- Home
- Citrix Certifications
- 1Y0-203 Citrix XenApp and XenDesktop 7.15 Administration Dumps
Pass Citrix CCA-V 1Y0-203 Exam in First Attempt Guaranteed!


1Y0-203 Premium File
- Premium File 132 Questions & Answers. Last Update: Jan 31, 2026
Whats Included:
- Latest Questions
- 100% Accurate Answers
- Fast Exam Updates
Last Week Results!
All Citrix CCA-V 1Y0-203 certification exam dumps, study guide, training courses are Prepared by industry experts. PrepAway's ETE files povide the 1Y0-203 Citrix XenApp and XenDesktop 7.15 Administration practice test questions and answers & exam dumps, study guide and training courses help you study and pass hassle-free!
Why Every Virtualization Professional Should Consider the Citrix 1Y0-203 Exam
Vendor certifications have become essential credentials distinguishing competent IT professionals from their peers in competitive employment markets. The Citrix 1Y0-203 exam validates specialized knowledge in XenApp and XenDesktop 7.15 administration, demonstrating to employers that candidates possess verified skills managing enterprise virtualization infrastructure. This certification proves particularly valuable as organizations increasingly rely on virtual desktop infrastructure and application virtualization for business continuity, remote work enablement, and centralized IT management. Certification achievement signals dedication to professional development and mastery of complex virtualization technologies that organizations depend upon for operational efficiency.
The credential provides tangible evidence of expertise that resume claims alone cannot substantiate, giving certified professionals competitive advantages during hiring processes and promotion considerations. Similar to how structured preparation approaches benefit professionals pursuing CISSP training roadmaps, Citrix certification requires systematic study and hands-on experience. Organizations investing in Citrix infrastructure specifically seek professionals with validated credentials ensuring they possess necessary knowledge for deployment, configuration, and troubleshooting. The certification opens doors to specialized roles including Citrix administrator, VDI engineer, and desktop virtualization specialist positions commanding premium compensation compared to generalist IT support roles.
Market Demand Dynamics for Virtualization Specialists
The virtualization market continues expanding as organizations embrace flexible work arrangements requiring remote access to corporate applications and desktops. Healthcare, financial services, education, and government sectors particularly depend on secure remote access solutions that Citrix technologies provide. Market research indicates sustained demand for virtualization specialists as legacy on-premises infrastructure migrates toward cloud-hosted virtual desktop solutions. Organizations implementing or maintaining Citrix environments require skilled professionals who can optimize performance, troubleshoot issues, and ensure security compliance across distributed virtual infrastructure.
Geographic location significantly influences demand patterns with major metropolitan areas and technology hubs offering more opportunities than rural regions. Career prospects similar to those emerging in cybersecurity's lucrative UK future demonstrate how specialized IT skills command premium compensation. Remote work normalization has partially decoupled geographic constraints from employment opportunities, enabling certified professionals to access positions across broader markets. Contract and consulting opportunities abound for experienced Citrix professionals as organizations undertake migration projects, capacity expansions, or optimization initiatives requiring temporary specialized expertise. The certification provides the foundation for pursuing these varied career pathways serving organizations at different virtualization maturity stages.
XenApp and XenDesktop Architecture Fundamentals
Understanding Citrix architecture represents core competency that the 1Y0-203 exam thoroughly assesses across multiple knowledge domains. XenApp delivers virtualized applications to endpoints without requiring full desktop deployments, enabling centralized application management and version control. XenDesktop provides complete virtual desktop experiences accessed from various endpoint types including thin clients, personal computers, or mobile devices. The architecture includes components like delivery controllers managing connections, StoreFront providing user interfaces for resource access, and Citrix Receiver client software enabling endpoint connectivity.
Database infrastructure stores site configuration and session information requiring high availability for production environments. Learning pathways comparable to GIAC certification journeys emphasize systematic knowledge development applicable to mastering Citrix architecture. Virtual Delivery Agent software installed on master images enables server-hosted or desktop-hosted resources to register with delivery controllers. Citrix policies control user experience settings, security configurations, and performance optimizations. Understanding how these architectural components interact enables administrators to troubleshoot issues, optimize performance, and design scalable deployments. The exam tests both theoretical architecture knowledge and practical application through scenario-based questions requiring candidates to select appropriate architectural decisions for specific business requirements.
Installation and Configuration Best Practices
Proper installation and configuration establish foundations for reliable, performant Citrix environments serving organizational productivity needs. Site creation defines administrative boundaries and database connections establishing management infrastructure. Delivery controller installation requires Windows Server operating systems meeting specific prerequisites including proper domain membership and service account configuration. StoreFront deployment provides users with access to published resources through web interfaces or Citrix Workspace applications. License server installation and configuration ensures compliance with Citrix licensing requirements and enables feature activation.
Machine catalog creation organizes virtual machines or physical computers into groups sharing common characteristics and management policies. Certification difficulty levels comparable to toughest cybersecurity credentials from CISSP onward demonstrate varied complexity across IT certifications. Delivery group configuration assigns users or groups to machine catalogs defining which resources users can access. Published application configuration makes applications available through XenApp without full desktop delivery. Connection policies optimize network bandwidth consumption and user experience based on connection types. The exam evaluates knowledge of proper installation sequences, prerequisite requirements, and configuration best practices ensuring candidates can implement production-ready environments following Citrix recommendations.
User Experience Optimization Through Citrix Policies
Citrix policies provide granular control over user sessions, application behavior, and resource consumption enabling administrators to balance performance, security, and user satisfaction. HDX policies optimize high-definition experience protocol settings controlling display quality, multimedia redirection, and peripheral device access. Bandwidth policies limit network consumption preventing individual sessions from degrading performance for other users. Printing policies control printer mapping, driver delivery, and print job routing addressing common user productivity requirements. Profile management policies control how user settings persist across sessions and machines maintaining consistent personalized experiences.
Security policies enforce encryption levels, authentication requirements, and session timeouts protecting organizational data from unauthorized access. Career development through certifications like GSEC passes starting cybersecurity parallels how Citrix credentials advance virtualization careers. Policy precedence rules determine which settings apply when multiple policies affect the same configuration area requiring administrators to understand priority evaluation. Template policies provide starting configurations for common scenarios that administrators customize for specific organizational requirements. The exam tests policy configuration knowledge, troubleshooting skills when policies conflict or fail to apply, and understanding of how policies affect user experiences and system performance.
Monitoring and Troubleshooting Production Environments
Proactive monitoring and efficient troubleshooting maintain user productivity and prevent minor issues from escalating into major outages. Director console provides real-time visibility into user sessions, application performance, and infrastructure health. Historical reporting identifies trends in resource consumption, connection patterns, and user experience metrics informing capacity planning decisions. Alert configuration notifies administrators about critical conditions requiring immediate attention including service failures, resource exhaustion, or connectivity problems. Log file analysis using built-in tools or third-party solutions diagnoses complex issues that monitoring dashboards cannot immediately identify.
Performance baseline establishment enables detection of degradation indicating problems requiring investigation. Industrial security domains covered in ICS410 certification guides demonstrate how specialized certifications address specific IT sectors similarly to Citrix expertise. Session troubleshooting resolves individual user connectivity problems, application launch failures, or performance complaints through systematic diagnostic procedures. Network troubleshooting identifies bandwidth constraints, latency issues, or connectivity interruptions affecting user experiences. The exam evaluates candidates' abilities to interpret monitoring data, diagnose root causes from symptoms, and implement appropriate remediation steps restoring service quickly while preventing recurrence through permanent fixes.
High Availability and Disaster Recovery Implementations
Enterprise Citrix deployments require robust high availability and disaster recovery capabilities ensuring business continuity during component failures or site disasters. Database mirroring or Always On availability groups protect site configuration databases from single server failures. Multiple delivery controllers provide redundancy eliminating single points of failure in connection brokering infrastructure. StoreFront server groups enable load balancing and failover for user authentication and resource enumeration. Zone preference configuration directs users to resources in specific geographic zones reducing latency while providing failover to alternate zones during outages.
Backup procedures protect virtual machine master images, site databases, and configuration settings enabling recovery from various failure scenarios. Exam preparation strategies similar to EC-Council CEH expert insights emphasize practical application knowledge applicable to Citrix certification. Disaster recovery planning documents recovery procedures, defines recovery time objectives, and establishes testing schedules validating preparedness. Site-to-site replication synchronizes configuration between geographically separated data centers enabling failover during regional disasters. The exam assesses understanding of high availability architecture options, implementation procedures, and testing methodologies ensuring certified professionals can design and implement resilient infrastructures supporting business requirements for uptime and data protection.
Security Considerations for Virtual Desktop Infrastructure
Security represents critical concern for virtual desktop infrastructure exposing organizational resources to remote access across untrusted networks. Multi-factor authentication strengthens access security beyond simple username and password combinations reducing credential compromise risks. Network segmentation isolates virtual desktop traffic from production networks limiting lateral movement during security breaches. Encryption protects data in transit between endpoints and Citrix infrastructure preventing interception of sensitive information. Session recording captures user activities supporting compliance requirements and security investigations when policy violations or data theft occur.
Access control policies restrict which users can access specific resources based on factors including group membership, device posture, or geographic location. Career paths into ethical hacking through CEH certification foundations demonstrate how security expertise complements infrastructure knowledge. SmartAccess and SmartControl features enforce dynamic access policies based on real-time conditions. Antivirus integration and endpoint analysis ensure connecting devices meet security standards before granting resource access. The exam covers security architecture design, policy implementation, and compliance frameworks applicable to healthcare, financial services, and government sectors with stringent regulatory requirements protecting sensitive data accessed through virtual desktop infrastructure.
Integration With Hypervisor and Cloud Platforms
Citrix XenApp and XenDesktop integrate with various hypervisor platforms and cloud providers enabling flexible deployment options matching organizational infrastructure strategies. VMware vSphere integration enables virtual machine lifecycle management through Citrix Studio including provisioning, power management, and snapshot operations. Microsoft Hyper-V support provides similar capabilities for organizations standardized on Microsoft virtualization infrastructure. Citrix Hypervisor (formerly XenServer) offers tightly integrated hypervisor purpose-built for Citrix workloads. Machine Creation Services automates virtual machine provisioning from master images using hypervisor native cloning capabilities.
Provisioning Services provides alternative provisioning method streaming virtual disk images from centralized servers rather than storing full copies on hypervisor storage. Vendor ecosystem developments like Fortinet news and vendor updates demonstrate how IT landscapes continuously evolve requiring professional adaptability. Azure and AWS integration enables cloud-hosted virtual desktops reducing on-premises infrastructure requirements. Hybrid cloud architectures combine on-premises and cloud resources providing flexibility, disaster recovery, and burst capacity during demand spikes. The exam evaluates knowledge of hypervisor integration requirements, provisioning technology trade-offs, and hybrid cloud architectural patterns enabling candidates to recommend appropriate infrastructure approaches for varied organizational requirements and constraints.
Licensing Models and Cost Optimization Strategies
Understanding Citrix licensing models enables organizations to optimize costs while maintaining compliance with vendor requirements. Concurrent user licensing charges based on simultaneous active users rather than total named users potentially reducing costs in shift work environments. Named user licensing assigns licenses to specific individuals regardless of simultaneous usage appropriate for organizations where most users access systems regularly. User/Device licensing provides flexibility allowing organizations to license either users or devices depending on which model yields better economics. Virtual Desktop Infrastructure licensing requires separate licenses beyond XenApp and XenDesktop depending on hosted operating systems and Microsoft licensing terms.
License server configuration tracks license consumption ensuring organizations remain within purchased entitlements. Content discovery methods using Google Translate for global ideas demonstrate creative approaches applicable to researching optimization strategies. License usage reporting identifies over-provisioning or consumption patterns suggesting opportunities for license pool adjustments. Subscription licensing provides OpEx financial models versus traditional CapEx purchases. Cloud services licensing differs from on-premises models requiring understanding when evaluating deployment options. The exam covers licensing concepts, compliance requirements, and cost optimization approaches ensuring certified professionals can advise organizations about appropriate licensing strategies matching usage patterns and budget constraints.
Application Delivery and Optimization Techniques
Efficient application delivery represents core XenApp value proposition enabling centralized management while providing user experiences comparable to locally installed applications. Application publishing makes Windows applications available through XenApp without full desktop delivery reducing resource consumption. Seamless windows mode presents applications in individual windows on user desktops rather than within published desktop sessions. Application streaming delivers applications on-demand caching components locally for offline use. Profile management solutions persist user settings, application preferences, and data across sessions and machines.
Application layering separates applications from base images enabling flexible application combinations without maintaining numerous master images. Risk management certifications like ISACA CRISC exam coverage demonstrate how specialized credentials address specific IT domains. Folder redirection centralizes user data on network storage protecting against data loss and enabling access from multiple machines. HDX MediaStream optimization offloads multimedia processing to endpoints reducing server resource consumption. App-V integration enables Microsoft application virtualization alongside Citrix infrastructure. The exam assesses application delivery configuration knowledge, optimization techniques reducing resource consumption, and troubleshooting skills addressing common application delivery challenges ensuring users receive productive experiences.
Profile Management Solutions for User Personalization
Profile management ensures users receive consistent personalized experiences across sessions and machines without consuming excessive storage or impacting logon performance. Citrix Profile Management synchronizes user settings between sessions storing profiles on centralized network shares. Profile streaming loads profile components on-demand rather than copying entire profiles during logon reducing logon times. Active write-back immediately saves changed settings rather than waiting until logoff preventing data loss from unexpected disconnections. Folder redirection moves special folders including documents and desktop to network storage separating data from profiles.
Large file handling prevents profile bloat from oversized files corrupting profiles or consuming storage. Compliance foundations through CAMS exam approaches show how certifications validate specialized competencies. Cross-platform profile support maintains consistent experiences across Windows and non-Windows endpoints. Profile cleanup policies automatically remove stale or unused profiles freeing storage space. The exam covers profile management architecture, configuration best practices, and troubleshooting common profile issues including corruption, slow logons, or settings that fail to persist properly ensuring certified professionals can implement solutions balancing user experience, storage consumption, and administrative overhead.
Director Analytics for Performance Insights
Director provides comprehensive analytics and monitoring capabilities enabling data-driven optimization decisions and proactive issue identification. Real-time session monitoring displays active users, connected endpoints, resource consumption, and application usage. Historical reporting reveals trends in user adoption, peak usage periods, and resource utilization informing capacity planning. User experience scoring quantifies session quality through metrics including logon duration, application launch times, and session responsiveness. Alert configuration notifies administrators about conditions requiring attention including failed logons, server crashes, or license exhaustion.
Failure tracking identifies recurring problems enabling prioritization of remediation efforts with greatest user impact. Process improvement methodologies like agile retrospectives in business parallel how Director analytics drive continuous optimization. Trending analysis compares current performance against baselines detecting degradation indicating emerging problems. Session recording playback recreates user sessions supporting troubleshooting and security investigations. The exam evaluates Director navigation knowledge, interpretation of monitoring data, and ability to translate analytics into actionable optimization recommendations ensuring certified professionals can leverage Director capabilities maximizing infrastructure value and user satisfaction.
Machine Creation Services Versus Provisioning Services
Organizations deploying Citrix environments must choose between Machine Creation Services and Provisioning Services for virtual desktop provisioning with significant operational implications. Machine Creation Services uses hypervisor cloning creating full virtual machine copies from master images consuming storage proportional to deployed desktop count. Fast cloning and linked clones reduce storage through differential disks sharing common base images. Provisioning Services streams virtual disk images from centralized servers to target devices requiring minimal hypervisor storage. Write cache handling options include writing to RAM, local disk, or dedicated cache storage affecting performance and persistence.
Machine catalog creation differs between technologies affecting deployment procedures and management workflows. Virtualization mastery through VMware 2V0-21-23 data center expertise demonstrates how platform-specific skills advance infrastructure careers. Provisioning Services requires additional infrastructure including streaming servers and database servers. Machine Creation Services integrates more tightly with hypervisor management platforms. Provisioning Services enables larger deployments with reduced storage costs. The exam assesses understanding of provisioning technology trade-offs, appropriate use cases for each approach, and implementation procedures ensuring candidates can recommend and deploy optimal solutions for specific organizational requirements balancing storage costs, management complexity, and operational considerations.
User Session Management and Policies
User session management controls how users connect, what resources they access, and how sessions behave addressing varied use cases and security requirements. Session timeout policies automatically disconnect idle sessions freeing resources and improving security. Session limits restrict multiple concurrent sessions per user preventing unintended resource consumption. Reconnection policies define whether users connect to existing disconnected sessions or start new sessions. Session reliability maintains connectivity during brief network interruptions preventing unnecessary session terminations from temporary connectivity issues.
Published desktop sessions provide full Windows desktop experiences while published application sessions deliver specific applications. Marketing insights from Netflix's winning strategies demonstrate how understanding user behavior drives optimization applicable to session management. Pre-launch applications start frequently used applications before users request them, reducing launch delays. Session sharing enables multiple published applications to run within a single session reducing resource consumption. The exam covers session policy configuration, behavior customization for different user groups, and troubleshooting session management issues ensuring certified professionals can implement session management strategies optimizing resource utilization while meeting user requirements for flexibility and responsiveness.
Preparing Effectively for Certification Examination
Successful certification achievement requires strategic preparation combining multiple learning approaches and realistic time allocation. Official Citrix training courses provide structured learning paths covering all exam objectives through instructor-led or self-paced formats. Hands-on laboratory experience proves essential for developing practical skills that reading alone cannot provide. Trial environments or home labs enable experimentation with configurations, troubleshooting scenarios, and feature exploration without affecting production systems. Practice examinations familiarize candidates with question formats, time management requirements, and knowledge areas requiring additional study.
Study materials including official courseware, documentation, community forums, and video training complement practical experience. Test-taking strategies like ACT and SAT retaking considerations emphasize learning from previous attempts applicable to certification exams. Study groups provide peer support and knowledge sharing accelerating learning through collaborative problem-solving. Time management during preparation allocates consistent study periods over weeks or months rather than cramming immediately before examinations. The certification validates comprehensive knowledge across multiple domains requiring thorough preparation rather than focusing narrowly on specific topics ensuring certified professionals possess well-rounded capabilities supporting various administrative responsibilities.
Exam Structure and Assessment Methodology
Understanding examination structure and assessment methods enables effective preparation and confident test-taking performance. The 1Y0-203 exam typically contains approximately 65 questions administered over 90 minutes requiring efficient time management. Question formats include multiple choice, multiple response, drag-and-drop, and scenario-based questions testing practical knowledge application. Passing scores generally fall around 64 percent with exact thresholds varying based on exam version difficulty through statistical equating processes. Candidates receive immediate preliminary results upon completion with detailed score reports available through Citrix certification portals.
Exam domains include architecture, installation and configuration, user layer, delivery resources, applications, desktops, and troubleshooting, each weighted differently affecting study prioritization. Mathematical preparation resources like comprehensive ASVAB math guides demonstrate structured learning approaches applicable to technical certification preparation. Scenario-based questions present realistic administrative situations requiring candidates to select appropriate actions, configurations, or troubleshooting steps. Non-disclosure agreements prevent specific question sharing, maintaining exam integrity and ensuring certifications remain meaningful credentials. The examination measures both theoretical knowledge and practical application abilities ensuring certified professionals can effectively administer production Citrix environments addressing real business requirements and technical challenges.
Advanced Biological System Analysis for Complex Problem Solving
Complex problem-solving skills transfer across disciplines including analyzing intricate biological systems and troubleshooting sophisticated IT infrastructure. Systematic diagnostic approaches identify root causes rather than treating superficial symptoms. Understanding interconnected components and their relationships enables predicting failure modes and optimization opportunities. Data interpretation skills extract meaningful insights from monitoring metrics and performance indicators. Hypothesis-driven investigation tests potential explanations systematically eliminating incorrect theories.
Analytical methodologies from nervous system MCAT concepts demonstrate structured approaches applicable to infrastructure troubleshooting. Pattern recognition identifies recurring issues suggesting systemic problems requiring permanent solutions. Documentation practices capture troubleshooting procedures enabling knowledge transfer and process refinement. Critical thinking skills evaluate multiple solution options considering trade-offs and constraints. The 1Y0-203 exam tests analytical capabilities through scenario-based questions requiring systematic problem diagnosis and appropriate solution selection demonstrating that certified professionals possess cognitive skills necessary for effective infrastructure administration beyond mere memorization of technical facts.
Standardized Test Result Interpretation Skills
Interpreting assessment results enables continuous improvement whether analyzing standardized test scores or infrastructure performance metrics. Score reports identify strengths and weaknesses guiding focused improvement efforts. Percentile rankings contextualize individual performance against peer groups. Sub-score analysis reveals specific knowledge areas requiring additional development. Longitudinal tracking monitors progress over time validating learning effectiveness.
Assessment analysis techniques from PSAT results interpretation apply to certification exam score reports. Error pattern analysis identifies conceptual misunderstandings versus careless mistakes. Performance comparison against objectives determines readiness for advancement or need for remediation. Feedback integration drives targeted study adjustments optimizing preparation efficiency. The Citrix certification provides detailed score reports across exam domains enabling candidates who don't pass initially to identify specific knowledge gaps requiring additional study before retesting ensuring subsequent attempts focus on actual weaknesses rather than wasting time reviewing already-mastered content.
Written Communication Excellence in Technical Documentation
Written communication excellence proves essential for technical professionals documenting configurations, procedures, and troubleshooting guides. Clear technical writing conveys complex information to varied audiences including technical peers and non-technical stakeholders. Structured documentation follows logical organization enabling readers to quickly locate relevant information. Precise language eliminates ambiguity preventing misinterpretation that could lead to configuration errors. Grammar and mechanics proficiency ensures professional presentation reflecting well on authors and organizations.
Writing skills developed through SAT writing section mastery transfer to technical documentation contexts. Audience awareness adapts content complexity and terminology to reader technical sophistication. Visual communication supplements text through diagrams, screenshots, and flowcharts enhancing comprehension. Version control tracks documentation updates maintaining accuracy as environments evolve. The 1Y0-203 certification indirectly validates communication capabilities through scenario questions requiring candidates to interpret technical situations and select appropriate actions demonstrating that certified professionals can understand complex technical descriptions necessary for effective documentation creation and consumption.
Data Management Principles for Virtualization Professionals
Data management principles underpin effective virtual desktop infrastructure administration ensuring organizational information remains protected, accessible, and properly governed. Database administration skills support Citrix site databases storing configuration and session information requiring backup, monitoring, and occasional troubleshooting. SQL Server knowledge enables database optimization, troubleshooting connectivity issues, and implementing high availability through mirroring or Always On availability groups. Profile management strategies balance user personalization against storage consumption and logon performance requiring data lifecycle policies.
Application data redirection centralizes user-generated content on network storage protecting against data loss from virtual machine image updates. Certification frameworks through CDMP credential programs demonstrate how data expertise complements infrastructure administration. Storage optimization includes deduplication, compression, and tiering strategies reducing capacity requirements for large virtual desktop deployments. Backup integration protects critical data including site databases, master images, and user profiles enabling recovery from corruption or disasters. The 1Y0-203 exam addresses data protection concepts, profile management configurations, and database administration essentials ensuring certified professionals understand data aspects of Citrix infrastructure supporting business continuity and compliance requirements.
Revenue Operations and Certification Investment Returns
Certification investment analysis considers direct costs including examination fees, training materials, and preparation time against career benefits including salary increases and expanded opportunities. Examination fees typically range from $300 to $400 representing modest financial investment compared to degree programs or bootcamps. Preparation costs vary widely depending on chosen resources from free online materials to expensive instructor-led training courses. Time investment represents significant opportunity cost requiring weeks or months of study alongside employment or other commitments requiring careful time management and dedication.
Platform expertise through Certinia certification pathways parallels how specialized credentials advance specific careers. Return on investment manifests through various mechanisms including direct salary increases, promotion eligibility, consulting rate improvements, or employment opportunities requiring certification as minimum qualification. Market research indicates certified IT professionals earn premium compensation compared to non-certified peers with exact differentials varying by geography, experience, and specific technologies. Long-term returns include career flexibility, professional credibility, and continued relevance as virtualization evolves. Organizations also benefit from certified staff through improved implementation quality, reduced troubleshooting time, and better optimization outcomes potentially justifying employer sponsorship of certification pursuits.
Emerging Technology Integration Capabilities
Emerging technology integration skills position certified professionals for future career relevance as virtualization intersects with cloud computing, artificial intelligence, and automation trends. Cloud integration enables hybrid deployments combining on-premises and cloud-hosted virtual desktops providing flexibility and disaster recovery capabilities. Container technologies increasingly supplement or replace virtual machine-based deployments in specific scenarios requiring understanding of containerization concepts. Artificial intelligence applications including chatbots for user support or predictive analytics for capacity planning integrate with traditional infrastructure management.
Automation through PowerShell scripting, APIs, or orchestration platforms reduces manual administration enabling infrastructure scalability. Industry trend awareness through CertNexus certification programs demonstrates how professionals maintain currency with evolving technologies. Edge computing brings processing closer to users improving performance for distributed workforces. Internet of Things endpoints require secure access to corporate applications extending traditional endpoint support. The 1Y0-203 certification provides foundations in core virtualization concepts that extend into emerging technology contexts ensuring certified professionals can adapt as technology landscapes evolve rather than requiring complete reskilling when new paradigms emerge.
Fundraising Technology Applications in Nonprofit Sectors
Nonprofit organizations increasingly rely on virtual desktop infrastructure supporting distributed workforces while managing tight technology budgets. Remote access enables volunteers and staff to access donor databases, constituent relationship management systems, and fundraising applications from various locations. Centralized application delivery simplifies software licensing and updates for organizations lacking dedicated IT staff. Security features protect sensitive donor information addressing compliance requirements for data privacy regulations affecting nonprofit operations.
Cost optimization through resource sharing and infrastructure consolidation proves particularly valuable for budget-constrained organizations. Development sector expertise through CFRE certification credentials demonstrates how specialized knowledge serves specific industries. Cloud-hosted virtual desktops eliminate on-premises infrastructure reducing capital expenditure and ongoing maintenance costs. Donation processing, grant management, and fundraising event coordination applications benefit from anywhere access that virtual desktops enable. The 1Y0-203 exam covers technical concepts equally applicable across sectors with certified professionals bringing valuable expertise to nonprofit organizations implementing or optimizing virtual desktop infrastructure supporting their charitable missions.
Network Security Fundamentals for Virtual Infrastructure
Network security represents a critical component of comprehensive virtual desktop infrastructure protection requiring understanding beyond basic Citrix administration. Firewall configuration enables secure remote access while preventing unauthorized connections to infrastructure components. Virtual private network integration provides encrypted tunnels for remote users accessing virtual desktops across untrusted networks. Network segmentation isolates virtual desktop traffic from production networks limiting lateral movement during security breaches. Intrusion detection and prevention systems monitor network traffic identifying suspicious patterns indicating potential attacks.
Gateway services provide secure external access with SSL/TLS encryption, authentication, and endpoint analysis before granting resource access. Network security expertise through CheckPoint certification pathways complements Citrix knowledge creating comprehensive security administration capabilities. Traffic inspection analyzes encrypted sessions identifying malware, data exfiltration attempts, or policy violations. Quality of service configurations prioritize virtual desktop traffic ensuring acceptable performance during network congestion. The exam addresses network security concepts, gateway configuration, and secure access architectures ensuring certified professionals understand how Citrix infrastructure integrates with broader organizational security frameworks protecting sensitive data and maintaining regulatory compliance.
Fortinet Infrastructure Integration Scenarios
Fortinet network security appliances integrate with Citrix infrastructure providing defense-in-depth protection for virtual desktop environments. FortiGate firewalls control traffic between network segments, enforce security policies, and inspect encrypted traffic identifying threats. VPN concentrator functionality enables secure remote access with authentication integration supporting multi-factor verification. Application control identifies and manages application usage including virtual desktop protocols and published applications. Intrusion prevention detects and blocks attack traffic protecting infrastructure components and virtual desktops from exploitation attempts.
Web filtering prevents users from accessing malicious or inappropriate websites through virtual desktop sessions. Foundational security through Fortinet NSE4 credentials establishes enterprise protection competencies. SSL inspection decrypts, analyzes, and re-encrypts traffic ensuring security policies apply to encrypted virtual desktop sessions. Logging and reporting provide visibility into security events, policy violations, and traffic patterns supporting compliance and investigation. The 1Y0-203 exam does not specifically cover Fortinet products but certified Citrix professionals benefit from understanding how network security appliances integrate with virtual infrastructure creating comprehensive protection strategies combining Citrix native security features with enterprise security infrastructure.
Advanced Fortinet Security Administration
Advanced Fortinet security administration supports sophisticated protection requirements in enterprise virtual desktop deployments. FortiAnalyzer aggregates logs from multiple security appliances enabling centralized analysis, compliance reporting, and long-term retention. FortiManager provides centralized management for distributed FortiGate deployments ensuring consistent security policy application across branch offices and data centers. Security fabric integration coordinates multiple Fortinet products sharing threat intelligence and automating response actions. Advanced threat protection including sandboxing analyzes suspicious files before allowing transmission preventing zero-day exploits.
Authentication integration with Active Directory and multi-factor authentication platforms strengthens access security. Advanced security expertise through Fortinet NSE5 programs demonstrates sophisticated protection capabilities. High availability configurations ensure security infrastructure remains operational during component failures maintaining protection during outages. IPsec and SSL VPN implementations provide encrypted remote access with granular access controls. Certified Citrix professionals collaborating with security teams benefit from understanding advanced security concepts ensuring virtual desktop infrastructure designs incorporate appropriate protection mechanisms balancing security requirements against user productivity and performance considerations.
Network Security Specialist Implementations
Network security specialist implementations address sophisticated threats requiring deep expertise beyond basic firewall administration. SD-WAN integration optimizes application performance across distributed networks while maintaining security policy enforcement. Secure web gateway functionality protects users from web-based threats regardless of location. Cloud access security broker capabilities extend protection to SaaS applications complementing on-premises virtual desktop security. Zero trust network access implementations verify every connection regardless of source location replacing traditional perimeter-based security models.
Threat intelligence integration consumes indicators of compromise automatically updating protection rules defending against emerging threats. Specialist expertise through Fortinet NSE7 credentials validates advanced security administration capabilities. Security orchestration automates response workflows reducing time between threat detection and remediation. Microsegmentation isolates applications and workloads preventing lateral movement during breaches. Citrix professionals pursuing security specializations complement 1Y0-203 certification with security credentials creating comprehensive skillsets valuable for organizations implementing virtual desktop infrastructure within demanding security environments requiring sophisticated protection strategies addressing evolving threat landscapes.
Agile Project Management for Infrastructure Deployments
Agile project management methodologies increasingly apply to infrastructure projects including Citrix deployments replacing traditional waterfall approaches. Sprint planning breaks implementations into manageable increments delivering functional capabilities at regular intervals. Daily standups maintain team alignment, identify obstacles, and coordinate activities. Sprint retrospectives capture lessons learned continuously improving processes and practices. Product backlog management prioritizes features and configurations based on business value and dependencies.
User story creation defines requirements from user perspectives focusing on business outcomes rather than technical specifications. Agile principles through Certified ScrumMaster programs demonstrate how methodology expertise complements technical skills. Iterative deployment enables earlier value realization and faster feedback incorporation compared to big-bang implementations. Change management aligns with agile delivery adapting communications and training to incremental rollouts. The 1Y0-203 exam focuses on technical knowledge but certified professionals increasingly work within agile frameworks requiring understanding of how technical work fits within modern project delivery approaches emphasizing collaboration, flexibility, and continuous improvement over rigid sequential planning.
Digital Marketing Infrastructure Supporting Remote Teams
Digital marketing operations increasingly depend on virtual desktop infrastructure enabling distributed teams to access marketing automation platforms, content management systems, and analytics tools. Creative professionals require high-performance graphics capabilities that modern HDX technologies deliver through GPU virtualization or pass-through configurations. Collaboration tools integrate with virtual desktops enabling teams to share campaigns, review content, and coordinate activities. Data security protections prevent intellectual property theft or inadvertent disclosure of confidential marketing strategies through data loss prevention and session recording.
Campaign management platforms accessed through virtual desktops centralize marketing operations supporting compliance and audit requirements. Marketing expertise through Google AdWords certifications demonstrates how specialized platforms require technical support infrastructure. Version control and workflow management systems ensure marketing materials progress through proper approval processes. Analytics and reporting tools provide insights into campaign performance informing optimization decisions. Citrix professionals supporting marketing departments benefit from understanding unique requirements including graphics performance, collaboration needs, and security considerations protecting competitive marketing strategies ensuring infrastructure configurations enable rather than hinder marketing team productivity and creative processes.
Fortinet Gateway Deployment and Administration
Fortinet gateway deployment provides secure external access to Citrix environments through integrated authentication, encryption, and endpoint analysis. FortiGate SSL VPN delivers remote access with certificate-based or credential authentication integrating with Active Directory and multi-factor platforms. Web application firewall functionality protects StoreFront and other web-facing Citrix components from attacks. Traffic inspection analyzes virtual desktop protocol traffic identifying anomalies or threats. IPsec site-to-site VPN configurations connect branch offices to central Citrix deployments extending access across organizational networks.
Client provisioning automates VPN software distribution and configuration for remote users. Gateway administration through Fortinet FCP-FGT-AD-7.6 credentials validates specialized expertise. Single sign-on integration reduces authentication friction for users accessing resources through VPN connections. Policy-based routing directs traffic to appropriate resources based on source, destination, or application characteristics. Citrix professionals implementing secure remote access benefit from understanding FortiGate capabilities ensuring gateway configurations provide appropriate security, performance, and user experience balancing protection requirements against usability and administrative complexity supporting remote workforce productivity.
FortiManager Centralized Management Capabilities
FortiManager centralized management simplifies administration for organizations with multiple FortiGate deployments protecting distributed Citrix environments. Device management provides a single interface for configuring and monitoring multiple security appliances. Policy management enables consistent security rule application across all devices ensuring uniform protection. Firmware management coordinates updates reducing administrative burden of upgrading distributed infrastructure. Template configuration applies common settings to multiple devices reducing configuration effort and errors.
Script automation performs bulk operations or scheduled tasks improving efficiency. Centralized management expertise through Fortinet FCP-FMG-AD-7.4 programs demonstrates administration scalability knowledge. Workflow approval processes ensure changes undergo review before implementation preventing unauthorized modifications. Device grouping organizes appliances by location, function, or administrative responsibility enabling granular delegation. Citrix administrators managing security infrastructure supporting virtual desktop deployments benefit from FortiManager capabilities particularly in organizations with branch offices or data centers each requiring local security appliances necessitating centralized oversight ensuring consistent security posture across distributed infrastructure protecting virtual desktops and applications regardless of user location.
Advanced FortiManager Administration Techniques
Advanced FortiManager administration addresses sophisticated management requirements in complex distributed environments. Global database synchronization maintains configuration consistency across management domains. ADOM (Administrative Domain) implementation provides multi-tenancy isolating configurations for different organizations or business units. Automation through scripts and APIs enables integration with orchest ration platforms and custom workflows. Policy package management groups configurations enabling bulk deployment and revision control. Compliance reporting validates configurations against security standards identifying deviations requiring remediation.
Advanced administration skills through Fortinet FCP-FMG-AD-7.6 expertise validate sophisticated management capabilities. High availability clustering ensures management continuity during component failures. Backup and restore procedures protect configuration databases enabling recovery from corruption or disasters. Log aggregation from managed devices provides centralized visibility into security events across distributed infrastructure. Citrix professionals supporting geographically dispersed virtual desktop infrastructure benefit from advanced FortiManager capabilities enabling efficient management at scale ensuring security policies consistently apply across all locations protecting organizational assets while minimizing administrative overhead through automation and centralized control reducing human error and improving security posture.
FortiMail Email Security Integration
FortiMail email security integration protects organizations from email-borne threats targeting users accessing email through virtual desktops. Spam filtering blocks unsolicited messages reducing inbox clutter and productivity drains. Malware protection scans attachments identifying and quarantining malicious files before reaching users. Phishing detection analyzes email characteristics identifying social engineering attempts. Data loss prevention inspects outbound messages preventing inadvertent or malicious disclosure of sensitive information. Email encryption protects confidential communications meeting compliance requirements.
Email security expertise through Fortinet FCP-FML-AD-7.4 credentials demonstrates messaging protection knowledge. Sandboxing analyzes suspicious attachments in isolated environments before delivery, preventing zero-day exploits. Email archiving retains messages supporting compliance, legal discovery, and business continuity. High availability configurations ensure continuous email processing during component failures. Citrix professionals supporting virtual desktop environments benefit from understanding email security integration ensuring users accessing email through published applications or virtual desktops receive comprehensive protection against email threats which represent primary attack vectors for credential compromise, malware delivery, and data exfiltration attempts targeting organizational assets through user endpoints.
FortiSandbox Advanced Threat Detection
FortiSandbox advanced threat detection analyzes suspicious files in isolated environments identifying zero-day threats that signature-based detection cannot recognize. Behavioral analysis observes file execution detecting malicious activities including registry modifications, network connections, or process injection. Virtual machine environments simulate various operating systems and application configurations ensuring comprehensive analysis. Threat intelligence sharing distributes discovered indicators to other Fortinet products coordinating protection across security infrastructure.
Integration with email and web security appliances enables automatic suspicious file submission. Advanced threat capabilities through Fortinet FCP-FSM-AN-7.2 programs validate detection expertise. API integration enables custom applications to submit files for analysis. Forensic reports document observed behaviors supporting incident investigation and response. High-volume licensing accommodates organizations analyzing thousands of files daily. Citrix professionals supporting secure virtual desktop infrastructure benefit from sandboxing capabilities particularly when users download files from internet sources or receive email attachments requiring analysis before permitting access through virtual desktop sessions ensuring advanced threats receive appropriate scrutiny before reaching organizational networks or endpoints.
FortiWeb Application Protection for Citrix Services
FortiWeb application protection shields web-facing Citrix components including StoreFront from attacks targeting web application vulnerabilities. SQL injection detection prevents database manipulation through malicious input. Cross-site scripting protection blocks attempts to inject malicious scripts into web pages. XML protection validates API requests preventing attacks targeting programmatic interfaces. Bot mitigation distinguishes malicious automated traffic from legitimate users preventing credential stuffing and data scraping.
API security enforces authentication, rate limiting, and input validation for REST and SOAP endpoints. Application security through Fortinet FCP-FWB-AD-7.4 credentials validates protection expertise. Machine learning capabilities adapt to application-specific traffic patterns improving detection accuracy. Logging provides detailed attack visibility supporting security investigations and compliance reporting. Citrix administrators implementing secure external access benefit from FortiWeb capabilities protecting StoreFront and other web services from sophisticated application-layer attacks that traditional network security appliances cannot detect, ensuring authentication portals, resource enumeration interfaces, and management consoles remain protected against evolving attack techniques targeting web application vulnerabilities.
FortiWiFi Secure Wireless Access for Mobile Endpoints
FortiWiFi secure wireless access provides enterprise-grade wireless networks supporting mobile devices accessing Citrix virtual desktops. WPA3 encryption protects wireless communications from eavesdropping and unauthorized access. Certificate-based authentication validates device identities before granting network access. Network segmentation isolates wireless traffic from wired networks limiting breach impacts. Guest access provides internet connectivity for visitors without exposing internal resources.
Rogue access point detection identifies unauthorized wireless networks that could compromise security. Wireless security expertise through Fortinet FCP-FWF-AD-7.4 programs demonstrates mobility protection knowledge. Wireless intrusion prevention detects and blocks attacks targeting wireless infrastructure. Cloud management enables centralized administration of distributed wireless deployments. Citrix professionals supporting mobile workforces benefit from understanding secure wireless access ensuring employees connecting to Citrix resources from smartphones, tablets, or laptops receive appropriate network protection whether in offices, remote locations, or public venues preventing wireless network vulnerabilities from compromising virtual desktop security protecting organizational data accessed through mobile endpoints.
Secure Gateway Services Administration
Secure gateway services provide external access to Citrix resources through comprehensive security controls protecting against unauthorized access and attacks. Multi-factor authentication strengthens access security requiring additional verification factors beyond passwords. SmartAccess policies dynamically adjust resource access based on endpoint security posture, location, or other contextual factors. Endpoint analysis scans connecting devices verifying compliance with security requirements before granting access. Session encryption protects data in transit preventing interception during remote access.
Gateway integration enables single sign-on reducing authentication friction while maintaining security. Gateway expertise through Fortinet FCP-GCS-AD-7.6 credentials validates secure access capabilities. High availability configurations ensure continuous access during component failures. Traffic optimization reduces bandwidth consumption improving performance for remote users. The 1Y0-203 exam covers Citrix Gateway configuration and secure access architectures ensuring certified professionals understand how gateway services integrate with XenApp and XenDesktop providing secure remote access supporting distributed workforces while maintaining appropriate security controls protecting organizational resources from external threats and unauthorized access attempts.
Wireless LAN Controller Administration Expertise
Wireless LAN controller administration centralizes wireless network management for distributed access point deployments supporting mobile Citrix users. Automatic RF optimization adjusts channel assignments and power levels maximizing coverage and performance. Seamless roaming enables mobile users to move between access points without disconnecting virtual desktop sessions. Load balancing distributes client connections across access points preventing overload. Quality of service prioritizes virtual desktop traffic ensuring acceptable performance during network congestion.
Guest access provides isolated wireless networks for visitors preventing exposure of internal resources. Controller expertise through Fortinet FCP-WCS-AD-7.4 programs demonstrates wireless management knowledge. Spectrum analysis identifies interference sources degrading wireless performance. Controller redundancy ensures continuous wireless service during component failures. Citrix administrators supporting wireless infrastructure benefit from controller capabilities managing wireless networks at scale ensuring consistent policy application, optimal performance, and centralized visibility across distributed wireless deployments supporting mobile users accessing virtual desktops from various locations throughout organizational facilities ensuring wireless networks provide reliable, secure connectivity supporting productivity.
Zero Trust Network Access Implementation
Zero trust network access implementations verify every connection request regardless of source location replacing traditional perimeter-based security. Identity verification authenticates users through multi-factor methods before granting access. Device posture assessment validates endpoint security configuration before permitting connections. Least privilege access restricts users to minimum necessary resources rather than granting broad network access. Continuous monitoring tracks session activities detecting anomalous behaviors indicating potential compromise.
Microsegmentation isolates applications preventing lateral movement during breaches. Zero trust expertise through Fortinet FCP-ZCS-AD-7.4 credentials validates modern security architecture knowledge. Software-defined perimeter obscures infrastructure from unauthorized discovery. Session recording captures activities supporting security investigations and compliance. The 1Y0-203 exam addresses access security concepts that align with zero trust principles including multi-factor authentication, conditional access, and session security ensuring certified Citrix professionals understand how virtual desktop infrastructure fits within modern security frameworks assuming breach mentality requiring verification of every access request protecting organizational assets.
Advanced AI-Driven Security Analytics
Advanced AI-driven security analytics apply machine learning and behavioral analysis to security event data identifying threats that rule-based systems miss. Anomaly detection establishes normal behavior baselines alerting on deviations indicating potential compromise. User behavior analytics identify insider threats through unusual activity patterns. Predictive threat intelligence anticipates attacks based on observed reconnaissance activities. Automated investigation correlates events across systems reconstructing attack timelines.
Response automation implements containment actions reducing time between detection and remediation. Advanced analytics through Fortinet FCSS-ADA-AR-6.7 expertise demonstrates AI security capabilities. Threat hunting capabilities enable proactive searching for undiscovered threats. False positive reduction improves analyst efficiency through improved detection accuracy. Citrix professionals supporting security operations benefit from AI-driven analytics capabilities particularly in large deployments generating substantial security event volumes requiring intelligent analysis identifying genuine threats among benign activities ensuring security teams can focus attention on true risks rather than investigating false alarms improving security posture while managing analyst workload.
Cloud-Delivered Security Services
Cloud-delivered security services provide protection without requiring on-premises security appliances reducing infrastructure complexity and capital expenditure. Cloud web security protects users from web-based threats regardless of location. Cloud email security provides comprehensive email protection without local appliances. Cloud access security broker capabilities extend protection to SaaS applications. Cloud sandbox analyzes suspicious files in cloud infrastructure scaling to meet demand.
Cloud management simplifies administration through centralized consoles managing global security policies. Cloud security expertise through Fortinet FCSS-CDS-AR-7.6 programs validates modern delivery models. Automatic updates ensure current protection without manual intervention. Usage-based pricing aligns costs with consumption. Citrix professionals considering cloud-hosted virtual desktops benefit from understanding cloud security services enabling comprehensive protection for cloud workloads ensuring users accessing resources from cloud data centers receive equivalent security regardless of hosting location maintaining consistent protection across hybrid infrastructure combining on-premises and cloud deployments.
Enterprise Firewall Advanced Administration
Enterprise firewall advanced administration addresses sophisticated security requirements in complex organizational environments. Application control identifies and manages application usage including non-standard ports and protocols. Advanced threat protection including intrusion prevention and antivirus protects against known and emerging threats. SSL inspection decrypts, inspects, and re-encrypts traffic ensuring security policies apply to encrypted communications. SD-WAN integration optimizes application performance while maintaining security enforcement.
Security fabric coordination shares threat intelligence across security infrastructure automating response. Advanced firewall skills through Fortinet FCSS-EFW-AD-7.4 credentials validate enterprise protection capabilities. High availability clustering ensures continuous security services during failures. Virtual domain implementation provides multi-tenancy isolating configurations for different business units. The 1Y0-203 exam covers security concepts applicable to firewall integration with Citrix infrastructure including network segmentation, access controls, and secure remote access ensuring certified professionals understand how enterprise firewalls protect virtual desktop environments providing defense-in-depth security architectures.
Contemporary Enterprise Firewall Features
Contemporary enterprise firewall features address modern threats and architectural patterns including cloud integration and encrypted traffic inspection. ZTNA (Zero Trust Network Access) verifies every connection attempt regardless of source location. Cloud integration protects branch offices connecting directly to internet and cloud services. API security protects programmatic interfaces preventing attacks targeting application integration points. Container security extends protection to containerized workloads supplementing virtual machine protection.
IoT security identifies and protects Internet of Things devices accessing networks. Modern firewall capabilities through Fortinet FCSS-EFW-AD-7.6 programs demonstrate current protection knowledge. Threat intelligence integration consumes external indicators automatically updating protection rules. Automation through APIs enables security orchestration coordinating with other security tools. Citrix professionals supporting modern infrastructure benefit from understanding contemporary firewall features ensuring virtual desktop security architectures incorporate current capabilities addressing evolving threats and architectural patterns including cloud adoption, remote work, and bring-your-own-device trends transforming organizational security requirements.
Local Edge Device Administration
Local edge device administration manages security appliances at branch offices and remote sites protecting distributed Citrix users. Edge device deployment simplifies branch security providing essential protection without full-featured firewalls. SD-WAN integration optimizes application performance across WAN connections. Cloud management enables centralized administration without local IT staff. Zero-touch provisioning automates device deployment reducing installation complexity.
Local breakout enables direct internet access for cloud applications bypassing headquarters. Edge expertise through Fortinet FCSS-LED-AR-7.6 credentials validates distributed security knowledge. High availability configurations provide redundancy for critical locations. Traffic shaping prioritizes business-critical applications during bandwidth constraints. Citrix professionals supporting distributed organizations benefit from edge device capabilities protecting branch users accessing virtual desktops across WAN connections ensuring appropriate security controls without requiring complex local security infrastructure enabling consistent protection across organizational locations regardless of size supporting growing distributed workforce trends.
AWS Machine Learning Integration Opportunities
AWS machine learning integration brings artificial intelligence capabilities to virtual desktop infrastructure through cloud services. Amazon SageMaker enables custom model development for usage prediction, capacity planning, or user behavior analysis. Rekognition image analysis processes screenshots or session recordings identifying sensitive information or policy violations. Comprehend natural language processing analyzes support tickets or user feedback extracting insights. Forecast time-series analysis predicts resource consumption informing capacity planning.
Personalize recommendation engines suggest applications or resources based on usage patterns. Machine learning expertise through AWS ML Specialty tutorials demonstrates AI implementation capabilities. Lambda serverless functions process events triggering automated responses. CloudWatch monitoring tracks infrastructure metrics enabling performance optimization. Citrix professionals exploring cloud integration benefit from AWS machine learning capabilities enhancing virtual desktop management through intelligent automation, predictive analytics, and user experience optimization leveraging cloud AI services augmenting traditional infrastructure management improving efficiency and user satisfaction.
Cloud Security Specialization Pathways
Cloud security specialization addresses unique security challenges in cloud-hosted virtual desktop deployments. Identity and access management controls user authentication and authorization for cloud resources. Encryption protects data at rest and in transit meeting compliance requirements. Security monitoring tracks activities across cloud infrastructure detecting anomalous behaviors. Compliance frameworks ensure cloud deployments meet regulatory requirements including data residency and privacy protections.
Incident response procedures address security events in cloud environments. Cloud security expertise through AWS Security Specialty credentials validates protection knowledge. Network security controls traffic between cloud resources and external networks. Container security protects containerized workloads alongside virtual machines. Citrix professionals pursuing cloud deployments benefit from security specialization ensuring cloud-hosted virtual desktops receive appropriate protection addressing cloud-specific threats and architectural patterns maintaining security posture equivalent to on-premises deployments while leveraging cloud advantages including scalability, global reach, and managed services.
Updated Cloud Security Certification Paths
Updated cloud security certification paths reflect evolving cloud platforms and emerging security practices. Current exam versions cover contemporary features including serverless security, container protection, and AI service security. Zero trust architectures emphasize verification over implicit trust. DevSecOps integration embeds security throughout development and deployment pipelines. Cloud-native security tools leverage platform capabilities rather than importing traditional security approaches.
Modern security skills through AWS Security SCS-C02 programs validate current expertise. Shared responsibility models clarify security obligations between cloud providers and customers. Compliance automation ensures continuous adherence to security standards. Citrix professionals maintaining cloud security knowledge through updated certifications ensure skills remain relevant as cloud platforms evolve supporting secure virtual desktop deployments leveraging current capabilities addressing contemporary threats ensuring organizational resources receive optimal protection through modern security practices aligned with cloud provider capabilities.
Solution Architecture Design for Enterprise Deployments
Solution architecture design creates comprehensive technical blueprints for enterprise Citrix deployments addressing requirements for performance, availability, security, and scalability. Requirements gathering identifies business objectives, user populations, application portfolios, and constraints. Capacity planning determines infrastructure sizing supporting anticipated workloads with acceptable performance. High availability design eliminates single points of failure ensuring business continuity. Disaster recovery planning implements replication and backup strategies enabling recovery from site disasters.
Security architecture applies defense-in-depth protection throughout infrastructure. Architecture skills through AWS Solutions Architect Associate credentials demonstrate design expertise. Network design optimizes connectivity, latency, and bandwidth consumption. Monitoring architecture enables proactive issue detection and performance optimization. The 1Y0-203 exam provides technical foundations that certified professionals apply in architecture roles designing comprehensive solutions addressing complex organizational requirements ensuring deployments meet functional requirements while supporting non-functional requirements including performance, availability, security, and maintainability throughout solution lifecycles.
Contemporary Cloud Architecture Patterns
Contemporary cloud architecture patterns address modern requirements including hybrid cloud, multi-cloud, and cloud-native designs. Microservices architectures decompose monolithic applications into independent services enabling independent scaling and deployment. Serverless computing eliminates infrastructure management focusing on application logic. Container orchestration manages containerized workloads at scale. Infrastructure-as-code defines resources programmatically enabling consistent reproducible deployments.
Event-driven architectures enable loose coupling and asynchronous processing. Modern architecture through AWS SAA-C02 certification paths validates contemporary design knowledge. API-first design enables integration and automation. Cloud-native databases leverage managed services reducing operational overhead. Citrix professionals understanding contemporary architecture patterns can recommend appropriate approaches for virtual desktop deployments whether on-premises, cloud-hosted, or hybrid ensuring solutions leverage modern patterns appropriate to organizational requirements balancing innovation against complexity and operational considerations supporting business objectives through well-architected solutions.
Conclusion
The Citrix 1Y0-203 exam represents substantial professional development investment validating comprehensive XenApp and XenDesktop administration expertise that enterprises increasingly demand. Successful certification achievement demonstrates to employers, clients, and peers that professionals possess verified capabilities managing critical virtualization infrastructure supporting organizational productivity, security, and business continuity. The credential distinguishes certified professionals in competitive employment markets where organizations specifically seek validated expertise ensuring candidates can effectively implement, configure, optimize, and troubleshoot complex virtual desktop deployments without extensive training periods following employment. This verified competency becomes increasingly valuable as remote work, cloud adoption, and digital transformation initiatives accelerate virtualization technology adoption across industries creating sustained demand for qualified professionals who can support these critical business platforms.
Organizations benefit substantially from employing certified Citrix professionals who can implement best practices, avoid common pitfalls, optimize resource consumption, and troubleshoot issues efficiently minimizing downtime and user frustration. Internal teams with verified expertise reduce dependence on expensive external consultants while delivering faster implementations and more effective ongoing support. Security postures improve when certified administrators understand and properly configure security features protecting organizational data and maintaining regulatory compliance. User productivity increases through optimized configurations, responsive troubleshooting, and effective training enabling employees to leverage virtual desktop capabilities effectively supporting business objectives rather than fighting technical obstacles.
The decision to pursue Citrix 1Y0-203 certification requires honest self-assessment considering career goals, current technical foundation, available preparation time, and organizational context. Professionals currently working with Citrix technologies or those targeting Citrix-focused roles derive greatest value from certification validating existing knowledge or supporting career transitions. Individuals in organizations implementing or expanding Citrix infrastructure gain immediate opportunities applying learned skills while preparing for certification. Those without Citrix exposure should evaluate whether certification aligns with realistic career opportunities in target markets or whether alternative credentials better support specific objectives. Strategic certification planning considers how Citrix expertise complements existing skills creating comprehensive capabilities rather than pursuing credentials opportunistically without clear purpose.
Return on certification investment manifests through multiple mechanisms beyond direct salary increases including expanded career options, professional credibility, networking opportunities through certified communities, and personal satisfaction from mastering complex technologies. The credential provides objective third-party validation that resume claims and interview assertions alone cannot achieve particularly valuable for individuals changing careers, seeking remote opportunities, or competing against candidates with similar experience levels. Certification discussions during interviews provide opportunities demonstrating knowledge depth, learning commitment, and professional development initiative beyond basic qualification requirements potentially differentiating candidates when multiple qualified applicants compete for limited positions.
Looking toward the future, virtualization technologies will continue evolving with emerging trends including artificial intelligence integration, advanced security capabilities, deeper cloud integration, and converged infrastructure platforms combining multiple technologies into unified solutions. Professionals positioning themselves at intersections of traditional virtualization expertise and emerging capabilities through continuous learning and strategic certification pursuits will command premium value as organizations pursue digital transformation initiatives requiring sophisticated technical skills across multiple domains. The 1Y0-203 certification provides solid foundations in core virtualization concepts that extend into emerging technology contexts ensuring certified professionals can adapt as landscapes evolve rather than requiring complete reskilling when paradigms shift.
The comprehensive nature of knowledge required for certification success, rigorous assessment methodology, and practical applicability of tested concepts make the Citrix 1Y0-203 exam valuable credential for virtualization professionals seeking to validate expertise, advance careers, and contribute meaningfully to organizational success through effective virtual desktop infrastructure administration. The investment of time, effort, and financial resources required for preparation and examination success represents sound professional development decisions for appropriately situated individuals pursuing careers in virtualization infrastructure management, particularly those working with or targeting positions involving Citrix technologies. Certification achievement opens doors to specialized career pathways, enhances professional credibility, and validates capabilities that organizations increasingly demand supporting both immediate career advancement and long-term professional growth in dynamic, evolving technology sectors where continuous learning and verified expertise determine sustained career success and professional satisfaction across decades-long careers in information technology.
Citrix CCA-V 1Y0-203 practice test questions and answers, training course, study guide are uploaded in ETE Files format by real users. Study and Pass 1Y0-203 Citrix XenApp and XenDesktop 7.15 Administration certification exam dumps & practice test questions and answers are to help students.
Exam Comments * The most recent comment are on top
- 1Y0-312 - Citrix Virtual Apps and Desktops 7 Advanced Administration
- 1Y0-204 - Citrix Virtual Apps and Desktops 7 Administration
- 1Y0-341 - Citrix ADC Advanced Topics - Security, Management, and Optimization
- 1Y0-205 - Citrix Virtual Apps and Desktops Administration
- 1Y0-231 - Deploy and Manage Citrix ADC 13 with Citrix Gateway
- 1Y0-241 - Deploy and Manage Citrix ADC 13 with Traffic Management
Why customers love us?
What do our customers say?
The resources provided for the Citrix certification exam were exceptional. The exam dumps and video courses offered clear and concise explanations of each topic. I felt thoroughly prepared for the 1Y0-203 test and passed with ease.
Studying for the Citrix certification exam was a breeze with the comprehensive materials from this site. The detailed study guides and accurate exam dumps helped me understand every concept. I aced the 1Y0-203 exam on my first try!
I was impressed with the quality of the 1Y0-203 preparation materials for the Citrix certification exam. The video courses were engaging, and the study guides covered all the essential topics. These resources made a significant difference in my study routine and overall performance. I went into the exam feeling confident and well-prepared.
The 1Y0-203 materials for the Citrix certification exam were invaluable. They provided detailed, concise explanations for each topic, helping me grasp the entire syllabus. After studying with these resources, I was able to tackle the final test questions confidently and successfully.
Thanks to the comprehensive study guides and video courses, I aced the 1Y0-203 exam. The exam dumps were spot on and helped me understand the types of questions to expect. The certification exam was much less intimidating thanks to their excellent prep materials. So, I highly recommend their services for anyone preparing for this certification exam.
Achieving my Citrix certification was a seamless experience. The detailed study guide and practice questions ensured I was fully prepared for 1Y0-203. The customer support was responsive and helpful throughout my journey. Highly recommend their services for anyone preparing for their certification test.
I couldn't be happier with my certification results! The study materials were comprehensive and easy to understand, making my preparation for the 1Y0-203 stress-free. Using these resources, I was able to pass my exam on the first attempt. They are a must-have for anyone serious about advancing their career.
The practice exams were incredibly helpful in familiarizing me with the actual test format. I felt confident and well-prepared going into my 1Y0-203 certification exam. The support and guidance provided were top-notch. I couldn't have obtained my Citrix certification without these amazing tools!
The materials provided for the 1Y0-203 were comprehensive and very well-structured. The practice tests were particularly useful in building my confidence and understanding the exam format. After using these materials, I felt well-prepared and was able to solve all the questions on the final test with ease. Passing the certification exam was a huge relief! I feel much more competent in my role. Thank you!
The certification prep was excellent. The content was up-to-date and aligned perfectly with the exam requirements. I appreciated the clear explanations and real-world examples that made complex topics easier to grasp. I passed 1Y0-203 successfully. It was a game-changer for my career in IT!

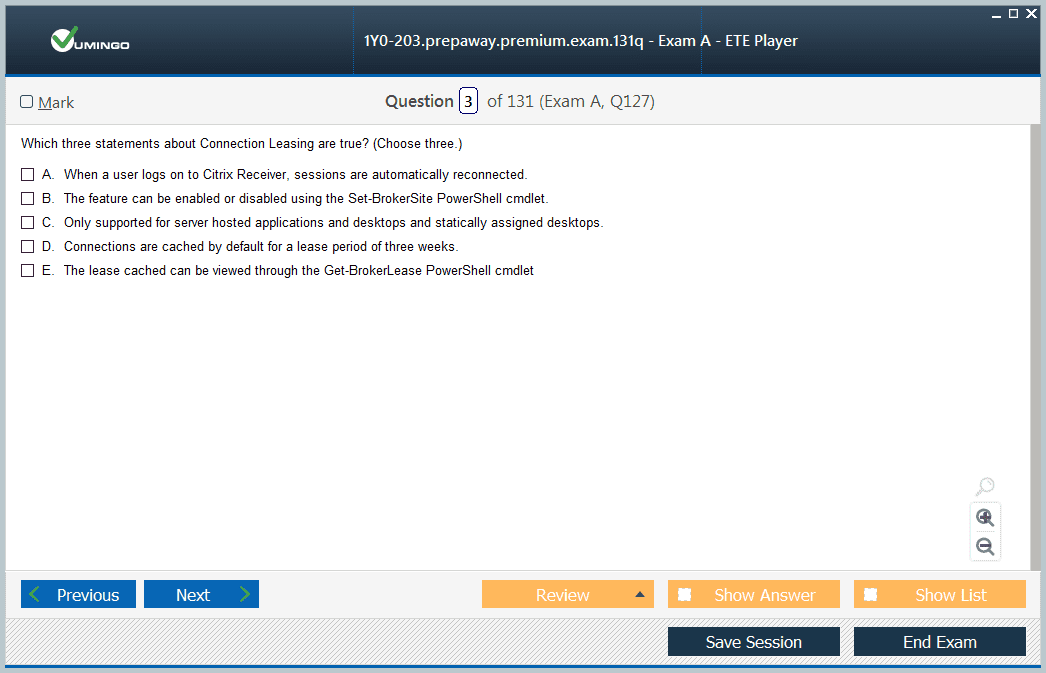
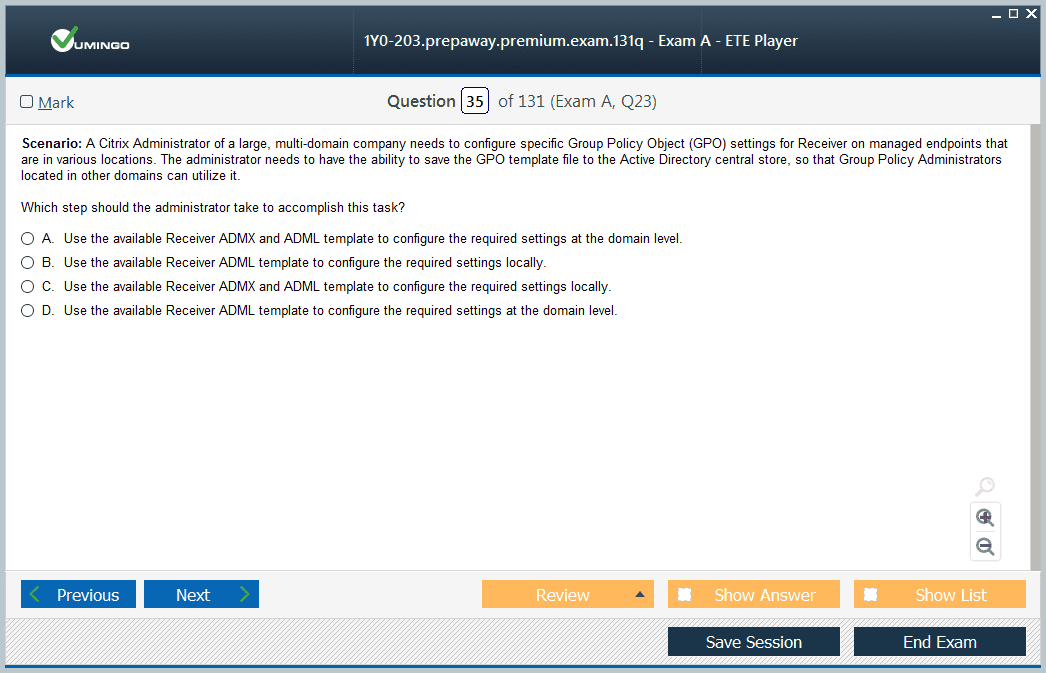
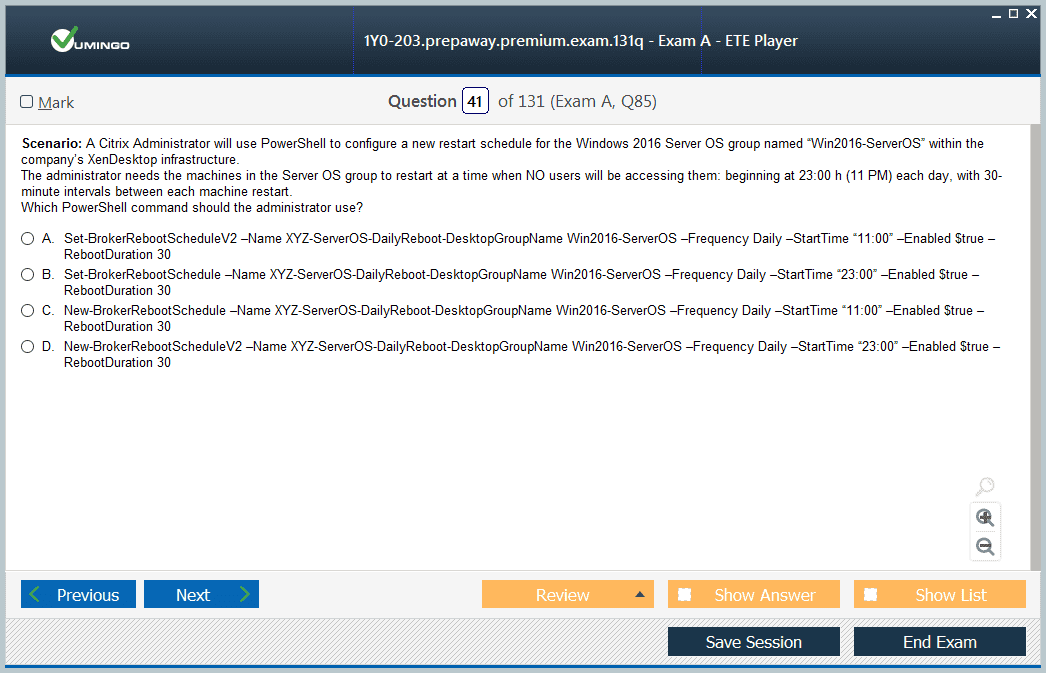
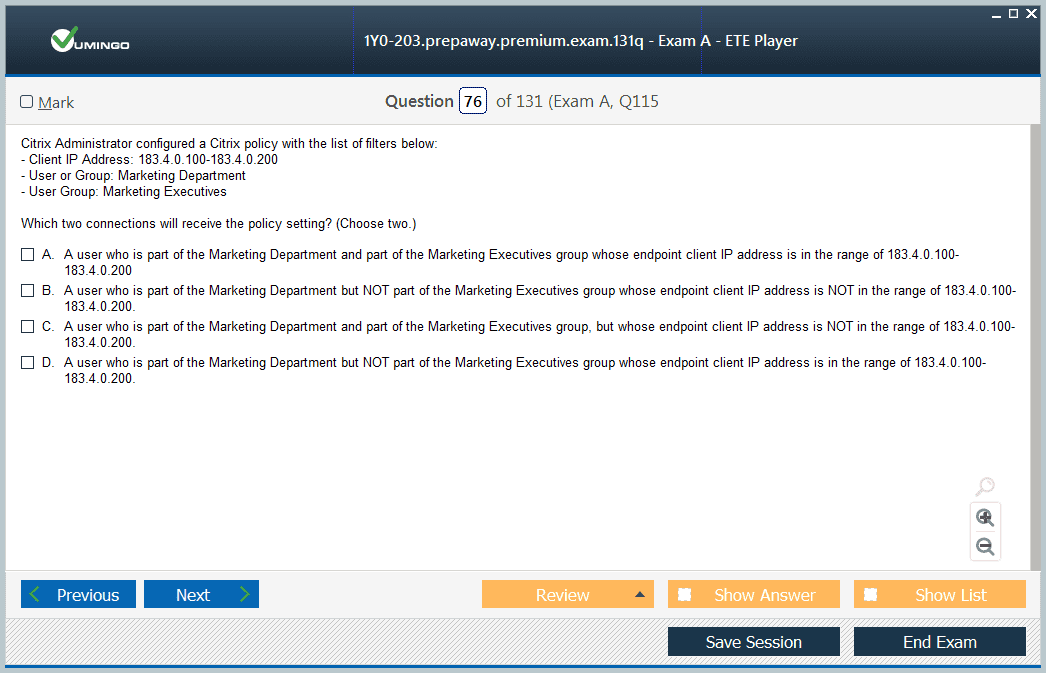




All the questions in the exam were in the Premium Bundle.
I answered exactly the same answers as they were in the Premium Bundle and I - got 80
Thanks in advance