensuring practitioners possess essential competencies. Azure architects supporting healthcare clients must understand HIPAA compliance requirements affecting cloud implementations, ensuring patient data protection through appropriate security controls and audit capabilities.
Advanced Financial Analysis Professional Certification
CFA Level 2 certification represents intermediate progression in Chartered Financial Analyst program validating advanced investment analysis skills. This rigorous certification requires mastering equity valuation, fixed income analysis, derivatives, portfolio management, and financial reporting. CFA candidates demonstrate commitment to financial analysis profession through extensive study and examination success. Level 2 examinations emphasize application of analytical techniques to practical investment scenarios. The CFA designation represents gold standard in investment management profession worldwide.
Professional certification programs in finance and technology demonstrate similar progression patterns from foundational through advanced expertise levels. Candidates preparing CFA Level 2 examinations pursue financial analysis expertise. IT certification progressions like Azure Fundamentals through Azure Expert certifications mirror this structured advancement. Both fields recognize value in demonstrating progressive competency development. Azure architects supporting financial services understand regulatory environments, performance requirements, and security considerations critical for financial applications. Real-time trading systems require ultra-low latency, while risk analytics demand massive computational capacity. Understanding client industry needs enables architects to design appropriate Azure solutions meeting specific sector requirements.
Portfolio Management and Wealth Planning Certification
CFA Level 3 represents final examination in Chartered Financial Analyst program focusing on portfolio management and wealth planning. This advanced certification emphasizes applying investment knowledge to portfolio construction, management, and wealth planning contexts. Examinations test synthesis of knowledge across all CFA program areas applied to realistic portfolio management scenarios. Successful candidates demonstrate ability to develop investment policy statements, construct appropriate portfolios, and manage client relationships effectively. The CFA charter represents pinnacle achievement in investment management profession.
Certification program structures often feature progressive difficulty levels requiring mastery of prerequisite knowledge before advanced progression. Professionals completing CFA Level 3 successfully achieve premier financial credentials. Azure certification paths similarly progress from fundamental through expert levels, each building on previous knowledge. Understanding certification progression importance helps candidates plan development pathways systematically. Azure architects supporting wealth management firms design secure, compliant infrastructures protecting sensitive client financial data. High availability requirements ensure trading platforms remain accessible during market hours, while disaster recovery capabilities protect against data loss. Tailoring Azure architectures to specific industry needs demonstrates architect value beyond generic infrastructure knowledge.
College-Level Academic Credit Through Standardized Testing
CLEP examinations enable students earning college credit by demonstrating knowledge equivalent to college courses. These standardized tests cover various subjects allowing students accelerating degree completion by testing out of introductory courses. CLEP examinations provide cost-effective alternatives to traditional coursework, reducing time and expense required for degree completion. Students prepare through self-study, online resources, and practice examinations. Successful CLEP performance demonstrates subject matter competency satisfying degree requirements.
Examination-based competency demonstration extends beyond academic contexts to professional certification realms. Organizations researching CLEP testing benefits understand knowledge validation alternatives. IT certifications similarly validate competency through examinations rather than requiring formal coursework. Both approaches recognize that knowledge acquisition occurs through diverse pathways beyond traditional classroom settings. Self-directed learning, online resources, and practical experience can develop competencies validated through examinations. Azure certification preparation leverages multiple learning resources including Microsoft Learn, instructor-led training, hands-on labs, and practice examinations. Successful candidates synthesize learning from diverse sources demonstrating comprehensive competency regardless of specific learning pathway.
Cloud Infrastructure Development and Management Legacy Certification
The retired 70-532 certification validated developing Microsoft Azure solutions focusing on infrastructure deployment, implementation monitoring, and cloud service orchestration. This certification covered virtual machine deployment, storage implementation, cloud service configuration, and Azure Active Directory integration. Though retired and replaced by role-based certifications, concepts remain relevant for understanding Azure infrastructure development. Historical certifications provide context for current certification framework evolution reflecting Azure platform maturity and changing industry needs.
Legacy certifications inform current Azure architecture understanding by documenting platform evolution and capability expansion over time. Professionals reviewing 70-532 examination content understand Azure historical development. Current AZ-303 certification encompasses similar infrastructure topics with expanded scope reflecting additional services and capabilities unavailable during 70-532's active period. Learning from legacy certification content can supplement current preparation by providing alternative perspectives on foundational concepts. However, candidates must prioritize current examination objectives ensuring preparation aligns with current Azure platform capabilities and best practices rather than outdated approaches.
Azure Infrastructure Implementation Classic Certification
The retired 70-533 certification focused on implementing Microsoft Azure infrastructure solutions including virtual machines, networks, storage, and identity services. This certification validated practical implementation skills rather than theoretical knowledge. Topics covered virtual machine configuration, virtual network design, storage account implementation, and Azure Active Directory management. Though retired, implementation concepts remain foundational for current Azure infrastructure management. Understanding infrastructure implementation fundamentals provides practical context for architectural decision-making.
Infrastructure implementation skills form essential foundation for architecture roles, as effective architects must understand practical implementation considerations. Candidates examining 70-533 legacy content gain implementation perspective. AZ-303 examination assumes implementation knowledge, focusing instead on architectural design decisions, service selection, and solution optimization. Practical implementation experience through labs and real-world projects complements certification preparation, ensuring candidates can apply theoretical architectural knowledge to practical scenarios. Hands-on experience implementing Azure services builds intuition for service capabilities, limitations, and appropriate use cases informing architectural designs.
Architecting Azure Solutions Classic Expert Certification
The retired 70-535 certification validated architecting Microsoft Azure solutions, representing predecessor to current expert-level architecture certifications. This certification covered infrastructure strategy, data platform solutions, identity management, security implementation, and solution deployments. Though retired, architectural concepts remain highly relevant for current Azure architects. The certification framework evolution reflects Azure maturity, increased service complexity, and need for specialized role-based certifications replacing generalized classic certifications.
Architectural thinking transcends specific certification frameworks, as core principles of scalability, reliability, security, and cost optimization remain constant despite platform evolution. Professionals studying 70-535 architectural concepts understand architecture fundamentals. Current AZ-303 and AZ-304 certifications split architectural competencies across technologies and design respectively, providing more focused assessment than single comprehensive examination. Both approaches validate essential architectural capabilities including requirement analysis, service selection, security implementation, and cost management. Understanding architecture evolution helps candidates appreciate current certification framework rationale while learning from historical architectural approaches that remain relevant despite specific implementation details changing.
Windows Enterprise Desktop Deployment Classic Certification
The retired 70-695 certification covered deploying Windows desktops and enterprise applications focusing on imaging, deployment tools, and application delivery. Desktop deployment specialists ensure consistent, efficient operating system and application deployment across enterprise environments. Deployment technologies included Windows Deployment Services, Microsoft Deployment Toolkit, and System Center Configuration Manager. Though specific to Windows deployment, concepts of standardization, automation, and efficient large-scale deployment remain relevant across technology domains.
Modern cloud platforms emphasize automation, infrastructure as code, and repeatable deployment patterns mirroring desktop deployment principles. Candidates reviewing 70-695 deployment methods understand systematization importance. Azure Resource Manager templates, Azure Blueprints, and Azure DevOps pipelines implement similar concepts for cloud infrastructure deployment. Infrastructure as code principles enable repeatable, version-controlled deployments eliminating manual configuration inconsistencies. Azure architects design deployment processes ensuring consistency across environments, automating repetitive tasks, and maintaining configuration standards. Understanding deployment automation importance helps architects design solutions supporting efficient operational management.
Enterprise Desktop Management Classic Windows Certification
The retired 70-696 certification focused on administering and maintaining Windows enterprise desktop environments. Enterprise desktop management encompasses configuration management, software deployment, security policy enforcement, and troubleshooting. Desktop administrators ensure consistent configurations, manage software updates, implement security policies, and support end users. Though focused on traditional desktop environments, management principles apply to modern cloud-managed endpoints through solutions like Microsoft Endpoint Manager.
Desktop and device management increasingly leverages cloud-based management platforms providing unified management across diverse device types and locations. Professionals examining 70-696 management topics understand endpoint administration. Azure architects supporting remote workforce initiatives design solutions integrating Azure Virtual Desktop for desktop delivery, Azure Active Directory for identity management, and Microsoft Endpoint Manager for device management. Modern work environments require architectures supporting diverse device types, remote access, and consistent security policies regardless of user location. Understanding endpoint management requirements helps architects design comprehensive solutions supporting organizational productivity and security objectives.
Windows Client Configuration Classic Certification Analysis
The retired 70-697 certification covered configuring Windows devices focusing on installation, configuration, management, and maintenance. Client configuration specialists ensure Windows devices meet organizational requirements through appropriate configuration, security settings, and management approaches. Topics included deployment planning, update management, device security, and troubleshooting. Though Windows-specific, configuration management principles extend to diverse platforms requiring consistent, secure configurations.
Configuration management in cloud environments leverages desired state configuration, policy enforcement, and automated remediation ensuring infrastructure maintains compliant configurations. Candidates studying 70-697 configuration approaches understand standardization value. Azure Policy enables defining and enforcing organizational standards for Azure resources, ensuring deployments comply with security and governance requirements. Azure Automation desired state configuration maintains server configurations preventing configuration drift. Azure architects incorporate configuration management throughout designs ensuring resources maintain consistent, secure configurations meeting organizational requirements. Automated configuration management reduces manual errors, improves security posture, and simplifies compliance demonstration.
Windows Installation and Configuration Classic Assessment
The retired 70-698 certification focused on installing and configuring Windows operating systems covering installation procedures, upgrade paths, configuration options, and troubleshooting. Operating system installation and configuration fundamentals provide foundational knowledge for IT professionals supporting Windows environments. Topics included installation planning, storage configuration, networking setup, and peripheral management. Though specific certification retired, underlying concepts remain relevant for understanding Windows deployment and management.
Operating system knowledge supports cloud infrastructure understanding, as virtual machines require appropriate operating system configuration even when running on cloud platforms. Professionals reviewing 70-698 Windows fundamentals understand OS basics. Azure architects designing solutions involving Windows virtual machines must understand operating system licensing, configuration requirements, and management approaches. Azure Hybrid Benefit enables using existing Windows licenses in Azure reducing costs. Understanding operating system considerations informs virtual machine sizing decisions, licensing strategy, and management approaches. While cloud platforms abstract infrastructure complexity, fundamental operating system knowledge remains valuable for effective architecture and troubleshooting.
OEM System Deployment and Activation Technologies
The retired 70-735 certification covered OEM manufacturing and deployment for Windows focusing on system image creation, deployment, and activation. OEM manufacturers customize Windows installations, integrate drivers and applications, and ensure proper activation. System builders leverage Windows Assessment and Deployment Kit creating customized installation images. Though specialized for hardware manufacturers, deployment concepts apply more broadly to enterprise system deployment scenarios.
Image-based deployment approaches enable consistent, repeatable system provisioning whether for OEM manufacturing or enterprise deployments. Candidates examining 70-735 OEM deployment understand image management. Azure supports custom virtual machine image creation, allowing organizations maintaining standardized configurations deployable repeatedly. Azure Compute Gallery (formerly Shared Image Gallery) distributes custom images across regions ensuring consistent virtual machine deployments globally. Azure architects designing virtual machine solutions consider image management strategies, update processes, and configuration standardization. Understanding image-based deployment concepts helps architects design efficient provisioning processes supporting organizational needs.
Windows Server Installation and Configuration Fundamentals
The retired 70-740 certification validated installation, storage, and compute functionality with Windows Server focusing on core infrastructure services. Server administrators implement Windows Server roles, configure storage solutions, manage Hyper-V virtualization, and maintain server infrastructure. Topics included server installation, storage technologies, Hyper-V implementation, and container deployment. Though certification retired, Windows Server remains prevalent in enterprise environments requiring ongoing administration and management.
Windows Server workloads frequently migrate to Azure as organizations adopt cloud strategies. Azure virtual machines support Windows Server deployments, while Azure Hybrid Benefit reduces licensing costs for cloud migrations. Professionals understanding 70-740 server fundamentals possess valuable infrastructure knowledge. Azure architects supporting Windows Server workloads design solutions considering high availability, disaster recovery, backup strategies, and hybrid connectivity. Azure Site Recovery provides disaster recovery for virtual machines, while Azure Backup protects data. Integration between on-premises Windows Server environments and Azure through Azure Arc enables unified management across hybrid environments. Understanding Windows Server capabilities informs hybrid architecture designs supporting organizational cloud adoption journeys.
Windows Server Networking Services Implementation
The retired 70-741 certification focused on Windows Server networking capabilities including DNS, DHCP, IPAM, and remote access. Network services provide essential infrastructure supporting organizational communications and connectivity. DNS provides name resolution, DHCP automates IP address assignment, IPAM enables IP address management, and remote access technologies enable secure connectivity from external locations. Network services implementation requires understanding networking fundamentals, protocol behavior, and service integration.
Cloud networking builds on traditional networking concepts while introducing new paradigms like software-defined networking and virtual network isolation. Candidates reviewing 70-741 networking services understand network service fundamentals. Azure networking services include Azure DNS for domain hosting, Azure Virtual Network for isolated networks, Azure VPN Gateway for hybrid connectivity, and Azure Load Balancer for traffic distribution. Azure architects design networking solutions ensuring appropriate connectivity, security, and performance. Understanding traditional network services provides context for cloud networking concepts, helping architects translate on-premises networking patterns to cloud equivalents effectively.
Windows Server Identity and Security Services
The retired 70-742 certification covered identity services with Windows Server focusing on Active Directory Domain Services, Certificate Services, and Rights Management. Identity services provide authentication, authorization, and access control foundational to enterprise security. Active Directory enables centralized identity management, group policies enforce configurations, and certificate services support public key infrastructure. Though Windows Server-specific, identity management concepts apply universally across platforms requiring secure access control.
Cloud identity management leverages Azure Active Directory providing cloud-based identity services integrating with on-premises Active Directory when necessary. Professionals mastering 70-742 identity services understand identity fundamentals. Azure architects design hybrid identity solutions synchronizing on-premises identities to Azure Active Directory enabling single sign-on across cloud and on-premises applications. Azure AD Connect synchronizes directory information, while Azure AD Application Proxy provides secure remote access to on-premises applications. Federation services enable trust relationships between organizations supporting business-to-business collaboration. Understanding identity architecture proves essential for secure Azure solution design protecting organizational resources through appropriate authentication and authorization.
Windows Server Clustering and High Availability
The retired 70-743 certification focused on upgrading skills to Windows Server including clustering, storage technologies, and network controller. High availability implementations prevent single points of failure ensuring services remain accessible despite component failures. Clustering technologies enable automatic failover maintaining service availability. Storage Replica provides block-level replication supporting disaster recovery scenarios. Software-defined networking through network controller enables programmatic network management.
High availability concepts apply universally requiring redundancy, failover mechanisms, and automated recovery. Architects examining 70-743 high availability understand resilience patterns. Azure provides high availability through availability zones, availability sets, and load balancing. Availability zones represent physically separated datacenters within regions providing resilience against datacenter-level failures. Availability sets distribute virtual machines across fault domains and update domains protecting against hardware failures and planned maintenance. Azure Load Balancer distributes traffic across healthy instances automatically removing failed instances from rotation. Azure architects design high availability architectures ensuring solutions meet organizational uptime requirements through appropriate redundancy and failover mechanisms.
Windows Server Security and Compliance Implementation
The retired 70-744 certification covered securing Windows Server including threat protection, security features, and privileged access management. Server security encompasses defense-in-depth strategies implementing multiple security layers protecting against diverse threats. Security features include Windows Defender, BitLocker encryption, and Credential Guard protecting against malware, data theft, and credential attacks. Privileged access management limits administrative credential use preventing unauthorized privileged access. Securing server infrastructure protects organizational data and prevents security breaches.
Security principles transcend specific platforms requiring comprehensive approaches addressing multiple attack vectors. Candidates studying 70-744 security implementation learn server security. Azure Security Center provides unified security management across hybrid environments offering recommendations, threat detection, and compliance assessment. Azure Defender extends Security Center with advanced threat protection for compute, data, and application resources. Azure architects implement defense-in-depth security through network security groups, Azure Firewall, application security controls, and data encryption. Security by design principles ensure appropriate controls implemented throughout architecture rather than added retrospectively. Understanding server security fundamentals informs comprehensive cloud security architecture design.
SQL Server Database Administration Core Skills
The retired 70-761 certification covered querying data with Transact-SQL focusing on query writing, data manipulation, and database programming. Database administrators and developers write SQL queries extracting, transforming, and analyzing data from relational databases. Transact-SQL extends standard SQL with procedural programming constructs, error handling, and transaction control. Though specific to SQL Server, SQL skills apply broadly across relational database platforms. Understanding SQL enables effective data interaction regardless of specific database platform.
Data platform solutions on Azure include Azure SQL Database, Azure SQL Managed Instance, and SQL Server on Azure Virtual Machines. Database professionals with 70-761 SQL expertise possess valuable query skills. Azure architects designing data solutions select appropriate database services based on workload requirements, management preferences, and migration constraints. Azure SQL Database provides fully managed platform-as-a-service, while Azure SQL Managed Instance offers near-complete SQL Server compatibility supporting easier migrations. Understanding database capabilities and limitations informs architecture decisions ensuring applications receive appropriate data platform support. Performance optimization, security implementation, and high availability configuration represent key architectural considerations for database solutions.
SQL Server Development and Database Management
The retired 70-762 certification focused on developing SQL databases covering database design, implementation, optimization, and maintenance. Database developers design schemas, implement stored procedures, optimize queries, and ensure data integrity. Database design principles including normalization, indexing strategies, and query optimization impact application performance significantly. Though SQL Server-specific, database development concepts apply broadly across relational database platforms. Understanding database development enables creating efficient, maintainable data structures supporting application requirements.
Cloud database platforms abstract infrastructure management while requiring sound database design for optimal performance. Professionals with 70-762 development skills design effective databases. Azure SQL Database offers serverless and provisioned compute tiers supporting diverse workload requirements. Hyperscale tier provides massive scale supporting databases up to 100TB. Azure architects designing database solutions consider scalability requirements, performance expectations, and cost constraints selecting appropriate service tiers and configurations. Database monitoring through Azure Monitor and Query Performance Insight identifies performance issues enabling optimization. Understanding database development principles ensures architects design appropriate data architectures supporting application success.
SQL Server Administration and Infrastructure Management
The retired 70-764 certification covered administering SQL database infrastructure including installation, configuration, security, backup, and high availability. Database administrators ensure database infrastructure reliability, performance, security, and availability. Infrastructure management includes server configuration, storage management, security implementation, and disaster recovery planning. Though focused on SQL Server, database administration concepts apply across platforms requiring reliable, secure data management.
Managed database services reduce administrative burden by handling infrastructure management, patching, and backup automatically. DBAs exploring 70-764 administration topics understand infrastructure management. Azure SQL Database and Azure SQL Managed Instance provide managed database services eliminating many traditional DBA responsibilities. However, database security, performance tuning, and architecture remain critical even with managed services. Azure architects design database solutions balancing management simplicity against control requirements. High availability through active geo-replication, automated backups, and point-in-time restore provide data protection without complex configuration. Understanding administration concepts helps architects design operationally efficient database solutions.
SQL Server Business Intelligence Platform Development
The retired 70-765 certification focused on provisioning SQL databases covering database deployment, migration, implementation, and management. Database provisioning encompasses creating databases, configuring services, implementing security, and ensuring appropriate resource allocation. Migration from on-premises to cloud requires careful planning addressing data transfer, application compatibility, and cutover processes. Though SQL Server-specific, provisioning and migration concepts apply broadly to diverse data platform migrations.
Database migration to Azure involves assessing current workloads, selecting appropriate target services, and executing migrations minimizing downtime. Teams with 70-765 provisioning expertise understand deployment approaches. Azure Database Migration Service facilitates migrations from various database platforms to Azure with minimal downtime. Azure architects design migration strategies considering data volumes, application dependencies, cutover timing, and rollback procedures. Hybrid configurations using Azure Arc enable gradual migrations allowing applications accessing databases regardless of location during transition periods. Understanding provisioning and migration complexities ensures architects design feasible transition strategies supporting organizational cloud adoption.
Data Warehousing and ETL Implementation Skills
The retired 70-767 certification covered implementing SQL data warehouse focusing on data warehouse design, ETL implementation, and data quality. Data warehouses consolidate organizational data from multiple sources supporting analytical and reporting needs. Extract, transform, load processes move data from source systems to warehouses transforming data into consistent formats. Data quality implementation ensures accurate, complete data supporting reliable analytics. Though focused on SQL Server technologies, data warehousing concepts apply broadly to analytical data platforms.
Modern analytical platforms on Azure include Azure Synapse Analytics providing integrated data warehousing and big data analytics. Professionals understanding 70-767 data warehousing possess analytical platform expertise. Azure Synapse combines SQL-based data warehousing with Spark-based big data processing enabling diverse analytical workloads within unified platforms. Azure Data Factory provides cloud-based ETL orchestration moving and transforming data from multiple sources. Azure architects designing analytical solutions consider data volumes, query patterns, and user concurrency selecting appropriate service configurations. Understanding data warehousing fundamentals ensures architects design analytical architectures supporting organizational business intelligence requirements effectively.
Linux System Administration Certification Progression
The LPIC-1 certification validates Linux system administration skills covering system architecture, installation, package management, and command line. Linux administrators manage Linux servers ensuring reliability, security, and performance. Command line proficiency enables efficient system management and automation. Package management ensures software installation, updates, and dependency resolution. Though Linux-specific, system administration concepts apply across operating systems requiring similar management approaches.
Linux workloads frequently deploy on Azure through virtual machines or containerized applications. Azure supports various Linux distributions including Ubuntu, Red Hat, SUSE, and others. Professionals with Linux administration certification manage Linux-based Azure resources. Azure architects supporting Linux workloads understand distribution selection, licensing implications, and configuration requirements. Linux virtual machines integrate with Azure services including Azure Monitor for logging, Azure Backup for protection, and Azure Security Center for security management. Container technologies like Azure Kubernetes Service predominantly use Linux enabling containerized application deployment. Understanding Linux fundamentals helps architects design solutions supporting diverse operating system requirements.
E-Commerce Platform Development and Certification
Magento certification validates e-commerce development expertise covering platform architecture, customization, and extension development. E-commerce platforms enable online retail operations including product catalogs, shopping carts, payment processing, and order management. Magento developers customize platforms meeting specific business requirements through theme development, extension creation, and API integration. E-commerce platforms require high performance, security, and reliability supporting business-critical sales operations.
E-commerce platforms increasingly deploy on cloud infrastructure leveraging scalability, global reach, and reliability. Organizations implementing Magento e-commerce solutions require robust infrastructure. Azure provides services supporting e-commerce including Azure App Service for application hosting, Azure CDN for content delivery, and Azure SQL Database for data storage. Azure architects design e-commerce solutions ensuring performance during traffic spikes, security protecting customer data, and compliance with payment card industry standards. Global deployments using Azure Traffic Manager and multi-region deployments provide geographic performance optimization. Understanding e-commerce requirements helps architects design solutions supporting online retail operations effectively.
Digital Literacy and Computer Fundamentals Assessment
Microsoft Technology Literacy certification validates basic computer skills including hardware fundamentals, software applications, networking concepts, and digital citizenship. Digital literacy represents foundational competency for modern workforce participation. Understanding computer basics enables effective technology tool utilization. Though fundamental, these skills provide necessary foundations for advanced technical learning. Digital literacy certifications demonstrate basic competency to employers and educational institutions.
While basic compared to advanced cloud certifications, digital literacy represents an essential starting point for technology careers. Candidates pursuing technology literacy certification establish foundational knowledge. Progressive learning pathways lead from fundamental literacy through specialized certifications like AZ-303. Understanding certification hierarchies helps professionals plan development systematically. Azure fundamentals certification similarly establishes cloud basics before progressing to advanced certifications. Both fundamental and advanced certifications serve important roles validating appropriate expertise levels. Strategic professional development includes both depth in specialized areas and breadth across complementary domains ensuring well-rounded technical capabilities.
Conclusion
The AZ-303 Microsoft Azure Architect Technologies certification represents a significant milestone in cloud architecture professional development, validating comprehensive expertise across Azure compute, storage, networking, and security domains. Throughout this examination preparation guide, we have explored the multifaceted knowledge requirements spanning infrastructure design, service selection, security implementation, cost optimization, and operational excellence necessary for successful Azure architects. The certification preparation journey encompasses not only technical knowledge acquisition but also understanding architectural patterns, best practices, and real-world implementation considerations that distinguish effective architects from those with merely theoretical knowledge. Successful candidates develop holistic perspectives integrating diverse Azure services into cohesive solutions addressing complex business requirements while maintaining security, reliability, and cost-effectiveness.
Professional development pathways leading to and beyond AZ-303 certification require strategic planning considering prerequisite knowledge, complementary skills, and career advancement objectives. Foundational certifications establish cloud computing basics, while specialized certifications develop expertise in specific technology domains or job roles. The Microsoft certification framework provides clear progression pathways from fundamental through expert levels enabling systematic skill development. Architects benefit from understanding adjacent technology areas including data platforms, AI and machine learning, DevOps practices, and security to design comprehensive solutions leveraging diverse Azure capabilities. Continuous learning through Microsoft Learn, hands-on practice, and real-world implementation experience ensures professionals maintain current knowledge as Azure services evolve and expand.
Certification preparation strategies emphasizing comprehensive topic coverage, hands-on laboratory practice, and simulated examination experience maximize success probability while developing practical skills applicable beyond examination contexts. Official Microsoft documentation provides authoritative information about Azure services and capabilities forming essential study resources. Hands-on experience implementing Azure solutions through laboratories and personal projects reinforces theoretical knowledge developing practical implementation skills. Practice examinations identify knowledge gaps requiring additional study while familiarizing candidates with examination formats, question types, and time management requirements. Study groups and online communities provide peer support, knowledge sharing, and diverse perspectives enriching learning experiences beyond individual study efforts.
The Azure architecture profession demands continuous adaptation to rapidly evolving cloud technologies, emerging service capabilities, and changing best practices. Architects must balance deep technical expertise with broad business understanding aligning technical solutions with organizational objectives. Effective architects communicate clearly with both technical teams and business stakeholders translating complex technical concepts into understandable business terms. Architectural decisions consider multiple factors including functional requirements, performance expectations, security mandates, compliance obligations, cost constraints, and operational capabilities. Successful architects develop systematic decision-making frameworks evaluating alternatives objectively rather than pursuing preferred technologies regardless of suitability.
Career opportunities for certified Azure architects span diverse industries and organization types from startups to global enterprises. Cloud architecture expertise remains in high demand as organizations continue migrating workloads to cloud platforms and developing cloud-native applications. Azure architects work as solution architects designing specific application solutions, enterprise architects planning organization-wide technology strategies, or cloud architects specializing in cloud platform implementations. Consulting opportunities enable architects working across multiple client organizations gaining exposure to diverse industries, challenges, and architectural patterns. Internal roles within single organizations provide deep domain expertise and long-term architectural vision implementation.
The investment required for AZ-303 certification including examination fees, study materials, and preparation time delivers substantial career returns through expanded opportunities, increased compensation, and professional credibility. Certification preparation develops practical skills immediately applicable to current roles even before examination success. The structured learning process ensures comprehensive coverage of Azure capabilities potentially revealing services and features previously unknown. Certification achievement demonstrates professional commitment and validates expertise to employers, clients, and peers. Maintaining certification currency through continuing education requirements ensures architects remain knowledgeable about platform evolution and emerging capabilities.
Beyond immediate certification achievement, successful Azure architects embrace lifelong learning attitudes recognizing that technology evolution demands continuous skill development. Emerging technologies including artificial intelligence, machine learning, internet of things, and edge computing create new architectural challenges and opportunities. Security threats continuously evolve requiring architects staying informed about current attack vectors and defensive strategies. Business requirements change necessitating architectural evolution supporting organizational transformation. Professional communities including user groups, conferences, and online forums provide knowledge sharing opportunities, networking connections, and exposure to innovative approaches adopted by others addressing similar challenges.
The comprehensive nature of Azure architecture requires integrating knowledge from multiple disciplines including networking, security, database management, application development, and business process understanding. Successful architects develop T-shaped skill profiles combining deep expertise in specific areas with broad awareness across complementary domains. Specialization areas might include data analytics, artificial intelligence, security, or specific industry verticals requiring focused expertise. Broad awareness enables identifying integration opportunities, understanding dependencies, and designing cohesive solutions rather than isolated components. Balancing specialization depth with breadth awareness creates versatile professionals capable of addressing diverse architectural challenges.
Ethical considerations in architecture practice ensure architects prioritize client interests, maintain objectivity in technology recommendations, protect confidential information, and admit knowledge limitations rather than providing uninformed guidance. Professional integrity builds client trust and enhances architect credibility. Architects should recommend appropriate solutions regardless of personal technology preferences, considering client contexts, constraints, and objectives rather than imposing predetermined approaches. Security and privacy considerations must guide architectural decisions protecting organizational data and customer information appropriately. Transparent communication about architectural trade-offs enables informed decision-making by organizational stakeholders understanding implications of various options.
The AZ-303 certification journey represents just one phase in a dynamic, rewarding career as a cloud architecture professional. The skills, knowledge, and professional discipline developed through certification preparation provide foundations for continued growth and achievement. Whether pursuing additional certifications, specializing in specific Azure services or industries, or progressing into leadership roles, the comprehensive understanding gained through AZ-303 preparation serves professionals throughout their cloud architecture careers. The cloud computing revolution continues reshaping how organizations leverage technology, creating sustained demand for skilled architects capable of designing innovative, secure, and efficient cloud solutions. Commitment to professional excellence, continuous learning, and ethical practice ensures Azure architects remain valuable contributors to organizational success in an increasingly cloud-dependent world.
Microsoft Azure Architect AZ-303 practice test questions and answers, training course, study guide are uploaded in ETE Files format by real users. Study and Pass AZ-303 Microsoft Azure Architect Technologies certification exam dumps & practice test questions and answers are to help students.
Exam Comments * The most recent comment are on top
- AZ-104 - Microsoft Azure Administrator
- DP-700 - Implementing Data Engineering Solutions Using Microsoft Fabric
- AI-102 - Designing and Implementing a Microsoft Azure AI Solution
- AI-900 - Microsoft Azure AI Fundamentals
- AZ-305 - Designing Microsoft Azure Infrastructure Solutions
- PL-300 - Microsoft Power BI Data Analyst
- MD-102 - Endpoint Administrator
- AZ-500 - Microsoft Azure Security Technologies
- AZ-900 - Microsoft Azure Fundamentals
- SC-200 - Microsoft Security Operations Analyst
- SC-300 - Microsoft Identity and Access Administrator
- MS-102 - Microsoft 365 Administrator
- AZ-204 - Developing Solutions for Microsoft Azure
- SC-401 - Administering Information Security in Microsoft 365
- DP-600 - Implementing Analytics Solutions Using Microsoft Fabric
- SC-100 - Microsoft Cybersecurity Architect
- AZ-700 - Designing and Implementing Microsoft Azure Networking Solutions
- PL-200 - Microsoft Power Platform Functional Consultant
- AZ-400 - Designing and Implementing Microsoft DevOps Solutions
- AZ-800 - Administering Windows Server Hybrid Core Infrastructure
- SC-900 - Microsoft Security, Compliance, and Identity Fundamentals
- AZ-140 - Configuring and Operating Microsoft Azure Virtual Desktop
- PL-400 - Microsoft Power Platform Developer
- MS-900 - Microsoft 365 Fundamentals
- PL-600 - Microsoft Power Platform Solution Architect
- AZ-801 - Configuring Windows Server Hybrid Advanced Services
- DP-300 - Administering Microsoft Azure SQL Solutions
- MS-700 - Managing Microsoft Teams
- MB-280 - Microsoft Dynamics 365 Customer Experience Analyst
- PL-900 - Microsoft Power Platform Fundamentals
- GH-300 - GitHub Copilot
- MB-800 - Microsoft Dynamics 365 Business Central Functional Consultant
- MB-330 - Microsoft Dynamics 365 Supply Chain Management
- MB-310 - Microsoft Dynamics 365 Finance Functional Consultant
- DP-100 - Designing and Implementing a Data Science Solution on Azure
- DP-900 - Microsoft Azure Data Fundamentals
- MB-820 - Microsoft Dynamics 365 Business Central Developer
- MB-230 - Microsoft Dynamics 365 Customer Service Functional Consultant
- GH-200 - GitHub Actions
- MB-700 - Microsoft Dynamics 365: Finance and Operations Apps Solution Architect
- MS-721 - Collaboration Communications Systems Engineer
- MB-910 - Microsoft Dynamics 365 Fundamentals Customer Engagement Apps (CRM)
- PL-500 - Microsoft Power Automate RPA Developer
- MB-920 - Microsoft Dynamics 365 Fundamentals Finance and Operations Apps (ERP)
- GH-900 - GitHub Foundations
- MB-335 - Microsoft Dynamics 365 Supply Chain Management Functional Consultant Expert
- MB-500 - Microsoft Dynamics 365: Finance and Operations Apps Developer
- GH-500 - GitHub Advanced Security
- AZ-120 - Planning and Administering Microsoft Azure for SAP Workloads
- DP-420 - Designing and Implementing Cloud-Native Applications Using Microsoft Azure Cosmos DB
- MB-240 - Microsoft Dynamics 365 for Field Service
- GH-100 - GitHub Administration
- SC-400 - Microsoft Information Protection Administrator
- DP-203 - Data Engineering on Microsoft Azure
- AZ-303 - Microsoft Azure Architect Technologies
- 62-193 - Technology Literacy for Educators
- MB-900 - Microsoft Dynamics 365 Fundamentals
- 98-383 - Introduction to Programming Using HTML and CSS
- MO-100 - Microsoft Word (Word and Word 2019)
- MB-210 - Microsoft Dynamics 365 for Sales
- 98-388 - Introduction to Programming Using Java
Purchase AZ-303 Exam Training Products Individually



Why customers love us?
What do our customers say?
The resources provided for the Microsoft certification exam were exceptional. The exam dumps and video courses offered clear and concise explanations of each topic. I felt thoroughly prepared for the AZ-303 test and passed with ease.
Studying for the Microsoft certification exam was a breeze with the comprehensive materials from this site. The detailed study guides and accurate exam dumps helped me understand every concept. I aced the AZ-303 exam on my first try!
I was impressed with the quality of the AZ-303 preparation materials for the Microsoft certification exam. The video courses were engaging, and the study guides covered all the essential topics. These resources made a significant difference in my study routine and overall performance. I went into the exam feeling confident and well-prepared.
The AZ-303 materials for the Microsoft certification exam were invaluable. They provided detailed, concise explanations for each topic, helping me grasp the entire syllabus. After studying with these resources, I was able to tackle the final test questions confidently and successfully.
Thanks to the comprehensive study guides and video courses, I aced the AZ-303 exam. The exam dumps were spot on and helped me understand the types of questions to expect. The certification exam was much less intimidating thanks to their excellent prep materials. So, I highly recommend their services for anyone preparing for this certification exam.
Achieving my Microsoft certification was a seamless experience. The detailed study guide and practice questions ensured I was fully prepared for AZ-303. The customer support was responsive and helpful throughout my journey. Highly recommend their services for anyone preparing for their certification test.
I couldn't be happier with my certification results! The study materials were comprehensive and easy to understand, making my preparation for the AZ-303 stress-free. Using these resources, I was able to pass my exam on the first attempt. They are a must-have for anyone serious about advancing their career.
The practice exams were incredibly helpful in familiarizing me with the actual test format. I felt confident and well-prepared going into my AZ-303 certification exam. The support and guidance provided were top-notch. I couldn't have obtained my Microsoft certification without these amazing tools!
The materials provided for the AZ-303 were comprehensive and very well-structured. The practice tests were particularly useful in building my confidence and understanding the exam format. After using these materials, I felt well-prepared and was able to solve all the questions on the final test with ease. Passing the certification exam was a huge relief! I feel much more competent in my role. Thank you!
The certification prep was excellent. The content was up-to-date and aligned perfectly with the exam requirements. I appreciated the clear explanations and real-world examples that made complex topics easier to grasp. I passed AZ-303 successfully. It was a game-changer for my career in IT!

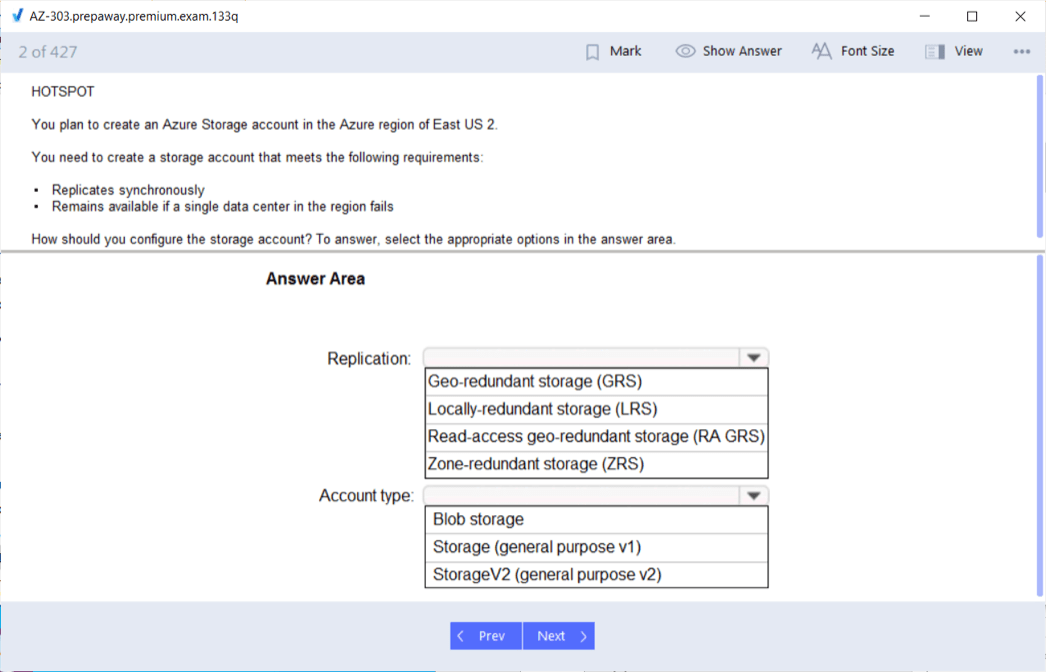
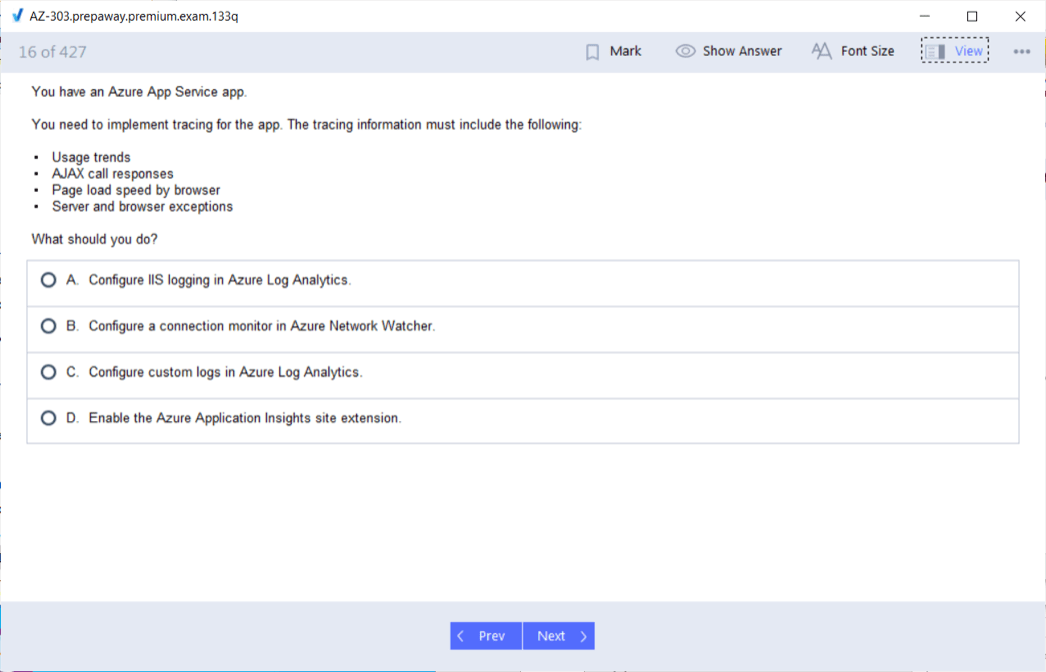
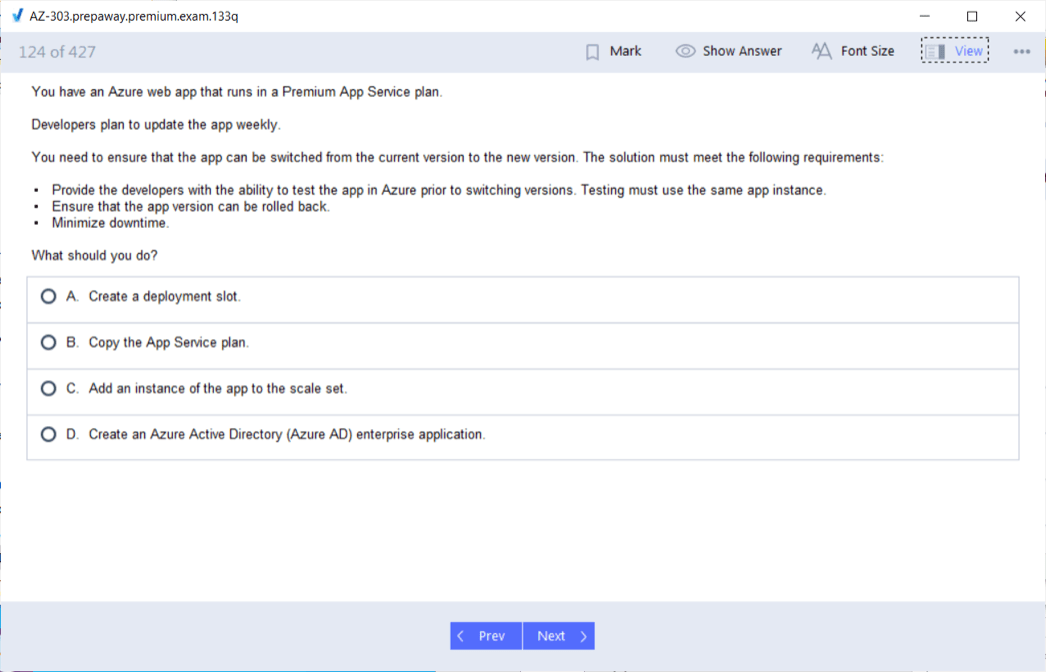
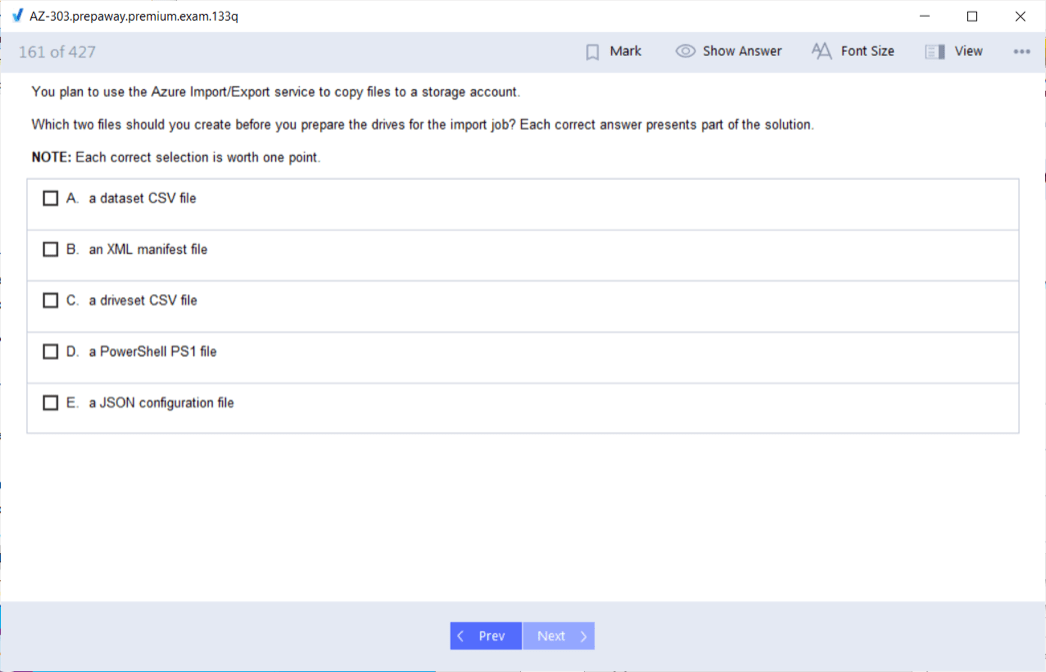








Thanks.