- Home
- Salesforce Certifications
- Certified Identity and Access Management Designer Certified Identity and Access Management Designer Dumps
Pass Salesforce Certified Identity and Access Management Designer Exam in First Attempt Guaranteed!
Get 100% Latest Exam Questions, Accurate & Verified Answers to Pass the Actual Exam!
30 Days Free Updates, Instant Download!


Certified Identity and Access Management Designer Premium File
- Premium File 60 Questions & Answers. Last Update: Feb 15, 2026
Whats Included:
- Latest Questions
- 100% Accurate Answers
- Fast Exam Updates
Last Week Results!
All Salesforce Certified Identity and Access Management Designer certification exam dumps, study guide, training courses are Prepared by industry experts. PrepAway's ETE files povide the Certified Identity and Access Management Designer Certified Identity and Access Management Designer practice test questions and answers & exam dumps, study guide and training courses help you study and pass hassle-free!
Mastering Advanced Identity Architecture for the Salesforce Certified Identity and Access Management Designer Exam
The Salesforce Certified Identity and Access Management Designer Exam evaluates professionals who design secure identity solutions within the Salesforce ecosystem. It tests the ability to design and implement secure access across systems while maintaining scalability, reliability, and compliance. This certification confirms a deep understanding of identity management principles and how Salesforce integrates with enterprise identity frameworks.
Importance of Identity and Access Management
Identity and access management is the foundation of digital security. It ensures that the right individuals have appropriate access to systems and data. Salesforce, as a core business platform, requires careful design of identity architectures that maintain user convenience while ensuring strict security controls. The exam validates a designer’s ability to balance security with usability in real-world Salesforce environments.
Role of a Certified Identity and Access Management Designer
The certified designer is responsible for developing architectures that handle authentication, authorization, and identity synchronization between Salesforce and other systems. They understand user lifecycle management, federation, and access control. Their work prevents unauthorized access, improves compliance posture, and enhances user experience across enterprise applications connected to Salesforce.
Benefits of the Certification
Achieving the Salesforce Certified Identity and Access Management Designer certification enhances professional credibility. It opens career paths in identity architecture, Salesforce security, and enterprise integration. Organizations value certified designers because they can secure user access, integrate systems seamlessly, and ensure compliance with data protection regulations. For individuals, the credential demonstrates advanced expertise in Salesforce identity design.
Who Should Take This Exam
This certification is ideal for Salesforce architects, solution designers, and security professionals who manage identity and access frameworks. It suits those who already have experience with Salesforce security features, authentication protocols, and enterprise identity systems. Candidates should understand how to connect Salesforce with identity providers, manage SSO configurations, and enforce access controls across multiple platforms.
Prerequisites for the Exam
Before taking the Salesforce Certified Identity and Access Management Designer Exam, candidates should possess a solid foundation in Salesforce administration and security. Familiarity with Salesforce Identity, connected apps, OAuth, SAML, and OpenID Connect is essential. Experience in configuring external identity providers, understanding session security, and managing user lifecycle processes is strongly recommended for success.
Exam Structure and Format
The exam typically consists of multiple-choice and multiple-select questions covering key areas of identity and access management. Candidates are tested on conceptual understanding, architectural decisions, and best practices. The time limit is generally two hours, and a minimum passing score is required. The questions are scenario-based, reflecting real-world enterprise situations that test applied knowledge.
Major Exam Domains
The major domains of the Salesforce Certified Identity and Access Management Designer Exam include identity management concepts, Salesforce as an identity provider, accepting third-party identities, access management best practices, and Salesforce identity features. Each domain assesses specific competencies necessary to design, implement, and manage robust identity solutions in the Salesforce platform and beyond.
Identity Management Concepts
Identity management involves defining, maintaining, and securing digital identities. It includes user provisioning, authentication, and authorization. In Salesforce, these processes ensure that users access data relevant to their roles. Understanding lifecycle management, federation standards, and identity protocols forms the foundation for passing the certification exam and performing effectively as an identity designer.
Salesforce as an Identity Provider
Salesforce can serve as an identity provider, allowing users to log into external systems using Salesforce credentials. As a certified designer, you must understand how to configure Salesforce Identity, manage single sign-on settings, and maintain trust relationships. This capability helps organizations streamline authentication across multiple platforms while ensuring strong access security.
Integrating Third-Party Identity Providers
Salesforce also supports integration with external identity providers through protocols such as SAML, OAuth, and OpenID Connect. Designers must determine when to use each approach based on enterprise requirements. They design trust relationships, token exchanges, and session management processes. This integration reduces login friction and improves security through centralized authentication and monitoring.
Access Management and Security Controls
Access management defines how users gain and use access within Salesforce. Certified designers plan roles, profiles, permission sets, and sharing models that enforce the principle of least privilege. They also design solutions for multifactor authentication, session timeout policies, and conditional access to enhance data protection and align with compliance standards.
Salesforce Identity Features
Salesforce provides powerful identity features such as My Domain, Single Sign-On, and Connected Apps. These features help unify user access across different Salesforce instances and external systems. The certified designer understands how to configure these tools to support secure authentication, seamless user experience, and consistent branding across multiple organizational environments.
Exam Preparation Strategy
Preparation for the Salesforce Certified Identity and Access Management Designer Exam requires a mix of theoretical study and practical experience. Candidates should review Salesforce documentation, practice with real-world scenarios, and understand architectural trade-offs. Hands-on experimentation with connected apps, identity providers, and user provisioning processes strengthens comprehension and builds exam readiness.
Common Challenges Faced by Candidates
Candidates often struggle with complex identity federation scenarios, understanding token flows, and mapping user attributes between systems. Another challenge lies in designing scalable and secure solutions that integrate with multiple identity sources. Consistent practice and review of Salesforce identity architecture patterns help overcome these challenges effectively and improve exam confidence.
Career Opportunities After Certification
Earning the Salesforce Certified Identity and Access Management Designer certification can lead to roles such as Security Architect, Identity Engineer, or Solution Designer. Professionals can work in consulting, large enterprises, or technology firms. The credential validates their ability to build and maintain enterprise-scale identity frameworks integrated with Salesforce and other business platforms.
Best Practices for Identity Design
Effective identity design emphasizes security, simplicity, and user experience. Certified designers follow best practices such as centralizing authentication, minimizing password use, enforcing strong policies, and integrating multifactor authentication. They ensure high availability, monitor for anomalies, and plan for incident response. These principles help maintain a secure and resilient Salesforce identity environment.
Maintaining and Updating Knowledge
Salesforce frequently updates its identity features and security settings. Certified designers must stay informed about platform changes, new protocols, and evolving best practices. Continuous learning through release notes, training sessions, and hands-on experimentation ensures ongoing competence and helps professionals keep their certifications relevant in a rapidly changing digital ecosystem.
Authentication Protocols and Identity Architecture Design
Authentication is the process of verifying a user’s identity before granting access to Salesforce. It ensures that only authorized individuals can access sensitive data and perform system actions. In Salesforce environments, authentication design must balance usability and security. The Salesforce Certified Identity and Access Management Designer Exam assesses knowledge of how different authentication protocols work and when to apply each.
Types of Authentication in Salesforce
Salesforce supports several authentication methods including username-password, delegated authentication, single sign-on, OAuth-based authentication, and certificate-based access. Designers must choose the right approach based on organizational requirements, user types, and security needs. Each method has distinct advantages, implementation complexities, and integration patterns that a certified designer must master for enterprise-grade identity solutions.
The Role of Single Sign-On
Single Sign-On (SSO) allows users to access multiple systems using one set of credentials. In Salesforce, SSO simplifies login management while improving security by centralizing authentication. Certified designers must design trust relationships, configure identity providers, and ensure token integrity. SSO implementation reduces password fatigue, minimizes help desk requests, and enhances user experience across integrated applications.
Benefits of Single Sign-On
SSO improves efficiency and security simultaneously. It provides faster access for users and ensures centralized password policies. With one secure authentication point, enterprises can enforce stronger security measures without disrupting workflows. For Salesforce environments integrated with multiple systems, SSO offers a unified authentication mechanism that simplifies user provisioning and access control across applications.
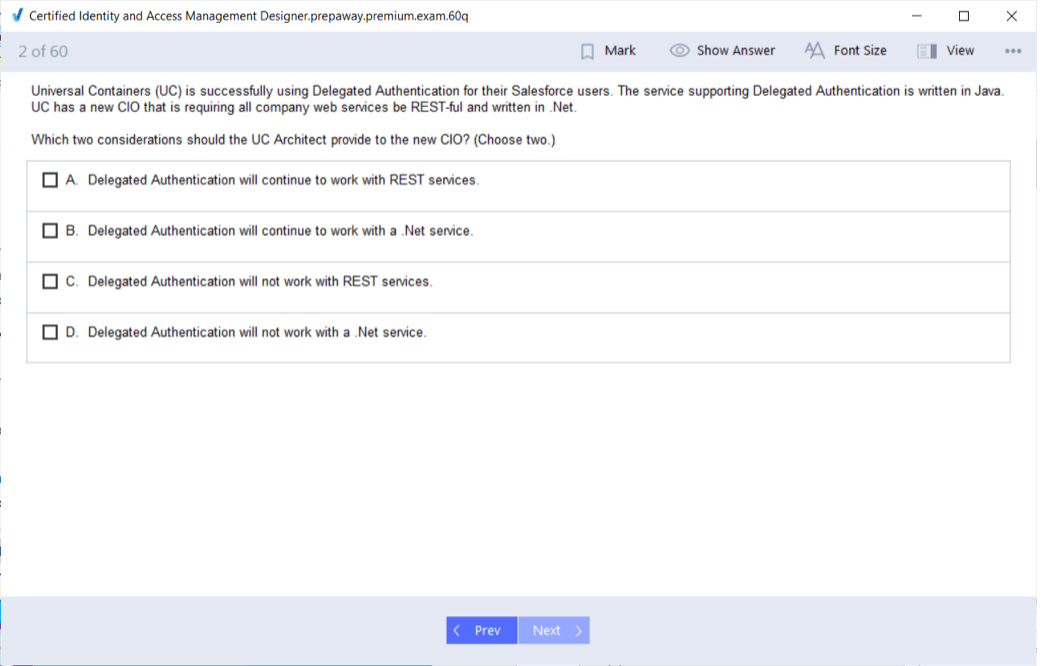
Delegated Authentication Overview
Delegated authentication allows an external system to validate Salesforce user credentials. Instead of verifying credentials within Salesforce, authentication requests are redirected to a corporate directory or identity provider. This approach supports existing enterprise password policies and enables centralized authentication management. Certified designers should understand when delegated authentication is appropriate and how to secure communication between systems.
When to Use Delegated Authentication
Delegated authentication is best suited for organizations that need real-time credential validation against corporate directories. It helps maintain consistency with existing authentication policies and enhances compliance. However, it introduces dependencies on external systems. The Salesforce Certified Identity and Access Management Designer must evaluate trade-offs between centralized control and potential reliability or performance impacts.
Introduction to OAuth
OAuth is an open standard authorization framework used to grant limited access to user resources without exposing credentials. In Salesforce, OAuth is central to API access and connected app configurations. Designers use OAuth flows to authenticate external applications securely. The exam requires understanding various OAuth flows, their purposes, and their application in different scenarios.
Common OAuth Flows in Salesforce
Salesforce supports multiple OAuth flows including the Web Server Flow, User-Agent Flow, JWT Bearer Flow, and Device Flow. Each flow serves different use cases depending on the client type and level of security required. Designers must know which flow to implement for web applications, mobile devices, service integrations, and server-to-server authentication models.
OAuth Web Server Flow
The Web Server Flow is used for applications running on secure web servers. It involves exchanging authorization codes for access tokens through back-end communication. This flow provides enhanced security by keeping tokens confidential between servers. Salesforce designers apply this flow when integrating secure web applications that interact with Salesforce APIs on behalf of users.
OAuth User-Agent Flow
The User-Agent Flow is designed for client-side applications, such as JavaScript or mobile apps, where client secrets cannot be stored securely. The flow allows direct token issuance after user authorization. While convenient, it requires careful implementation to avoid token exposure. Certified designers must implement browser security and short token lifetimes to minimize risks.
OAuth JWT Bearer Flow
The JWT Bearer Flow is used for server-to-server communication where no user interaction occurs. It allows a system to authenticate using a digitally signed JWT assertion. This flow is ideal for integrations requiring automated access, such as background services or scheduled data synchronization. Designers ensure proper key management and certificate-based signing to protect integrity.
OAuth Device Flow
The Device Flow supports devices with limited input capability, such as smart terminals or connected equipment. Users authenticate through a separate device by entering a code provided by Salesforce. This flow enhances security by separating authentication from the device itself. Designers must ensure secure code generation and session management to prevent misuse.
OpenID Connect Fundamentals
OpenID Connect builds upon OAuth to provide authentication along with authorization. It introduces the concept of ID tokens that confirm user identity. Salesforce supports OpenID Connect for integrating with identity providers and handling federated logins. Certified designers must understand token validation, claims mapping, and integration patterns for external identity providers using OpenID Connect.
Security Tokens and Token Management
Tokens are the core of modern authentication mechanisms. Salesforce uses access tokens, refresh tokens, and ID tokens to manage sessions and authorizations. Designers must ensure tokens are transmitted securely, stored safely, and revoked when compromised. Proper token management practices reduce risk and maintain compliance with security and privacy regulations.
SAML-Based Authentication
Security Assertion Markup Language (SAML) enables federated authentication through XML-based assertions. In Salesforce, SAML allows users to authenticate once with an identity provider and gain access without re-entering credentials. Certified designers must configure SAML settings, manage certificates, and troubleshoot assertion issues. Understanding SAML request-response flows is essential for exam success and real-world implementations.
Components of a SAML Configuration
A SAML setup includes a Service Provider, an Identity Provider, certificates, and metadata exchanges. Salesforce can act as either a service provider or an identity provider. Designers define assertion attributes, manage certificates for signing and encryption, and establish trust between systems. Correct configuration ensures secure, seamless user authentication across connected systems.
Benefits and Limitations of SAML
SAML offers strong security and enterprise compatibility. It supports centralized authentication and simplifies access for users. However, it requires careful setup and maintenance of certificates. Its XML-based structure can introduce complexity. Certified designers must evaluate whether SAML or OAuth better fits a specific scenario, based on organizational needs and integration environments.
Identity Architecture Principles
A robust identity architecture is built on principles of scalability, security, and simplicity. Certified designers plan how identities are stored, synchronized, and authenticated across systems. They consider factors such as multi-tenancy, integration methods, and future expansion. The goal is to create an architecture that supports evolving business needs while maintaining consistent access control.
Designing for Multiple Identity Sources
Enterprises often have multiple identity sources, such as Active Directory, external identity providers, or social login systems. Salesforce designers must create solutions that unify these identities through federation or synchronization. They define mapping strategies for user attributes and ensure consistency across directories. This approach improves user experience and reduces administrative overhead.
Identity Federation in Salesforce
Identity federation allows users to authenticate across multiple systems using a single identity. In Salesforce, federation can be achieved through SAML, OpenID Connect, or OAuth-based mechanisms. Designers establish trust frameworks that connect identity providers with Salesforce organizations. Federation reduces redundancy and enables users to access various services seamlessly with minimal friction.
Designing Identity Flows
Identity flows define how authentication and authorization requests move between systems. A Salesforce Certified Identity and Access Management Designer maps login and logout processes, token exchanges, and session terminations. The flow must ensure secure communication and maintain user experience consistency. Properly designed identity flows prevent session hijacking and unauthorized access.
Authentication vs Authorization
Authentication verifies identity, while authorization determines access rights. Both concepts are closely linked in Salesforce identity architecture. Designers implement authentication first, then define authorization policies using roles, profiles, and permission sets. Misalignment between these layers can create vulnerabilities. Certified designers ensure both processes work harmoniously to maintain data security and compliance.
Identity Lifecycle Management
Identity lifecycle management includes user creation, modification, and deactivation. In Salesforce environments, it ensures users have the correct access at all times. Designers plan automated provisioning and deprovisioning processes based on HR or directory changes. Lifecycle management prevents orphaned accounts, enforces compliance, and streamlines onboarding for new users across multiple systems.
Role of Connected Apps
Connected Apps in Salesforce enable secure integration between Salesforce and external systems using OAuth. They define policies for authentication, token lifetimes, and IP restrictions. Certified designers configure connected apps to enforce security standards and control API access. Properly managed connected apps protect sensitive data while supporting flexible integration requirements.
Identity Connect Overview
Identity Connect synchronizes user data between Salesforce and Active Directory. It simplifies identity management by maintaining consistency across systems. Designers configure synchronization rules, manage conflict resolution, and ensure secure connections. This tool reduces administrative workload and enhances security by ensuring users’ Salesforce access reflects their corporate directory status.
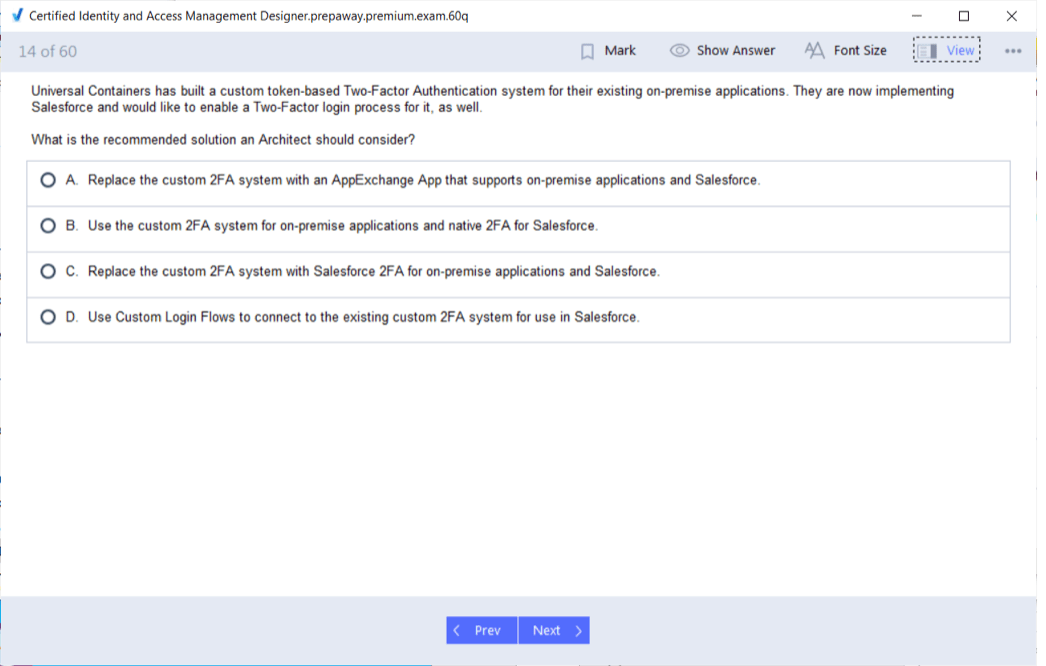
Multi-Factor Authentication Integration
Multi-factor authentication adds an extra layer of security by requiring users to verify their identity using more than one method. Salesforce supports native and external MFA options. Certified designers integrate MFA with SSO and other identity systems to provide robust protection without sacrificing usability. Proper implementation deters unauthorized access attempts effectively.
Designing Secure Session Management
Session management ensures that user sessions are properly initiated, maintained, and terminated. Salesforce allows control over session timeout, IP restrictions, and login hours. Designers establish policies to balance security with usability. Proper session management minimizes risks associated with session hijacking or unauthorized use of active sessions across different devices.
Handling Identity for Communities and Portals
Salesforce Communities and Experience Cloud sites often require custom identity solutions for partners and customers. Certified designers must support external authentication using SSO, self-registration, and social logins. The architecture must handle large-scale identity management, ensuring performance, branding consistency, and security. Properly designed systems enhance collaboration without compromising sensitive data.
Integrating Social Identity Providers
Organizations may allow users to log in using social identities such as Google or LinkedIn. Salesforce supports this through OpenID Connect and custom authentication providers. Designers integrate these services securely, map identity attributes, and maintain compliance with privacy policies. Social authentication simplifies user access while maintaining high security and consistent user management.
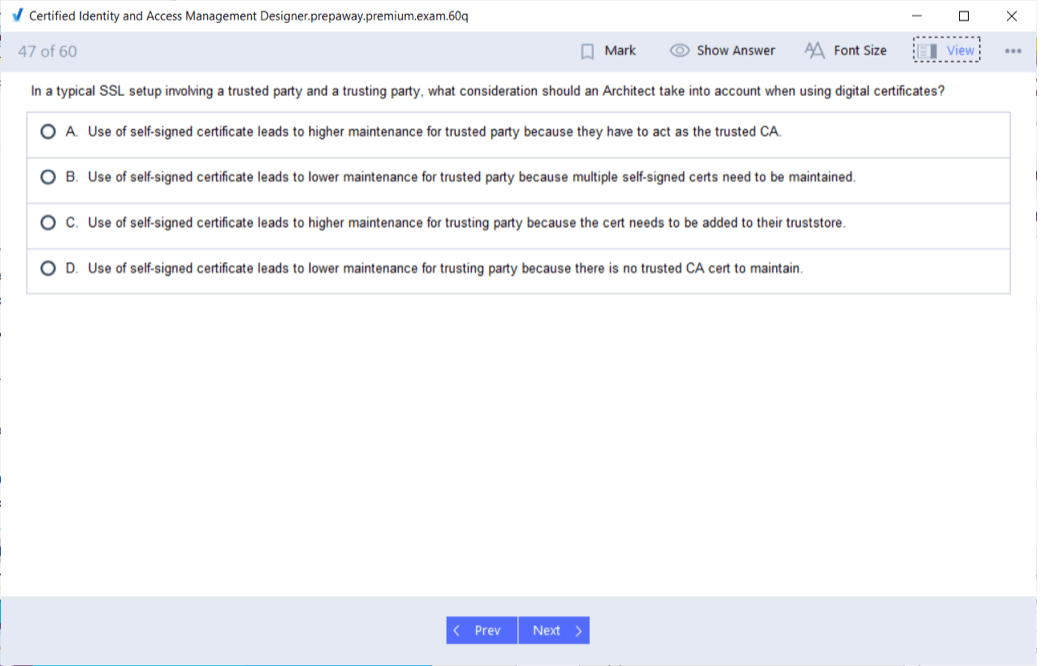
Trust Framework and Certificates
A trust framework defines how systems establish and maintain trust for authentication. Certificates play a critical role in signing and encrypting identity assertions. Designers manage certificate lifecycles, renewals, and rotations to prevent outages. Regular certificate management ensures continued trust between Salesforce and connected systems, supporting uninterrupted authentication flows.
Designing for Scalability and Performance
Scalability ensures that identity systems can handle growing user bases and authentication volumes. Certified designers design architectures that support caching, load balancing, and distributed identity services. They evaluate system limits, latency impacts, and redundancy. A scalable identity design ensures consistent performance and reliability as organizational demands evolve.
Identity Governance and Compliance
Identity governance ensures accountability, traceability, and compliance in access management. Designers implement audit trails, role reviews, and access certification processes. They align identity architecture with industry regulations such as GDPR and other data protection standards. Effective governance promotes transparency and ensures Salesforce environments meet internal and external compliance requirements.
Security Considerations for Identity Design
Security must be built into every layer of identity design. Certified designers evaluate potential threats like token theft, replay attacks, or phishing. They enforce encryption, secure protocols, and minimal privilege principles. Regular security reviews and penetration testing ensure identity solutions remain resilient against evolving threats within Salesforce ecosystems.
Monitoring and Auditing Access
Continuous monitoring detects unusual login patterns, failed authentication attempts, and privilege escalations. Salesforce provides event monitoring tools for tracking access behavior. Designers configure alerts, dashboards, and automated responses. Auditing ensures accountability and helps identify weaknesses before exploitation. A proactive monitoring approach strengthens overall identity and access security posture.
Designing for Business Continuity
Identity systems are critical to business operations. Designers must plan for redundancy, disaster recovery, and failover mechanisms. Backup identity providers, replicated metadata, and alternative login methods ensure uninterrupted access during outages. A resilient identity architecture supports business continuity even when certain components experience downtime or connectivity issues.
Future of Identity in Salesforce
The evolution of identity management is moving toward passwordless authentication, biometric verification, and adaptive access. Salesforce continues to expand its identity capabilities with AI-driven access control and risk-based authentication. Certified designers must stay informed about these developments to design future-ready architectures that align with emerging technologies and security models.
Authorization, Access Control, and Role Design
Authorization determines what an authenticated user is allowed to do once they gain access to Salesforce. It defines access to data, applications, and functions based on permissions and roles. In the Salesforce Certified Identity and Access Management Designer Exam, candidates must understand how authorization aligns with business objectives and security principles across multiple integrated systems.
Difference Between Authentication and Authorization
Authentication confirms identity, while authorization defines the scope of access. Even if a user is authenticated, they may not be authorized to view specific data or perform certain actions. A certified designer must separate these two processes when designing security frameworks. Proper distinction ensures better control, reduces vulnerabilities, and enforces the principle of least privilege.
The Principle of Least Privilege
The principle of least privilege ensures users have only the permissions necessary to perform their jobs. In Salesforce, this means designing access models that limit exposure to sensitive data. Certified designers implement least privilege through a combination of roles, profiles, and permission sets. The approach enhances security while supporting flexibility in business operations.
Role Hierarchies in Salesforce
Role hierarchies define data visibility within an organization. Higher roles inherit access to records owned by lower roles. A well-designed hierarchy mirrors the company’s reporting structure while enforcing security. Certified designers must ensure role hierarchies align with business governance models and do not unintentionally grant broad data visibility that compromises confidentiality.
Designing Role Hierarchies Effectively
Effective role design requires understanding the organization’s structure and operational flow. Too many roles can cause maintenance complexity, while too few can reduce flexibility. Designers must balance simplicity with granularity. They should create scalable hierarchies that accommodate growth, acquisitions, or reorganizations without disrupting access models or violating compliance requirements.
Understanding Profiles
Profiles in Salesforce define baseline permissions for users, including object access, field-level security, and system privileges. Each user is assigned one profile that determines their general capabilities. Certified designers must understand how profiles interact with roles, permission sets, and sharing rules. Proper profile management forms the foundation of secure access control strategies.
Profile Management Best Practices
Profiles should be kept minimal and standardized across similar user groups. Avoid creating unique profiles for each user, as it increases administrative overhead. Instead, combine profiles with permission sets to add flexibility. Designers maintain governance by naming profiles clearly, documenting their purpose, and periodically auditing assigned permissions to ensure alignment with security policies.
Permission Sets and Permission Set Groups
Permission sets provide additional access rights beyond what profiles define. They allow temporary or role-specific permissions without altering core profiles. Permission set groups bundle multiple permission sets, simplifying complex permission management. Certified designers use these tools to create modular, scalable access control frameworks that adapt to evolving business and security requirements.
When to Use Permission Sets
Permission sets are ideal when users require temporary or specialized access. For instance, project-based roles can receive additional rights without modifying existing profiles. Designers use them to minimize the proliferation of profiles. They also help implement principle-based access control, enabling consistent management of user privileges across departments and systems.
Field-Level Security
Field-level security controls access to specific fields within an object. It ensures that even if a user can view a record, they may not see sensitive fields like salaries or personal information. Certified designers must configure field permissions through profiles, permission sets, and object-level security. Field-level restrictions protect confidential data and ensure compliance.
Object-Level and Record-Level Security
Object-level security controls access to entire objects, while record-level security defines which individual records within an object a user can access. Certified designers manage object access using profiles and permission sets and manage record access through sharing rules, organization-wide defaults, and role hierarchies. Together, these mechanisms ensure comprehensive access governance.
Organization-Wide Defaults
Organization-wide defaults (OWD) set the baseline level of record access for all users in an organization. Designers choose among public read/write, public read-only, controlled by parent, or private settings. A private default ensures maximum restriction, requiring explicit sharing for additional access. Certified designers begin with restrictive defaults and open access only when necessary.
Sharing Rules in Salesforce
Sharing rules provide exceptions to organization-wide defaults by granting specific users or groups additional record access. They can be based on ownership or criteria. Certified designers use sharing rules to enable collaboration without compromising security. Proper design ensures that sharing rules remain efficient, scalable, and easy to maintain as organizations evolve.
Manual Sharing and Team Access
Manual sharing allows individual users to share specific records with others. Teams, such as account or opportunity teams, facilitate controlled collaboration. Certified designers must understand how manual sharing interacts with role hierarchies and sharing rules. Although flexible, excessive manual sharing can complicate audits, so designers implement governance to prevent misuse.
Apex Managed Sharing
Apex Managed Sharing provides programmatic control over record sharing. It allows developers to create or revoke access dynamically based on business logic. Certified designers must know when to use Apex sharing instead of declarative methods. Proper implementation ensures that programmatic sharing aligns with security rules and does not override established access boundaries.
Territory Management
Territory management organizes access by geography, product, or business unit rather than hierarchy. It supports complex sales models by assigning users to territories that determine record visibility. Certified designers must understand how territory models interact with role hierarchies and sharing rules. Proper configuration optimizes collaboration without compromising security or performance.
Public Groups and Queues
Public groups simplify sharing by allowing administrators to group users, roles, or territories. Queues are used for managing unassigned records awaiting processing. Certified designers utilize groups and queues to streamline sharing configurations. They reduce redundancy and make access models easier to maintain, especially in large-scale Salesforce implementations with thousands of users.
Criteria-Based Sharing
Criteria-based sharing automatically grants access to records that meet specific conditions. It allows flexible collaboration based on dynamic business requirements. Certified designers use this feature to provide targeted visibility while maintaining control. Well-crafted criteria-based rules reduce manual administration and ensure consistent enforcement of access policies throughout the system.
Permission Dependency and Overlap
In complex Salesforce environments, multiple permissions may overlap or conflict. Certified designers must identify redundant access rights and resolve conflicts that grant unintended privileges. Reviewing dependencies between profiles, permission sets, and sharing rules ensures users only have required permissions. Continuous audits prevent privilege creep and strengthen overall access security.
Role-Based Access Control
Role-based access control (RBAC) assigns permissions based on job roles. In Salesforce, roles determine data visibility and access rights. Certified designers align RBAC structures with organizational hierarchies to reflect real-world responsibilities. Implementing RBAC ensures scalability, simplifies management, and provides a clear framework for granting and revoking access consistently across departments.
Attribute-Based Access Control
Attribute-based access control (ABAC) extends RBAC by using user attributes, environmental conditions, or resource properties to make access decisions. Salesforce designers use ABAC principles in complex integrations or external identity systems. It provides dynamic access decisions based on context, improving flexibility and supporting advanced compliance requirements for adaptive access control.
Policy-Based Access Management
Policy-based access management centralizes access rules as policies rather than hard-coded permissions. Certified designers create policies that evaluate context such as location, device, or time. This approach complements traditional role models and enhances flexibility. Implementing policies in Salesforce ensures scalable and consistent enforcement across multiple systems and integration layers.
Access Control in Integrated Environments
When Salesforce integrates with external systems, consistent access control is critical. Designers synchronize permissions through federation or centralized authorization. They ensure tokens and roles map correctly across platforms. Integration design must prevent privilege escalation or data leakage. Unified access control across systems guarantees compliance and maintains a secure enterprise identity environment.
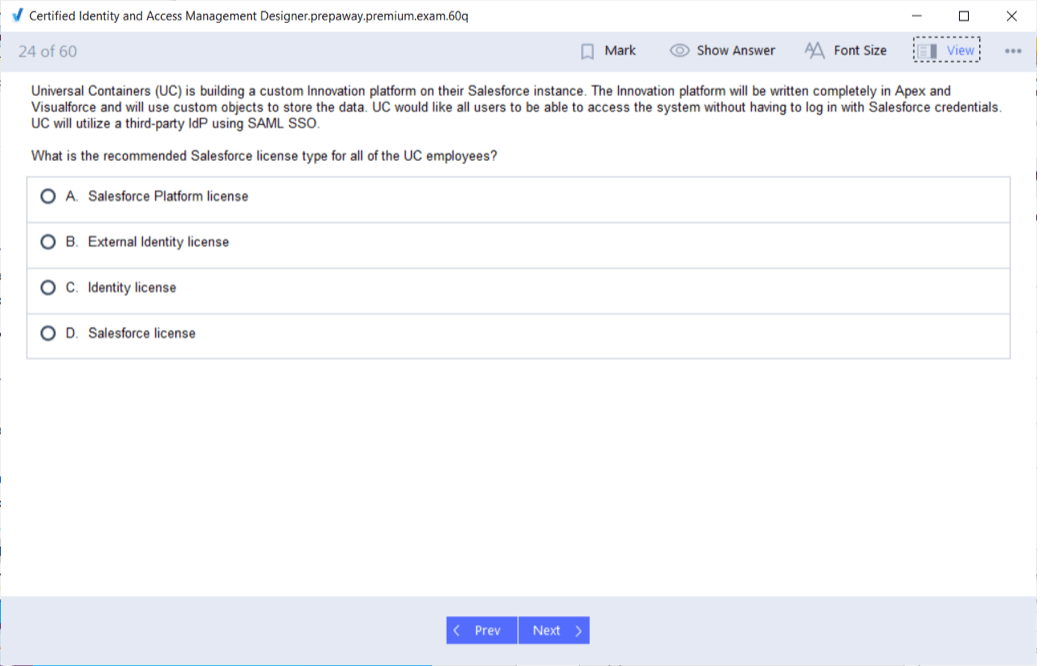
Managing Access for External Users
External users such as partners or customers access Salesforce through Experience Cloud or portals. Certified designers must tailor security for these users without compromising internal data. They define separate roles, profiles, and authentication mechanisms. Designs include limited visibility, strict session controls, and segregation from internal user data to maintain data integrity.
Community User Access Models
Community users have different access needs based on their community type. Designers configure access using sharing sets and rules tied to contact or account relationships. The configuration ensures partners can collaborate efficiently while customers access only relevant data. Certified designers design community architectures that balance openness with controlled visibility and compliance.
Integration with External Access Control Systems
Many enterprises use external identity or access management systems. Salesforce designers integrate these solutions to synchronize authorization policies. This ensures centralized governance and reduces redundancy. Integration may involve SAML, OAuth scopes, or custom APIs. Proper mapping between Salesforce permissions and external roles ensures seamless authorization across applications.
Evaluating Access Risk
Risk evaluation involves assessing potential vulnerabilities in access models. Designers review privileges, audit logs, and role assignments to detect excessive access. High-risk roles undergo stricter controls. Risk-based access decisions help organizations enforce adaptive security. Certified designers implement automated risk evaluation mechanisms to adjust access dynamically based on threat levels.
Temporary and Conditional Access
Certain scenarios require time-bound or conditional access. Salesforce designers apply permission sets or session-based restrictions to control temporary privileges. For instance, administrative access may expire after completion of a task. Conditional access policies based on user context, device, or location enhance flexibility while preserving security in sensitive operations.
Data Sharing Across Multiple Orgs
Organizations with multiple Salesforce orgs often need to share data securely. Designers implement integration models like APIs, external objects, or identity federation to synchronize access. They ensure consistent authorization policies across instances. Cross-org data sharing must maintain integrity and privacy, especially when handling customer information or regulated data.
Encryption and Access Control
Encryption protects data even if access controls fail. Salesforce supports encryption at rest and field-level encryption. Designers combine encryption with access control to safeguard sensitive information. They ensure encryption keys are securely managed and only authorized processes can decrypt data. Layered security enhances compliance and reduces the risk of exposure.
Delegated Administration
Delegated administration allows specific users to manage subsets of data or users without granting full administrative privileges. Certified designers use delegated administration to distribute responsibilities safely. It reduces the burden on system administrators while maintaining strict access limits. Proper governance ensures delegated administrators cannot alter global configurations or sensitive data.
Access Reviews and Certification
Regular access reviews verify that user permissions remain appropriate. Certified designers establish review cycles where managers validate access for their teams. Certification processes identify redundant or outdated privileges. Periodic reviews maintain compliance with security standards and reduce insider threats by ensuring only authorized personnel retain necessary access.
Implementing Access Policies for Compliance
Compliance standards require structured access policies that align with legal and industry frameworks. Designers define and document policies governing user access, data sharing, and authentication. These policies guide system configuration and audits. Implementing standardized policies ensures consistency across departments and demonstrates compliance during security assessments or regulatory reviews.
Managing Access During Mergers or Acquisitions
When organizations merge, Salesforce environments often require consolidation. Designers plan identity mapping, role restructuring, and access realignment. Temporary policies maintain security during transitions. Properly managed mergers ensure data integrity while allowing seamless collaboration. The certified designer plays a critical role in mitigating risks and aligning access control with new governance frameworks.
Troubleshooting Authorization Issues
Authorization problems can arise from misconfigured profiles, roles, or sharing settings. Certified designers troubleshoot by analyzing user permissions, examining record-level access, and validating rule logic. Tools like login history and debug logs assist in identifying issues. Quick and structured troubleshooting maintains user productivity and prevents potential security exposures.
Auditing and Logging Access
Auditing ensures transparency and accountability in access control. Designers configure logging mechanisms to track permission changes, login activity, and data modifications. Regular audits detect unauthorized actions and support forensic investigations. Maintaining detailed audit trails helps organizations meet compliance standards and fosters trust in the security of Salesforce environments.
Automating Access Management
Automation reduces human error and increases efficiency in managing permissions. Certified designers implement workflows, approval processes, or integration with identity governance systems. Automated provisioning and deprovisioning ensure timely updates when users change roles or leave the organization. Automation supports scalable, secure, and consistent access management across large enterprises.
Future Trends in Access Control
Access management continues to evolve with emerging technologies like adaptive access, machine learning-based anomaly detection, and zero-trust models. Salesforce designers must stay ahead by embracing these innovations. The future emphasizes continuous verification, behavior-based policies, and dynamic privileges. Understanding these trends ensures that certified professionals design resilient and forward-looking authorization frameworks.
Identity Federation, External Integrations, and Trust Frameworks
Identity federation enables users to access multiple systems using a single set of credentials. In Salesforce environments, federation allows seamless authentication between Salesforce and external applications. It eliminates the need for duplicate credentials and enhances security by centralizing authentication. The Salesforce Certified Identity and Access Management Designer Exam emphasizes designing scalable and secure federation models.
The Role of Identity Federation in Modern Enterprises
Organizations often operate multiple cloud and on-premise systems. Identity federation connects these systems under a unified authentication model. It simplifies user management, improves access control, and supports compliance. By implementing federation, enterprises reduce administrative overhead while maintaining consistent policies across diverse platforms. Certified designers ensure integration aligns with business objectives and security standards.
Components of a Federated Identity Model
A federated identity model includes the identity provider, service provider, authentication protocol, and trust relationships. The identity provider authenticates the user and issues assertions, while the service provider relies on those assertions for access decisions. Salesforce can function as either component depending on requirements. Designers must configure each element carefully to ensure reliability and trust.
Identity Provider and Service Provider Roles
An identity provider manages user credentials and authenticates identities. The service provider relies on these validations to grant access to resources. Salesforce may act as an identity provider when managing access to external systems or as a service provider when relying on corporate credentials. Certified designers determine which configuration best suits each scenario.
Establishing Trust Between Systems
Trust is fundamental to federation. Systems exchange certificates or keys to verify assertions and ensure message integrity. Designers establish trust through metadata exchange and secure configuration of endpoints. They manage certificates to avoid expiration or compromise. Maintaining consistent trust ensures reliable communication between Salesforce and other platforms in federated environments.
Benefits of Identity Federation
Federation improves the user experience by reducing password fatigue and login complexity. It also enhances security through centralized authentication policies and improved visibility. Administrators can manage user access from one system, reducing risks of inconsistency. Certified designers implement federation to create unified identity ecosystems that scale efficiently while maintaining strong security posture.
Common Federation Standards
Several standards govern identity federation, including SAML, OpenID Connect, OAuth, and WS-Federation. Each protocol defines how authentication data is exchanged between systems. Salesforce supports SAML and OpenID Connect as primary federation protocols. Certified designers must know how each standard functions, their advantages, and their compatibility with Salesforce environments to ensure proper implementation.
SAML in Federated Architectures
SAML enables secure exchange of authentication data using XML-based assertions. In a federated setup, Salesforce and the identity provider exchange SAML requests and responses. Designers configure attributes, certificates, and endpoints to ensure successful communication. SAML is widely used in enterprise integrations where formal trust agreements and strict compliance requirements exist.
OpenID Connect in Federated Architectures
OpenID Connect extends OAuth to provide identity verification along with authorization. It uses tokens such as ID tokens to carry user identity information. Salesforce supports OpenID Connect for modern, lightweight federation. Designers use it for integrations with external identity systems and social logins. OpenID Connect simplifies token management and supports mobile and web applications efficiently.
OAuth-Based Federation Scenarios
OAuth enables delegated access between applications without sharing credentials. In Salesforce federation, OAuth is used to integrate with systems requiring API access or token-based communication. Designers implement OAuth flows suitable for specific use cases like service integrations, automation, or mobile access. Secure token handling and proper scope definitions are crucial for maintaining trust.
Trust Framework Fundamentals
A trust framework defines policies, standards, and procedures that govern identity relationships between organizations. It specifies how entities authenticate, authorize, and share information securely. Salesforce designers use trust frameworks to ensure predictable behavior in federated identity systems. Establishing consistent frameworks enhances interoperability and ensures compliance with organizational and industry security requirements.
Establishing a Federation Trust Framework
When designing a trust framework, certified professionals define identity sources, data exchange rules, and authentication standards. They determine how tokens and assertions are validated and how revocation is handled. The framework outlines responsibilities between identity providers and service providers. Clear definitions prevent miscommunication and ensure secure, transparent operations across systems.
Identity Assertion and Validation
In federation, an identity assertion is a statement confirming that a user has been authenticated. Assertions include attributes like username, email, or roles. Validation ensures the assertion is authentic and unaltered. Salesforce verifies assertions through certificates and digital signatures. Certified designers implement validation logic that protects against tampering and replay attacks.
Token Exchanges and Trust
Federated authentication often involves token exchanges between systems. Tokens serve as temporary credentials that represent user sessions. Designers define token lifecycles, renewal processes, and revocation policies. Maintaining token integrity is essential to prevent unauthorized access. A well-managed token exchange process strengthens trust and ensures continuous, secure communication between federated entities.
Multi-Org Federation in Salesforce
Enterprises may operate multiple Salesforce orgs that require unified authentication. Federation allows users to move between orgs without re-authentication. Designers implement single sign-on across orgs using identity providers or Salesforce-to-Salesforce trust configurations. This approach simplifies access, reduces administrative complexity, and ensures consistent enforcement of identity governance policies throughout the enterprise.
Cross-Domain Authentication
Cross-domain authentication enables users to access resources hosted in different domains under the same organization. Designers configure cookies, tokens, and session settings to allow secure transitions. This functionality enhances usability in multi-brand or multi-region environments. Certified designers ensure security measures prevent token leakage or unauthorized cross-domain access while maintaining seamless user experiences.
Integrating Salesforce with External Identity Providers
Integration with external identity providers is common in large organizations that maintain centralized identity management. Designers configure Salesforce to accept authentication assertions from systems like Active Directory or other cloud identity platforms. Proper integration ensures single authentication points and centralized governance. It also improves compliance with enterprise-wide security policies.
Salesforce as an Identity Provider
Salesforce can act as an identity provider for other applications. In this configuration, it authenticates users and issues assertions to external service providers. Certified designers configure identity provider settings, manage certificates, and map user attributes. This approach is useful when Salesforce serves as the central authentication hub for partner or customer systems.
Salesforce as a Service Provider
When Salesforce functions as a service provider, it relies on an external identity provider for authentication. Users log in through the identity provider, which sends assertions to Salesforce. Designers must ensure correct metadata exchange, certificate management, and session configuration. This setup integrates Salesforce within enterprise single sign-on frameworks while maintaining robust security.
Designing for Multi-Factor Federation
Multi-factor authentication can be integrated into federated logins to strengthen security. The identity provider performs additional verification steps, such as SMS codes or biometric checks. Designers ensure MFA tokens flow securely through federation processes without disrupting user sessions. Implementing MFA in federated contexts enhances protection against credential theft and unauthorized access.
Identity Linking and Attribute Mapping
When integrating multiple identity systems, user accounts must be linked accurately across platforms. Attribute mapping ensures user information aligns between identity providers and Salesforce. Designers define mapping rules for identifiers like username, email, or employee ID. Consistent mapping prevents duplicate accounts, simplifies synchronization, and ensures accurate identity representation throughout the federation.
Directory Synchronization
Directory synchronization ensures that user data remains consistent across systems. Designers integrate Salesforce with corporate directories to synchronize attributes like name, role, and status. Automated synchronization minimizes manual administration and prevents discrepancies. It also supports real-time provisioning and deprovisioning, ensuring users retain appropriate access as their organizational roles change.
Handling Identity Lifecycle in Federated Systems
Managing identity lifecycle in federated environments involves coordinating provisioning, updates, and deactivation across multiple systems. Designers create workflows that propagate changes from the identity provider to Salesforce automatically. Proper lifecycle management prevents orphaned accounts and ensures compliance. It also maintains synchronization between employee status and access privileges across federated systems.
Challenges in Federated Identity Design
Designing federated systems presents challenges such as managing multiple trust relationships, ensuring token security, and handling diverse protocols. Certified designers must anticipate potential failures and design redundancy. They also implement monitoring to detect trust issues quickly. Overcoming these challenges requires deep understanding of authentication flows, encryption, and cross-system communication patterns.
Federation Security Considerations
Security in federation extends beyond protocol implementation. Designers must consider encryption, key rotation, and endpoint security. Ensuring data is transmitted only through secure channels protects against interception. Additionally, monitoring failed login attempts and assertion anomalies helps detect malicious activity. Proactive management ensures ongoing trust and protection within federated environments.
Monitoring Federated Authentication
Monitoring is essential to maintain transparency in federated systems. Designers implement logging for all authentication events, including assertion validation and token exchanges. They analyze logs for irregularities and generate alerts for potential breaches. Continuous monitoring enhances visibility, supports incident response, and ensures the trust relationship remains secure and verifiable over time.
Troubleshooting Federation Issues
Federation issues often arise from misconfigured certificates, attribute mismatches, or incorrect endpoints. Certified designers approach troubleshooting methodically by analyzing logs, verifying metadata, and testing assertion validity. Proper documentation of configurations aids in quick resolution. Effective troubleshooting ensures minimal downtime and prevents disruptions in authentication for users across federated systems.
Federation Scalability and Performance
As organizations grow, federated systems must handle increased authentication loads. Designers plan for scalability by optimizing metadata, using load balancers, and distributing identity provider services. They monitor response times and implement caching strategies where appropriate. Scalable design ensures consistent performance, even during peak authentication requests or system integrations.
Integrating Third-Party Applications
Federation extends to third-party applications that connect to Salesforce. Designers configure trust and authentication flows that allow secure access for partner systems. Each integration must follow established policies for token handling and access control. Proper governance ensures that external applications participate safely in federated ecosystems without creating vulnerabilities.
Federation in Hybrid Environments
Many enterprises operate hybrid infrastructures combining cloud and on-premise systems. Salesforce federation bridges these environments by providing unified access. Designers ensure compatibility between legacy systems and modern protocols. Hybrid federation designs support smooth transitions to the cloud, preserving existing security investments while adopting scalable identity solutions for the future.
API Federation and Access
Federation is not limited to user authentication; it also extends to APIs. Salesforce APIs can be protected using federated tokens to authorize third-party integrations. Designers configure secure token validation, scope definitions, and expiration management. API federation supports automated data exchange while enforcing strict security standards across integrated services.
Business-to-Business Federation
B2B federation enables secure authentication and data exchange between organizations. In Salesforce, it allows partners or vendors to access shared portals using their own identity systems. Designers establish inter-company trust agreements, define attribute mappings, and enforce role-based access. B2B federation enhances collaboration while ensuring each party retains control over its user identities.
Business-to-Consumer Federation
For customer-facing systems, federation allows consumers to log in with social or existing identities. Salesforce supports this through OpenID Connect and social identity integration. Designers prioritize convenience while maintaining data protection and privacy. Consumer federation simplifies access, enhances engagement, and aligns with modern expectations for seamless digital experiences.
Legal and Compliance Aspects of Federation
Federation involves transferring identity information between entities, which raises compliance considerations. Designers ensure adherence to privacy regulations by minimizing attribute sharing and obtaining consent where necessary. They document data flows and establish clear policies for data retention. Compliance ensures that federated architectures operate within legal boundaries and maintain user trust.
Certificate and Key Management
Certificates secure federated communication through signing and encryption. Designers manage certificate lifecycles by tracking expiration dates, renewing keys, and updating metadata proactively. They implement secure storage for private keys and enforce strict access control. Reliable certificate management prevents authentication failures and preserves trust relationships across federated systems.
Disaster Recovery in Federated Systems
Federated identity systems must remain available during outages. Designers plan redundancy for identity providers, maintain backup certificates, and implement failover routes. In disaster recovery scenarios, users should still authenticate through alternative trusted systems. Continuity planning ensures authentication resilience and protects business operations from disruption due to federation failures.
Governance of Federated Identity Systems
Governance ensures federated identity systems operate consistently and securely. Designers establish policies for onboarding new providers, managing trust relationships, and reviewing configurations. Periodic audits confirm adherence to standards. Governance frameworks also define escalation procedures for incident management, maintaining long-term reliability and confidence in federated identity environments.
Automation in Federation Management
Automation reduces manual configuration errors in complex federation networks. Designers automate tasks such as certificate renewal, attribute mapping, and provisioning synchronization. Automated monitoring alerts administrators of anomalies in real time. This proactive approach increases efficiency, minimizes risk, and supports continuous compliance with security and operational requirements.
Federation Testing and Validation
Before deployment, federation configurations require thorough testing. Designers validate assertion exchanges, session management, and failover scenarios. Testing ensures compatibility between identity providers and service providers. Regular validation after updates or certificate changes prevents unexpected authentication issues. Systematic testing guarantees stability and reliability across federated Salesforce environments.
Future of Federated Identity
Federation continues to evolve toward more secure and user-friendly models. Trends such as decentralized identity, passwordless access, and blockchain-based trust systems are shaping future architectures. Salesforce designers must adapt to these innovations while maintaining compatibility with current standards. Understanding these emerging trends ensures long-term relevance and adaptability in identity management strategies.
Identity Governance, Compliance, and Lifecycle Management
Identity governance ensures that access to systems and data remains controlled, compliant, and traceable throughout an organization. Within Salesforce environments, governance defines how identities are created, managed, and retired securely. The Salesforce Certified Identity and Access Management Designer Exam emphasizes governance as a key competency, requiring designers to implement policies that enforce consistent access management.
The Role of Governance in Identity Management
Governance extends beyond technical access controls. It includes defining roles, enforcing segregation of duties, and implementing auditing. In Salesforce, governance connects identity architecture with business policies. Certified designers establish frameworks that align security with organizational objectives, ensuring every user’s access is appropriate, justified, and monitored for compliance.
Importance of Compliance in Identity Systems
Compliance frameworks protect organizations from data breaches and legal liabilities. Regulations such as privacy acts and data protection laws define how user data should be stored and accessed. The certified designer ensures that Salesforce identity systems comply with these regulations by implementing access reviews, consent tracking, and transparent audit trails.
Principles of Identity Lifecycle Management
Identity lifecycle management refers to the process of provisioning, updating, and deactivating user accounts. It ensures that users have the right access at the right time and lose it when no longer needed. In Salesforce, lifecycle management integrates with directories, identity providers, and HR systems to automate transitions and reduce administrative risk.
Stages of Identity Lifecycle
The identity lifecycle includes creation, maintenance, modification, suspension, and deletion. Each stage requires precise control and tracking. Designers ensure that user provisioning aligns with onboarding policies and that changes reflect real-time job responsibilities. When employment ends or roles change, deactivation processes automatically remove access to Salesforce and integrated applications.
Automating User Provisioning
Automated provisioning connects identity systems to HR and directory platforms. When new employees join, accounts and permissions are created based on predefined templates. Salesforce supports automated provisioning through APIs and connected identity platforms. Automation ensures accuracy, reduces human error, and speeds up onboarding, making it an essential capability for certified designers.
Managing Role-Based Access
Role-based access control assigns permissions based on job functions. In Salesforce, designers use roles, profiles, and permission sets to enforce least privilege. Governance requires regular review of these configurations to prevent privilege creep. Properly designed roles simplify access assignment, maintain scalability, and reduce security risks associated with excessive or outdated permissions.
Attribute-Based Access Control in Salesforce
Attribute-based access control enhances flexibility by considering user attributes, context, and resource sensitivity. Salesforce designers use this model for advanced scenarios such as conditional access or geographic restrictions. By leveraging attributes like department or device type, designers enforce fine-grained policies that improve security while maintaining operational efficiency and user convenience.
Policy-Based Governance
Policies define how identity systems should behave under various conditions. Certified designers implement policies for authentication strength, session duration, and data access. Salesforce allows policy enforcement through features like login IP ranges and password expiration. Establishing clear policies ensures consistent security behavior across users and reduces the likelihood of misconfiguration.
Identity Governance Frameworks
Governance frameworks provide structure to identity management operations. They define accountability, control mechanisms, and performance metrics. Salesforce designers align with frameworks that guide compliance and best practices. A well-designed governance framework ensures consistency across multiple business units and simplifies audits by providing clear documentation of identity operations.
Access Certification and Review
Access certification involves periodic verification of user privileges. Reviewers confirm that users retain only necessary access. Salesforce designers implement automated reports and dashboards to streamline certification. Regular reviews detect orphaned accounts or unnecessary permissions. This practice strengthens governance and demonstrates compliance to regulators and auditors.
Segregation of Duties in Salesforce
Segregation of duties prevents conflict of interest by separating responsibilities among different users. For example, a user approving financial transactions should not also create them. Salesforce designers define and monitor these separations using permission sets and profiles. Proper segregation ensures data integrity and reduces fraud or misuse within the platform.
Governance Through Audit Trails
Auditing provides transparency and accountability within identity systems. Salesforce maintains audit logs that record authentication events, permission changes, and configuration updates. Certified designers configure auditing tools to capture critical actions and generate reports for compliance. An effective audit trail supports forensic analysis and compliance verification during external audits.
Integrating Governance with Directory Services
Directory integration enhances governance by centralizing user data. Salesforce connects with directories to synchronize user attributes, enforce access rules, and streamline lifecycle events. Designers ensure consistent attribute mapping and bidirectional synchronization. Integration reduces data silos and ensures that access rights remain synchronized with corporate identity policies.
Governance in Federated Environments
Federated systems add complexity to governance due to distributed identity sources. Designers implement centralized governance layers that monitor authentication and authorization across all connected platforms. Policies apply uniformly regardless of where authentication originates. This approach maintains control, enforces compliance, and prevents gaps in oversight within federated Salesforce environments.
Identity Risk Assessment
Governance involves evaluating risks associated with user access. Designers perform identity risk assessments to identify high-risk accounts, sensitive data exposure, and weak configurations. Risk scoring models guide remediation actions. Salesforce provides visibility into login anomalies and user activity trends, helping organizations prioritize governance controls effectively and proactively.
Compliance Auditing and Reporting
Compliance auditing verifies adherence to organizational and regulatory requirements. Salesforce offers reporting tools that assist in demonstrating compliance. Certified designers create dashboards showing authentication activity, access changes, and provisioning timelines. Detailed reports simplify audit processes and provide evidence of consistent governance and compliance management across the organization.
Legal and Regulatory Alignment
Compliance involves aligning Salesforce configurations with legal mandates. Designers ensure privacy policies match system behaviors. Data retention, encryption, and consent collection must reflect applicable regulations. Maintaining alignment prevents penalties and protects organizational reputation. Certified professionals continuously assess and update configurations as new legal requirements emerge.
Handling Personally Identifiable Information
Salesforce identity systems often store personally identifiable information. Designers enforce strict policies for data minimization, encryption, and anonymization. Access to sensitive attributes is limited based on business needs. Proper handling ensures privacy compliance, prevents data misuse, and maintains customer trust in enterprise Salesforce implementations.
Identity Governance Automation
Automation strengthens governance by enforcing consistent policies without manual intervention. Automated workflows manage provisioning, deactivation, and access reviews. Salesforce integrates automation through flows and APIs. Designers implement triggers that enforce policy adherence in real time. Automation ensures governance processes scale efficiently and remain reliable as the organization grows.
Role of Artificial Intelligence in Governance
Artificial intelligence enhances governance by analyzing patterns in user behavior and detecting anomalies. Salesforce’s analytics tools can identify unusual access patterns or permission escalations. Certified designers leverage AI-driven insights to improve risk management and reduce manual review efforts. This proactive approach increases accuracy and operational efficiency in governance programs.
Policy Enforcement and Remediation
Governance requires enforcement of policies when violations occur. Designers define automated remediation processes that revoke access or trigger alerts. For example, inactive accounts are automatically suspended after a defined period. Salesforce’s flexible configuration allows automated responses to policy breaches, ensuring timely correction and maintaining security compliance.
Data Protection and Encryption Governance
Data protection forms a critical part of compliance. Salesforce supports field-level encryption and platform encryption features. Designers implement encryption policies to safeguard sensitive data at rest and in transit. They also define key management procedures aligned with compliance standards. Encryption governance ensures secure data handling throughout the identity lifecycle.
Consent and Privacy Management
Governance frameworks include managing user consent for data usage. Salesforce enables consent tracking through custom objects and records. Certified designers ensure users can grant, modify, or withdraw consent transparently. Privacy management reinforces user trust and meets regulatory expectations regarding personal data processing and disclosure.
Identity Governance in Multi-Org Architectures
Large enterprises often operate multiple Salesforce orgs under a single governance policy. Designers coordinate identity and access policies across all orgs to ensure consistency. Centralized policy management prevents misalignment and simplifies compliance reporting. Multi-org governance provides unified visibility while supporting the unique operational needs of each business unit.
Real-Time Governance Monitoring
Continuous monitoring ensures governance remains effective. Designers configure real-time alerts for events like privilege escalation, multiple failed logins, or permission changes. Monitoring dashboards provide instant insights into compliance status. This visibility enables organizations to respond rapidly to deviations, reducing the window of potential security exposure within Salesforce environments.
Identity Lifecycle Automation Tools
Automation tools streamline user lifecycle events. Salesforce integrates with external identity management platforms that handle provisioning and deactivation based on HR data. Designers define event-driven workflows that automatically reflect employment status changes. Automated lifecycle control prevents dormant accounts, ensures accurate access levels, and enhances compliance readiness.
Auditing Access Provisioning
Auditing provisioning ensures that user creation processes follow governance policies. Salesforce maintains records of when, how, and by whom accounts are created. Certified designers implement mechanisms for reviewing provisioning accuracy. Regular audits prevent misuse of elevated privileges and confirm that automated workflows operate according to compliance standards.
Governance in Role Transitions
Employees often change roles within organizations. Designers create governance policies ensuring permissions adjust promptly to reflect new responsibilities. Automation handles permission removal and assignment during transitions. This prevents access accumulation and maintains least privilege. Accurate role transition management supports compliance and minimizes risks associated with outdated permissions.
Deactivation and Termination Governance
When users leave the organization, prompt deactivation is essential. Governance policies dictate deactivation timelines and data handling procedures. Designers configure automated workflows that disable accounts and revoke tokens immediately. Proper deactivation prevents unauthorized post-employment access and maintains audit integrity by logging all account termination actions.
Governance Metrics and Key Performance Indicators
Effective governance programs use measurable indicators. Salesforce designers track metrics such as policy compliance rate, audit success rate, and access review completion. Key performance indicators help assess program efficiency and identify areas needing improvement. Regular measurement ensures governance remains aligned with organizational security objectives and evolving risks.
Collaboration Between Security and Compliance Teams
Governance requires cooperation between multiple departments. Designers coordinate with security, HR, and legal teams to align technical policies with organizational objectives. Collaboration ensures identity solutions address both operational and compliance needs. Unified efforts reduce conflict, improve efficiency, and create an integrated governance culture throughout the organization.
Continuous Improvement in Governance
Identity governance is an evolving process. Certified designers continuously evaluate policies, technologies, and practices to identify opportunities for improvement. Lessons from incidents, audits, and user feedback inform policy refinement. Continuous improvement ensures governance frameworks remain effective, adaptive, and aligned with emerging security and compliance trends.
Documentation in Governance Processes
Proper documentation ensures transparency and consistency. Designers maintain records of configurations, policies, and audit outcomes. Documentation supports training and compliance verification. In Salesforce environments, documentation extends to workflows, access structures, and integration mappings. Well-documented governance simplifies audits and preserves institutional knowledge for long-term management.
Compliance with Industry Standards
Organizations adopt industry standards for identity governance, such as ISO and NIST frameworks. Designers align Salesforce configurations with these standards to demonstrate maturity and reliability. Compliance fosters stakeholder confidence and simplifies integration with external systems adhering to similar standards. Standard alignment ensures global consistency in identity practices.
Governance Challenges and Mitigation Strategies
Governance challenges include balancing usability with control, managing policy exceptions, and addressing system complexity. Designers mitigate these issues by simplifying configurations, applying automation, and fostering user awareness. Regular reviews identify emerging risks and enable timely adjustments. Resilient governance frameworks adapt quickly while maintaining compliance and operational efficiency.
Incident Response and Governance
Governance extends to incident management processes. When identity-related breaches occur, designers ensure response procedures activate immediately. Audit logs and monitoring data help identify the root cause. Post-incident reviews contribute to policy updates and risk prevention. Effective incident governance ensures accountability and minimizes business impact from identity-related incidents.
Governance in Cloud and Hybrid Deployments
As organizations adopt hybrid architectures, governance becomes more distributed. Designers ensure consistent identity policies across cloud and on-premise environments. Centralized control and unified monitoring maintain compliance and simplify audit processes. Governance consistency across hybrid Salesforce implementations supports interoperability and enhances overall system resilience.
Future Trends in Identity Governance
The future of identity governance focuses on intelligent automation, adaptive policies, and decentralized identities. Blockchain-based verification and self-sovereign identity concepts are transforming governance models. Salesforce designers must adapt by embracing technologies that enhance transparency and security. Understanding these trends ensures readiness for evolving compliance and identity landscapes.
Continuous Certification Maintenance
Governance does not end with certification. Professionals maintain expertise by staying informed about Salesforce updates, evolving standards, and regulatory changes. Continuous learning ensures certified designers remain effective in implementing governance strategies. Ongoing education sustains the relevance of the Salesforce Certified Identity and Access Management Designer credential.
Advanced Architecture Scenarios and Real-World Design Strategies
Advanced identity architecture in Salesforce integrates security, scalability, and interoperability. Certified designers must understand how to apply theoretical knowledge to real-world business challenges. The Salesforce Certified Identity and Access Management Designer Exam assesses the ability to create designs that function efficiently in complex, multi-system environments while maintaining compliance and high performance.
The Role of Architecture Design in Identity Management
Architecture design defines how authentication, authorization, and identity synchronization interact across platforms. It connects business needs with technical configurations. In Salesforce, architecture decisions influence performance, user experience, and security resilience. Certified designers analyze organizational structures, data flows, and risk factors to develop identity architectures optimized for enterprise success.
Designing Scalable Identity Architectures
Scalability ensures identity systems handle growth in users and integrations. Designers build scalable Salesforce identity solutions using federated authentication, directory synchronization, and load-balanced infrastructure. Scalable architectures support high availability and consistent authentication speed under heavy demand. Effective scalability planning prevents performance degradation as organizations expand and user activity increases.
Designing Multi-Org Identity Strategies
Many enterprises use multiple Salesforce orgs for different business units or geographies. Designers develop unified authentication and access management across all orgs. They employ centralized identity providers, consistent My Domain configurations, and trust relationships. Multi-org strategies simplify administration, enhance user experience, and maintain compliance through standardized authentication mechanisms.
Centralized Authentication Across Enterprises
Centralized authentication improves security and reduces complexity by consolidating login systems. Designers integrate Salesforce with enterprise identity providers to achieve single sign-on. Centralization allows enforcement of uniform password, session, and multi-factor policies. It simplifies auditing and provides unified visibility into access patterns, ensuring compliance and operational efficiency across all systems.
Decentralized Authentication Models
In some scenarios, decentralized authentication suits regional or independent business operations. Designers configure local identity providers connected to Salesforce service providers. Decentralization enables autonomy while maintaining secure interoperability. Each identity provider enforces its policies while participating in shared governance frameworks. This model supports flexible architectures aligned with diverse business requirements.
Architecture for Federated Organizations
Federated organizations require identity architectures that connect multiple independent systems under a shared trust framework. Designers define trust relationships, federation metadata, and standardized authentication protocols. Federated architectures enable collaboration while preserving organizational boundaries. Salesforce supports federation through SAML and OpenID Connect configurations tailored to complex enterprise and partner ecosystems.
Multi-Factor Authentication in Complex Architectures
Multi-factor authentication adds a crucial security layer to advanced identity architectures. Designers ensure seamless integration of MFA within federated and single sign-on systems. Salesforce supports adaptive MFA policies that evaluate risk context before requiring verification. Properly architected MFA maintains security without interrupting usability, even across multiple connected identity providers.
Identity Propagation in Enterprise Integrations
Identity propagation allows secure transmission of authenticated user identities across integrated systems. Designers ensure tokens and assertions maintain user context throughout workflows. In Salesforce, identity propagation supports API-based automation, external app access, and partner portal authentication. Consistent propagation ensures traceability and compliance by maintaining auditability across connected platforms.
Token Management Architecture
Token management governs how access and refresh tokens are generated, validated, and revoked. Designers establish token policies based on session sensitivity and security requirements. Salesforce supports token management through OAuth configurations and revocation endpoints. Proper design prevents token reuse, enforces expiration, and ensures consistent authentication performance under varying load conditions.
Architecture for External Partner Access
External partners often require controlled access to Salesforce environments. Designers develop architectures using partner community licenses, SAML federation, and role-based access. External access designs balance collaboration with data security. By defining partner-specific policies, organizations maintain visibility and compliance while offering efficient, secure access for trusted third parties.
Architecture for Customer Identity Management
Customer identity management architectures support large-scale user bases for portals and applications. Designers configure Salesforce Experience Cloud for seamless registration, authentication, and profile management. Identity providers handle authentication, while Salesforce stores user data securely. Proper architecture enables scalability, compliance, and a frictionless customer experience through personalized, secure access channels.
Cross-System Identity Synchronization
Synchronization ensures consistency between identity systems and Salesforce. Designers implement synchronization using APIs, identity connectors, and event-driven automation. Bidirectional synchronization keeps user data accurate and prevents identity drift. Proper synchronization maintains attribute alignment, supports lifecycle management, and reduces operational overhead in complex, multi-platform identity ecosystems.
Hybrid Identity Architecture
Hybrid identity combines cloud and on-premise authentication. Designers integrate Salesforce with legacy directories through secure gateways. Hybrid architectures support gradual cloud adoption while retaining compliance with existing infrastructure. They ensure consistent policy enforcement, data protection, and user experience across environments. Hybrid models are common in regulated or transition-phase organizations.
Architecture for API Access Management
APIs require secure authentication independent of user sessions. Designers implement OAuth-based token flows to manage API authorization between Salesforce and external applications. API access management includes defining scopes, client credentials, and expiration rules. Effective architecture ensures APIs operate securely, preventing unauthorized integration while enabling scalable automation.
Architecture for Mobile Access
Mobile access introduces unique challenges such as token storage and network security. Designers integrate Salesforce mobile applications with identity providers using OAuth and OpenID Connect. Mobile architectures include offline access considerations and adaptive MFA. By designing secure mobile authentication flows, organizations maintain protection without sacrificing user convenience or performance.
Architecture for High Availability
High availability ensures authentication remains uninterrupted during failures. Designers deploy redundant identity provider instances, backup certificates, and failover routing. Salesforce supports high availability through reliable metadata and load-balanced federation endpoints. Proper architecture minimizes downtime and guarantees users can always access Salesforce even when certain services become temporarily unavailable.
Architecture for Disaster Recovery
Disaster recovery planning preserves authentication continuity during crises. Designers establish secondary identity environments that replicate configuration and trust relationships. Recovery procedures include certificate backups and revalidation strategies. Salesforce architectures must define recovery timelines and test them periodically. Robust disaster recovery planning minimizes business disruption and data loss risks.
Designing Identity Security Architecture
Security architecture defines protection measures at every authentication layer. Designers implement encryption, certificate management, and access control mechanisms. Salesforce identity architecture incorporates secure protocols, key rotation, and policy enforcement. A layered security approach mitigates threats such as token theft, replay attacks, and unauthorized access attempts across enterprise integrations.
Authentication Flow Optimization
Optimizing authentication flows improves user experience and system efficiency. Designers reduce redirects, optimize token exchanges, and configure appropriate caching. Salesforce supports streamlined login flows that balance speed and security. Optimization reduces latency while preserving strong security controls, providing fast and reliable access for all authenticated sessions.
Integrating Salesforce with Multiple Identity Providers
Enterprises often use multiple identity providers across business divisions. Designers configure Salesforce to integrate with all providers using metadata and conditional routing. This allows users to authenticate through their regional or departmental systems. Multi-provider integration offers flexibility while maintaining central governance and visibility into authentication activities.
Architecture for Conditional Access
Conditional access enforces authentication based on contextual factors such as device, location, or risk level. Designers use Salesforce policies to evaluate login conditions before granting access. Conditional access enhances security by adapting dynamically to risk. This model prevents unauthorized connections from unrecognized environments while supporting legitimate flexible access for trusted users.
Architecture for Delegated Administration
Delegated administration allows localized management without compromising overall governance. Designers architect delegated models where business units manage user access within defined boundaries. In Salesforce, delegated administration uses specific roles and permissions. Proper design empowers teams while preserving compliance and minimizing centralized administrative load across large organizations.
Integration with Third-Party Security Tools
Salesforce identity architectures often connect with third-party tools for monitoring, analytics, and enforcement. Designers ensure secure integration with tools that manage events, detect anomalies, or analyze authentication patterns. Integration enhances visibility and automation in governance workflows. Secure data exchange maintains system integrity and improves response efficiency to potential threats.
Data Residency and Regional Authentication
Global organizations face regional data residency requirements. Designers plan authentication architectures that comply with regional data handling laws. Salesforce configurations ensure that user data and authentication logs remain within approved jurisdictions. Data residency alignment protects privacy and maintains legal compliance across international identity architectures.
Architecture for External Identity Broker Integration
An identity broker simplifies connections between multiple identity providers and Salesforce. Designers configure brokers to route authentication requests securely. Brokers manage complexity in environments with diverse identity systems. This architecture centralizes control while allowing flexibility in connecting varied protocols and identity sources across an enterprise ecosystem.
Designing for Performance Optimization
Performance optimization ensures identity systems operate efficiently under load. Designers use caching, connection pooling, and lightweight token flows. Salesforce performance tuning includes optimizing federation endpoints and managing session durations. Efficient architecture minimizes latency, ensures reliable authentication, and improves user satisfaction during high-traffic operations across business-critical environments.
Zero Trust Architecture in Salesforce
Zero trust models eliminate implicit trust between systems. Designers create architectures where every access request is verified continuously. Salesforce supports zero trust principles through strong authentication, conditional access, and session monitoring. Zero trust design reduces internal and external threats, ensuring access is always verified based on context and intent.
Adaptive Authentication Strategies
Adaptive authentication adjusts security requirements based on real-time context. Designers integrate Salesforce with systems that evaluate behavior, device posture, and location. Risk-based decisions enforce stronger controls when anomalies appear. Adaptive strategies protect users while minimizing friction, ensuring a balance between security strength and usability in complex environments.
Designing Secure Integration with APIs and Web Services
Secure integration ensures that APIs and web services use proper authentication flows. Designers define trust relationships and enforce token scopes between Salesforce and external endpoints. API gateways handle traffic inspection and rate limiting. A secure integration design prevents data leaks, supports governance, and maintains traceable, auditable interactions across systems.
Identity Architecture for Mergers and Acquisitions
When organizations merge, identity systems must integrate without disrupting access. Designers architect unified authentication by connecting separate identity providers through federation. They synchronize user attributes and standardize policies. This approach maintains business continuity while ensuring compliance. Mergers demand flexible, well-documented identity architectures that adapt to new organizational structures efficiently.
Role of Monitoring and Analytics in Advanced Architecture
Monitoring provides insights into identity architecture performance. Designers implement analytics to track login trends, token usage, and session durations. Salesforce analytics tools help identify bottlenecks or suspicious patterns. Continuous monitoring ensures architectures remain optimized and secure. Analytics also informs capacity planning and enhances predictive governance strategies.
Architecture Governance and Documentation
Every advanced architecture requires governance and documentation. Designers document configurations, integration points, and trust relationships. Governance ensures all changes follow approval workflows. Comprehensive documentation assists in audits, troubleshooting, and scalability. Consistent architectural documentation promotes transparency, reduces dependency on individuals, and supports long-term identity management stability.
Testing and Validation of Identity Architectures
Testing validates architecture functionality before deployment. Designers simulate authentication flows, failure scenarios, and recovery events. Validation ensures configurations meet design goals for security and performance. Salesforce testing environments enable safe verification of identity integrations. Rigorous testing prevents production issues and guarantees reliable operation under varied conditions.
Real-World Case Studies and Applications
In real-world enterprises, identity architecture supports global operations and multiple applications. Designers apply standardized frameworks that connect Salesforce with external identity providers, directories, and partner networks. These case studies highlight the need for flexible, secure, and compliant architectures capable of supporting millions of users without sacrificing governance or performance.
Common Pitfalls in Advanced Design
Complex identity architectures risk misconfiguration, token mismanagement, and integration failure. Designers avoid pitfalls through structured planning, documentation, and periodic review. Testing updates before deployment prevents disruptions. Understanding dependency chains between systems ensures stability. Awareness of common issues strengthens reliability and resilience in advanced Salesforce identity implementations.
Continuous Optimization and Maintenance
Identity architectures evolve with technology and business needs. Designers regularly review configurations, monitor performance, and update integrations. Continuous optimization ensures scalability and compliance remain intact. Regular certificate renewal, metadata refresh, and protocol updates preserve reliability. Proactive maintenance prevents downtime and enhances long-term sustainability in enterprise identity ecosystems.
Future of Advanced Identity Architecture
The future of Salesforce identity architecture includes decentralized identity, passwordless authentication, and biometric security. Blockchain-based verifiable credentials and AI-driven risk scoring will redefine identity verification. Designers must adapt to these innovations while maintaining compatibility with legacy systems. Staying current ensures Salesforce identity environments remain secure, agile, and future-ready.
Preparing for the Salesforce Certified Identity and Access Management Designer Exam
Preparation for advanced topics requires practical experience with multi-org setups, federation, and API integrations. Candidates should study architecture patterns and understand trade-offs between performance, scalability, and security. Reviewing complex case studies builds critical thinking for real-world design scenarios. The exam tests not only knowledge but also design judgment and architectural reasoning.
Maintaining Expertise After Certification
Certification marks the beginning of continued professional development. Designers maintain expertise by following Salesforce releases, new security trends, and evolving identity standards. Engaging in continuous learning ensures relevance and adaptability. Ongoing practice in real-world projects refines architectural skills, maintaining the designer’s value as an enterprise identity expert.
Final Thoughts
Advanced identity architecture represents the highest level of expertise required for the Salesforce Certified Identity and Access Management Designer Exam. It integrates governance, scalability, and innovation into cohesive solutions. Certified designers who master these advanced design strategies can lead organizations in implementing secure, efficient, and future-proof Salesforce identity ecosystems across global enterprises.
Salesforce Certified Identity and Access Management Designer practice test questions and answers, training course, study guide are uploaded in ETE Files format by real users. Study and Pass Certified Identity and Access Management Designer Certified Identity and Access Management Designer certification exam dumps & practice test questions and answers are to help students.
- Certified Agentforce Specialist
- Certified Data Cloud Consultant
- Certified Integration Architect
- Certified Service Cloud Consultant - Salesforce Certified Service Cloud Consultant
- Certified Platform App Builder
- Certified Platform Developer II
- Certified Sharing and Visibility Architect
- Certified Development Lifecycle and Deployment Architect
- Certified Business Analyst
- Certified Platform Developer
- Certified Data Architect
- Certified Tableau Desktop Foundations
- Certified Sales Cloud Consultant
- Certified Advanced Administrator
- Certified MuleSoft Developer I
- ADM-201 - Administration Essentials for New Admins
- Certified Marketing Cloud Email Specialist
- Certified Marketing Cloud Administrator
- Certified Experience Cloud Consultant
- CRT-450 - Salesforce Certified Platform Developer I
- Certified Tableau Data Analyst
- Field Service Consultant
- Certified Marketing Cloud Consultant
- Certified OmniStudio Consultant
- Certified Identity and Access Management Designer
- Health Cloud Accredited Professional
- Field Service Lightning Consultant
- Certified Associate
- Certified AI Associate
- Certified User Experience Designer
- Certified Tableau CRM and Einstein Discovery Consultant
- Certified AI Specialist
- Financial Services Cloud Accredited Professional
- Certified OmniStudio Developer
- Certified MuleSoft Integration Architect I - Salesforce Certified MuleSoft Integration Architect I
- Certified Sharing and Visibility Designer
- Certified Marketing Cloud Account Engagement Specialist
- Certified Platform Administrator II
- CRM Analytics and Einstein Discovery Consultant - Certified CRM Analytics and Einstein Discovery Consultant
Why customers love us?
What do our customers say?
The resources provided for the Salesforce certification exam were exceptional. The exam dumps and video courses offered clear and concise explanations of each topic. I felt thoroughly prepared for the Certified Identity and Access Management Designer test and passed with ease.
Studying for the Salesforce certification exam was a breeze with the comprehensive materials from this site. The detailed study guides and accurate exam dumps helped me understand every concept. I aced the Certified Identity and Access Management Designer exam on my first try!
I was impressed with the quality of the Certified Identity and Access Management Designer preparation materials for the Salesforce certification exam. The video courses were engaging, and the study guides covered all the essential topics. These resources made a significant difference in my study routine and overall performance. I went into the exam feeling confident and well-prepared.
The Certified Identity and Access Management Designer materials for the Salesforce certification exam were invaluable. They provided detailed, concise explanations for each topic, helping me grasp the entire syllabus. After studying with these resources, I was able to tackle the final test questions confidently and successfully.
Thanks to the comprehensive study guides and video courses, I aced the Certified Identity and Access Management Designer exam. The exam dumps were spot on and helped me understand the types of questions to expect. The certification exam was much less intimidating thanks to their excellent prep materials. So, I highly recommend their services for anyone preparing for this certification exam.
Achieving my Salesforce certification was a seamless experience. The detailed study guide and practice questions ensured I was fully prepared for Certified Identity and Access Management Designer. The customer support was responsive and helpful throughout my journey. Highly recommend their services for anyone preparing for their certification test.
I couldn't be happier with my certification results! The study materials were comprehensive and easy to understand, making my preparation for the Certified Identity and Access Management Designer stress-free. Using these resources, I was able to pass my exam on the first attempt. They are a must-have for anyone serious about advancing their career.
The practice exams were incredibly helpful in familiarizing me with the actual test format. I felt confident and well-prepared going into my Certified Identity and Access Management Designer certification exam. The support and guidance provided were top-notch. I couldn't have obtained my Salesforce certification without these amazing tools!
The materials provided for the Certified Identity and Access Management Designer were comprehensive and very well-structured. The practice tests were particularly useful in building my confidence and understanding the exam format. After using these materials, I felt well-prepared and was able to solve all the questions on the final test with ease. Passing the certification exam was a huge relief! I feel much more competent in my role. Thank you!
The certification prep was excellent. The content was up-to-date and aligned perfectly with the exam requirements. I appreciated the clear explanations and real-world examples that made complex topics easier to grasp. I passed Certified Identity and Access Management Designer successfully. It was a game-changer for my career in IT!