Pass ECCouncil CEH Certification Exam in First Attempt Guaranteed!
Get 100% Latest Exam Questions, Accurate & Verified Answers to Pass the Actual Exam!
30 Days Free Updates, Instant Download!


312-50v10 Premium Bundle
- Premium File 322 Questions & Answers. Last update: Nov 15, 2025
- Training Course 182 Video Lectures
- Study Guide 1299 Pages

312-50v10 Premium Bundle
- Premium File 322 Questions & Answers
Last update: Nov 15, 2025 - Training Course 182 Video Lectures
- Study Guide 1299 Pages
Purchase Individually

Premium File

Training Course

Study Guide
312-50v10 Exam - Certified Ethical Hacker v10 Exam
| Download Free 312-50v10 Exam Questions |
|---|
ECCouncil CEH Certification Practice Test Questions and Answers, ECCouncil CEH Certification Exam Dumps
All ECCouncil CEH certification exam dumps, study guide, training courses are prepared by industry experts. ECCouncil CEH certification practice test questions and answers, exam dumps, study guide and training courses help candidates to study and pass hassle-free!
Introduction to Ethical Hacking and the CEH Certification
The concept of ethical hacking was born from a simple yet powerful realization: to defend against a skilled adversary, you must first understand their methods. In the early days of computing, the term "hacker" was not inherently negative. It often referred to creative programmers who could push systems beyond their intended limits. However, as networked systems became more prevalent and valuable, a criminal element emerged, exploiting vulnerabilities for personal gain. This created a clear division between malicious attackers, often called "black hats," and those who used their skills for defensive purposes. To counter the rising threat of cybercrime, organizations began to see the value in proactively testing their own defenses. They needed individuals who could mimic the tools, techniques, and mindset of a malicious attacker but do so with permission and for the purpose of improving security. This practice became known as ethical hacking or penetration testing. It marked a strategic shift from a reactive security posture, which only responds to incidents after they occur, to a proactive one that seeks to identify and remediate weaknesses before they can be exploited by real-world adversaries.
Defining the Modern Ethical Hacker
A modern ethical hacker is a skilled cybersecurity professional who specializes in offensive security tactics. They are employed by organizations to perform authorized, simulated cyberattacks against their own computer systems, networks, and web applications. The primary goal is to uncover security vulnerabilities that a malicious actor could potentially exploit. Unlike their malicious counterparts, ethical hackers operate under a strict code of ethics and with the explicit, documented permission of the organization they are assessing. Their work is bound by a defined scope and rules of engagement to ensure no actual harm comes to the target systems. These professionals are sometimes referred to as "white hat" hackers. They use the same portfolio of tools and techniques as black hat hackers, including port scanners, vulnerability analysis tools, and exploitation frameworks. The key difference lies in their intent and authorization. The findings of an ethical hacking engagement are compiled into a detailed report that not only identifies the vulnerabilities but also assesses their potential business impact and provides concrete recommendations for remediation. This process helps organizations strengthen their security defenses in a measurable and verifiable way, turning theoretical risks into actionable intelligence.
Introducing the Certified Ethical Hacker Credential
The Certified Ethical Hacker, or CEH, is a globally recognized cybersecurity certification that validates an individual's knowledge and skills in the domain of ethical hacking. It is one of the most well-known credentials offered by the International Council of Electronic Commerce Consultants, a prominent nonprofit body dedicated to cybersecurity education and training. The certification was established to create a standard for the profession and to certify individuals in the specific discipline of ethical hacking from a vendor-neutral perspective. It demonstrates that the holder understands how to look for weaknesses and vulnerabilities in target systems. The CEH certification covers a broad range of topics, ensuring that certified professionals have a comprehensive understanding of the entire hacking lifecycle. It is designed to be an early-career certification that serves as a strong foundation for those interested in offensive security roles. By earning the CEH, professionals can signal to employers that they possess a foundational body of knowledge in assessing system security and are committed to upholding a professional code of conduct. This makes it a popular starting point for aspiring penetration testers, security analysts, and vulnerability assessors.
The Philosophy Behind the CEH: Thinking Like an Attacker
The core philosophy of the CEH certification is encapsulated in the phrase, "To beat a hacker, you need to think like one." This principle guides the entire curriculum, which is designed to immerse candidates in an attacker's mindset. Rather than simply learning about defensive measures like firewalls and antivirus software, CEH candidates learn how these defenses can be bypassed. They study the methodologies that malicious actors use to conduct reconnaissance, gain unauthorized access, maintain persistence within a network, and cover their tracks. This offensive perspective is crucial for effective defense. By understanding the attacker's point of view, security professionals can better anticipate potential attack vectors and identify weaknesses that might otherwise be overlooked. This approach helps them move beyond a simple checklist mentality of security and into a more dynamic and critical way of thinking. They learn to see their own organization's network and applications not as a collection of assets to be protected, but as a landscape of potential targets with various entry points. This adversarial mindset is what separates a truly effective security professional from a system administrator with security responsibilities.
Understanding the CEH Certification Pathway
The CEH certification program offers a two-tiered pathway for professionals to demonstrate their capabilities. The first level is the core Certified Ethical Hacker credential. To achieve this, a candidate must pass a comprehensive multiple-choice examination. This exam is designed to test a broad spectrum of theoretical knowledge across numerous security domains, from reconnaissance techniques to cryptography. Passing this exam certifies that the individual possesses the foundational knowledge required of an ethical hacker. This is the most widely recognized component of the certification program and the first major milestone for any candidate. Upon successfully earning the CEH certification, individuals become eligible to pursue the next level: the CEH Master designation. This is achieved by passing a second, entirely different examination known as the CEH Practical. Unlike the knowledge-based multiple-choice exam, the Practical is a hands-on, performance-based test. Candidates are placed in a simulated lab environment and tasked with completing a series of real-world ethical hacking challenges within a strict time limit. Earning the CEH Master status demonstrates not only that you know the concepts but that you can successfully apply them in a practical setting.
Who Is the Ideal Candidate for the CEH?
The ideal candidate for the CEH certification is an IT professional who is looking to specialize or transition into a cybersecurity role, particularly one with a focus on offensive security. This includes individuals currently working as network administrators, system administrators, security analysts, and IT auditors. These roles provide a strong foundational understanding of IT infrastructure, which is essential context for learning how to attack it. The certification provides a structured pathway for them to build upon their existing knowledge and acquire the specific skills needed for roles like penetration testing and vulnerability analysis. Aspiring cybersecurity professionals who are just starting their careers can also be great candidates, provided they have a solid understanding of networking and operating systems. The CEH can serve as a powerful entry point into the security field, demonstrating a proactive interest and a baseline level of knowledge that can set them apart from other applicants. Ultimately, the certification is for anyone who is passionate about cybersecurity and wants to understand the offensive side of the equation to build a more robust and resilient defensive strategy for their organization or clients.
Core Prerequisites: Experience vs. Official Training
The certification body has established two distinct pathways to become eligible for the CEH exam, catering to candidates with different backgrounds. The first path is for individuals who have demonstrable work experience. To qualify through this route, a candidate must have at least two years of professional experience in the information security domain. They are required to submit an application that includes verifiable proof of their employment and a detailed description of their security-related job duties. This ensures that candidates who choose to self-study still possess a foundational level of practical knowledge before attempting the exam. The second path is designed for individuals who may not have the requisite two years of work experience or who prefer a more structured learning environment. These candidates can choose to attend official training from an accredited training center or an approved academic institution. Completing an official training course automatically makes a candidate eligible to sit for the exam without needing to document their prior work history. This option provides a comprehensive and guided preparation experience, often including lab access and instructor support, which can be invaluable for those new to the field of ethical hacking.
Navigating the Application and Eligibility Process
Regardless of the path chosen, every candidate must begin by completing an application process. For those relying on work experience, the application is more rigorous. It requires submitting details of your employer, your manager's contact information for verification, and a summary of your hands-on security experience. There is also a non-refundable application fee that must be paid for the certification body to review your submission. The review process can take several business days, during which your work history is vetted. Once approved, you receive an eligibility voucher to purchase your exam. For candidates who opt for official training, the process is more straightforward. The cost of the training program often includes the exam voucher, and the training provider typically handles the eligibility verification as part of the course enrollment. It is important to note that there are also age requirements for candidacy, which can vary depending on the country. Individuals who are below the minimum age may be able to obtain consent from a parent or guardian to enroll in official training and take the exam, but this is handled on a case-by-case basis by the certification body.
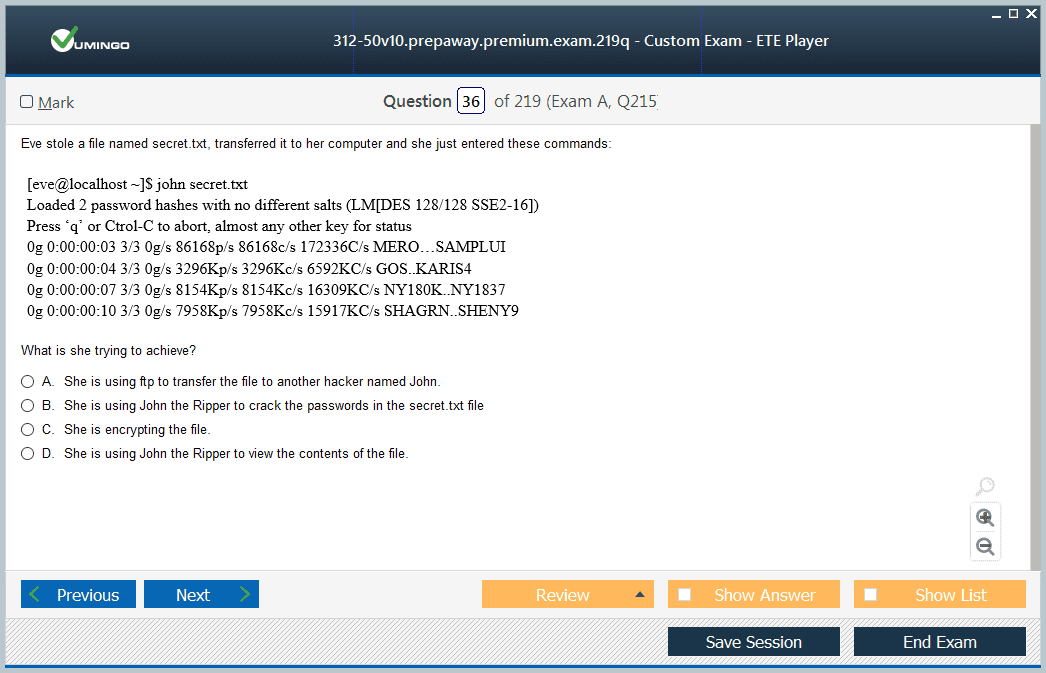
Deconstructing the CEH Exam Blueprint
To succeed on the Certified Ethical Hacker exam, it is essential to have a thorough understanding of its structure and content. The exam is a four-hour ordeal consisting of 125 multiple-choice questions. It is governed by a detailed exam blueprint that breaks down the testable material into nine distinct domains. Each domain is assigned a specific weight, indicating the proportion of questions that will be drawn from that topic area. A strategic study plan should allocate time and effort in accordance with these weights, focusing more heavily on the domains that make up a larger percentage of the exam. The blueprint serves as the definitive guide to what you need to know. It covers the entire ethical hacking lifecycle, from the initial information-gathering phases to the final stages of maintaining access and covering tracks. The domains encompass a wide array of technologies and methodologies, including network scanning, system hacking, web application vulnerabilities, wireless security, mobile platforms, cloud computing, and cryptography. A comprehensive grasp of each of these areas is necessary to pass the exam and earn the certification, as the questions are designed to test both knowledge and analytical thinking.
Domain 1: Information Security and Ethical Hacking Overview
This foundational domain, which accounts for a small but crucial portion of the exam, sets the stage for all the topics that follow. It covers the core concepts of information security, such as the principles of confidentiality, integrity, and availability, also known as the CIA triad. Candidates are expected to understand key security policies, procedures, and controls. The domain also formally defines ethical hacking, differentiating it from malicious hacking and explaining its role within a comprehensive security program. It introduces the legal and regulatory frameworks that govern security testing, emphasizing the importance of obtaining proper authorization before conducting any assessments. You will be tested on your knowledge of various attack types, such as phishing, malware, and social engineering, from a high-level perspective. The domain also introduces the five phases of hacking: reconnaissance, scanning, gaining access, maintaining access, and covering tracks. This five-phase methodology provides a structured framework that is referenced throughout the other, more technical domains of the exam. A solid understanding of these fundamental concepts is critical, as they provide the context for all the practical skills and techniques that are tested in the remainder of the exam.
Domain 2: Reconnaissance Techniques
Representing a significant portion of the exam, the reconnaissance domain is one of the most heavily weighted topics. Reconnaissance, also known as footprinting or information gathering, is the first and arguably most important phase of any hacking engagement. This domain covers the various techniques used to collect information about a target organization before launching any attacks. It distinguishes between passive reconnaissance, which involves gathering information from publicly available sources without directly interacting with the target, and active reconnaissance, which involves probing the target's systems to gather data. Candidates must be familiar with a wide range of tools and methods. This includes using search engines and social media to find information about employees and technologies, performing DNS queries to map out a company's network infrastructure, and using tools to discover public-facing IP address ranges. The goal of this phase is to build a comprehensive profile of the target, including its network topology, operating systems, and potential vulnerabilities. The depth of knowledge tested in this domain reflects the real-world importance of thorough preparation before any penetration test.
Domain 3: System Hacking Phases and Attack Techniques
This domain delves into the core of offensive operations: the process of gaining and maintaining control over a target system. It is another heavily weighted section of the exam. It covers the methodologies used to exploit vulnerabilities and escalate privileges once a foothold has been established. Candidates will need to understand techniques for cracking passwords using methods like brute force, dictionary attacks, and rainbow tables. The domain also explores the use of malware, including viruses, worms, trojans, and ransomware, to compromise systems and exfiltrate data. Furthermore, this section covers the concepts of privilege escalation, where an attacker who has gained low-level access to a system attempts to gain higher-level permissions, such as administrator or root access. It also examines techniques for maintaining access over time, such as installing backdoors or rootkits. Finally, the domain addresses the fifth phase of hacking: covering tracks. This involves methods for erasing evidence of the attacker's presence, such as deleting log files or manipulating system timestamps, to avoid detection by security personnel.
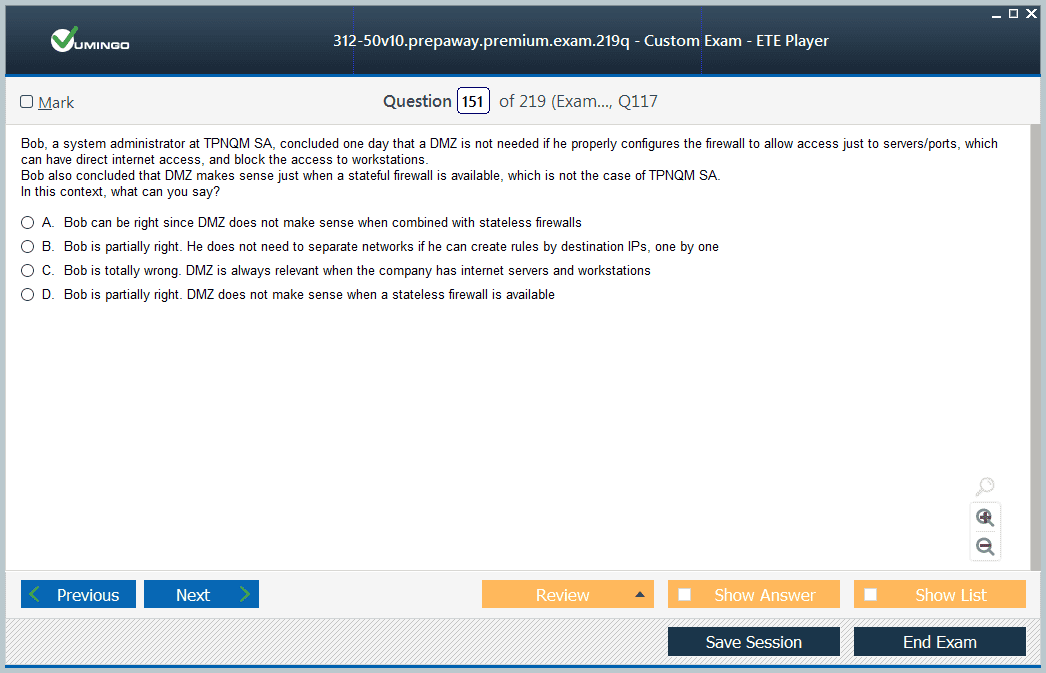
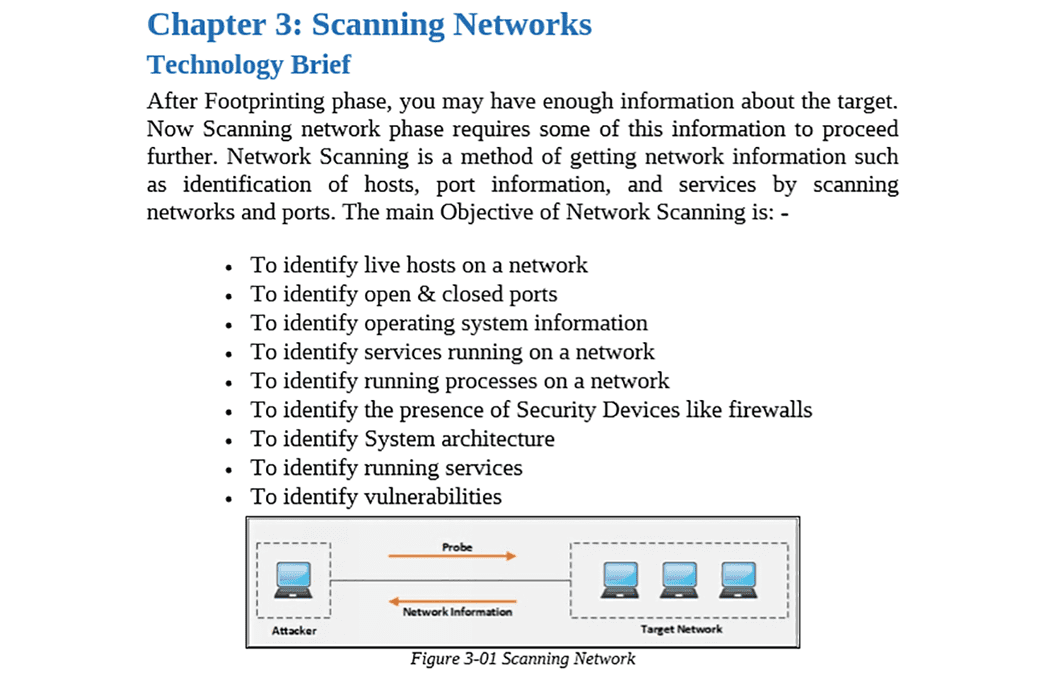
Domain 4: Network and Perimeter Hacking
This domain focuses on the techniques used to identify and exploit vulnerabilities in network infrastructure and perimeter defenses. It covers the process of scanning and enumeration in great detail. Scanning involves using tools to discover live hosts, open ports, and running services on a target network. Candidates must be familiar with different types of scans, such as TCP connect scans and SYN stealth scans, and the tools used to perform them. Enumeration is the process of extracting more detailed information from the discovered services, such as user accounts, network shares, and application version numbers. The domain also explores various network-level attacks. This includes sniffing network traffic to capture sensitive information like usernames and passwords in plaintext. It also covers session hijacking, where an attacker takes over a valid user session to gain unauthorized access to a system or application. Social engineering techniques, which manipulate human psychology to trick individuals into divulging confidential information or performing actions that compromise security, are also a key part of this section. Understanding how to attack the network itself is a fundamental skill for any ethical hacker.
Domain 5: Web Application Hacking
With the proliferation of web-based services, securing web applications has become a critical concern, and this is reflected in the significant weight of this exam domain. This section covers the most common vulnerabilities that affect web applications, as described in industry-standard lists like the OWASP Top Ten. Candidates must have a deep understanding of attacks such as SQL injection, which involves manipulating database queries to extract or modify sensitive data. They also need to know about Cross-Site Scripting (XSS), which involves injecting malicious scripts into web pages viewed by other users. The domain covers other critical web application vulnerabilities as well. This includes broken authentication and session management, insecure direct object references, and cross-site request forgery. For each vulnerability, candidates are expected to understand how the attack works, how to identify it, and the general principles of how to defend against it. Familiarity with common web application security tools, such as intercepting proxies like Burp Suite or OWASP ZAP, is also essential for success in this domain, as they are fundamental to testing modern web applications.
Domain 6: Wireless Network Hacking
This domain addresses the security of wireless networks, which are a common entry point into an organization's internal infrastructure. It covers the fundamentals of wireless networking standards, such as 802.11, and the various security protocols designed to protect them, including WEP, WPA, WPA2, and the latest WPA3 standard. Candidates must understand the weaknesses of older protocols like WEP and the types of attacks that can be used to crack their encryption and gain unauthorized access to a wireless network. The domain explores the entire process of discovering, analyzing, and attacking wireless networks. This includes techniques for discovering hidden SSIDs, bypassing MAC filtering, and performing attacks against the Wi-Fi Protected Setup (WPS) feature. The domain also covers more advanced attacks, such as creating rogue access points or evil twins to trick users into connecting to a malicious network and capturing their credentials or other sensitive data. A practical understanding of the tools used for wireless auditing and attacks is a key component of the knowledge tested in this section of the CEH exam.
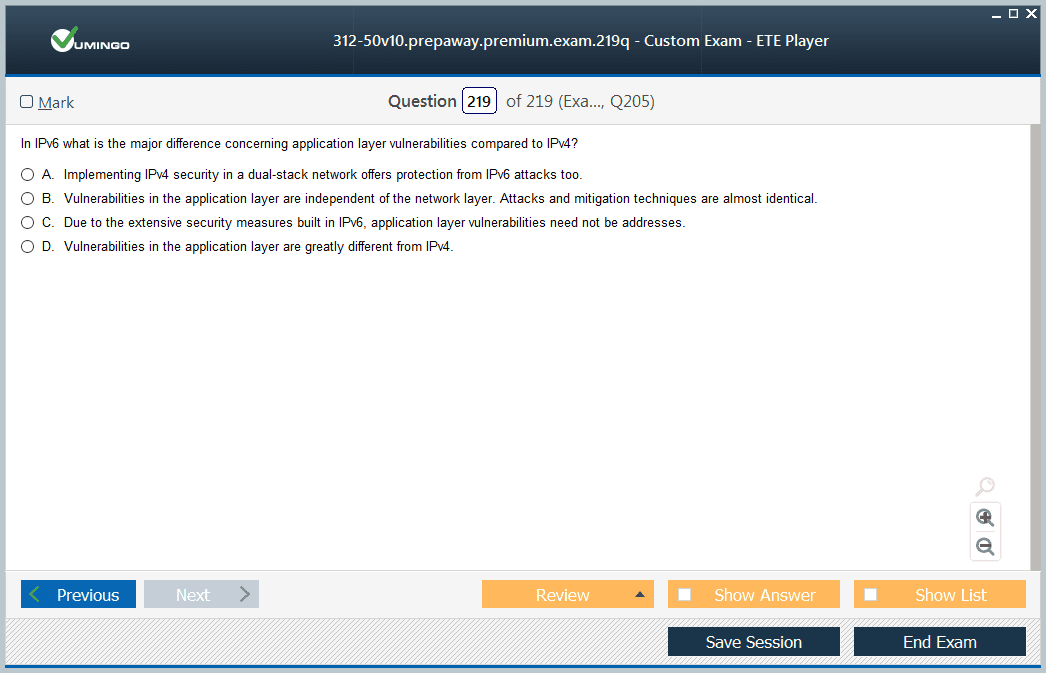
Domain 7: Mobile, IoT, and OT Hacking
Reflecting the modern technological landscape, this domain covers the security challenges associated with emerging platforms, including mobile devices, the Internet of Things (IoT), and Operational Technology (OT). The mobile platform section focuses on the security of Android and iOS operating systems, covering common vulnerabilities, mobile malware, and techniques for reverse-engineering mobile applications. It also addresses attacks against the mobile ecosystem, such as those targeting mobile device management (MDM) solutions or app stores. This area is critical as more business is conducted on mobile devices. The IoT portion of the domain explores the unique security risks posed by the vast number of connected devices, from smart home gadgets to industrial sensors. It covers common IoT vulnerabilities, such as default credentials, insecure network services, and lack of encryption. The OT section introduces candidates to the world of industrial control systems, such as SCADA, which are used to manage critical infrastructure. It discusses the specific protocols and attack vectors relevant to these environments, highlighting the potential for cyberattacks to have physical, real-world consequences.
Domain 8: Cloud Computing
As organizations increasingly migrate their infrastructure and services to the cloud, understanding cloud security has become essential for any cybersecurity professional. This domain introduces the core concepts of cloud computing, including the different service models like IaaS, PaaS, and SaaS, and deployment models like public, private, and hybrid clouds. It covers the security challenges and vulnerabilities that are specific to cloud environments, such as misconfigured cloud storage buckets, insecure APIs, and account hijacking. The domain emphasizes the shared responsibility model, where security duties are divided between the cloud provider and the customer. Candidates will be tested on their knowledge of common cloud-based attacks and how to identify them. This includes containerization technologies like Docker and orchestration platforms like Kubernetes, which are frequently used in cloud-native application development. The domain focuses on the methodologies for performing security assessments of cloud environments, highlighting how traditional penetration testing techniques must be adapted for the cloud. A foundational understanding of the major cloud providers and their security features is also an important part of the material covered in this section.
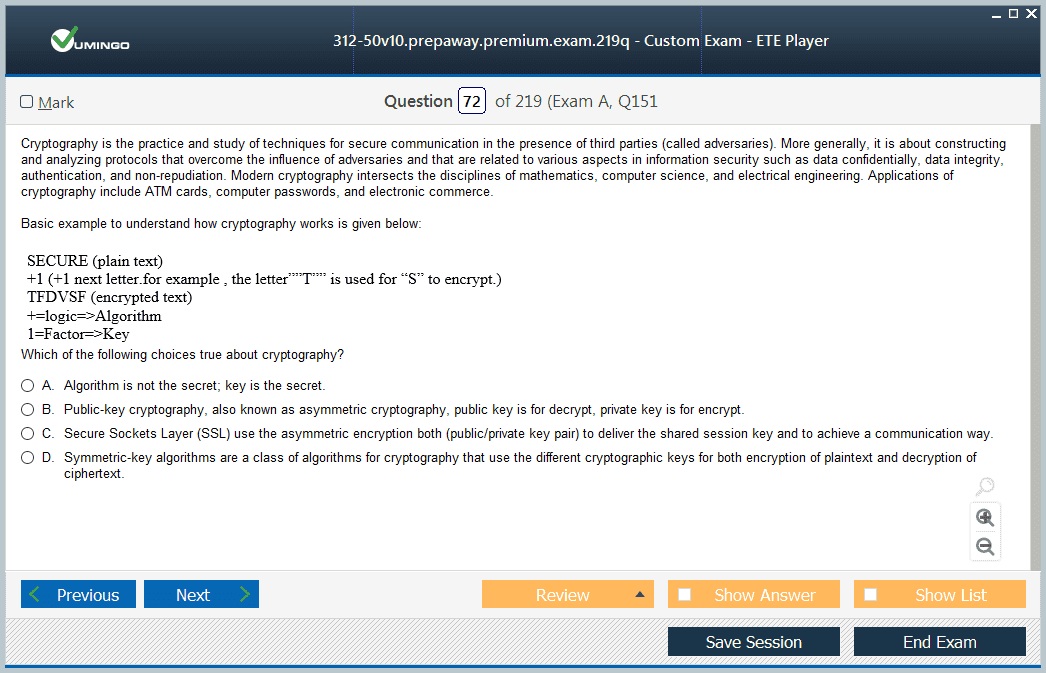
Domain 9: The Role of Cryptography
The final domain of the CEH exam covers the principles of cryptography, which is the science of secure communication. This section provides a high-level overview of cryptographic concepts that are essential for a security professional to understand. It covers the difference between symmetric and asymmetric encryption, explaining how algorithms like AES and RSA work in practice. The domain also introduces the concept of hashing, which is used to verify data integrity, and discusses common hashing algorithms like SHA-256. These cryptographic primitives are the building blocks of modern secure systems. Candidates will need to understand the role of a Public Key Infrastructure (PKI) in managing digital certificates and enabling secure communication over the internet through protocols like SSL/TLS. The domain also touches upon common cryptographic attacks, such as password cracking and man-in-the-middle attacks, and discusses the principles of steganography, which is the practice of concealing a message within another file or message. While this domain is not as heavily weighted as others, a solid grasp of these concepts is necessary to have a complete understanding of information security.
Navigating the Complex Cost Structure of the CEH
Understanding the full financial investment required for the Certified Ethical Hacker certification can be surprisingly complex, as the total cost is composed of several different components. The first fee nearly every candidate will encounter is a non-refundable application fee, which is required for the certification body to review and approve your eligibility to take the exam. This fee is mandatory for candidates who are seeking eligibility based on their professional work experience. After the application is approved, the next major expense is the exam voucher itself. The cost of this voucher can vary significantly. Purchasing the voucher directly from the official body to take the exam at an authorized testing center represents one price point. However, this price can be different if you purchase it as part of a training bundle. Training costs, which represent the largest potential expense, are highly variable and depend on the format and provider you choose. Finally, for those who wish to achieve the advanced CEH Master designation, there is an additional, separate fee for the Practical exam. It is crucial to budget for all these potential costs from the outset to avoid any financial surprises during your certification journey.
A Breakdown of Official Training Options
For candidates who choose to fulfill the eligibility requirement through formal education, the certification body offers several official training packages. These programs are designed to provide a comprehensive and structured learning experience that covers all the exam domains in detail. One popular option is an on-demand video course, which provides pre-recorded lessons that you can watch at your own pace. This format typically includes access to virtual lab environments for hands-on practice and a voucher for the CEH exam. This is a flexible option for those with busy schedules. For learners who prefer a more interactive experience, there is often a live online training option. This format features a live instructor who delivers the course material in real-time over a set period, usually an intensive one-week bootcamp. This allows for direct interaction with the instructor and peers, enabling you to ask questions and participate in discussions. While these live courses are generally the most expensive official option, they provide a highly immersive and focused learning environment. All official training paths are designed to thoroughly prepare you for the exam and automatically grant you eligibility upon completion.
Evaluating Third-Party Training Providers and Bootcamps
Beyond the official training offered directly by the certification body, there is a vast ecosystem of accredited training centers and independent providers that offer CEH preparation courses and bootcamps. These third-party options can vary considerably in terms of cost, format, and instructional quality. Many of these providers are official partners, meaning their curriculum is approved and they are authorized to deliver the official courseware. These courses often provide a similar experience to the official live training, sometimes at a more competitive price point or with additional study materials included. When evaluating a third-party provider, it is important to do your research. Look for reviews and testimonials from past students. Inquire about the instructor's credentials and real-world experience in the cybersecurity field. Check if the course includes access to hands-on labs, practice exams, and an exam voucher. Some bootcamps offer additional benefits, such as career counseling or post-course support. While these options can provide excellent value, it is essential to ensure they are reputable and that their training methods align with your personal learning style to maximize your investment.
The Self-Study Path: Is It Right for You?
For candidates who already possess the required two years of information security experience, the self-study path offers a more flexible and cost-effective route to certification. This option allows you to prepare for the exam using your own resources and on your own schedule, without the need to enroll in a formal training course. This path is ideal for disciplined, self-motivated individuals who are comfortable directing their own learning and already have a strong foundational knowledge of networking and security concepts. It can significantly reduce the overall cost of obtaining the certification. However, the self-study path is not without its challenges. It requires a high degree of personal commitment and time management. You will be responsible for sourcing all your study materials, building a hands-on lab environment for practice, and ensuring you cover every topic in the exam blueprint in sufficient detail. Without the structure of a formal course, it can be easy to fall behind or to overlook critical topic areas. Before choosing this path, honestly assess your learning style and the amount of time you can realistically dedicate to your studies.
Essential Study Resources: Books and Official Guides
For those on the self-study path, or even for those in a formal course looking for supplementary material, high-quality study guides are indispensable. There are several highly regarded books specifically written for CEH exam preparation. These guides are often comprehensive, covering each exam domain in great detail with clear explanations, diagrams, and examples. A good study guide will not only teach the theoretical concepts but also provide practical insights into how these concepts are applied in the real world. Many guides also include chapter review questions and practice exams to help you test your comprehension. Two of the most frequently recommended resources are the "CEH Certified Ethical Hacker All-in-One Exam Guide" and the "CEH Certified Ethical Hacker Study Guide." These books are written by experienced security professionals and are updated regularly to align with the latest version of the exam blueprint. In addition to third-party books, the official courseware provided by the certification body can sometimes be purchased separately. These official materials are the most direct source of information and are guaranteed to be aligned with the exam content, making them a valuable, if sometimes costly, resource.
The Importance of Hands-On Labs and Practical Experience
The CEH exam, while multiple-choice, is not just a test of rote memorization. Many questions are scenario-based, requiring you to apply your knowledge to solve a practical problem. Therefore, hands-on experience is not just a recommendation; it is a critical component of effective preparation. Reading about a tool or technique is one thing, but actually using it to perform a task solidifies your understanding in a way that passive learning cannot. You need to spend significant time in a lab environment, practicing the skills covered in the exam blueprint. You can build your own lab using virtualization software like VirtualBox or VMware. This allows you to create a network of virtual machines, including attacker machines and vulnerable target systems, where you can safely and legally practice your skills. There are many intentionally vulnerable virtual machines available online specifically for this purpose. Alternatively, many online platforms offer pre-configured virtual lab environments for a subscription fee. These services remove the complexity of setting up and maintaining your own lab, allowing you to focus purely on learning the techniques.
Utilizing Practice Exams and Quizzes for Readiness Assessment
Practice exams are an essential tool for gauging your readiness and refining your test-taking strategy. They help you become familiar with the format, style, and difficulty of the questions you will face on the real exam. Taking a full-length practice test under timed conditions can help you identify any knowledge gaps across the different domains. After completing a practice exam, it is crucial to review every question, both those you got right and those you got wrong. Understanding why a particular answer is correct and why the others are incorrect provides a valuable learning opportunity. There are many sources for practice questions, including the end-of-chapter quizzes in study guides, dedicated books of practice tests, and online platforms that offer large banks of questions. Some online providers offer adaptive quizzes that can help you focus on your weakest areas. Regularly incorporating practice questions into your study routine can help you track your progress over time and build your confidence. By the time you sit for the actual exam, the experience should feel familiar, reducing anxiety and allowing you to perform at your best.
Developing an Effective and Consistent Study Plan
To tackle the vast amount of material covered by the CEH, a structured study plan is essential. Start by downloading the official exam blueprint and use it as a checklist. Break down each of the nine domains into smaller, more manageable topics. Then, allocate specific blocks of time in your calendar for studying. Consistency is more important than intensity. Studying for one or two hours every day is far more effective than cramming for ten hours once a week. This approach, known as spaced repetition, helps move information from your short-term to your long-term memory. Your study plan should incorporate a variety of learning activities to keep you engaged. Mix up your sessions between reading study guides, watching video tutorials, working in your hands-on lab, and taking practice quizzes. This multi-modal approach caters to different learning styles and reinforces concepts in different ways. Set realistic weekly goals and track your progress against your plan. Be prepared to adjust your schedule as needed based on which topics you find more challenging. A well-organized plan will keep you focused and ensure you cover all the required material before your exam date.
Time Management Strategies for Exam Day
The CEH exam gives you four hours to answer 125 questions, which averages out to just under two minutes per question. Effective time management during the exam is critical to your success. Before you start, it is a good idea to quickly scan through the entire exam to get a sense of the questions. As you work through the test, do not get bogged down on any single question. If you encounter a question that you are unsure about, make your best educated guess, flag it for review, and move on. You can always come back to it later if you have time. Your goal should be to complete a full pass of all 125 questions, answering all the ones you are confident about. This ensures you secure all the "easy" points. Then, you can use your remaining time to go back and review the questions you flagged. Pacing yourself is key. Keep an eye on the clock and be aware of how much time you have left. Having practiced with full-length, timed exams beforehand will make this process feel much more natural and will help you stay calm and focused under pressure.
Moving Beyond Theory: An Introduction to the CEH Practical
The Certified Ethical Hacker Practical exam represents the next step in the certification journey, designed for those who want to prove their hands-on skills in addition to their theoretical knowledge. While the initial CEH exam is a multiple-choice test that validates what you know, the Practical is a performance-based assessment that validates what you can do. It is an entirely separate exam that can only be taken after you have successfully passed the CEH knowledge-based exam. Its purpose is to provide a verifiable demonstration of a candidate's real-world ethical hacking abilities in a simulated environment. This exam is not about recalling facts or choosing the best answer from a list. Instead, it requires you to actively perform penetration testing tasks. Candidates are presented with a series of challenges that require them to use common hacking tools and techniques to find and exploit vulnerabilities in live systems. Successfully passing this rigorous exam earns the candidate the prestigious CEH Master designation, which signals a higher level of competence and practical expertise to employers. It is the definitive answer to the question of whether a CEH holder can apply their knowledge in a real-world scenario.
The CEH Practical Exam Format and Environment
The CEH Practical is a six-hour, open-book exam that is conducted entirely online. Candidates connect to a specialized, browser-based virtual lab environment provided by the certification body. This environment, often referred to as a "cyber range," contains a network of virtual machines that are intentionally configured with various vulnerabilities. You are presented with 20 separate challenges, each with a specific objective that you must complete. The exam is proctored remotely via webcam to ensure the integrity of the testing process. The open-book format means you are allowed to use your own notes and search the internet for information. This format is designed to simulate a real-world penetration testing engagement, where testers have access to resources and are judged on their results, not their ability to memorize commands. The challenges are not linear; you can tackle them in any order you choose. Each successfully completed challenge earns you points, and you must reach a minimum passing score to pass the exam. The six-hour time limit is strict, making time management a crucial skill. The entire experience is designed to be an immersive and realistic test of your practical abilities.
Key Skills Tested in the Practical Exam
The CEH Practical exam tests a wide range of hands-on skills that mirror the phases of a real penetration test. You will be required to demonstrate proficiency in information gathering and reconnaissance. This includes using tools to perform network scanning and enumeration to discover live hosts, open ports, and running services on the target network. Once you have mapped out the network, you will need to identify potential vulnerabilities. This involves using vulnerability scanning tools and manually probing services to find weaknesses that can be exploited, which is a core skill for any penetration tester. The exam then moves on to exploitation. You will be expected to use your findings to gain unauthorized access to target systems. This could involve exploiting a known software vulnerability, cracking passwords, or leveraging a misconfiguration. After gaining access, you may need to perform privilege escalation to gain higher-level control of the system. The exam also tests skills in areas like web application hacking, requiring you to perform attacks such as SQL injection or directory traversal. Throughout the exam, you must be able to effectively use a variety of common penetration testing tools.
Mastering Port Scanning and Vulnerability Identification Tools
A significant portion of the challenges in the CEH Practical will rely on your ability to effectively use scanning tools to gather information and identify weaknesses. Mastery of tools like Nmap is absolutely essential. You need to go beyond a simple default scan and understand how to use Nmap's various scan types, its scripting engine for advanced enumeration, and its output options for parsing results. You will also be tested on your ability to use other tools, such as hping, for crafting custom network packets to probe firewall rules and network behavior. Beyond port scanning, you will need to be proficient with dedicated vulnerability assessment tools. This could include using scanners to automatically check for known vulnerabilities in the operating systems and services you discover on the network. However, the exam is not just about running automated tools. It also tests your ability to manually verify the findings of these tools and to identify vulnerabilities that automated scanners might miss. This requires a deep understanding of how different services and protocols work and the common misconfigurations associated with them.
Simulating Real-World Attacks: System and Network Exploitation
The ultimate goal of the CEH Practical is to test your ability to compromise systems. The challenges will require you to perform a variety of attacks against the virtual machines in the lab environment. This includes network-level attacks, such as sniffing network traffic to capture credentials or other sensitive information. You might also be required to perform session hijacking or denial-of-service attacks to disrupt services. The exam is designed to test your ability to think creatively and chain together multiple smaller vulnerabilities to achieve a larger objective, just as a real attacker would. System-level exploitation is also a key component. This could involve using a framework like Metasploit to launch an exploit against a vulnerable service to gain a remote shell on a target machine. You will also be tested on your knowledge of password attacks, requiring you to use tools to crack password hashes that you might discover on a compromised system. The challenges are designed to be realistic, reflecting the types of scenarios you would encounter during an actual penetration testing engagement, providing a true measure of your offensive security skills.
Deep Dive into Web Application and SQL Injection Attacks
Given the prevalence of web applications, a number of the CEH Practical challenges will focus specifically on web-based vulnerabilities. You must be prepared to identify and exploit common web application flaws. This requires proficiency with tools that can intercept and manipulate web traffic, allowing you to analyze and modify the requests sent from your browser to the web server. This is a fundamental technique for testing the security of any web application. The exam will test your ability to use these tools to find and exploit vulnerabilities. One of the most critical skills tested is SQL injection. You will be expected to demonstrate your understanding of how to manually identify and exploit SQL injection vulnerabilities to bypass authentication, extract sensitive data from the database, or even gain control of the underlying database server. This goes beyond simply using automated tools; it requires a true understanding of SQL syntax and how web applications construct database queries. Other web attacks, such as file inclusion, command injection, and directory traversal, are also likely to be included in the challenges.
Essential Tools for the CEH Practical Exam
To be successful on the CEH Practical, you must be comfortable with a wide range of standard penetration testing tools. The attacker machine provided in the lab environment is typically a Linux distribution that comes pre-loaded with most of the tools you will need. You should have hands-on experience with network scanners like Nmap and vulnerability scanners. For exploitation, familiarity with the Metasploit Framework is crucial, including how to search for exploits, configure payloads, and manage sessions. For password cracking, you should know how to use tools like John the Ripper or Hashcat. For web application testing, proficiency with an intercepting proxy is non-negotiable. You should also be familiar with common command-line tools for interacting with web servers, such as cURL or Wget. Knowledge of scripting languages like Python or Bash can also be extremely helpful for automating repetitive tasks, although it is not strictly required. Since the exam is open-book, you do not need to memorize the exact syntax for every command, but you must know which tool is appropriate for a given task and where to find the documentation for it quickly.
Strategies for Tackling the 20 Live Challenges
With 20 challenges to complete in just six hours, an effective strategy is essential. Start by taking some time at the beginning of the exam to read through all the challenges. This will give you a high-level overview of the tasks you need to complete. Triage the challenges and start with the ones that seem easiest or most familiar to you. These "quick wins" will help you build momentum and confidence, and they will bank you some early points. Do not attempt to complete the challenges in numerical order unless that happens to align with your strategy. Time management is your most important asset. Do not spend too much time stuck on a single challenge. If you are not making progress after a reasonable amount of time, move on to another one. You can always come back to it later. The open-book nature of the exam is a huge advantage. Use it. If you are unsure about a tool's syntax or a particular technique, use the internet to look it up. The goal is not to prove you have memorized everything but to prove you can solve problems efficiently, which is exactly what a real penetration tester does.
Preparing for a Hands-On, Performance-Based Assessment
Preparation for the CEH Practical is fundamentally different from preparing for the multiple-choice exam. While theoretical knowledge is still important, your focus must be almost entirely on hands-on practice. The best way to prepare is to spend as much time as possible in a lab environment, working through practical scenarios. Build your own lab or subscribe to an online cyber range platform that offers penetration testing challenges. Work through intentionally vulnerable machines, practicing the entire lifecycle from scanning and enumeration to exploitation and privilege escalation. Document your process as you work through these practice machines. Take notes on the commands you use and the techniques that work. This will not only help you learn but will also create a valuable set of notes that you can reference during the open-book exam. The more hands-on practice you get, the faster and more efficient you will become. The goal is to build muscle memory so that when you face a challenge on the exam, you can quickly identify the right tool and technique to use without wasting precious time.
The Demand for Ethical Hackers in the Modern Workforce
In today's digitally driven world, the demand for skilled ethical hackers has never been higher. As organizations of all sizes face an ever-increasing barrage of sophisticated cyber threats, they are recognizing that a purely defensive security strategy is no longer sufficient. Companies are actively seeking professionals who can think like an attacker to proactively identify and fix security flaws before they are exploited. This has created a robust job market for individuals with offensive security skills, and the demand is projected to continue growing for the foreseeable future. This demand is driven by several factors, including the increasing complexity of IT environments, the widespread adoption of cloud computing and IoT devices, and a growing body of data privacy regulations that mandate stringent security measures. Breaches are not only technically damaging but can also result in enormous financial losses, regulatory fines, and irreparable harm to a company's reputation. As a result, organizations are investing heavily in their security teams, and ethical hackers are a cornerstone of a mature and proactive security program, making them highly sought-after professionals.
Translating CEH Certification into Job Opportunities
Holding the Certified Ethical Hacker certification can significantly enhance your job prospects in the cybersecurity field. It is one of the most recognized entry-to-intermediate level certifications in the industry, and it often serves as a key filter for recruiters and hiring managers. When a company is looking for a candidate with offensive security knowledge, the CEH credential on a resume immediately signals a certain baseline of knowledge. It demonstrates a formal understanding of hacking methodologies and a commitment to the ethical and professional standards of the profession. For those looking to enter the cybersecurity field, the CEH can be a powerful differentiator. It can help your resume stand out from a pile of applicants who may have general IT experience but no specific security credentials. For those already in IT roles, it can open doors to more specialized security positions. While the certification alone is not a guarantee of a job, it is a valuable tool that can get you noticed and help you secure an interview, at which point you can further demonstrate your practical skills and knowledge.
A Final Analysis
The question of whether any certification is "worth it" is subjective and depends on an individual's career goals and circumstances. However, for those looking to build a career in offensive cybersecurity, the general consensus is that the Certified Ethical Hacker certification provides significant value. It offers a structured and comprehensive curriculum that covers the essential knowledge areas of ethical hacking. It is one of the most recognized brand names in the certification world, which can provide a significant boost to your visibility in the job market. While the cost can be a considerable investment, especially for those who opt for official training, the potential return in terms of job opportunities and salary potential is substantial. The certification is particularly valuable for those who are trying to break into the cybersecurity field or transition from a general IT role. While some experienced professionals may debate its merits compared to more advanced, hands-on certifications, few would argue against its effectiveness as a foundational credential that opens doors and establishes a solid baseline of knowledge for a successful career in ethical hacking.
CEH certification practice test questions and answers, training course, study guide are uploaded in ETE files format by real users. Study and pass ECCouncil CEH certification exam dumps & practice test questions and answers are the best available resource to help students pass at the first attempt.