- Home
- McAfee Certifications
- MA0-100 Certified McAfee Security Specialist - ePO Dumps
Pass McAfee MA0-100 Exam in First Attempt Guaranteed!
Get 100% Latest Exam Questions, Accurate & Verified Answers to Pass the Actual Exam!
30 Days Free Updates, Instant Download!


MA0-100 Premium File
- Premium File 157 Questions & Answers. Last Update: Mar 05, 2026
Whats Included:
- Latest Questions
- 100% Accurate Answers
- Fast Exam Updates
Last Week Results!
All McAfee MA0-100 certification exam dumps, study guide, training courses are Prepared by industry experts. PrepAway's ETE files povide the MA0-100 Certified McAfee Security Specialist - ePO practice test questions and answers & exam dumps, study guide and training courses help you study and pass hassle-free!
Mastering Intel Security Certified Product Specialist MA0-100 : Exam Overview and Preparation
The MA0-100 exam evaluates the skills and knowledge required for effectively managing and implementing security solutions using McAfee ePolicy Orchestrator and McAfee Virus Scan. This certification is intended for professionals responsible for deploying, configuring, and maintaining enterprise security systems. Candidates are tested on their ability to install and configure servers, manage policies, monitor system health, handle agents, and create queries and reports. The exam focuses on both theoretical understanding and practical proficiency, ensuring that certified individuals are capable of handling complex tasks in enterprise environments.
The exam requires candidates to demonstrate competence in all operational aspects of the tools covered, including server setup, policy deployment, and system monitoring. In addition, understanding troubleshooting methods and performance optimization is crucial. Candidates are expected to be able to implement solutions that maintain security, compliance, and system reliability, while also being able to identify and resolve potential issues proactively.
Installation and Configuration of Servers
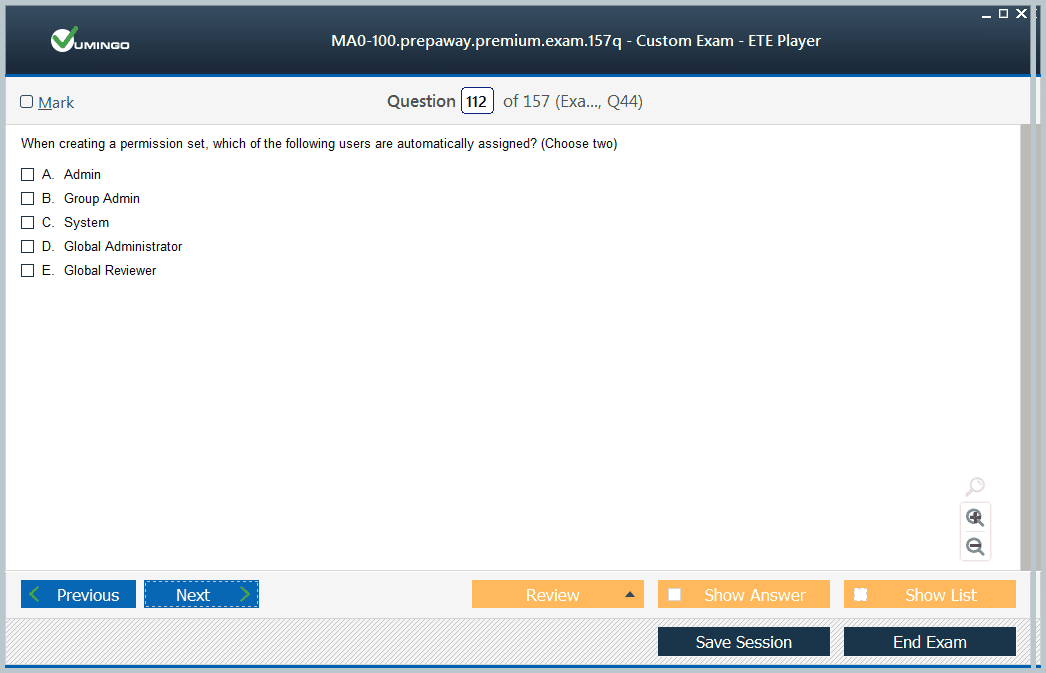
A critical domain of the exam is the installation and configuration of server environments. Candidates must be proficient in performing full installations of McAfee ePolicy Orchestrator, including selecting appropriate protocols, encryption settings, and default configurations. They are expected to navigate the user interface efficiently, manage repositories, configure user accounts, and define permission sets to ensure a secure and organized deployment.
Understanding how to automate responses and organize system resources is also essential. Candidates must be capable of configuring automatic responses to security events, maintaining repositories for agent deployment, and establishing a stable environment that supports ongoing operations. Proper installation and configuration are foundational skills, as they influence all other aspects of server management and policy enforcement.
Managing Server Health and Maintenance
Effective management of the server includes monitoring performance, conducting health checks, analyzing logs, and performing routine maintenance. Candidates must understand how to interpret server logs to identify potential issues and maintain optimal performance. Knowledge of SQL is often necessary for managing data stored in the backend, running queries for operational oversight, and troubleshooting errors related to database interactions.
Performance monitoring involves analyzing server metrics, ensuring that tasks are executed efficiently, and addressing bottlenecks that may impact agent performance or system stability. Maintenance procedures such as backups, updates, and patches are critical to prevent downtime and ensure continuous protection across all managed endpoints. Candidates are expected to demonstrate an ability to maintain a secure and reliable system environment proactively.
Product and Policy Management
Another significant area of the exam is product and policy administration. Candidates need to understand how to manage the policy catalogue, which includes creating and configuring policies for agents, super users, and specific endpoints. This requires knowledge of assignment rules, extension installation, and ongoing maintenance of policies to meet organizational needs.
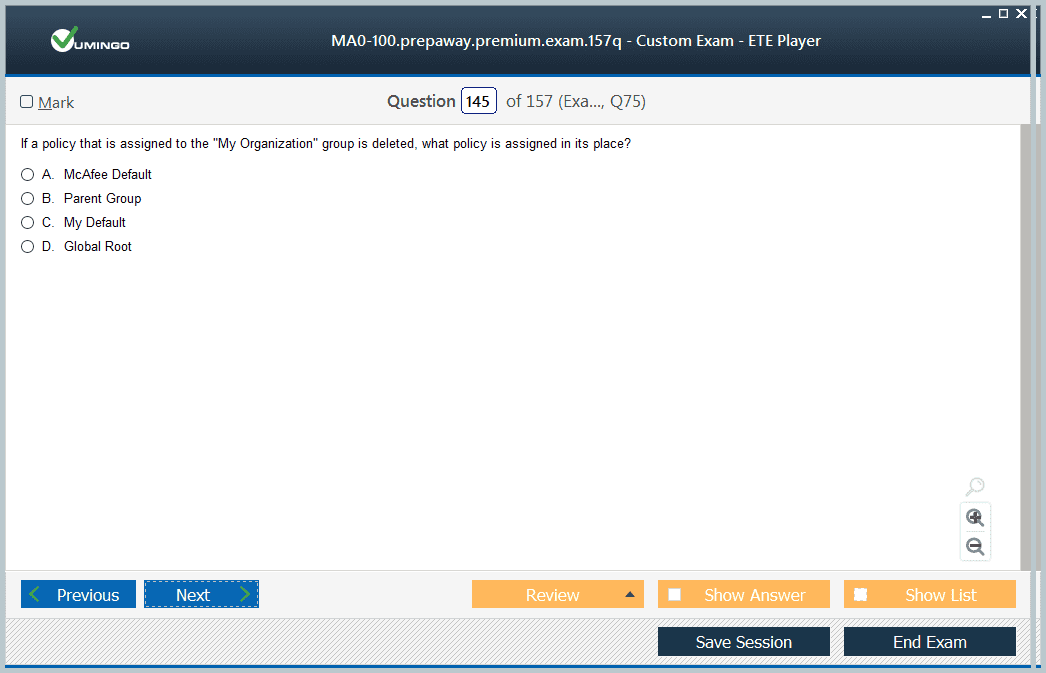
Effective policy management ensures that security configurations are consistently applied, threats are mitigated, and client systems remain compliant with established standards. Candidates must also be able to troubleshoot issues related to policy enforcement and adjust configurations as needed to address evolving security requirements. Knowledge of policy hierarchy and precedence is critical for ensuring that rules are applied correctly and conflicts are minimized.
McAfee Agent Communication and Management
Understanding the role and functionality of the McAfee Agent is essential for exam readiness. Candidates must be familiar with agent communication protocols, including peer-to-peer and agent-to-agent interactions, which facilitate updates and reporting across endpoints. Knowledge of logging mechanisms, distributed repositories, and troubleshooting common issues such as duplicate GUIDs, site list conflicts, and XML configuration errors is crucial for maintaining agent reliability.
Candidates are expected to deploy agents effectively, ensure consistent communication with the server, and resolve issues that may disrupt normal operations. This includes verifying agent health, managing updates, and maintaining secure communication channels between agents and the server. Proper agent management ensures that endpoints remain protected and that policies are consistently enforced throughout the network.
System Tree Setup and Monitoring
Setting up and monitoring the system tree is a vital skill tested in the exam. Candidates need to be able to populate the system tree accurately, organize endpoints into logical groups, and apply tagging for efficient management. This involves understanding how to deploy systems, categorize clients, and implement group-level policies to streamline operations.
Monitoring the system tree includes identifying rogue systems, verifying client compliance, and ensuring that all endpoints are accounted for within the organizational structure. Candidates must be able to detect anomalies, resolve configuration issues, and maintain a clear overview of the system’s status. Effective system tree management is key to organizing large-scale environments and ensuring that security policies are applied uniformly.
Query Creation and Report Analysis
The ability to create queries and analyze reports is another essential area of the MA0-100 exam. Candidates must be able to devise queries to extract relevant information about endpoints, security events, and policy compliance. They must also be able to run these queries, interpret the results, and generate reports that provide actionable insights for system administrators.
Dashboards, monitors, and audit logs are important tools for analyzing system performance and identifying potential threats. Candidates should be able to examine reports critically, recognize trends, and implement corrective measures based on the data. Understanding how to purge outdated or unnecessary information while maintaining accurate records is also important for system efficiency and security compliance.
Troubleshooting and Issue Resolution
Exam preparation emphasizes the importance of troubleshooting skills. Candidates are expected to identify and resolve issues that arise in server management, agent communication, policy enforcement, and system monitoring. This includes understanding common failure points, analyzing logs for root causes, and implementing solutions to restore normal operations.
Candidates must be adept at diagnosing errors, performing corrective actions, and verifying that issues have been resolved without introducing new risks. Troubleshooting also involves anticipating potential problems, preparing contingency plans, and maintaining system reliability under varying conditions. A methodical approach to problem-solving ensures that the environment remains secure and operational at all times.
Practical Experience and Preparation
While theoretical knowledge is essential, hands-on experience is a critical component of preparation for the MA0-100 exam. Candidates benefit from direct exposure to server deployment, agent installation, policy configuration, and query/report creation. Working with the system in real-world scenarios helps internalize processes, understand dependencies, and develop confidence in executing administrative tasks.
Practical exercises include configuring repositories, applying policies, monitoring system performance, and troubleshooting agent issues. Candidates gain insight into optimizing server performance, maintaining endpoint security, and implementing efficient workflows. This combination of theoretical knowledge and practical application ensures readiness for the exam and the ability to perform effectively in professional environments.
System Security and Compliance Management
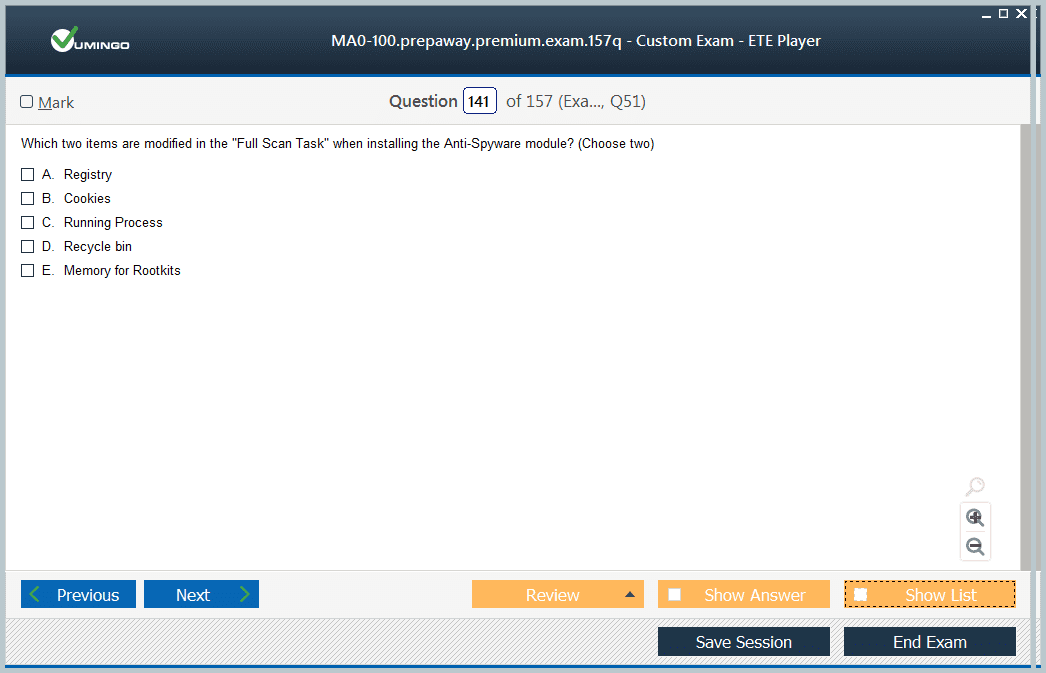
Candidates must also understand the principles of system security and compliance as they relate to the tools covered in the exam. This includes ensuring that endpoints are protected according to organizational policies, monitoring for vulnerabilities, and maintaining compliance with established standards. Knowledge of encryption, authentication, and access controls is essential for safeguarding sensitive data and maintaining system integrity.
Maintaining compliance involves monitoring reports, conducting audits, and implementing corrective actions when deviations are detected. Candidates must be able to assess risks, apply necessary updates, and ensure that all systems operate in accordance with security policies. Effective management of these processes ensures a secure, reliable, and compliant environment.
Reporting and Decision-Making
The ability to generate accurate and actionable reports is a core skill tested in the MA0-100 exam. Candidates should be proficient in creating queries, analyzing results, and presenting findings in a manner that supports informed decision-making. Reports are used to track system performance, monitor endpoint compliance, and identify security threats, providing administrators with the data needed to make timely interventions.
Candidates are expected to understand how to interpret dashboards, analyze trends, and apply findings to optimize policies and workflows. Reporting skills contribute to proactive system management, enabling administrators to maintain secure and well-functioning environments while supporting organizational objectives.
The Intel Security Certified Product Specialist exam is designed to evaluate comprehensive knowledge in server installation, agent management, policy administration, system monitoring, troubleshooting, and reporting. Candidates who master these domains demonstrate the ability to deploy, configure, and maintain enterprise security solutions effectively. Practical experience, combined with an understanding of system operations and security principles, equips candidates to handle complex environments, ensuring reliable and secure performance across all managed endpoints
Advanced Server Configuration and Optimization
A deep understanding of server configuration is critical for the MA0-100 exam. Candidates are expected to know not only how to perform basic installations but also how to optimize the server environment for performance and scalability. This includes configuring encryption settings, managing communication protocols, and setting up repositories to efficiently handle large numbers of endpoints. Proper organization of user accounts, permission sets, and automatic responses ensures that administrators can manage tasks systematically and maintain consistent security standards.
Optimization also involves configuring the server to handle high loads without performance degradation. Candidates should be familiar with techniques to balance system resources, prioritize critical tasks, and manage event handling to avoid bottlenecks. Effective optimization guarantees that endpoints receive timely updates, policies are enforced promptly, and overall system responsiveness is maintained even in complex enterprise environments.
Health Monitoring and Performance Evaluation
Monitoring the health of the server is a key responsibility tested in the MA0-100 exam. Candidates are required to evaluate performance metrics, analyze logs, and ensure that all components are functioning correctly. Knowledge of SQL queries for data analysis, understanding of log file interpretation, and the ability to identify anomalies in system behavior are essential skills.
Candidates must also be proficient in implementing proactive maintenance routines such as backups, updates, and patches. Regular health checks, including monitoring memory usage, processor load, and storage capacity, allow administrators to anticipate problems and address them before they impact system performance. Understanding the interplay between different components of the security infrastructure helps maintain stability and reduces downtime.
Policy Design and Implementation
Policy management is a core domain of the exam, requiring candidates to create, implement, and maintain comprehensive security policies. Candidates need to understand policy hierarchies, assignment rules, and how policies interact with different agent types. Knowledge of configuring product settings, installing extensions, and adjusting policies to meet evolving organizational requirements is crucial.
Effective policy implementation ensures that endpoints remain compliant with organizational standards. Candidates should be able to identify conflicts between policies, prioritize enforcement rules, and deploy updates systematically. Regular review and adjustment of policies based on monitoring results and emerging threats ensures that security measures remain robust and adaptive.
Agent Deployment and Troubleshooting
Proficiency in managing McAfee Agents is essential for the MA0-100 exam. Candidates should understand agent communication protocols, including peer-to-peer and agent-to-agent interactions, and how these mechanisms facilitate updates and reporting. Knowledge of logging practices, distributed repositories, and common troubleshooting scenarios such as duplicate GUIDs, site list errors, and XML misconfigurations is required to maintain agent reliability.
Candidates must be able to deploy agents efficiently, verify their communication with the server, and resolve issues that could disrupt functionality. This includes monitoring agent health, ensuring timely updates, and maintaining secure channels for data transmission. Effective agent management guarantees that endpoints are consistently protected and policies are applied correctly.
System Tree Management and Organization
Organizing and maintaining the system tree is a critical aspect of administration. Candidates need to understand how to populate the system tree, assign endpoints to groups, and implement tagging for efficient management. This includes monitoring group compliance, detecting rogue systems, and ensuring that all clients are accurately represented in the hierarchy.
Candidates should also be able to restructure the system tree when needed, deploy group-level policies, and perform audits to verify the accuracy of endpoint assignments. Proper system tree management ensures that policies are enforced consistently, compliance is monitored effectively, and administrators have a clear overview of the network structure.
Query Creation and Data Analysis
The ability to create queries and analyze data is a major component of the MA0-100 exam. Candidates must be capable of devising queries to extract relevant security information, running them efficiently, and interpreting the results to support decision-making. Knowledge of dashboard usage, monitor configurations, and audit logs is essential for tracking system performance and identifying potential threats.
Candidates should also be able to analyze the output of queries to detect anomalies, track policy compliance, and generate actionable insights. Understanding how to filter, sort, and interpret data allows administrators to respond effectively to security events and maintain a secure environment. Proper data analysis supports proactive management, helping prevent issues before they escalate.
Reporting and Decision Support
Generating and interpreting reports is a critical skill for maintaining system oversight. Candidates are expected to produce reports that summarize policy enforcement, agent status, and security events. The ability to read dashboards, analyze trends, and make data-driven decisions is essential for maintaining operational efficiency.
Reports are used to inform administrators about system health, compliance status, and potential risks. Candidates should be able to identify patterns, detect vulnerabilities, and implement corrective measures based on report findings. Proficiency in reporting ensures that administrators can make informed decisions that enhance security and maintain network stability.
Troubleshooting and Issue Resolution
Troubleshooting forms a central part of the exam, assessing a candidate’s ability to resolve operational issues effectively. Candidates must identify problems related to server performance, agent communication, policy enforcement, and system monitoring. Understanding root causes, analyzing logs, and implementing solutions to restore normal operation is essential.
Candidates should be skilled in systematic problem-solving, including verifying fixes, monitoring results, and ensuring that corrective actions do not create additional issues. Troubleshooting also involves anticipating potential failures, preparing contingency plans, and applying proactive measures to maintain system reliability.
Practical Skills and Hands-On Experience
Practical experience is essential for candidates preparing for the MA0-100 exam. Working with servers, agents, policies, and system trees in real-world scenarios helps solidify theoretical knowledge. Hands-on practice allows candidates to understand dependencies, identify issues quickly, and implement efficient solutions.
Practical exercises include configuring repositories, applying policies, monitoring system performance, deploying agents, and analyzing reports. Exposure to these tasks helps candidates gain confidence in managing complex security environments, ensuring they are well-prepared for the operational challenges they may encounter.
Security Compliance and Risk Management
Maintaining compliance and managing security risks is an integral part of system administration. Candidates are expected to ensure that endpoints adhere to organizational standards, monitor vulnerabilities, and maintain appropriate access controls. Knowledge of encryption, authentication, and audit practices is necessary to safeguard sensitive data and prevent unauthorized access.
Candidates must also implement procedures to identify potential threats, assess their impact, and apply preventive or corrective measures. Ensuring compliance requires continuous monitoring, regular audits, and adjustments to policies based on findings. Effective risk management supports a secure and reliable operational environment.
Performance Monitoring and Optimization
Performance monitoring is essential for ensuring that all components function efficiently. Candidates must understand how to monitor server metrics, analyze agent activity, and optimize system resources. Techniques for minimizing bottlenecks, balancing workloads, and enhancing processing efficiency are critical for maintaining smooth operations.
Optimization extends to managing queries, reports, and dashboards. Candidates should be able to configure systems for rapid data retrieval, reduce unnecessary processing, and ensure timely application of updates and policies. A focus on performance ensures that endpoints remain protected and that administrators can respond effectively to security events.
Enterprise-Level Administration
Candidates must be prepared to handle enterprise-level administration tasks, including managing multiple endpoints, configuring group policies, and deploying agents across diverse environments. Knowledge of scalable architectures, distributed repositories, and system tree organization is essential for managing large deployments efficiently.
Enterprise administration also involves coordinating updates, ensuring policy compliance, and monitoring performance across multiple groups. Candidates should be able to implement solutions that maintain consistency, optimize resources, and support growth in both endpoints and operational complexity.
Reporting Tools and Analytics
Proficiency in reporting tools and analytics is critical for the MA0-100 exam. Candidates must be able to generate comprehensive reports, monitor trends, and interpret security events accurately. This involves creating queries, analyzing output, and using dashboards to track system health and compliance status.
Analytics supports proactive decision-making, enabling administrators to identify emerging threats, detect vulnerabilities, and implement timely interventions. Understanding how to leverage reporting tools ensures that administrators maintain a clear overview of system performance and security posture.
System Maintenance and Updates
Routine maintenance and updates are essential for maintaining system stability. Candidates must understand how to schedule updates, apply patches, and manage system resources effectively. Regular maintenance prevents downtime, ensures compliance, and keeps security measures up to date.
Candidates should also be able to troubleshoot issues arising from updates or changes, verify successful application, and monitor system behavior post-maintenance. A structured approach to maintenance ensures operational continuity and minimizes disruption to security operations.
Preparing for Exam Scenarios
Effective preparation for the MA0-100 exam combines hands-on practice with theoretical study. Candidates should simulate real-world tasks such as agent deployment, policy application, query creation, and report analysis. This practical approach helps candidates internalize workflows, understand dependencies, and develop problem-solving skills.
Breaking preparation into focused domains such as server management, agent troubleshooting, system monitoring, and reporting ensures comprehensive readiness. Candidates gain confidence in managing security environments, anticipating issues, and applying efficient solutions.
The MA0-100 exam is designed to assess comprehensive knowledge and practical skills in deploying, configuring, and maintaining enterprise security systems. Mastery of server installation, agent management, policy enforcement, system monitoring, troubleshooting, and reporting ensures that candidates are prepared to manage complex security environments effectively. Practical experience, combined with a deep understanding of security operations, equips candidates to maintain secure, compliant, and optimized IT infrastructures
Advanced Policy Configuration and Enforcement
For the MA0-100 exam, understanding advanced policy configuration is critical. Candidates must be able to design, implement, and maintain policies that cover all aspects of endpoint security, including antivirus settings, firewall rules, and system compliance checks. Knowledge of policy precedence, inheritance, and exception handling ensures that security measures are applied consistently across multiple endpoints. Candidates should be capable of creating layered policies that balance security requirements with operational flexibility, allowing organizations to enforce protective measures without disrupting workflow.
Endpoint Grouping and Targeted Policy Deployment
Managing endpoints effectively requires knowledge of grouping strategies and targeted policy deployment. Candidates must understand how to categorize devices based on function, location, or risk profile and apply policies accordingly. This includes creating dynamic groups that update automatically based on predefined criteria and assigning policies that align with each group's security requirements. Efficient grouping and deployment reduce administrative overhead and ensure that endpoints receive the correct protection according to organizational standards.
Monitoring Agent Health and System Compliance
A significant focus of the exam is the ability to monitor the health of agents and ensure system compliance. Candidates should be able to track agent connectivity, update status, and system interactions to detect anomalies or failures. Monitoring dashboards, alerts, and audit logs provide critical information about endpoint status, policy compliance, and security events. Candidates must analyze these indicators to take corrective actions, maintain operational stability, and prevent security breaches.
Incident Detection and Response
Incident detection and response are integral to maintaining enterprise security. Candidates are expected to identify potential threats, determine their impact, and initiate appropriate response procedures. This includes analyzing logs, reviewing security events, and coordinating with policies to mitigate risk. Understanding automated response mechanisms and integrating them into the security workflow allows administrators to respond promptly to incidents while minimizing manual intervention and operational disruption.
Query Optimization and Reporting Techniques
Generating meaningful reports and optimizing queries is a core skill for the MA0-100 exam. Candidates must understand how to create efficient queries that extract relevant data about endpoints, security events, and policy compliance. Knowledge of report templates, data visualization tools, and dashboard configurations enables administrators to present insights in a clear and actionable manner. Candidates should also be able to optimize queries for speed and accuracy, ensuring that reports are generated promptly and support timely decision-making.
System Tree Structuring and Management
The system tree is the backbone of endpoint management, and candidates must demonstrate proficiency in its structuring and maintenance. Proper organization allows administrators to categorize endpoints logically, apply group-level policies efficiently, and monitor compliance effectively. Candidates should understand how to tag systems, deploy policies to specific groups, and detect rogue or non-compliant systems. Maintaining a well-structured system tree supports operational clarity, simplifies policy enforcement, and enhances the ability to respond to security events.
Troubleshooting Communication and Connectivity Issues
Candidates are tested on their ability to troubleshoot agent communication and connectivity problems. This includes identifying issues related to peer-to-peer interactions, server connections, site lists, XML configurations, and duplicate identifiers. Understanding how agents communicate with the server and with each other enables administrators to diagnose failures, restore connectivity, and ensure uninterrupted policy enforcement. Effective troubleshooting reduces downtime and ensures that security measures are consistently applied across all endpoints.
Automation and Scheduled Tasks
The exam emphasizes the importance of automation in maintaining enterprise security. Candidates must be familiar with scheduling tasks, automating updates, and configuring automated responses to security events. This reduces the need for manual intervention, ensures timely policy enforcement, and enhances overall system efficiency. Knowledge of cron jobs, automated scans, and scheduled reporting allows administrators to maintain continuous protection while optimizing operational workflows.
Integration of Security Components
Candidates are expected to understand how different security components integrate within the enterprise environment. This includes coordinating antivirus software, ePolicy Orchestrator, firewall settings, and other endpoint protection tools. Understanding dependencies, data flow, and configuration interactions allows administrators to implement cohesive security strategies and minimize conflicts or redundancies. Integration skills ensure that all systems work together seamlessly to provide comprehensive protection.
Backup, Recovery, and Redundancy Planning
Effective system administration requires planning for backups, recovery, and redundancy. Candidates should know how to configure automated backups of configuration files, policy data, and system logs. Understanding recovery procedures for failed agents or servers is critical to maintain business continuity and reduce downtime. Knowledge of redundancy planning, including distributing repositories and ensuring failover capabilities, supports resilience and reliability in enterprise environments.
Advanced Reporting and Audit Capabilities
Generating advanced reports and conducting audits are essential for compliance and operational insight. Candidates must be able to create detailed audit logs, review historical events, and identify patterns or anomalies. Reporting skills enable administrators to communicate security posture, verify policy enforcement, and document compliance efforts. Proficiency in audits ensures that systems adhere to regulatory standards and organizational policies, providing accountability and transparency.
Policy Testing and Validation
Before deploying policies across the enterprise, candidates should understand how to test and validate their effectiveness. This involves simulating policy application, verifying agent responses, and checking endpoint compliance. Policy validation ensures that intended security measures are correctly implemented and that there are no unintended consequences. Candidates must also know how to adjust policies based on testing outcomes to optimize performance and protection.
Performance Tuning and Resource Management
Optimizing system performance is a critical area for the MA0-100 exam. Candidates should understand how to allocate resources, prioritize tasks, and manage workloads to prevent performance degradation. This includes tuning server settings, optimizing query execution, and managing memory and storage usage effectively. Resource management ensures that endpoints operate efficiently, policies are applied promptly, and system responsiveness remains high under varying conditions.
Threat Analysis and Prevention
Candidates are expected to demonstrate knowledge of identifying potential threats and implementing preventive measures. This involves analyzing security logs, monitoring alerts, and applying proactive configurations to mitigate risk. Understanding threat patterns, implementing firewall rules, and configuring antivirus protection are critical for maintaining a secure environment. Effective threat analysis supports proactive security management and minimizes the likelihood of breaches.
Endpoint Lifecycle Management
Managing the entire lifecycle of endpoints is another focus area. Candidates must be able to onboard new devices, deploy agents, apply policies, monitor compliance, and retire or reassign endpoints as necessary. Lifecycle management ensures that all devices are integrated into the system tree, maintain compliance, and contribute to the overall security posture. Understanding lifecycle processes enables administrators to maintain organization and control across large numbers of endpoints.
Custom Dashboards and Visualization
Creating custom dashboards and visualizations is essential for efficient system monitoring. Candidates should be able to design dashboards that highlight key metrics, policy compliance, agent status, and system health. Effective visualization allows administrators to quickly assess operational status, detect anomalies, and make informed decisions. Custom dashboards enhance situational awareness and support proactive management of security environments.
Change Management and Configuration Control
Candidates must understand how to manage changes to policies, configurations, and system settings. Change management ensures that updates are implemented systematically, documented properly, and tested before full deployment. Configuration control prevents accidental misconfigurations, maintains consistency, and supports audit requirements. Knowledge of change management processes ensures that system modifications do not compromise security or performance.
Proactive Monitoring and Alert Management
Proactive monitoring and alert management are critical for maintaining system integrity. Candidates should know how to configure alerts for policy violations, agent failures, and potential security incidents. Proactive monitoring enables administrators to respond quickly to issues, reduce downtime, and maintain compliance. Effective alert management ensures that critical events are addressed promptly and that the system remains secure and operational.
Documentation and Operational Procedures
Comprehensive documentation of operational procedures, policies, and system configurations is essential. Candidates are expected to maintain records of installation processes, agent deployments, policy settings, and troubleshooting actions. Documentation supports knowledge transfer, facilitates audits, and ensures continuity of operations in case of personnel changes. Well-maintained operational procedures provide a clear reference for managing complex security environments efficiently.
Continuous Improvement and System Evaluation
Finally, candidates should be proficient in evaluating system performance and implementing continuous improvements. This involves analyzing reports, reviewing policies, and optimizing configurations based on emerging threats and performance metrics. Continuous evaluation ensures that the security environment adapts to new challenges, maintains high performance, and continues to meet organizational standards. Candidates who master these skills are equipped to maintain robust, efficient, and adaptive enterprise security systems
Comprehensive Understanding of Server Architecture
For the MA0-100 exam, candidates must have an in-depth understanding of the underlying server architecture of McAfee ePolicy Orchestrator. This includes knowledge of database structures, repository management, and the interactions between different system components. A clear understanding of how data flows between agents, repositories, and the server allows administrators to optimize system performance, prevent bottlenecks, and troubleshoot issues effectively.
Understanding the architecture also includes familiarity with the software stack, network dependencies, and the configuration of system services. Candidates should be capable of designing environments that are resilient, scalable, and maintainable. Knowledge of the server’s role in handling requests, processing policies, and generating reports is crucial for ensuring reliable operations.
Advanced Agent Management Strategies
Candidates need to demonstrate expertise in managing agents across the enterprise environment. This includes deploying agents efficiently, verifying their connectivity, and monitoring their operational status. Understanding agent update mechanisms, communication protocols, and failover procedures ensures that endpoints remain protected and compliant.
Advanced agent management also involves analyzing agent logs, identifying communication failures, and resolving configuration issues. Candidates must be capable of coordinating peer-to-peer updates, distributed repository synchronization, and handling large-scale deployments while minimizing disruptions. Proper agent management contributes to overall system stability and ensures consistent application of security policies.
Policy Hierarchies and Conflict Resolution
The MA0-100 exam tests candidates on their ability to design and manage complex policy hierarchies. Understanding the relationships between global, group, and individual policies allows administrators to enforce rules effectively without causing conflicts. Candidates must be able to resolve conflicts that arise from overlapping policies and ensure that the correct settings are applied to each endpoint.
Knowledge of policy precedence, inheritance, and exception handling is essential. Candidates should also understand how to use policy testing environments to validate configurations before deployment. Effective policy management minimizes errors, ensures compliance, and enhances the overall security posture of the enterprise.
System Tree Optimization and Endpoint Classification
Optimizing the system tree is a key skill for the exam. Candidates should be able to categorize endpoints based on roles, risk levels, or operational requirements and assign them to appropriate groups. Proper classification facilitates targeted policy deployment, simplifies monitoring, and ensures that compliance requirements are met efficiently.
Candidates should be proficient in detecting and managing rogue or non-compliant systems. This involves tagging endpoints, auditing group structures, and reorganizing the system tree as necessary to maintain clarity and operational efficiency. A well-maintained system tree supports rapid troubleshooting, effective reporting, and streamlined administration.
Reporting, Dashboards, and Data Interpretation
Generating reports and interpreting data are central to exam competency. Candidates must be able to create queries that extract meaningful insights from system logs, agent statuses, and policy compliance information. They should understand how to use dashboards and visualization tools to monitor system health, track incidents, and communicate findings effectively.
Data interpretation involves analyzing trends, identifying anomalies, and providing actionable insights to improve security measures. Candidates must be able to generate comprehensive reports that guide decision-making, support audits, and verify compliance. Advanced reporting skills ensure that administrators can maintain visibility and control over enterprise security operations.
Troubleshooting Complex System Issues
Troubleshooting is a critical aspect of the MA0-100 exam. Candidates should be able to diagnose and resolve issues related to agent communication, server performance, policy enforcement, and system tree inconsistencies. Understanding root causes, analyzing logs, and implementing corrective actions are essential skills.
Effective troubleshooting requires systematic approaches, including verifying system configurations, testing connectivity, and monitoring results. Candidates must be capable of handling both common and complex issues, ensuring that endpoints remain secure and operational. Proactive problem-solving reduces downtime and maintains the integrity of the enterprise security environment.
Automation and Task Scheduling
Candidates are expected to understand automation features within the system, including task scheduling, automated updates, and policy enforcement mechanisms. Automating repetitive tasks reduces administrative burden, improves efficiency, and ensures consistent application of security measures.
Knowledge of scheduling tools, automated scans, and event-triggered actions is essential. Candidates should also be capable of monitoring automated tasks, verifying successful execution, and adjusting configurations to optimize performance. Automation ensures continuous protection, timely policy application, and efficient system operations.
Security Event Analysis and Threat Mitigation
Understanding security events and implementing mitigation strategies is essential for the exam. Candidates should be able to monitor alerts, analyze potential threats, and respond appropriately to protect endpoints. Knowledge of incident response workflows, automated remediation, and threat prioritization enables administrators to maintain a proactive security posture.
Candidates should also be able to document security events, track resolution progress, and adjust policies based on lessons learned. Effective threat mitigation ensures that the system can handle emerging risks, maintain compliance, and safeguard sensitive information across all endpoints.
Backup, Recovery, and Disaster Planning
Enterprise environments require comprehensive backup and recovery strategies. Candidates should understand how to configure automated backups of repositories, policy data, and system logs. Knowledge of recovery procedures for failed agents or server components is critical to ensure business continuity.
Disaster planning involves setting up redundancy, distributing repositories, and ensuring failover capabilities. Candidates must be capable of designing systems that recover quickly from failures while minimizing data loss and operational disruption. A robust backup and recovery plan supports resilience, reliability, and long-term system stability.
System Maintenance and Patch Management
Routine maintenance and patch management are important competencies for the exam. Candidates should be able to schedule and implement updates, verify system integrity, and manage resources efficiently. Regular maintenance prevents vulnerabilities, ensures system stability, and maintains compliance with organizational policies.
Candidates must also be proficient in assessing the impact of updates, resolving conflicts, and validating successful deployments. Proper maintenance practices ensure that endpoints remain protected, policies are applied correctly, and overall system performance is optimized.
Scalability and Performance Tuning
Candidates should understand principles of scalability and performance tuning for large-scale deployments. This includes managing server resources, optimizing query execution, and balancing workloads across multiple endpoints. Knowledge of indexing, caching, and repository optimization contributes to enhanced system responsiveness.
Performance tuning also involves analyzing system metrics, identifying bottlenecks, and implementing solutions to maintain efficiency under heavy loads. Candidates must ensure that security measures do not degrade performance and that endpoints continue to operate effectively during high-demand periods.
Lifecycle Management of Endpoints
Managing the lifecycle of endpoints is a key area of focus. Candidates should be able to onboard new devices, deploy agents, assign policies, monitor compliance, and retire endpoints as needed. Lifecycle management ensures that all endpoints are tracked, protected, and properly integrated into the system tree.
Understanding endpoint lifecycle processes allows administrators to maintain security, streamline policy deployment, and ensure organizational consistency. Candidates must be capable of managing transitions effectively, including hardware replacements, role changes, and decommissioning of outdated systems.
Customization of Dashboards and Monitoring Tools
Effective monitoring requires the ability to customize dashboards and monitoring tools. Candidates should be able to configure dashboards to highlight critical metrics, track incidents, and provide visual insights into system health. Customization enhances situational awareness and supports proactive management of security operations.
Candidates must also understand how to configure alerts, notifications, and automated monitoring rules to detect deviations from expected behavior. Tailored dashboards and monitoring setups ensure timely response to issues and improved visibility into enterprise security performance.
Change Management and Configuration Audits
Change management and configuration audits are essential skills for the MA0-100 exam. Candidates should be able to document system changes, track policy adjustments, and ensure consistency across all endpoints. Configuration audits verify that changes are implemented correctly and that the environment remains compliant with organizational standards.
Candidates must also be capable of testing changes in controlled environments before full deployment. Effective change management prevents misconfigurations, reduces operational risk, and maintains the integrity of security operations.
Continuous Evaluation and Improvement
Candidates are expected to understand the importance of continuous evaluation and improvement. This involves analyzing system performance, reviewing policy effectiveness, and implementing updates based on observed trends. Continuous improvement ensures that the enterprise security environment adapts to evolving threats, maintains efficiency, and meets organizational objectives.
Candidates must develop strategies for ongoing assessment, including periodic reviews of agent performance, policy compliance, system metrics, and incident response effectiveness. A focus on continuous improvement ensures that security operations remain robust, reliable, and capable of addressing emerging challenges.
Knowledge Integration and Practical Application
Practical application of knowledge is essential for the MA0-100 exam. Candidates should combine theoretical understanding with hands-on experience in configuring servers, managing agents, enforcing policies, analyzing reports, and troubleshooting issues. This integrated approach ensures that candidates can operate effectively in real-world environments.
Working on practical scenarios allows candidates to internalize workflows, understand dependencies between system components, and develop problem-solving skills. Mastery of integrated knowledge ensures that administrators can maintain secure, compliant, and optimized environments across the enterprise.
The MA0-100 exam assesses comprehensive capabilities in server configuration, agent management, policy enforcement, system monitoring, reporting, troubleshooting, automation, threat mitigation, backup and recovery, performance tuning, endpoint lifecycle management, dashboard customization, change management, and continuous improvement. Candidates who master these areas are equipped to manage complex enterprise security environments efficiently, maintain compliance, optimize performance, and ensure reliable protection for all endpoints
Comprehensive Server Administration
For the MA0-100 exam, candidates must demonstrate a thorough understanding of server administration, including deployment, configuration, and maintenance of McAfee ePolicy Orchestrator environments. This involves designing servers to handle high-volume endpoint interactions, optimizing database performance, and ensuring reliable communication between agents and the server. Candidates should be familiar with server roles, service dependencies, and the integration of repositories to ensure smooth system operations. Effective server administration includes managing resources, monitoring logs, and performing preventive maintenance to maintain a stable and secure environment.
Advanced Endpoint Management
Candidates need to manage endpoints efficiently by deploying agents, monitoring health, and ensuring compliance with security policies. Understanding how to group endpoints, assign targeted policies, and maintain system trees is critical. Candidates should be able to handle dynamic endpoint populations, reorganize groups as needed, and detect rogue or non-compliant systems. Knowledge of agent lifecycle management, including onboarding, updates, communication checks, and retirement, ensures consistent protection across all devices.
Policy Design and Optimization
Policy management is a cornerstone of the MA0-100 exam. Candidates must know how to design policies for antivirus, firewall, and compliance requirements, while understanding inheritance, precedence, and exceptions. Optimizing policies involves testing them in controlled environments, verifying application accuracy, and ensuring that policies do not conflict or impede operations. Candidates should be able to manage large-scale policy deployments, adjust configurations dynamically, and maintain alignment with organizational security objectives.
Advanced Monitoring and Reporting
Monitoring system health, agent status, and compliance metrics is essential for effective administration. Candidates should be able to configure dashboards, generate reports, and analyze trends for informed decision-making. Reporting involves creating queries to extract meaningful data from logs and system events, visualizing metrics for quick assessment, and identifying anomalies or potential threats. Candidates must interpret these reports to optimize performance, detect security risks, and guide operational improvements.
Troubleshooting Complex Scenarios
Troubleshooting is a critical skill tested in the exam. Candidates must identify and resolve issues related to server performance, agent connectivity, policy application, and system tree structure. Understanding the root causes of problems, analyzing logs, and applying corrective measures are necessary for restoring normal operations. Effective troubleshooting also requires anticipating potential failures, implementing contingency plans, and ensuring that system stability and security are maintained during resolution.
Automation and Task Management
Candidates should be proficient in automating routine tasks such as policy enforcement, agent updates, and security scans. Knowledge of scheduling tools, automated responses, and event-driven actions is important to reduce manual workload and improve operational efficiency. Effective task management ensures timely application of updates, consistent policy enforcement, and continuous monitoring of system health. Candidates must be able to configure and verify automated tasks, adjusting them to respond to evolving operational needs.
Incident Response and Threat Mitigation
Understanding how to respond to incidents and mitigate threats is a core area of the exam. Candidates should be able to analyze security events, determine severity, and initiate appropriate actions. This includes configuring automated remediation, monitoring alerts, and coordinating policy adjustments to address potential vulnerabilities. Effective incident response minimizes downtime, prevents data breaches, and maintains the integrity of the security environment.
Backup, Recovery, and Redundancy Planning
Candidates must be able to configure comprehensive backup and recovery strategies. This involves automating backups of repositories, policies, and system logs, and designing failover mechanisms to maintain continuity. Knowledge of disaster recovery planning, including redundancy and distributed repositories, ensures that critical systems remain operational during failures. Candidates must also be capable of restoring systems quickly and verifying the integrity of recovered data to maintain security and operational efficiency.
Performance Optimization
Performance tuning is essential for managing large-scale deployments. Candidates should understand resource allocation, workload balancing, and query optimization to maintain system responsiveness. Knowledge of indexing, caching, and repository management helps reduce latency and improves agent communication. Candidates must ensure that security measures are applied efficiently without negatively impacting endpoint performance or system responsiveness.
Lifecycle Management of Systems and Policies
Candidates should be proficient in managing the lifecycle of endpoints, policies, and system configurations. This includes onboarding new devices, deploying policies, monitoring compliance, and retiring outdated components. Proper lifecycle management ensures that endpoints are consistently protected, policies remain current, and the system tree accurately reflects organizational structures. Candidates must be capable of adapting lifecycle management practices to evolving enterprise needs and changing security requirements.
Custom Dashboards and Visualization
Candidates are expected to design and customize dashboards to display critical metrics and trends. Effective visualization allows administrators to monitor security events, agent performance, and policy compliance efficiently. Candidates should be able to configure dashboards to highlight anomalies, track operational performance, and provide actionable insights. Custom dashboards improve situational awareness and facilitate rapid response to emerging issues.
Change Management and Configuration Control
Managing changes in policies, configurations, and system settings is a critical skill. Candidates should be able to document changes, verify their impact, and ensure consistency across endpoints. Change management practices prevent misconfigurations, reduce operational risk, and support compliance audits. Candidates must test changes before full deployment, monitor results, and adjust configurations to maintain optimal performance and security.
Proactive Monitoring and Alerting
Proactive monitoring involves configuring alerts, tracking system events, and identifying deviations from expected behavior. Candidates should know how to set thresholds, configure notifications, and respond to critical incidents promptly. Proactive alerting ensures that potential issues are addressed quickly, minimizing downtime and maintaining security. Candidates must integrate monitoring tools with operational workflows to maintain a responsive and secure environment.
Documentation and Knowledge Management
Maintaining detailed documentation of configurations, policies, and operational procedures is essential. Candidates should be able to record installation steps, agent deployments, policy updates, and troubleshooting activities. Proper documentation supports continuity, facilitates audits, and ensures that knowledge is retained within the organization. Knowledge management allows administrators to maintain consistency, train new personnel, and standardize operational practices.
Continuous Evaluation and Improvement
Candidates must be able to evaluate system performance, policy effectiveness, and operational workflows continuously. This involves reviewing reports, analyzing trends, and implementing adjustments based on observed outcomes. Continuous improvement ensures that the enterprise security environment remains effective, responsive, and aligned with organizational objectives. Candidates should develop strategies for ongoing assessment, optimization, and adaptation to emerging threats or changing requirements.
Integration and Interoperability
Understanding how different components of the security infrastructure interact is critical. Candidates should know how agents, servers, policies, and reporting tools integrate to create a cohesive system. This includes managing dependencies, ensuring data consistency, and resolving conflicts between components. Effective integration supports seamless operations, reduces administrative overhead, and enhances the overall security posture of the enterprise.
Strategic Planning and Risk Assessment
Candidates should be able to plan strategically for security operations, including assessing risks, prioritizing resources, and preparing for potential threats. This involves evaluating system capabilities, identifying vulnerabilities, and implementing preventive measures. Strategic planning ensures that security operations are proactive, resilient, and capable of handling complex enterprise environments efficiently.
Real-World Scenario Management
The MA0-100 exam requires candidates to apply their knowledge to realistic scenarios. This includes simulating deployment challenges, troubleshooting complex issues, and managing multi-layered policies across diverse endpoints. Practical scenario management tests candidates’ ability to integrate skills, make informed decisions, and maintain secure and compliant environments under operational pressure.
Collaboration and Communication
Candidates must demonstrate the ability to work collaboratively with other IT and security teams. This includes sharing insights from reports, coordinating incident responses, and communicating policy changes effectively. Strong collaboration ensures that security operations align with broader organizational goals and that issues are addressed comprehensively and efficiently.
Conclusion
The MA0-100 exam evaluates a candidate’s ability to manage enterprise security systems comprehensively, covering server administration, agent management, policy design, monitoring, reporting, troubleshooting, automation, incident response, backup and recovery, performance optimization, lifecycle management, dashboards, change control, proactive monitoring, documentation, continuous improvement, integration, strategic planning, scenario management, and collaboration. Mastery of these areas equips candidates to maintain secure, compliant, and efficient enterprise environments, demonstrating readiness to handle complex operational challenges and maintain high standards of security and performance
McAfee MA0-100 practice test questions and answers, training course, study guide are uploaded in ETE Files format by real users. Study and Pass MA0-100 Certified McAfee Security Specialist - ePO certification exam dumps & practice test questions and answers are to help students.
Why customers love us?
What do our customers say?
The resources provided for the McAfee certification exam were exceptional. The exam dumps and video courses offered clear and concise explanations of each topic. I felt thoroughly prepared for the MA0-100 test and passed with ease.
Studying for the McAfee certification exam was a breeze with the comprehensive materials from this site. The detailed study guides and accurate exam dumps helped me understand every concept. I aced the MA0-100 exam on my first try!
I was impressed with the quality of the MA0-100 preparation materials for the McAfee certification exam. The video courses were engaging, and the study guides covered all the essential topics. These resources made a significant difference in my study routine and overall performance. I went into the exam feeling confident and well-prepared.
The MA0-100 materials for the McAfee certification exam were invaluable. They provided detailed, concise explanations for each topic, helping me grasp the entire syllabus. After studying with these resources, I was able to tackle the final test questions confidently and successfully.
Thanks to the comprehensive study guides and video courses, I aced the MA0-100 exam. The exam dumps were spot on and helped me understand the types of questions to expect. The certification exam was much less intimidating thanks to their excellent prep materials. So, I highly recommend their services for anyone preparing for this certification exam.
Achieving my McAfee certification was a seamless experience. The detailed study guide and practice questions ensured I was fully prepared for MA0-100. The customer support was responsive and helpful throughout my journey. Highly recommend their services for anyone preparing for their certification test.
I couldn't be happier with my certification results! The study materials were comprehensive and easy to understand, making my preparation for the MA0-100 stress-free. Using these resources, I was able to pass my exam on the first attempt. They are a must-have for anyone serious about advancing their career.
The practice exams were incredibly helpful in familiarizing me with the actual test format. I felt confident and well-prepared going into my MA0-100 certification exam. The support and guidance provided were top-notch. I couldn't have obtained my McAfee certification without these amazing tools!
The materials provided for the MA0-100 were comprehensive and very well-structured. The practice tests were particularly useful in building my confidence and understanding the exam format. After using these materials, I felt well-prepared and was able to solve all the questions on the final test with ease. Passing the certification exam was a huge relief! I feel much more competent in my role. Thank you!
The certification prep was excellent. The content was up-to-date and aligned perfectly with the exam requirements. I appreciated the clear explanations and real-world examples that made complex topics easier to grasp. I passed MA0-100 successfully. It was a game-changer for my career in IT!