- Home
- Checkpoint Certifications
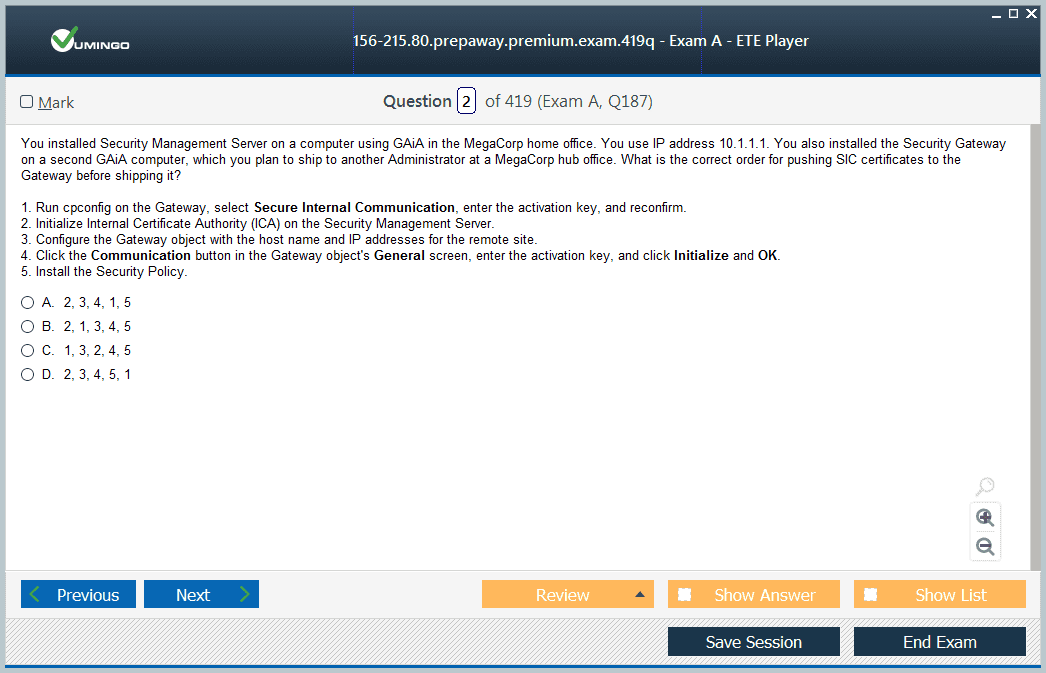
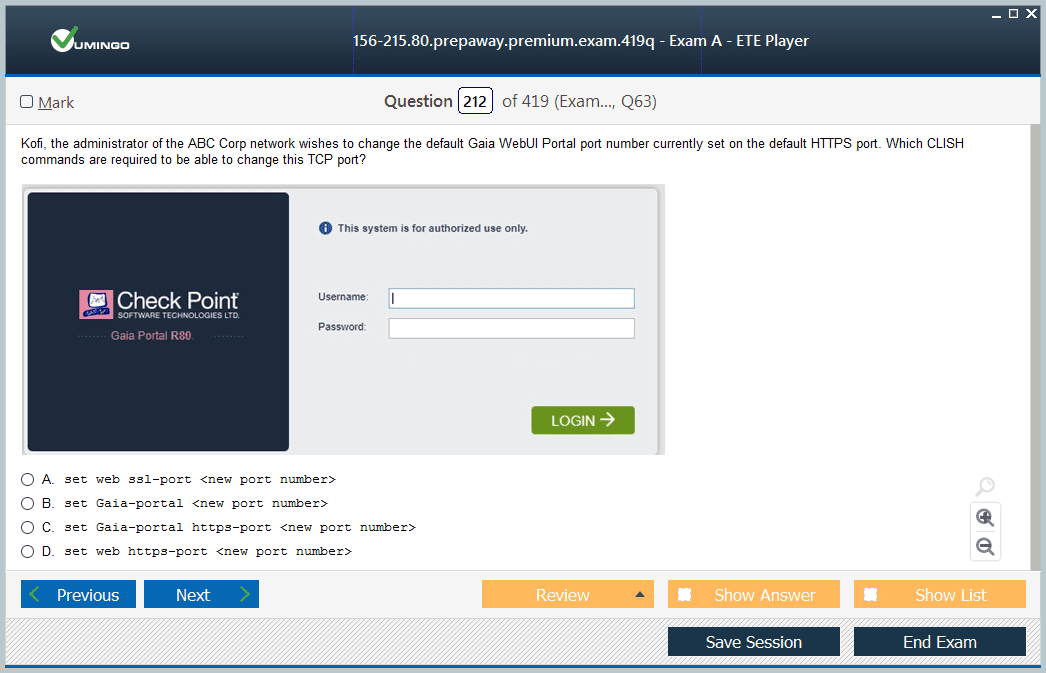
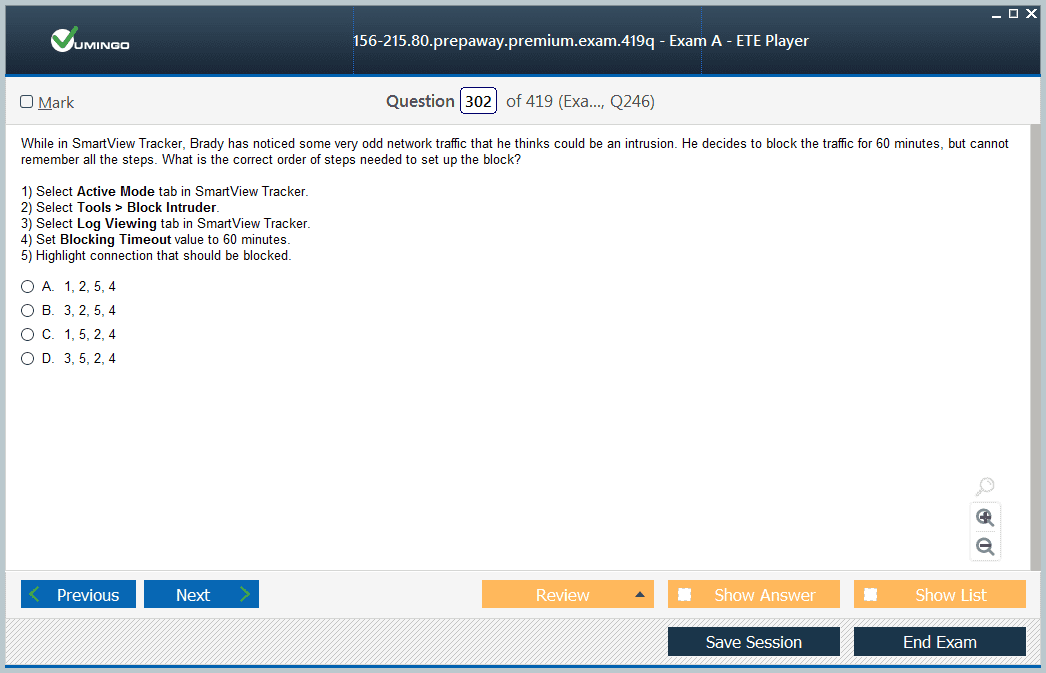
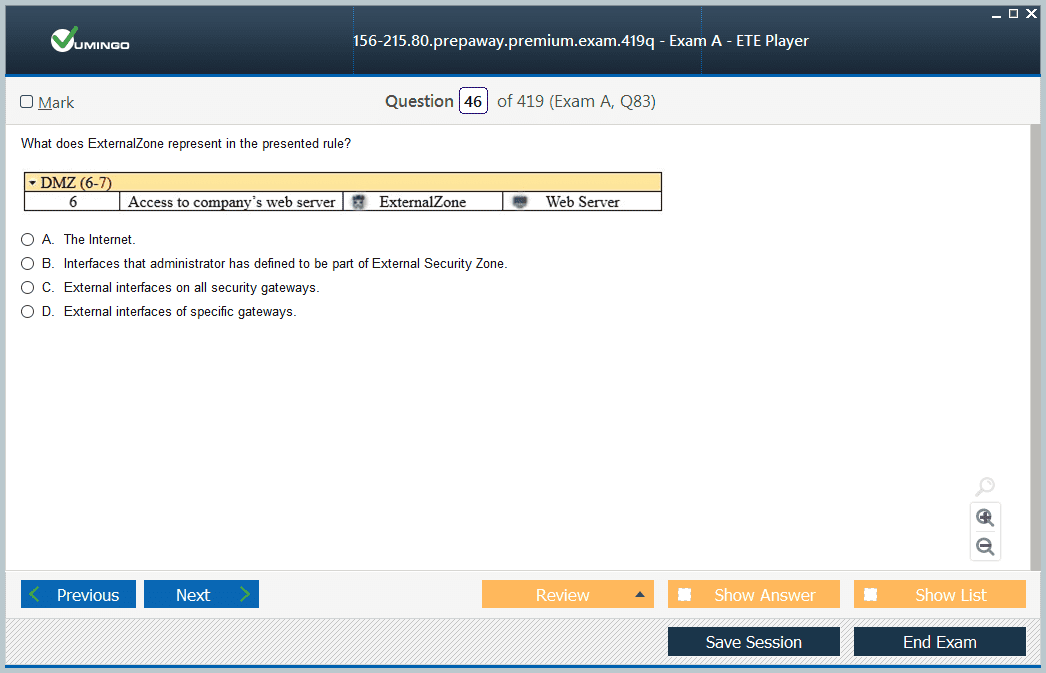
- 156-215.80 Check Point Certified Security Administrator (CCSA R80) Dumps
Pass Checkpoint CCSA 156-215.80 Exam in First Attempt Guaranteed!
Get 100% Latest Exam Questions, Accurate & Verified Answers to Pass the Actual Exam!
30 Days Free Updates, Instant Download!


156-215.80 Premium Bundle
- Premium File 536 Questions & Answers. Last update: Jan 20, 2026
- Training Course 48 Video Lectures
Last Week Results!

Includes question types found on the actual exam such as drag and drop, simulation, type-in and fill-in-the-blank.

Based on real-life scenarios similar to those encountered in the exam, allowing you to learn by working with real equipment.
All Checkpoint CCSA 156-215.80 certification exam dumps, study guide, training courses are Prepared by industry experts. PrepAway's ETE files povide the 156-215.80 Check Point Certified Security Administrator (CCSA R80) practice test questions and answers & exam dumps, study guide and training courses help you study and pass hassle-free!
From Fundamentals to Proficiency: Checkpoint 156-215.80 Certification Guide
The Checkpoint 156-215.80 certification exam, commonly referred to as the Checkpoint Certified Security Administrator exam, is designed for professionals who want to validate their knowledge and skills in managing Checkpoint security solutions. It focuses on the foundational level of security administration, making it ideal for individuals who are looking to step into the world of network and cybersecurity or for those who are already working with security technologies but wish to formalize and strengthen their expertise. The exam tests both theoretical understanding and hands-on practical skills, ensuring that certified individuals are capable of performing the responsibilities expected of a security administrator in real working environments.
Checkpoint security solutions are widely recognized for their role in protecting enterprise environments, and the certification ensures that candidates are able to configure, implement, and maintain these technologies effectively. The exam is not simply a measure of memorized concepts; it evaluates the candidate’s ability to think critically about configurations, manage policies, and handle security incidents. For this reason, preparation must be both comprehensive and practical, with attention given to how concepts apply in real situations rather than purely theoretical scenarios.
Core Objectives of the Exam
The primary aim of the 156-215.80 exam is to measure a candidate’s ability to manage and secure Checkpoint Security Gateway and Management systems. This includes setting up security policies that define what traffic is allowed, configuring firewall rules, and ensuring secure access for authorized users while denying unauthorized attempts. Another key component of the exam is the candidate’s ability to monitor ongoing activity, interpret logs, and respond to threats or unusual behavior that might indicate an attempted attack.
Candidates are also expected to demonstrate knowledge of installing security gateways, performing initial configuration tasks, and integrating them into a larger network environment. Understanding network address translation, secure communication using VPNs, and handling basic troubleshooting tasks are also part of the objectives. By mastering these concepts, candidates are able to ensure smooth functioning of enterprise systems while protecting them from external and internal threats.
What makes the exam particularly valuable is the focus on real-world application. For instance, configuring a policy is not just about knowing which button to click, but also about understanding the broader implications of that policy on business operations, user productivity, and overall network security. This approach ensures that those who pass the exam are well-prepared to handle the challenges of actual security administration roles.
Practical Skills Gained Through Preparation
Preparing for the 156-215.80 exam equips candidates with a wide range of skills that go beyond the exam itself. These skills are directly transferable to professional environments, making certified administrators highly effective in their roles. One of the first skills developed is the ability to install and configure a Checkpoint security gateway. This involves working with the management interface, applying initial security settings, and ensuring that the system integrates with the broader network infrastructure without disruption.
Another important skill is policy management. Candidates learn how to create, modify, and optimize security rules that dictate how traffic flows through the network. This includes understanding the importance of allowing necessary communication while blocking potentially harmful traffic. Policy management also involves reviewing and optimizing rules to maintain efficiency and prevent conflicts that might cause disruptions.
Monitoring and log analysis form another critical part of the skillset. Administrators must be able to interpret data from logs to detect suspicious activity, trace potential security incidents, and take corrective action before damage occurs. Developing this ability requires practice in identifying patterns and anomalies that might indicate malicious behavior.
Additionally, candidates preparing for the exam strengthen their troubleshooting capabilities. This involves diagnosing common configuration errors, network issues, or policy conflicts and resolving them quickly to minimize downtime. Troubleshooting skills not only help in passing the exam but also prove invaluable in real job roles where quick problem resolution is essential for maintaining network reliability.
Career Impact of the 156-215.80 Certification
Earning the 156-215.80 certification has a significant impact on career opportunities in the field of network and security administration. It serves as an official validation of the individual’s knowledge and competence with Checkpoint technologies, which are widely used across organizations of different sizes and industries. Employers view certification holders as individuals who have proven their ability to handle the responsibilities of securing networks, which makes them valuable additions to security teams.
This certification is often sought by professionals aiming to move into dedicated security roles or advance from general networking positions to specialized security administration. It can open doors to positions such as security administrator, firewall administrator, and network security specialist. Beyond the job title itself, the certification demonstrates the ability to protect enterprise networks from modern threats, which is a skillset in consistently high demand.
From a professional development standpoint, the certification provides a solid foundation on which individuals can build more advanced knowledge and expertise. The ability to understand the essentials of Checkpoint solutions, combined with hands-on skills in configuration and troubleshooting, creates a strong base for further career growth in cybersecurity. This foundation allows professionals to tackle more complex responsibilities in the future, whether that involves managing larger infrastructures or moving into roles with greater responsibility for security strategy and design.
Strategies for Effective Preparation
Preparing for the 156-215.80 exam requires a structured approach that balances theory, practice, and review. One of the first steps in preparation is understanding the exam objectives thoroughly. Each objective corresponds to a real-world task that administrators must perform, and familiarity with these objectives ensures that study efforts are targeted and efficient. Candidates who align their study plans with the objectives avoid wasting time on unrelated content and instead focus on the knowledge that will be directly assessed.
Using multiple study resources is another key element of preparation. Different materials provide different perspectives, and by reviewing more than one resource, candidates reinforce their understanding of complex concepts. For example, one guide may explain a configuration process step by step, while another might provide deeper insight into why a specific setting is important for security. Combining these approaches helps build both practical skills and theoretical understanding.
Hands-on practice is arguably the most important part of preparation. Building a lab environment, even a small one using virtual machines, allows candidates to experiment with configurations, policies, and troubleshooting scenarios in a safe setting. This practice not only makes concepts clearer but also builds the confidence needed to perform these tasks under exam conditions. Practical experience often makes the difference between simply memorizing commands and truly understanding how to apply them effectively.
Another strategy that contributes significantly to preparation is the use of practice exams. These help candidates become familiar with the structure and format of the test, as well as the type of questions they might encounter. Taking practice exams also highlights weak areas, allowing candidates to focus additional study on those topics before the real exam. Reviewing answers, especially incorrect ones, is a powerful way to deepen understanding and ensure readiness.
Finally, maintaining a consistent study schedule ensures that preparation progresses steadily. Breaking down study goals into smaller, achievable targets keeps motivation high and reduces the risk of last-minute stress. By pacing themselves properly, candidates can cover all the material in depth without feeling overwhelmed.
Building Confidence for Exam Day
Beyond mastering the material, candidates must also prepare themselves mentally for the exam. Confidence plays a critical role in performance, and one way to build it is by practicing active learning techniques. Explaining concepts to others, summarizing topics in personal notes, or even teaching oneself out loud are methods that reinforce memory and comprehension. The more comfortable a candidate feels with the material, the more confident they will be on exam day.
Time management is another factor in building confidence. During preparation, candidates should practice answering questions under timed conditions to simulate the actual exam environment. This reduces anxiety and ensures that they can allocate enough time to each question without rushing or leaving items unanswered.
Maintaining personal well-being is also essential. Adequate rest, proper nutrition, and regular breaks during study sessions contribute to sharper focus and improved performance. On the day of the exam, arriving with a clear mind and a calm approach can make a significant difference in how effectively knowledge is applied.
The Checkpoint 156-215.80 certification exam provides an essential foundation for professionals pursuing a career in network security administration. It validates both theoretical understanding and practical skills in configuring, managing, and maintaining Checkpoint security solutions. Through focused preparation, hands-on practice, and consistent review, candidates can build the expertise needed to succeed in the exam and apply their knowledge in real-world environments.
Achieving this certification not only enhances career opportunities but also provides practical skills that can be immediately applied in professional roles. By approaching preparation with dedication and a structured plan, candidates can confidently demonstrate their ability to secure enterprise networks and establish themselves as capable security administrators.
Deep Dive into the 156-215.80 Exam Structure
The 156-215.80 exam is specifically designed to validate a candidate’s ability to work with Checkpoint security technologies at the administrative level. It is not only a test of memory but a comprehensive assessment of knowledge application, problem-solving, and critical decision-making. The structure of the exam covers multiple sections that reflect real-world tasks an administrator is expected to perform daily. These include installation and configuration of security gateways, policy management, traffic inspection, user access control, and network address translation. A key part of the exam also involves demonstrating the ability to use monitoring tools effectively and respond to potential threats.
Understanding the structure helps candidates allocate their preparation time wisely. While every topic is essential, some areas like security policies, VPNs, and troubleshooting are tested more rigorously. The exam often includes scenario-based questions that require applying multiple concepts together, ensuring that candidates understand the interconnected nature of network security.
Installation and Configuration Knowledge
The installation and configuration component of the exam requires candidates to understand how to set up Checkpoint Security Gateways and Management servers from the ground up. This begins with deploying the operating system, initializing security software, and establishing initial connectivity. Candidates must be familiar with basic command-line instructions and graphical interfaces used to configure the system.
During this phase, candidates are also tested on licensing, software updates, and connecting the management server with security gateways. Proper configuration ensures that gateways communicate securely with management tools, allowing administrators to monitor and enforce policies consistently. An often overlooked but critical part of installation is ensuring that system resources are allocated appropriately to avoid performance bottlenecks, which is also assessed in the exam indirectly through scenario-based questions.
Security Policy Management
Policy management forms one of the largest portions of the 156-215.80 exam. A security administrator must be able to create and manage rules that control how traffic flows in and out of the network. This includes defining which applications, services, and users are permitted access and which must be restricted. The exam evaluates the candidate’s ability to build structured policies, optimize rule order, and prevent conflicts between overlapping rules.
Understanding how security policies impact business operations is vital. Candidates need to strike a balance between tightening security and ensuring legitimate communication flows smoothly. For example, blocking unnecessary ports is essential, but doing so without considering required business services can result in downtime. The exam scenarios highlight this by presenting situations where poorly designed policies could interfere with operations, requiring candidates to choose the correct adjustments.
Another crucial aspect is policy verification. Once policies are configured, administrators must validate their correctness by monitoring logs, testing connectivity, and ensuring that intended rules function properly without unintended side effects. This is a practical skill that candidates are expected to demonstrate in the exam context.
Network Address Translation in the Exam
Network Address Translation is another key area covered in the 156-215.80 exam. NAT allows internal private addresses to communicate with external networks by mapping them to public addresses. Administrators must know how to configure both static and dynamic NAT, depending on the needs of the network.
Static NAT is useful for servers that need consistent external access, such as web servers, while dynamic NAT is more suitable for client machines requiring occasional internet connectivity. Candidates must also understand the security implications of each configuration, such as preventing unintended exposure of internal resources. The exam often includes questions that involve troubleshooting NAT rules, where candidates must identify why a connection is failing and apply the correct adjustment.
The exam does not only test whether the candidate can set up NAT but also whether they can integrate it with existing policies, ensuring no conflicts arise. Mastery of NAT demonstrates a candidate’s ability to handle complex networking tasks while maintaining strong security.
VPN Configuration and Management
Virtual Private Networks play a central role in modern network security, and this is reflected in the exam objectives. The 156-215.80 exam requires candidates to know how to configure site-to-site and remote-access VPNs. Site-to-site VPNs are used for connecting different office locations securely, while remote-access VPNs allow users to connect to the corporate network from outside securely.
Candidates must understand encryption protocols, authentication methods, and key exchange mechanisms used in VPNs. The exam tests not only configuration steps but also the ability to troubleshoot issues such as failed tunnel negotiations or mismatched policies. Candidates are expected to interpret logs and identify where the problem lies, whether in encryption settings, peer configurations, or firewall rules blocking VPN traffic.
The role of VPNs in enabling secure communication for enterprises makes this a high-value section of the exam. Properly configured VPNs protect sensitive data as it travels over untrusted networks, and the exam ensures that candidates can implement this effectively.
Monitoring and Log Analysis
Another important component of the 156-215.80 exam is the ability to monitor network activity and analyze logs. Administrators are expected to use Checkpoint monitoring tools to gain visibility into traffic flows, identify anomalies, and respond to security incidents.
Candidates must be familiar with how to filter logs to find specific information, interpret different types of log entries, and recognize signs of attacks such as port scans, brute-force login attempts, or unusual traffic patterns. The exam evaluates how well candidates can distinguish between normal activity and potential threats, which is crucial in preventing and mitigating attacks.
Log analysis also ties back to other objectives such as policy management and VPN configuration. For example, if a VPN tunnel fails, the logs may show mismatched encryption methods or missing rules, and candidates must be able to piece this information together to resolve the issue. The ability to read and understand logs effectively demonstrates practical troubleshooting ability, making this a skill heavily emphasized in the exam.
Troubleshooting and Problem Resolution
Troubleshooting is one of the most practical aspects of the 156-215.80 exam. Candidates are expected to diagnose and resolve common issues that administrators face on a daily basis. These could include connectivity failures, misconfigured policies, licensing problems, or performance bottlenecks.
The exam emphasizes a systematic approach to troubleshooting. Candidates must know how to isolate the problem, check relevant logs or configurations, and implement changes without causing new issues. A structured method ensures that problems are resolved efficiently, reducing downtime and maintaining security.
Troubleshooting scenarios in the exam are often presented in a way that tests both technical skill and logical reasoning. For instance, a connectivity issue may be due to overlapping rules in a security policy, a missing NAT entry, or a blocked VPN port. The candidate must analyze the evidence provided and choose the correct resolution, demonstrating their ability to think critically under pressure.
Building a Study Plan for Success
Success in the 156-215.80 exam depends on careful preparation and consistent practice. A well-structured study plan begins with reviewing the official exam objectives and breaking them into manageable topics. Candidates should allocate dedicated time to each topic, ensuring they develop both theoretical understanding and practical skills.
Hands-on labs are essential in preparation. Setting up a virtual environment with Checkpoint software allows candidates to practice real configurations, experiment with policies, and troubleshoot simulated issues. This type of practice reinforces concepts in a way that reading alone cannot achieve.
Practice exams should also be included in the study plan. These help candidates familiarize themselves with the exam format, question styles, and timing. Reviewing incorrect answers provides insight into weak areas that need further study. Over time, this builds confidence and ensures readiness for the real exam.
Consistency is the key to effective preparation. Spacing out study sessions over several weeks allows for gradual reinforcement of concepts, while last-minute cramming often leads to gaps in understanding. A steady pace ensures that knowledge is deeply absorbed and easily recalled during the exam.
The Checkpoint 156-215.80 exam is a comprehensive assessment of the skills required to manage and secure enterprise networks using Checkpoint technologies. It covers essential areas such as installation, policy management, NAT, VPNs, monitoring, and troubleshooting. By mastering these areas, candidates not only prepare to pass the exam but also build practical skills that are directly applicable in professional roles.
Preparation requires a balance of theory, practice, and review. A structured study plan, hands-on lab experience, and practice exams contribute to thorough readiness. The certification validates a candidate’s ability to protect networks from modern threats and demonstrates their competence as a security administrator. For professionals aiming to advance in network security, achieving the 156-215.80 certification is a critical step that establishes both credibility and practical expertise.
Advanced Security Features in the 156-215.80 Exam
The 156-215.80 exam goes beyond basic administration and expects candidates to demonstrate knowledge of advanced security features built into Checkpoint technologies. These features are designed to address evolving threats and ensure comprehensive protection across an enterprise network. One such area is the use of Application Control and URL Filtering. Administrators must be able to identify and control traffic at the application level rather than relying solely on ports and protocols. This means recognizing applications that use dynamic ports or encrypted traffic, which traditional firewalls might miss. The exam requires candidates to understand how to implement rules that allow or restrict access to specific applications or categories, such as social media, streaming platforms, or business-critical tools.
Another advanced feature tested is the use of Threat Prevention technologies like Antivirus, Anti-Bot, and Intrusion Prevention Systems. These tools provide real-time inspection of network traffic to detect and stop malicious activity. Candidates must understand how to configure these protections, ensure they are applied correctly to policies, and monitor their effectiveness using the management console. The exam also evaluates knowledge of performance tuning to balance security inspection with network throughput, a skill that directly impacts the usability of the network.
High Availability and Cluster Management
High availability is a crucial component of enterprise security environments, and the exam ensures that candidates know how to implement it effectively. ClusterXL, Checkpoint’s clustering solution, allows multiple gateways to work together to provide redundancy and load sharing. The exam assesses a candidate’s understanding of how to configure clusters, synchronize state information, and handle failover scenarios.
Administrators must be familiar with different cluster modes, such as Load Sharing and High Availability, and when to apply each based on organizational needs. The configuration involves ensuring that cluster members communicate consistently, that interfaces are aligned properly, and that synchronization occurs without error. Questions often involve troubleshooting scenarios where one member fails to synchronize or where a failover does not occur as expected, testing a candidate’s ability to resolve real-world issues.
The importance of high availability in the exam reflects its value in enterprise operations. A properly configured cluster ensures minimal downtime, protects against hardware failures, and maintains continuous enforcement of security policies. Understanding the nuances of ClusterXL is therefore essential for success in the 156-215.80 exam.
Identity Awareness and Access Control
Identity Awareness is another major area tested in the 156-215.80 exam. Traditional firewalls rely on IP addresses to enforce policies, but in modern networks, this approach is insufficient. Devices may change IP addresses frequently, and different users may share the same machine. Identity Awareness allows administrators to enforce policies based on user identity rather than just IP information.
Candidates must know how to integrate Checkpoint gateways with directory services such as LDAP or Active Directory to retrieve user information. The exam tests the ability to create rules that allow or deny access based on group membership or user identity. For example, administrators might configure rules to allow marketing staff access to specific web applications while restricting other groups.
The practical side of Identity Awareness involves configuring login options, managing captive portals, and troubleshooting authentication failures. Candidates should be able to determine why a user’s identity is not being recognized, whether due to misconfiguration of the directory connection, authentication settings, or mismatched group membership. Since user-based policies play an increasingly important role in enterprise environments, this knowledge is a critical part of the exam.
Integration with Enterprise Environments
The 156-215.80 exam also evaluates how well candidates can integrate Checkpoint technologies into larger enterprise environments. This includes working with third-party systems, managing traffic between different network segments, and ensuring compatibility with existing security solutions. Candidates are expected to understand how Checkpoint gateways can coexist with other devices, such as routers, switches, and non-Checkpoint firewalls.
Part of this integration involves configuring routing correctly. Candidates must be able to implement both static and dynamic routing to ensure traffic flows efficiently between different parts of the network. The exam scenarios often present situations where incorrect routing causes connectivity issues, requiring candidates to identify and correct the problem.
Another area of integration involves logging and monitoring systems. Enterprises often use centralized systems to collect security logs from multiple devices. The exam expects candidates to understand how to configure Checkpoint devices to send logs to external servers, how to ensure data integrity, and how to troubleshoot when logs are not being transmitted correctly.
Performance Optimization
Performance optimization is another critical aspect of the 156-215.80 exam. Security gateways must inspect traffic thoroughly without introducing significant delays. Candidates must understand how to adjust configurations to balance security and performance. For example, enabling deep inspection on all traffic may cause noticeable slowdowns, but administrators can configure exceptions for trusted applications or traffic types.
The exam requires familiarity with acceleration features such as SecureXL and CoreXL. SecureXL improves performance by offloading connections to the hardware level, while CoreXL allows multiple CPU cores to process traffic simultaneously. Candidates must know how to enable and verify these features, as well as troubleshoot when performance does not meet expectations.
Resource monitoring is also tested. Administrators must be able to monitor CPU, memory, and interface usage to identify bottlenecks. If a system is overloaded, candidates must determine whether the issue lies in configuration, hardware limitations, or an external factor such as a denial-of-service attack. This demonstrates practical ability to maintain network performance under various conditions.
Threat Intelligence and Response
The 156-215.80 exam emphasizes proactive threat intelligence and response capabilities. Administrators are expected to configure gateways to leverage real-time intelligence feeds that update protections against emerging threats. Understanding how to apply these updates automatically and verify their effectiveness is part of the exam objectives.
Incident response is another component. Candidates must know how to use Checkpoint tools to detect intrusions, analyze attack patterns, and respond effectively. This might involve blocking malicious IP addresses, isolating compromised systems, or adjusting policies to prevent further incidents. The exam scenarios often simulate situations where administrators must make decisions quickly based on limited log data, reflecting real-world conditions where time is critical.
Practical Troubleshooting Scenarios
Troubleshooting remains a central theme throughout the 156-215.80 exam. Candidates are often presented with complex scenarios where multiple issues intersect. For example, a VPN connection may fail not only because of a misconfigured policy but also due to NAT interference. The exam tests the ability to piece together evidence from logs, system status, and policies to identify the root cause.
Administrators must be comfortable using both graphical tools and command-line utilities to diagnose problems. This includes running diagnostic commands, checking system processes, and reviewing error messages. The exam assesses whether candidates can take a structured approach to troubleshooting, ruling out simple causes before moving to complex ones.
Troubleshooting is also evaluated in terms of communication. Candidates must demonstrate the ability to interpret error messages clearly and apply corrective actions that do not disrupt other parts of the network. This skill is essential for minimizing downtime and maintaining security posture in real environments.
Building Confidence for the Exam
Preparation for the 156-215.80 exam requires more than memorization. Candidates must build confidence in their ability to apply knowledge under exam conditions. This involves consistent practice, reviewing weak areas, and simulating real-world tasks. By working through complex scenarios in practice environments, candidates can develop the problem-solving mindset required to succeed.
Confidence also comes from understanding the exam objectives thoroughly. Candidates should know not only what topics are covered but how they are interconnected. For example, configuring NAT affects VPN traffic, which in turn is impacted by security policies. Recognizing these relationships is crucial for answering scenario-based questions correctly.
Time management is another factor. The exam is timed, so candidates must balance careful analysis with efficiency. Practicing under timed conditions helps develop the ability to work quickly without sacrificing accuracy. This skill ensures that all questions are attempted within the allotted time.
The Checkpoint 156-215.80 exam is an in-depth assessment of an administrator’s ability to secure enterprise networks using advanced Checkpoint features. It covers topics ranging from installation and policy management to high availability, identity awareness, performance optimization, and threat response. Success requires both theoretical understanding and practical experience, particularly in troubleshooting and integration.
Preparation should focus on mastering core concepts while also practicing advanced scenarios that reflect real-world conditions. By developing hands-on skills and building confidence in applying knowledge, candidates can approach the exam with the assurance that they are ready to meet its challenges. Passing the exam not only validates technical competence but also strengthens professional credibility as a capable security administrator.
SmartConsole and Management in the 156-215.80 Exam
The 156-215.80 exam places a significant focus on SmartConsole, the centralized interface for managing Checkpoint environments. Candidates must be comfortable navigating SmartConsole, understanding its layout, and applying its various features to manage security gateways, policies, users, and logs. A key skill assessed in the exam is the ability to create, modify, and implement security policies through SmartConsole. This involves defining rules, applying them to specific network objects, and understanding how the rule base processes traffic in order.
Candidates must also know how to work with the object-oriented nature of Checkpoint management. Objects such as networks, hosts, users, and services are created and used repeatedly across policies. The exam tests the ability to organize these objects efficiently, reuse them where appropriate, and avoid unnecessary duplication. An understanding of object hierarchies and inheritance is also important, as it allows administrators to build scalable configurations that are easy to maintain.
SmartConsole also plays a vital role in monitoring and troubleshooting. The exam may test whether candidates can locate logs, filter them for relevant information, and correlate events to identify the source of an issue. For example, if a connection is blocked, the administrator must be able to trace which rule or layer caused the block and adjust the configuration accordingly. This practical knowledge demonstrates proficiency not just in configuration but also in maintaining operational stability.
Security Policy Management
Policy management is central to the 156-215.80 exam. Candidates must demonstrate the ability to design and enforce policies that protect enterprise assets while still enabling necessary communication. The exam focuses on understanding the rule base, which defines what traffic is permitted or denied, and in what order these rules are applied.
An important concept is the principle of “top-down” rule processing. Rules at the top of the rule base are evaluated before those below, which means misordering can cause unintended behavior. The exam tests whether candidates can identify and resolve issues caused by misplaced or overlapping rules. For example, a broad rule allowing wide access could inadvertently override a more restrictive rule placed beneath it.
Another focus area is the use of layers in policies. Security administrators can create ordered layers or inline layers to organize rules more effectively. Inline layers allow for grouping of related rules, while ordered layers allow for segmentation of different policy types, such as access control and threat prevention. Candidates must understand when and how to use these layers to achieve clarity and precision in policy design.
The exam also assesses skills in configuring security zones, NAT rules, and application control within the policy framework. Candidates should know how to write policies that incorporate user identity, application-level restrictions, and inspection of encrypted traffic. This requires combining multiple Checkpoint features into cohesive policies that address both security and business needs.
Software Updates and Version Management
Maintaining updated software is critical for security, and the 156-215.80 exam evaluates knowledge of Checkpoint’s update process. Candidates are expected to understand how to apply hotfixes, patches, and major upgrades in a controlled manner. This includes planning updates to minimize downtime, verifying compatibility with existing environments, and ensuring that updates do not disrupt ongoing operations.
The exam requires familiarity with the tools and processes for performing updates. Candidates must know how to use the upgrade wizard, backup configurations before applying updates, and verify that updates have been installed successfully. They should also understand the difference between applying a minor hotfix to address a specific issue versus upgrading to a newer version that introduces new features.
Rollback procedures are another important area. If an update causes unexpected problems, administrators must be able to restore the previous configuration quickly. The exam may present scenarios where candidates need to troubleshoot update failures or manage environments with different versions of software across multiple gateways. The goal is to ensure that candidates can maintain system stability while keeping security protections current.
User Management and Access Control
User management is a key component of the 156-215.80 exam. Security policies are often tied to user identities, so administrators must know how to manage user accounts, authentication methods, and group memberships. Candidates are tested on integrating Checkpoint environments with external authentication systems, configuring local users, and setting up different login methods such as passwords, certificates, or multi-factor authentication.
Access control based on user identity requires administrators to map network activity to specific users. The exam evaluates the ability to configure Identity Awareness, connect to directory services, and enforce policies based on user groups. For example, rules may allow certain groups access to sensitive systems while denying others. Candidates must also know how to troubleshoot common issues, such as when a user’s identity is not recognized by the system.
Administrators must balance usability with security. While strong authentication is critical, it must not overly burden legitimate users. The exam scenarios often reflect this balance, requiring candidates to configure solutions that are both secure and practical. For instance, using single sign-on can streamline user access while maintaining security policies across the environment.
VPN and Remote Access
The 156-215.80 exam also covers virtual private networks (VPNs) and remote access, as these are essential for secure connectivity. Candidates must understand how to configure site-to-site VPNs between gateways, ensuring that traffic is encrypted and authenticated. The exam tests knowledge of VPN communities, encryption methods, and tunnel management.
Remote access VPNs are another focus. Administrators must know how to configure client-based and clientless remote access, ensuring secure connectivity for remote users. This involves setting up authentication methods, distributing client software, and troubleshooting common issues like tunnel failures or dropped connections.
NAT often interacts with VPNs, and candidates are expected to understand how to configure policies so that NAT does not interfere with VPN traffic. Troubleshooting scenarios in the exam may present problems where NAT or policy misconfiguration breaks VPN connectivity, requiring candidates to diagnose and resolve the issue.
Logging, Monitoring, and Event Analysis
Effective logging and monitoring are essential for maintaining security, and the 156-215.80 exam evaluates a candidate’s ability to configure and use these features. Administrators must know how to collect logs from gateways, filter them for relevant information, and analyze events to identify threats or operational issues.
The exam also assesses knowledge of SmartEvent, which aggregates logs and provides real-time event analysis. Candidates must understand how to configure SmartEvent to detect significant incidents, generate alerts, and create reports. For example, SmartEvent might be configured to alert administrators when a large number of failed login attempts occur, indicating a potential brute-force attack.
In addition to configuring logging systems, candidates must be able to troubleshoot issues such as missing logs, delayed reporting, or misconfigured log servers. The ability to identify the root cause of these issues ensures that organizations maintain visibility into their security environment, which is crucial for both compliance and threat response.
Layered Defense and Security Strategies
The concept of layered defense is central to the 156-215.80 exam. Administrators must understand how to implement multiple layers of security to protect against different types of threats. This includes using firewalls, intrusion prevention systems, application control, URL filtering, antivirus, and anti-bot technologies in combination.
The exam assesses whether candidates can design and configure policies that take advantage of this layered approach. For example, a firewall rule might block certain traffic, while intrusion prevention examines the traffic that is allowed to ensure it does not contain malicious payloads. Similarly, application control can restrict use of risky applications, while URL filtering blocks access to harmful websites.
Layered defense strategies also involve segmenting the network to limit the spread of attacks. Candidates may be tested on configuring internal security zones, applying different policies to different segments, and ensuring that critical systems have stronger protections. This demonstrates the ability to design comprehensive security architectures rather than relying on a single layer of defense.
The 156-215.80 exam demands a broad and deep understanding of Checkpoint technologies, with a focus on practical administration. From SmartConsole management to user control, VPNs, updates, and layered security strategies, the exam requires candidates to demonstrate real-world skills in protecting enterprise environments. Success requires not only familiarity with the tools but also the ability to apply them effectively under complex scenarios.
By mastering policy management, user integration, monitoring, and troubleshooting, candidates prepare themselves to meet the challenges of the exam and demonstrate their capabilities as skilled security administrators. The knowledge gained through this preparation also translates directly into the workplace, where the same skills are necessary to maintain secure and efficient networks.
Advanced Troubleshooting in the 156-215.80 Exam
Troubleshooting is a critical part of the 156-215.80 exam because it evaluates whether candidates can effectively respond to operational issues. Administrators must demonstrate not only technical knowledge but also a structured approach to problem-solving. A typical troubleshooting scenario begins with identifying the symptoms of a problem, such as a user being unable to access a specific service, and then narrowing down the possible causes. This involves checking logs, analyzing rule bases, reviewing NAT configurations, and confirming user authentication.
The exam places a strong emphasis on diagnosing rule conflicts, as these are a common cause of issues in Checkpoint environments. Candidates need to know how to review the rule base carefully to detect overlaps or misordering of rules. For instance, a broad deny rule placed above a specific allow rule can unintentionally block legitimate traffic. Similarly, shadowed rules, which are hidden by rules above them, may create confusion and require reordering to achieve the intended behavior.
Network address translation can also complicate troubleshooting. The exam assesses whether candidates can determine if a NAT rule is interfering with connectivity, particularly when dealing with VPN tunnels or public-facing services. Administrators must know how to confirm translation behavior and modify NAT rules to resolve conflicts without creating new issues.
Performance troubleshooting is another important area. Candidates should understand how to identify high CPU or memory usage on a security gateway, analyze logs for unusual patterns, and take steps to mitigate issues. This could involve optimizing rule bases, reviewing traffic loads, or distributing policies more efficiently across multiple gateways. The ability to apply systematic troubleshooting practices is essential for passing the exam and succeeding in real-world environments.
Disaster Recovery and Backup Management
Disaster recovery plays a vital role in the 156-215.80 exam because administrators must ensure business continuity even in the event of a failure. Candidates are tested on their ability to back up configurations, restore systems, and minimize downtime. The exam requires knowledge of backup tools available in Checkpoint environments, including exporting configuration files, creating snapshots, and managing backups through SmartConsole.
Understanding when to use different types of backups is important. A snapshot may be ideal for capturing the full system state before a major upgrade, while configuration exports are useful for saving specific policy and object data. The exam may present scenarios where candidates must decide which backup method to use to ensure the fastest recovery with the least data loss.
Restoring systems from backups is equally important. Candidates must demonstrate how to recover a corrupted or failed system by applying backups effectively. This involves verifying backup integrity, reinstalling systems if necessary, and reapplying configurations to restore services. Additionally, disaster recovery planning includes having redundancy in place, such as using high availability clusters. The exam may test whether candidates can configure and manage clusters to ensure that if one gateway fails, another takes over without disrupting traffic.
Scalability and Performance Considerations
The 156-215.80 exam also addresses scalability, as modern enterprise environments often require security solutions that can handle large volumes of traffic. Candidates are expected to understand how to design and configure Checkpoint environments that scale effectively. This includes distributing traffic across multiple gateways, optimizing rule bases, and using hardware resources efficiently.
One area the exam tests is the ability to evaluate and refine rule bases for performance. Overly complex or poorly ordered rules can slow down traffic processing, so administrators must know how to simplify policies without compromising security. For example, consolidating redundant rules, using groups instead of individual objects, and avoiding unnecessary deep inspection can improve performance significantly.
Another aspect of scalability is clustering. The exam assesses whether candidates can configure Checkpoint clusters to operate in high availability or load sharing modes. High availability ensures redundancy, while load sharing distributes traffic across multiple gateways for improved performance. Candidates must know how to configure synchronization between cluster members, troubleshoot failovers, and ensure that traffic flows are not disrupted during maintenance or outages.
Real-World Simulation Scenarios
The 156-215.80 exam often presents real-world scenarios that require candidates to apply multiple skills simultaneously. For example, a scenario might describe a remote office unable to connect through a VPN tunnel, with logs indicating that certain traffic is being blocked. To resolve this, candidates must combine their knowledge of VPN configuration, NAT behavior, rule base management, and log analysis. This tests not only technical proficiency but also the ability to think critically under pressure.
Another type of scenario may involve a performance issue, such as slow access to applications. Candidates must determine whether the issue lies in the firewall rules, application control policies, or system resource usage. This requires a holistic understanding of how different Checkpoint features interact and how to optimize them.
These simulation-based questions are designed to mimic the challenges administrators face in daily operations. The exam is not just about memorizing commands or features but about applying them in a way that demonstrates real-world problem-solving. Candidates who can adapt their knowledge to diverse situations are more likely to succeed.
Identity Awareness and Access Control in Practice
Identity awareness is a recurring theme in the 156-215.80 exam. The ability to tie network activity to specific users enhances policy precision and accountability. Candidates must understand how to configure identity sources, integrate with directory services, and apply rules based on user or group identity. This allows administrators to create more granular policies, such as allowing access to sensitive systems only for members of a specific department.
The exam may also test scenarios where identity awareness is not functioning correctly, requiring candidates to troubleshoot integration issues or misconfigurations. For example, a user might not be recognized because of synchronization problems with a directory service, and the administrator must identify and correct the issue.
Identity awareness also plays a role in remote access VPNs. By linking user identities with VPN sessions, administrators can enforce differentiated policies based on user roles. For instance, an administrator might allow IT staff broader access than regular employees. Demonstrating this ability in the exam shows proficiency in implementing practical and secure access control measures.
Threat Prevention and Advanced Protections
Threat prevention is another critical part of the 156-215.80 exam. Candidates must understand how to configure and manage features such as intrusion prevention, antivirus, anti-bot, and URL filtering. These tools work together to provide layered protection against a wide range of threats.
Intrusion prevention policies require careful configuration to detect and block malicious traffic without causing false positives that disrupt legitimate communication. The exam evaluates whether candidates can balance sensitivity and performance when enabling these protections. Similarly, antivirus and anti-bot protections require configuration of updates, policies, and monitoring to detect emerging threats.
URL filtering and application control are also tested. Candidates must know how to create rules that restrict access to harmful websites, enforce corporate usage policies, and monitor application traffic. These features not only enhance security but also help enforce organizational compliance requirements.
The exam scenarios may combine these features with broader policy management, requiring candidates to apply threat prevention tools in conjunction with firewall and identity-based rules. This ensures that candidates can configure comprehensive protections that adapt to the evolving threat landscape.
Preparing Effectively for the Exam
Success in the 156-215.80 exam requires a balance of theoretical knowledge and practical skills. Candidates must study the objectives thoroughly but also spend significant time practicing configurations and troubleshooting in a lab environment. Hands-on practice helps solidify concepts and prepares candidates for the practical nature of the exam scenarios.
A structured study plan is essential. Candidates should break down the exam objectives into manageable sections, allocate time to each, and set clear goals. Reviewing logs, creating different policy scenarios, and simulating failures in a lab environment provide valuable experience.
Practice exams and self-assessment also play a role in preparation. By simulating exam conditions, candidates can identify weak areas and focus their studies accordingly. Time management is another skill tested indirectly in the exam, so practicing under timed conditions is beneficial
Long-Term Skill Development Through the 156-215.80 Exam
One of the most important aspects of preparing for and earning the 156-215.80 certification is the opportunity to develop long-term skills that remain useful throughout a professional career in network and security administration. Unlike basic knowledge that may fade with time, the core competencies required for this exam are designed to provide lasting value. These include proficiency in firewall configuration, security policy management, VPN setup, user identity awareness, threat prevention, and system troubleshooting. By repeatedly practicing these skills in different configurations and scenarios, administrators build confidence that extends beyond the scope of the exam.
The certification ensures that professionals not only understand theoretical concepts but can also apply them effectively in real-world settings. This balance of knowledge and practical ability leads to stronger analytical thinking, decision-making skills, and adaptability. Each area of study reinforces another, creating an interconnected set of abilities that can be drawn upon as technology evolves.
Another long-term benefit is the mindset the exam encourages. Candidates learn to approach challenges methodically, breaking down complex problems into manageable parts and applying logical troubleshooting processes. This approach is highly valued in security roles where quick and accurate responses to incidents are essential. Ultimately, the 156-215.80 exam promotes the development of an adaptable, security-focused professional ready to face new threats and system requirements.
Exam-Day Strategies for Success
The day of the 156-215.80 exam can often bring stress and pressure, but having a strategy in place makes a significant difference. Time management is critical, as the exam is designed to assess both knowledge and the ability to apply it under constraints. Candidates should avoid spending too long on a single question and instead return to challenging items after addressing those they feel more confident about.
Reading questions carefully is another important strategy. Some exam items may contain multiple layers of information, and missing a small detail can lead to an incorrect response. Administrators must take time to understand whether the question is asking about configuration, troubleshooting, or theory, and tailor their response accordingly.
It is also helpful to apply the method of elimination. If a candidate is unsure of the correct answer, they should eliminate clearly incorrect options to improve their chances of selecting the right one. This is especially useful in scenario-based questions that provide several possible solutions, some of which may be plausible but not the most effective.
Maintaining a calm and focused mindset is essential. Stress often leads to mistakes, but steady breathing, clear thinking, and pacing oneself help avoid errors. Reviewing answers if time allows is also beneficial, as it provides an opportunity to catch overlooked mistakes. Going into the exam with a clear plan of approach allows candidates to demonstrate their full capabilities under exam conditions.
Post-Certification Growth and Opportunities
Earning the 156-215.80 certification is not the end of the journey but the beginning of new opportunities. The certification establishes a professional foundation that can be built upon with more advanced roles and responsibilities. Certified administrators gain credibility in their organizations as skilled professionals capable of managing critical security systems.
The knowledge gained from preparing for the exam also provides a strong base for continued learning. Security technologies evolve rapidly, and those with certification already have the framework to adapt to new tools, updated versions of Checkpoint software, and emerging security threats. This adaptability is often what distinguishes a certified administrator from peers who lack formal validation of their skills.
Professionals who pass the exam are better positioned for career advancement. Roles in security administration, network management, and IT operations often prioritize candidates who have proven certifications. The certification also helps candidates develop transferable skills that apply to a wide range of environments, allowing them to pursue diverse opportunities in security management.
The Importance of Hands-On Experience
While studying and memorizing exam objectives are important, hands-on practice is what solidifies knowledge into usable skill. The 156-215.80 exam requires candidates to demonstrate understanding through real-world scenarios that simulate practical challenges. Without hands-on practice, even well-prepared candidates may struggle to apply their knowledge effectively.
Creating a personal lab environment is one of the best ways to gain experience. By setting up gateways, configuring policies, and troubleshooting errors in a controlled environment, administrators gain the type of confidence that cannot be achieved through study alone. This practice also helps uncover gaps in understanding, which can then be addressed before the exam.
Hands-on experience ensures candidates learn not only how features work, but also why they are configured in a certain way. For example, configuring a VPN teaches both the technical steps involved and the reasoning behind securing communication channels. These insights lead to a deeper mastery of security principles and make candidates stronger administrators in professional environments.
Building a Structured Study Plan
A structured study plan is key to succeeding in the 156-215.80 exam. Without a clear schedule, preparation can feel overwhelming, and important objectives may be overlooked. The best approach is to break the exam topics into sections and focus on one area at a time. This allows candidates to give proper attention to each objective while building knowledge progressively.
The plan should include dedicated time for reading, hands-on practice, and review. Balancing these elements ensures that candidates not only understand concepts but can also apply them under exam conditions. Allocating time for practice tests is also important, as it helps candidates gauge their readiness and identify weak areas that need improvement.
Consistency is critical in following the plan. Even short daily sessions are more effective than long, infrequent study periods because regular exposure helps reinforce learning. Establishing achievable milestones keeps motivation high, as candidates can track their progress and see tangible improvement over time. By following a structured plan, preparation becomes manageable and increases the likelihood of success.
Conclusion
The 156-215.80 exam is designed to evaluate a candidate’s ability to administer Checkpoint environments effectively, covering everything from basic configuration to advanced troubleshooting and threat prevention. Its practical focus ensures that those who pass are not only familiar with the technology but also capable of applying it in real-world scenarios.
By mastering skills in disaster recovery, scalability, troubleshooting, identity management, and layered defenses, candidates prepare themselves for the challenges of securing complex enterprise networks. Success in this exam demonstrates readiness to take on critical roles in network and security administration, making it a valuable step in an IT professional’s career path.
Checkpoint CCSA 156-215.80 practice test questions and answers, training course, study guide are uploaded in ETE Files format by real users. Study and Pass 156-215.80 Check Point Certified Security Administrator (CCSA R80) certification exam dumps & practice test questions and answers are to help students.
Exam Comments * The most recent comment are on top
- 156-315.81.20 - Check Point Certified Security Expert - R81.20
- 156-587 - Check Point Certified Troubleshooting Expert - R81.20 (CCTE)
- 156-215.81.20 - Check Point Certified Security Administrator - R81.20 (CCSA)
- 156-536 - Check Point Certified Harmony Endpoint Specialist - R81.20 (CCES)
- 156-582 - Check Point Certified Troubleshooting Administrator - R81.20 (CCTA)
- 156-835 - Check Point Certified Maestro Expert
- 156-560 - Check Point Certified Cloud Specialist (CCCS)
- 156-585 - Check Point Certified Troubleshooting Expert
Purchase 156-215.80 Exam Training Products Individually


Why customers love us?
What do our customers say?
The resources provided for the Checkpoint certification exam were exceptional. The exam dumps and video courses offered clear and concise explanations of each topic. I felt thoroughly prepared for the 156-215.80 test and passed with ease.
Studying for the Checkpoint certification exam was a breeze with the comprehensive materials from this site. The detailed study guides and accurate exam dumps helped me understand every concept. I aced the 156-215.80 exam on my first try!
I was impressed with the quality of the 156-215.80 preparation materials for the Checkpoint certification exam. The video courses were engaging, and the study guides covered all the essential topics. These resources made a significant difference in my study routine and overall performance. I went into the exam feeling confident and well-prepared.
The 156-215.80 materials for the Checkpoint certification exam were invaluable. They provided detailed, concise explanations for each topic, helping me grasp the entire syllabus. After studying with these resources, I was able to tackle the final test questions confidently and successfully.
Thanks to the comprehensive study guides and video courses, I aced the 156-215.80 exam. The exam dumps were spot on and helped me understand the types of questions to expect. The certification exam was much less intimidating thanks to their excellent prep materials. So, I highly recommend their services for anyone preparing for this certification exam.
Achieving my Checkpoint certification was a seamless experience. The detailed study guide and practice questions ensured I was fully prepared for 156-215.80. The customer support was responsive and helpful throughout my journey. Highly recommend their services for anyone preparing for their certification test.
I couldn't be happier with my certification results! The study materials were comprehensive and easy to understand, making my preparation for the 156-215.80 stress-free. Using these resources, I was able to pass my exam on the first attempt. They are a must-have for anyone serious about advancing their career.
The practice exams were incredibly helpful in familiarizing me with the actual test format. I felt confident and well-prepared going into my 156-215.80 certification exam. The support and guidance provided were top-notch. I couldn't have obtained my Checkpoint certification without these amazing tools!
The materials provided for the 156-215.80 were comprehensive and very well-structured. The practice tests were particularly useful in building my confidence and understanding the exam format. After using these materials, I felt well-prepared and was able to solve all the questions on the final test with ease. Passing the certification exam was a huge relief! I feel much more competent in my role. Thank you!
The certification prep was excellent. The content was up-to-date and aligned perfectly with the exam requirements. I appreciated the clear explanations and real-world examples that made complex topics easier to grasp. I passed 156-215.80 successfully. It was a game-changer for my career in IT!