- Home
- ECCouncil Certifications
- 312-50v10 Certified Ethical Hacker v10 Exam Dumps
Pass ECCouncil CEH 312-50v10 Exam in First Attempt Guaranteed!
Get 100% Latest Exam Questions, Accurate & Verified Answers to Pass the Actual Exam!
30 Days Free Updates, Instant Download!


312-50v10 Premium Bundle
- Premium File 322 Questions & Answers. Last update: Oct 02, 2025
- Training Course 182 Video Lectures
- Study Guide 1299 Pages
Last Week Results!

Includes question types found on the actual exam such as drag and drop, simulation, type-in and fill-in-the-blank.

Based on real-life scenarios similar to those encountered in the exam, allowing you to learn by working with real equipment.

Developed by IT experts who have passed the exam in the past. Covers in-depth knowledge required for exam preparation.
All ECCouncil CEH 312-50v10 certification exam dumps, study guide, training courses are Prepared by industry experts. PrepAway's ETE files povide the 312-50v10 Certified Ethical Hacker v10 Exam practice test questions and answers & exam dumps, study guide and training courses help you study and pass hassle-free!
Exploring the Worth of the Certified Ethical Hacker 312-50v10 Certification
The 312-50v10 exam is designed to assess the knowledge and skills of cybersecurity professionals in ethical hacking and penetration testing. It evaluates the ability to think like a hacker while maintaining ethical and legal boundaries, ensuring that candidates can identify, analyze, and mitigate threats to information systems effectively. The exam is structured to test practical knowledge across various domains including network security, system vulnerabilities, web applications, and wireless systems.
Ethical hacking requires a combination of technical expertise, analytical thinking, and practical problem-solving. Candidates must understand the full spectrum of attack vectors that malicious actors may exploit. This includes reconnaissance techniques, vulnerability scanning, exploitation, post-exploitation, and reporting. The 312-50v10 exam emphasizes applying these concepts in real-world scenarios, reinforcing the importance of both defensive strategies and proactive threat identification.
Understanding the scope of the 312-50v10 exam involves recognizing its emphasis on legal and ethical considerations. Ethical hackers must adhere to professional standards and organizational policies, ensuring that testing and security evaluations do not compromise sensitive data or violate regulatory requirements. This ethical framework is integral to the certification, distinguishing it from general hacking knowledge by focusing on responsible and lawful practices.
Core Knowledge Areas of the 312-50v10 Exam
The 312-50v10 exam covers multiple critical knowledge areas essential for modern cybersecurity operations. One primary domain is footprinting and reconnaissance, which involves gathering information about target systems through both passive and active methods. Candidates learn how to analyze publicly available information, perform network mapping, and identify potential points of entry for further testing. This foundational knowledge is crucial for understanding system exposure and designing effective security measures.
Scanning and enumeration are also central to the exam, requiring candidates to detect live hosts, open ports, and running services. These activities help ethical hackers identify potential vulnerabilities and assess risk levels within a network environment. Skills in vulnerability analysis, using both automated tools and manual techniques, are tested to ensure that candidates can identify weaknesses accurately and prioritize remediation efforts.
System hacking is another important area covered by the 312-50v10 exam. Candidates must understand methods for gaining access to systems, escalating privileges, and maintaining persistence in a controlled and ethical manner. Knowledge of password cracking, privilege escalation techniques, and exploiting misconfigurations enables professionals to evaluate the effectiveness of security controls. The exam tests the ability to apply these skills without causing harm, demonstrating mastery of ethical hacking principles.
Web Application and Database Security
Modern enterprise environments rely heavily on web applications, making their security a vital component of the 312-50v10 exam. Candidates are expected to understand common web application vulnerabilities, including SQL injection, cross-site scripting, cross-site request forgery, and file inclusion attacks. They must also know how to use testing tools to identify weaknesses and implement appropriate mitigations.
Database security forms an integral part of web application assessment. Candidates learn to analyze database configurations, permissions, and query execution to identify potential vulnerabilities. Understanding injection attacks, privilege escalation within database systems, and secure configuration practices ensures that sensitive data remains protected from unauthorized access. The ability to simulate attacks in a controlled environment demonstrates practical proficiency in protecting web-facing systems.
Wireless Network Security
The 312-50v10 exam also emphasizes securing wireless networks, an area of growing importance in enterprise security. Candidates are tested on their understanding of wireless protocols, encryption methods, and authentication mechanisms. Knowledge of Wi-Fi security standards, including WPA, WPA2, and WPA3, allows professionals to assess network resilience against attacks such as rogue access points, man-in-the-middle attacks, and eavesdropping.
Candidates must also understand wireless scanning and exploitation techniques, including cracking weak encryption, exploiting default configurations, and intercepting traffic. Skills in detecting unauthorized access points, monitoring network traffic, and implementing robust security controls are essential for maintaining enterprise wireless security. Practical application ensures that ethical hackers can identify risks without compromising legitimate users or operations.
Network Defense and Countermeasures
Beyond identifying vulnerabilities, the 312-50v10 exam emphasizes implementing security measures and countermeasures. Candidates must understand firewalls, intrusion detection systems, intrusion prevention systems, and endpoint security solutions. Knowledge of network segmentation, access control lists, and traffic monitoring is critical for designing resilient defenses.
Ethical hackers are also expected to provide actionable recommendations based on assessments. This includes advising on patch management, secure configuration, and mitigation of identified risks. The ability to document findings and communicate technical issues effectively to management and technical teams is a key component of the exam. Candidates must demonstrate not only technical skills but also analytical and reporting capabilities that support enterprise security governance.
Threat Analysis and Risk Assessment
Risk assessment forms a major component of the 312-50v10 exam. Candidates must evaluate the potential impact of security breaches and prioritize threats based on severity and likelihood. This involves understanding attack vectors, threat intelligence sources, and vulnerability management frameworks. Candidates are tested on their ability to conduct risk analysis for systems, networks, and applications, ensuring that security strategies are aligned with organizational priorities.
The exam also covers social engineering, a critical component of real-world security testing. Candidates must understand techniques such as phishing, pretexting, and baiting, and how to assess an organization’s susceptibility to these attacks. Awareness of human factors in cybersecurity complements technical knowledge and ensures that professionals can provide holistic recommendations to reduce risk across all layers of the enterprise environment.
Malware Analysis and Threat Detection
The 312-50v10 exam evaluates knowledge of malware types, behaviors, and analysis techniques. Candidates learn to identify viruses, worms, trojans, ransomware, and spyware. Understanding the propagation methods, payload capabilities, and detection mechanisms for malware is essential for effective security management.
Practical skills in malware analysis, sandboxing, and forensic investigation are tested to ensure candidates can assess and mitigate threats efficiently. Ethical hackers must be able to detect and respond to malicious activity while preserving evidence for incident response or regulatory compliance. Knowledge of malware detection tools and behavior-based analysis supports proactive defense strategies in enterprise environments.
Penetration Testing Methodologies
Penetration testing is a core focus of the 312-50v10 exam. Candidates are expected to conduct structured testing using recognized methodologies. This includes planning, reconnaissance, scanning, exploitation, post-exploitation, and reporting. Emphasis is placed on maintaining ethical standards and ensuring that testing activities do not disrupt production environments.
Candidates also learn to design test scenarios that simulate realistic attack patterns, evaluate the effectiveness of security controls, and propose mitigation strategies. Penetration testing skills demonstrate the ability to identify vulnerabilities in a controlled environment and provide organizations with actionable insights to enhance overall security posture.
Incident Response and Reporting
The 312-50v10 exam highlights the importance of incident response and communication. Candidates must understand the procedures for responding to detected attacks, containing threats, and restoring systems to a secure state. Reporting findings clearly and effectively is essential, as security recommendations must be understood by both technical staff and organizational leadership.
Documentation and reporting skills are evaluated to ensure that professionals can convey technical details, risk assessments, and remediation recommendations in a structured and actionable format. This competency supports decision-making and strengthens the organization’s ability to prevent, detect, and respond to future threats.
Continuous Learning and Skill Development
The 312-50v10 exam encourages continuous learning and adaptation to emerging cybersecurity challenges. Candidates are expected to stay informed about new vulnerabilities, attack techniques, and defense mechanisms. Hands-on practice, scenario-based exercises, and engagement with evolving technologies reinforce knowledge and maintain proficiency in ethical hacking practices.
Mastery of the 312-50v10 objectives equips professionals with the skills necessary to secure enterprise environments effectively, anticipate attacks, and provide informed guidance on risk mitigation. The exam evaluates both conceptual understanding and practical proficiency, ensuring that candidates are capable of applying ethical hacking principles across a wide range of systems and networks
Preparing for the 312-50v10 Exam
Effective preparation for the 312-50v10 exam requires a structured approach that combines theoretical knowledge with practical experience. Candidates must build a deep understanding of cybersecurity concepts, penetration testing methodologies, and ethical hacking frameworks. Study plans typically begin with reviewing the exam objectives, which outline domains such as network security, web application security, wireless security, malware analysis, and risk assessment. A thorough comprehension of these domains ensures that candidates are well-prepared to apply their skills in realistic scenarios.
Hands-on practice is a critical component of preparation. Candidates are encouraged to use lab environments that simulate real-world networks, systems, and applications. These environments allow ethical hackers to safely explore vulnerabilities, execute penetration tests, and analyze security controls without risking actual organizational assets. By practicing these techniques, candidates reinforce their understanding of attack methods and defensive strategies, making theoretical concepts tangible and actionable.
In addition to practical labs, familiarity with a wide range of cybersecurity tools is essential. Candidates must understand how to use scanning tools, vulnerability assessment platforms, exploitation frameworks, and traffic analysis utilities. Mastery of these tools enables ethical hackers to perform tasks efficiently and accurately, from footprinting and reconnaissance to post-exploitation and reporting. The ability to apply these tools effectively is often a distinguishing factor for success on the 312-50v10 exam and in professional roles.
Exam Domains and Skills
The 312-50v10 exam covers a broad spectrum of technical and analytical skills. Reconnaissance is a foundational domain where candidates learn to gather information about systems and networks, identifying potential weaknesses before attempting exploitation. Skills in passive reconnaissance, such as analyzing publicly available information, and active reconnaissance, such as port scanning and network mapping, are both assessed. Understanding how to identify and interpret data from these activities is crucial for developing effective penetration testing strategies.
Scanning and enumeration are next, requiring candidates to detect live hosts, discover services, and identify system vulnerabilities. Skills in using tools to automate scanning while interpreting the results accurately are emphasized. Candidates must prioritize vulnerabilities based on severity and potential impact, demonstrating the ability to focus resources on the most critical areas for remediation.
System hacking involves techniques to gain access to systems and escalate privileges within ethical boundaries. Candidates learn about password attacks, privilege escalation, and exploitation of misconfigurations. Mastery of these concepts enables professionals to simulate realistic attack scenarios, identify potential weaknesses, and recommend corrective actions that enhance system security.
Web application security is a critical domain, reflecting the widespread reliance on web-based services in enterprise environments. Candidates must understand vulnerabilities such as SQL injection, cross-site scripting, and insecure authentication mechanisms. Skills in testing, analyzing, and mitigating these vulnerabilities are essential for securing applications and protecting sensitive data. Knowledge of secure coding practices, input validation, and session management further supports robust application security.
Wireless Network Security and Threat Mitigation
The 312-50v10 exam also emphasizes securing wireless networks, which are increasingly prevalent in organizational infrastructures. Candidates must understand encryption protocols, authentication methods, and common wireless attacks. Techniques for detecting rogue access points, performing traffic analysis, and exploiting weak configurations are assessed. Candidates are expected to recommend and implement secure configurations that prevent unauthorized access and maintain network integrity. Understanding emerging standards, including WPA3, and their implications for security, is vital for modern enterprise networks.
Threat mitigation strategies are critical for both wireless and wired networks. Candidates must demonstrate knowledge of firewall configurations, intrusion detection and prevention systems, and network segmentation. Implementing layered defenses, monitoring network activity, and responding to anomalies are core skills that reflect the practical requirements of ethical hacking. The exam tests the ability to integrate these strategies into a cohesive security framework that addresses multiple attack vectors simultaneously.
Malware Analysis and Detection
Malware analysis is an essential component of the 312-50v10 exam. Candidates must understand various malware types, propagation methods, and payload behaviors. Skills in identifying viruses, trojans, worms, ransomware, and spyware are assessed, along with knowledge of detection techniques and countermeasures. Practical exercises in sandbox environments allow candidates to analyze malware behavior safely, evaluate the impact on systems, and recommend mitigation strategies.
Candidates are also expected to interpret log files, network traffic, and system behavior to detect potential infections. Understanding how malware interacts with operating systems, applications, and network components enables ethical hackers to anticipate attack patterns and design preventive measures. This domain reinforces the integration of technical knowledge and analytical skills necessary for effective cybersecurity operations.
Penetration Testing Methodologies and Reporting
Penetration testing is central to the 312-50v10 exam. Candidates must demonstrate a structured approach, including planning, reconnaissance, scanning, exploitation, post-exploitation, and reporting. The exam emphasizes the importance of maintaining ethical standards while simulating real-world attacks. Candidates are evaluated on their ability to identify vulnerabilities, exploit weaknesses responsibly, and provide actionable recommendations for remediation.
Effective reporting is an essential skill. Candidates must document findings clearly, providing technical details, risk assessments, and mitigation suggestions. The ability to communicate results to both technical and non-technical stakeholders ensures that organizations can take informed actions to enhance security. Reporting also reinforces the importance of ethical responsibility, transparency, and accountability in cybersecurity practice.
Risk Assessment and Threat Modeling
Risk assessment and threat modeling are critical components of the 312-50v10 exam. Candidates must evaluate potential security risks, prioritize threats, and recommend mitigation strategies based on severity and likelihood. This involves understanding the business impact of security breaches, attack vectors, and organizational assets. Candidates are expected to analyze complex systems, identify vulnerabilities, and assess the effectiveness of existing security controls.
Threat modeling provides a structured approach to anticipating attacks. Candidates learn to map potential attack paths, evaluate vulnerabilities, and develop defense strategies. Skills in assessing both technical and human factors, including social engineering risks, ensure that candidates can provide comprehensive recommendations that enhance organizational resilience.
Professional Relevance and Career Impact
The 312-50v10 certification is recognized for its relevance across multiple cybersecurity roles. Security analysts benefit from the ability to monitor networks, identify anomalies, and respond to incidents effectively. Security engineers leverage the knowledge gained from the exam to design resilient systems that account for potential attack vectors. Penetration testers use practical skills to conduct assessments and provide actionable insights. Security consultants and managers gain a holistic understanding of threats, enabling informed decision-making and policy development.
The exam also supports career progression by validating expertise in ethical hacking and penetration testing. Candidates demonstrate the ability to think strategically, apply technical skills, and communicate findings effectively. Employers recognize the certification as evidence of proficiency in protecting enterprise systems, reducing risks, and maintaining compliance with security standards. Professionals who achieve the 312-50v10 credential are equipped to advance into leadership roles, guide security initiatives, and contribute to organizational resilience against evolving threats
Advanced Preparation Strategies for the 312-50v10 Exam
Preparing for the 312-50v10 exam requires a multi-faceted approach that goes beyond reading study guides and memorizing concepts. Candidates must engage in a combination of theoretical study, hands-on practice, and scenario-based exercises. Understanding the exam blueprint is critical, as it identifies domains such as reconnaissance, scanning, system hacking, web application attacks, wireless security, malware analysis, social engineering, and risk assessment. Familiarity with these domains allows candidates to allocate study time efficiently and focus on areas that require deeper understanding
A key component of advanced preparation involves creating a lab environment that replicates real-world networks and systems. Virtual machines, isolated networks, and simulated enterprise environments enable candidates to practice penetration testing safely. These labs should include various operating systems, network devices, web applications, and databases. By experimenting with attack techniques, candidates develop an intuitive understanding of how vulnerabilities can be exploited and how defenses can be implemented effectively
Practical exercises should cover both automated and manual testing approaches. Automated tools accelerate scanning, vulnerability assessment, and enumeration, but understanding the underlying principles ensures that candidates can interpret results accurately. Manual testing complements automation by revealing subtle vulnerabilities, misconfigurations, and complex attack paths that tools alone may not detect. This combination reinforces comprehensive skill development and mirrors the real-world tasks performed by professional ethical hackers
Reconnaissance and Information Gathering
The reconnaissance phase is fundamental to ethical hacking and is heavily emphasized in the 312-50v10 exam. Candidates must understand passive and active reconnaissance techniques. Passive reconnaissance includes analyzing publicly available information, such as domain registration records, IP address ranges, and social media profiles, to identify potential targets. Active reconnaissance involves scanning networks, enumerating services, and probing systems to gather detailed technical information
Candidates should practice using reconnaissance tools to perform network mapping, service identification, and vulnerability discovery. Understanding how to collect, analyze, and synthesize information from multiple sources enables professionals to identify attack vectors effectively. Scenario-based exercises, such as simulating an enterprise network assessment, help candidates develop the ability to prioritize targets and plan testing strategies based on risk and potential impact
Scanning, Enumeration, and Vulnerability Analysis
Scanning and enumeration are critical domains within the 312-50v10 exam, requiring candidates to detect live hosts, open ports, running services, and system vulnerabilities. Skills in interpreting scan results, identifying false positives, and correlating data from multiple tools are essential. Candidates must also understand how to use vulnerability assessment tools to classify and prioritize weaknesses based on severity, exploitability, and potential impact on the organization
Practical exercises should include scanning internal and external networks, analyzing service banners, and evaluating system configurations. Candidates should be familiar with different scanning techniques, including TCP, UDP, ICMP, and stealth scans, and understand their implications for detection and evasion. Enumeration tasks, such as identifying shared resources, user accounts, and network services, are also critical for understanding the potential scope of an attack and planning mitigation strategies
System Hacking and Exploitation Techniques
System hacking is a central focus of the 312-50v10 exam. Candidates must master techniques for gaining access to systems, escalating privileges, maintaining persistence, and covering tracks. This domain includes password attacks, exploiting misconfigurations, and leveraging software vulnerabilities. Understanding how attackers achieve unauthorized access allows ethical hackers to implement preventive measures and improve system resilience
Scenario-based exercises enhance learning by simulating real-world attacks. Candidates can practice exploiting test systems in a controlled environment, gaining experience in identifying and mitigating weaknesses. Skills in privilege escalation, session hijacking, and persistence techniques are essential for demonstrating proficiency on the exam and applying knowledge in professional penetration testing engagements
Web Application Security Testing
Web application security is a critical area for the 312-50v10 exam, reflecting the prevalence of web-based services in enterprise environments. Candidates must understand common vulnerabilities, such as SQL injection, cross-site scripting, cross-site request forgery, and insecure authentication mechanisms. Practical exercises should include testing web applications for input validation flaws, session management weaknesses, and improper configuration of security headers
Candidates must also learn how to interpret results from web application scanners and apply manual testing techniques to uncover subtle vulnerabilities. Understanding secure coding practices, encryption of sensitive data, and implementation of access controls reinforces the ability to protect web applications effectively. Scenario-based labs allow candidates to simulate attacks on web environments, evaluate defenses, and recommend remediation strategies
Wireless Network Assessment
Wireless network security is increasingly important in enterprise environments, and the 312-50v10 exam assesses candidates on their ability to evaluate and secure wireless infrastructures. Knowledge of encryption standards, authentication protocols, and common attack vectors is essential. Candidates should practice detecting unauthorized access points, analyzing wireless traffic, and exploiting weak configurations in a controlled lab environment
Scenario-based exercises can include auditing wireless networks for rogue devices, performing traffic analysis, and simulating attacks such as man-in-the-middle or packet injection. Understanding emerging standards, including WPA3, and their implications for network security is important for both the exam and real-world applications. Candidates should also be prepared to recommend mitigation strategies and secure configurations for enterprise wireless deployments
Malware Analysis and Reverse Engineering
Malware analysis is a domain that evaluates the candidate's ability to identify, analyze, and mitigate malicious software. Candidates must understand malware types, behaviors, propagation methods, and detection techniques. Practical exercises should include analyzing malware in sandboxed environments, identifying indicators of compromise, and understanding the impact on system and network resources
Scenario-based learning may involve simulating malware infections, analyzing payload behavior, and implementing containment and remediation strategies. Candidates should be familiar with signature-based and behavior-based detection methods, as well as techniques for preventing malware propagation within an enterprise environment. Skills in documenting findings and recommending proactive measures are essential for demonstrating mastery of this domain on the exam
Social Engineering and Risk Assessment
The 312-50v10 exam includes social engineering as a component of ethical hacking. Candidates must understand techniques used to manipulate individuals into revealing sensitive information or performing actions that compromise security. Scenario-based exercises should include analyzing phishing campaigns, pretexting, baiting, and tailgating, and evaluating the effectiveness of security awareness programs
Risk assessment is closely related, requiring candidates to evaluate the likelihood and impact of potential threats. Candidates should practice identifying critical assets, mapping potential attack vectors, and prioritizing risks based on organizational context. Understanding the interplay between technical vulnerabilities and human factors is essential for comprehensive security assessments
Penetration Testing Methodology and Reporting
Structured penetration testing methodology is central to the 312-50v10 exam. Candidates are expected to follow a systematic approach, including planning, reconnaissance, scanning, exploitation, post-exploitation, and reporting. Scenario-based exercises allow candidates to simulate full testing engagements, assess defenses, and provide actionable recommendations for improving security
Reporting skills are emphasized to ensure that findings can be communicated effectively to technical teams and decision-makers. Candidates must learn to present vulnerabilities, risk levels, and mitigation strategies in a clear and actionable format. This domain tests not only technical knowledge but also the ability to convey complex security information to diverse audiences
Integration of Skills in Enterprise Environments
Mastery of the 312-50v10 exam objectives equips professionals to apply ethical hacking skills in enterprise settings. Candidates are expected to integrate knowledge across domains, combining reconnaissance, scanning, exploitation, malware analysis, and social engineering into a comprehensive security strategy. Scenario-based labs that mirror enterprise networks reinforce practical application, ensuring that professionals can anticipate attacks, implement defenses, and communicate findings effectively
Candidates who excel in the 312-50v10 demonstrate both technical expertise and strategic thinking. They can design security programs, assess vulnerabilities, mitigate risks, and support organizational objectives. The exam emphasizes holistic security knowledge, combining ethical hacking techniques with professional judgment, risk management, and communication skills
Applying 312-50v10 Skills in Enterprise Environments
The 312-50v10 exam equips cybersecurity professionals with the expertise needed to evaluate and secure enterprise systems effectively. Candidates are trained to integrate technical knowledge, risk assessment, and practical skills into a coherent strategy for protecting information assets. Enterprise environments often consist of complex networks, web applications, databases, and wireless systems, making a comprehensive understanding of vulnerabilities essential. Ethical hackers apply the techniques learned in reconnaissance, scanning, and exploitation to identify weaknesses before they can be exploited by malicious actors
Scenario-based exercises help professionals apply their skills in realistic environments. Simulated enterprise networks, including multiple subnets, firewalls, intrusion detection systems, and authentication mechanisms, provide opportunities to practice attack and defense techniques. Candidates can experiment with advanced penetration testing scenarios, performing tasks such as privilege escalation, lateral movement, and controlled exploitation, ensuring that learning is practical and applicable to real-world situations
Integrating skills across multiple domains is critical. Professionals must correlate findings from network scans, web application tests, and wireless assessments to develop a holistic understanding of the organization’s security posture. By combining technical analysis with strategic thinking, ethical hackers can prioritize vulnerabilities based on potential impact and recommend effective mitigation strategies. This multidisciplinary approach reflects the expectations of the 312-50v10 exam and supports effective decision-making in enterprise cybersecurity
Advanced Scenario-Based Exercises
Advanced scenario-based exercises are a key component of preparation for the 312-50v10 exam. Candidates simulate complex attack chains, incorporating multiple techniques and tools to identify vulnerabilities, test defenses, and analyze outcomes. These exercises often involve multi-layered networks, critical applications, and sensitive data, requiring professionals to consider both technical and procedural defenses
Scenarios include evaluating web applications for SQL injection, cross-site scripting, and insecure authentication, while simultaneously performing network scans and identifying misconfigured services. Candidates must also simulate social engineering attacks, assess the organization’s susceptibility, and implement preventive measures. Wireless network attacks, including rogue access point detection and encryption cracking, are incorporated to ensure comprehensive coverage of security domains
Through these exercises, candidates develop the ability to think like an attacker while maintaining ethical and legal boundaries. Understanding attack paths, recognizing potential vulnerabilities, and correlating findings across domains reinforces the practical application of the 312-50v10 exam content. Scenario-based labs also provide experience in documenting findings, presenting risk assessments, and proposing actionable solutions to technical and managerial stakeholders
Continuous Learning and Skill Enhancement
Mastery of the 312-50v10 exam requires ongoing learning and adaptation to new threats, tools, and methodologies. Cybersecurity professionals must stay informed about emerging vulnerabilities, advanced attack techniques, and evolving regulatory requirements. Continuous engagement with lab environments, simulations, and threat intelligence platforms ensures that skills remain current and applicable to professional roles
Hands-on practice remains critical for skill enhancement. Professionals should regularly perform penetration tests on controlled networks, evaluate new tools and scripts, and analyze malware and attack patterns. Experimenting with novel attack scenarios, such as advanced persistent threats or zero-day exploits, develops the analytical skills necessary to anticipate and mitigate emerging risks. This active learning approach mirrors the practical expectations of the 312-50v10 exam and supports ongoing professional growth
Collaborating with peers, participating in cybersecurity forums, and engaging with simulated incident response exercises also contribute to skill development. Sharing insights, discussing techniques, and analyzing case studies allows professionals to refine their approach and learn from diverse perspectives. Ethical hackers who adopt a mindset of continuous improvement are better prepared to address complex enterprise security challenges and maintain proficiency in multiple domains
Professional Applications and Career Impact
The knowledge and skills validated by the 312-50v10 exam have direct applications in numerous cybersecurity roles. Security analysts leverage expertise in reconnaissance, scanning, and intrusion detection to monitor networks, identify anomalies, and respond to incidents proactively. Security engineers use insights from penetration testing and risk assessment to design resilient architectures, implement security controls, and reduce exposure to attacks
Penetration testers apply scenario-based skills to evaluate systems, simulate attacks, and provide actionable recommendations. Their ability to integrate findings across network, web, and wireless domains enhances organizational security posture. Security consultants use the certification to advise enterprises on risk management strategies, develop security policies, and recommend mitigations based on a holistic understanding of potential threats
The 312-50v10 certification also benefits managers and leadership roles. Professionals in supervisory positions can leverage their understanding of ethical hacking principles to guide security initiatives, assess risk, and communicate effectively with technical teams. This competency ensures that decision-makers are informed, capable of evaluating security proposals, and able to implement strategies that align with organizational objectives
Incident Response and Threat Mitigation
Ethical hackers certified with 312-50v10 skills are trained to respond effectively to security incidents. They understand how to detect, contain, and remediate breaches while preserving evidence for analysis and compliance. This includes interpreting log files, network traffic, and system behavior to identify indicators of compromise and assess the scope of an incident
Scenario-based incident response exercises reinforce practical knowledge. Candidates practice isolating affected systems, analyzing malware behavior, and implementing mitigation measures to prevent further damage. Coordinating responses across technical teams, evaluating impact on business operations, and communicating findings to management are essential skills that reflect the expectations of enterprise cybersecurity roles and the 312-50v10 exam
Threat mitigation strategies extend beyond immediate incident response. Professionals apply knowledge of secure configurations, patch management, access controls, and monitoring solutions to reduce vulnerabilities. Implementing proactive measures ensures that the organization is better prepared to prevent future attacks, aligning technical skills with strategic objectives and regulatory compliance
Communication and Reporting Skills
The 312-50v10 exam emphasizes the importance of reporting and communication skills. Ethical hackers must document vulnerabilities, analyze risk levels, and provide recommendations in a clear, actionable format. Effective communication ensures that technical teams understand remediation priorities, while leadership can make informed decisions based on comprehensive risk assessments
Scenario-based labs and exercises reinforce reporting skills. Candidates prepare detailed documentation that includes technical findings, attack paths, mitigation strategies, and recommendations for improving overall security posture. These reports bridge the gap between technical expertise and managerial decision-making, demonstrating the ability to communicate complex security issues clearly and persuasively
Integration of Ethical Hacking Practices
Integrating ethical hacking practices into enterprise security operations is a key outcome of the 312-50v10 exam. Professionals apply principles learned in reconnaissance, scanning, exploitation, web and wireless security, malware analysis, social engineering, and incident response to develop robust defense strategies. This holistic approach ensures that vulnerabilities are identified, risks are prioritized, and mitigation measures are effectively implemented
Continuous practice, scenario-based exercises, and cross-domain integration allow ethical hackers to anticipate attacks, design resilient systems, and maintain compliance with regulatory and organizational requirements. Mastery of these skills supports a proactive security posture, enhancing the organization’s ability to protect critical assets, sensitive data, and operational continuity
Career Growth and Professional Recognition
Achieving 312-50v10 certification validates a professional’s expertise in ethical hacking and penetration testing. It demonstrates proficiency in identifying vulnerabilities, implementing mitigation strategies, and managing security risks across diverse enterprise environments. Employers recognize the certification as evidence of practical skills, ethical responsibility, and strategic thinking
Certified professionals are often positioned for advanced roles, including senior security analyst, penetration tester, security consultant, security engineer, and cybersecurity manager. The certification supports career advancement by providing tangible proof of competence, enhancing credibility, and demonstrating a commitment to maintaining up-to-date knowledge in a rapidly evolving field
Final Preparation Strategies for the 312-50v10 Exam
The last phase of preparation for the 312-50v10 exam should integrate knowledge, hands-on practice, and simulated scenarios. Candidates are advised to review the entire exam blueprint, ensuring familiarity with each domain, including reconnaissance, scanning, system exploitation, web application security, wireless networks, malware analysis, social engineering, and risk assessment. A comprehensive review allows candidates to identify areas that require reinforcement and focus study efforts efficiently
Practical labs should be revisited to consolidate skills. Candidates should simulate multi-step attacks, starting with information gathering, proceeding to scanning and enumeration, exploiting vulnerabilities, and documenting findings. These exercises reinforce logical sequencing and decision-making skills under exam conditions. Practicing in a controlled environment enables candidates to apply theoretical knowledge while gaining confidence in executing tasks accurately and efficiently
Reviewing past lab exercises and analyzing mistakes is an essential component of final preparation. Candidates should assess which techniques were challenging, whether tool usage was optimal, and how findings were documented. This reflection allows candidates to address knowledge gaps, refine methodologies, and increase efficiency. Understanding both successful and unsuccessful attempts provides insight into potential pitfalls during the actual exam
Scenario Mastery and Complex Attack Simulations
Scenario-based mastery is crucial for success on the 312-50v10 exam. Candidates should focus on multi-layered scenarios that combine multiple attack techniques across domains. For example, a simulated enterprise network may include vulnerable web applications, misconfigured servers, unsecured wireless networks, and simulated malware infections. Candidates are required to prioritize targets, identify vulnerabilities, and simulate attacks while maintaining ethical constraints
Simulations should include the application of defensive measures as well. Candidates should practice mitigating vulnerabilities they identify, configuring firewalls, implementing access controls, and securing wireless networks. This dual approach of attack and defense mirrors real-world cybersecurity roles and demonstrates the practical applicability of skills. Integrating threat modeling and risk assessment into scenario exercises allows candidates to evaluate potential impacts and prioritize mitigation efforts effectively
Candidates should also practice reporting their findings comprehensively. Each scenario should be documented, including detailed descriptions of vulnerabilities, methods used, potential impacts, and recommended countermeasures. This ensures that candidates can communicate their results clearly to technical teams and management, reflecting the professional expectations associated with the 312-50v10 certification
Time Management and Exam Strategy
Effective time management is a critical factor for passing the 312-50v10 exam. Candidates must develop strategies to allocate time efficiently across domains, balancing detailed analysis with broader coverage. Practicing timed lab exercises and mock exams helps candidates simulate the pacing of the actual test, reducing anxiety and improving decision-making under pressure
Candidates should focus on their strengths while allocating additional time to weaker areas. By prioritizing high-weighted domains and ensuring all topics are reviewed, candidates can maximize their score potential. Time management also involves deciding how long to spend on complex scenario questions, understanding when to move on, and ensuring that all questions are addressed within the allotted time frame
Developing a systematic approach to reading and interpreting questions is also important. Candidates should practice identifying key objectives, analyzing scenario details, and mapping them to appropriate techniques and tools. This strategic approach helps prevent misinterpretation and ensures that answers reflect the candidate’s practical skills and understanding of ethical hacking principles
Continuous Learning and Knowledge Reinforcement
Even during final exam preparation, continuous learning remains essential. Cybersecurity is a rapidly evolving field, and candidates must stay updated on emerging threats, attack techniques, and defensive technologies. Engaging with threat intelligence feeds, analyzing recent vulnerabilities, and testing mitigation strategies in lab environments reinforces the practical relevance of the 312-50v10 exam content
Knowledge reinforcement can be achieved through repeated practice of critical tasks. For example, candidates should regularly perform network reconnaissance, web application testing, wireless security audits, and malware analysis. By repeating these exercises, candidates strengthen procedural memory, refine tool usage, and gain confidence in executing complex operations efficiently
Collaborative learning can also enhance preparation. Candidates may benefit from study groups or peer exercises where scenario-based tasks are discussed and solutions are evaluated collectively. This approach allows for multiple perspectives, shared insights, and the identification of gaps in understanding. Peer discussions also provide opportunities to practice communication and reporting skills, which are essential for professional application of 312-50v10 knowledge
Professional Integration of 312-50v10 Skills
Beyond passing the exam, the 312-50v10 certification equips professionals to apply ethical hacking skills in enterprise and organizational contexts. Candidates are prepared to conduct penetration tests, assess risk, and recommend security improvements across network, system, and application layers. Mastery of these skills enables professionals to anticipate attacks, implement effective defenses, and contribute to overall organizational resilience
Integrating skills across domains ensures comprehensive security coverage. Professionals combine reconnaissance, vulnerability assessment, exploitation techniques, and defensive strategies to evaluate enterprise systems holistically. This integration allows ethical hackers to identify interdependencies, assess systemic weaknesses, and propose mitigations that address both technical vulnerabilities and human factors
Ethical hackers certified with 312-50v10 skills also contribute to strategic decision-making. Their insights support risk management, policy development, and security governance. By understanding the potential impact of threats on business operations, professionals can advise leadership on prioritization of security initiatives and resource allocation. This strategic contribution enhances organizational preparedness and ensures that security measures align with enterprise objectives
Advanced Incident Response and Threat Mitigation
Incident response is a key application of 312-50v10 skills. Certified professionals can detect, analyze, and respond to security incidents effectively. They are trained to identify indicators of compromise, contain threats, remediate affected systems, and preserve forensic evidence for analysis and compliance. Scenario-based incident response exercises allow candidates to practice real-world procedures, from isolating infected hosts to analyzing malware behavior and implementing countermeasures
Threat mitigation extends beyond immediate incident response. Professionals implement proactive measures such as secure configurations, patch management, access control policies, network segmentation, and monitoring solutions. These preventive strategies reduce the likelihood of successful attacks and enhance the overall security posture of the organization. By combining technical knowledge with strategic planning, candidates are prepared to manage both ongoing threats and long-term security challenges
Reporting and Communication for Enterprise Security
Effective reporting and communication are critical outcomes of 312-50v10 preparation. Professionals must document vulnerabilities, analyze risks, and provide actionable recommendations in a format that is understandable to technical teams and management. Clear, comprehensive reporting ensures that identified issues are addressed appropriately and that risk management decisions are informed by accurate technical analysis
Scenario-based exercises reinforce reporting skills. Candidates practice preparing detailed documentation that includes technical findings, attack vectors, risk ratings, and proposed mitigations. This process helps professionals convey complex security concepts concisely and persuasively, supporting collaboration between technical staff and leadership. Strong communication skills are essential for translating technical expertise into practical security solutions and ensuring organizational readiness
Consolidating Professional Competence
Achieving 312-50v10 certification represents the culmination of theoretical knowledge, hands-on practice, scenario mastery, and professional application. Candidates demonstrate proficiency in ethical hacking, penetration testing, risk assessment, malware analysis, wireless and web security, social engineering, and incident response. This comprehensive skill set enables professionals to contribute effectively to enterprise security initiatives, reduce organizational risk, and support regulatory compliance
Certified professionals are positioned for a range of career opportunities, including senior security analyst, penetration tester, security consultant, cybersecurity manager, and security engineer. The certification validates both technical expertise and strategic judgment, making professionals valuable assets to organizations seeking to enhance their cybersecurity posture. By mastering the domains covered in the 312-50v10 exam, candidates can advance their careers, influence security strategy, and ensure the resilience of enterprise systems against evolving threats
Advanced Integration of 312-50v10 Skills
The 312-50v10 exam is designed to validate comprehensive ethical hacking and penetration testing expertise. Professionals who achieve certification are expected to integrate multiple domains of knowledge to evaluate and enhance enterprise security. Advanced integration involves correlating reconnaissance, scanning, exploitation, web and wireless security, social engineering, malware analysis, and risk assessment into unified operational strategies. This integration ensures that vulnerabilities are not assessed in isolation but understood in the broader context of enterprise security architecture
In enterprise environments, multiple interdependent systems and networks create complex attack surfaces. Certified professionals apply advanced techniques to assess these surfaces systematically. They perform multi-layered penetration tests, analyze threat vectors, and evaluate the effectiveness of defensive measures. By combining findings from network scans, application testing, and social engineering exercises, ethical hackers can develop actionable mitigation plans that address both technical and procedural weaknesses
Advanced integration also includes understanding regulatory and compliance requirements. Professionals must ensure that assessments, testing procedures, and remediation strategies align with organizational policies and industry standards. Scenario-based exercises in controlled lab environments allow candidates to simulate compliance-oriented testing, including documenting audit trails, analyzing security controls, and verifying adherence to risk management protocols
Enterprise-Level Security Planning and Architecture
Achieving mastery in the 312-50v10 domains empowers professionals to contribute to enterprise-level security planning. Security architecture involves designing network segmentation, access controls, monitoring frameworks, and incident response protocols. Candidates apply knowledge from reconnaissance, vulnerability assessment, and exploitation techniques to identify potential weaknesses in architecture before deployment. This proactive approach minimizes exposure to threats and strengthens overall organizational resilience
Candidates also focus on multi-layered defense strategies. This includes implementing perimeter defenses such as firewalls and intrusion detection systems, securing web applications and databases, encrypting sensitive data, and managing identity and access management systems. By integrating these strategies into enterprise planning, professionals ensure that defensive measures are robust, comprehensive, and adaptable to emerging threats
Advanced planning also incorporates threat modeling and scenario simulations. Candidates evaluate potential attack paths, estimate the likelihood of exploitation, and assess the impact on critical business functions. This process allows organizations to prioritize security investments, optimize resource allocation, and implement preventative measures tailored to their operational environment. Ethical hackers who can link technical findings to strategic decision-making enhance organizational preparedness and risk management capabilities
Continuous Threat Intelligence and Vulnerability Management
The dynamic nature of cybersecurity threats necessitates continuous engagement with threat intelligence and vulnerability management. Certified professionals use threat intelligence feeds, security bulletins, and research publications to stay informed about emerging attack vectors and exploit techniques. This ongoing awareness enables timely identification of potential risks and informs proactive defense measures
Vulnerability management is closely linked to threat intelligence. Candidates practice identifying, classifying, and prioritizing vulnerabilities based on severity, exploitability, and potential business impact. Tools for automated scanning, patch management, and configuration auditing are applied to maintain system security. Professionals also evaluate the effectiveness of mitigation strategies, conducting follow-up assessments to ensure vulnerabilities are properly addressed and that defenses remain effective over time
Scenario-based exercises reinforce the connection between threat intelligence and practical application. Candidates simulate attacks based on recent vulnerabilities, test defenses, and assess how security controls respond under real-world conditions. This approach strengthens the ability to anticipate, detect, and mitigate threats in an enterprise context, reflecting the expectations of the 312-50v10 exam
Advanced Malware Analysis and Containment
Malware analysis is an essential component of the 312-50v10 exam, and advanced skills involve examining complex malicious software in enterprise environments. Certified professionals analyze malware behavior, propagation methods, payload execution, and potential impact on networks and systems. They apply sandboxing, static and dynamic analysis, and forensic techniques to understand malware functionality and develop containment strategies
Advanced containment strategies include isolating infected systems, blocking malicious traffic, and applying system-level mitigations. Professionals are trained to document findings, identify indicators of compromise, and recommend remediation plans that minimize operational disruption. Scenario-based exercises help candidates practice coordinated responses, integrating technical and procedural measures to limit the scope and impact of malware infections
Understanding malware in the context of enterprise systems also involves evaluating user behavior, network configurations, and application vulnerabilities. Ethical hackers use these insights to design preventive measures, including security awareness programs, system hardening, and automated monitoring solutions. Mastery of malware analysis ensures that professionals can respond effectively to incidents while maintaining operational continuity
Multi-Domain Penetration Testing and Red Team Exercises
The 312-50v10 exam emphasizes multi-domain penetration testing, which requires combining network, system, web application, and wireless assessments into comprehensive testing scenarios. Certified professionals conduct red team exercises, simulating realistic attack campaigns against enterprise environments. These exercises evaluate the effectiveness of security controls, test incident response procedures, and provide actionable recommendations for risk mitigation
Red team exercises also develop collaboration and communication skills. Candidates work alongside blue teams, sharing insights, coordinating responses, and validating the effectiveness of defensive measures. Scenario-based simulations reflect real-world enterprise challenges, requiring professionals to adapt techniques, prioritize targets, and maintain ethical standards while conducting assessments
Advanced multi-domain testing requires proficiency in both automated and manual techniques. Candidates practice using vulnerability scanners, exploitation frameworks, and penetration testing tools, while also performing detailed manual testing to identify subtle weaknesses. Integrating findings across domains allows professionals to deliver a holistic view of enterprise security and propose improvements that address systemic vulnerabilities
Strategic Risk Assessment and Management
Risk assessment and management are core competencies validated by the 312-50v10 exam. Certified professionals evaluate threats, vulnerabilities, and potential impacts to determine organizational risk. Scenario-based exercises involve identifying critical assets, assessing likelihood and consequences of exploitation, and prioritizing mitigation efforts. This approach ensures that resources are allocated efficiently and that high-risk areas are addressed proactively
Strategic risk management also incorporates policy development and compliance evaluation. Professionals ensure that security policies align with regulatory requirements and organizational objectives. They recommend technical and procedural controls, establish monitoring frameworks, and develop contingency plans for incident response. By integrating risk assessment into enterprise operations, ethical hackers enhance resilience and support informed decision-making at leadership levels
Continuous Learning and Professional Development
The 312-50v10 exam reinforces the importance of ongoing professional development. Cybersecurity threats evolve constantly, requiring professionals to engage in continuous learning, including research, lab experimentation, and participation in community forums. Staying current with emerging attack vectors, defense strategies, and tool advancements ensures that certified professionals maintain proficiency and adaptability in real-world environments
Continuous learning also involves reflecting on past assessments and penetration tests. Candidates analyze successes and shortcomings, adapt methodologies, and update skills accordingly. This iterative process strengthens analytical capabilities, enhances problem-solving skills, and ensures that ethical hackers remain effective in dynamic enterprise contexts
Advanced professional development may include mentoring, collaboration on complex security projects, and contributing to organizational security strategy. Certified professionals leverage their 312-50v10 skills to influence enterprise security policies, guide technical teams, and support continuous improvement initiatives, demonstrating leadership and expertise beyond technical proficiency
Career Impact and Enterprise Value
The 312-50v10 certification has significant career implications. Professionals who achieve this credential demonstrate mastery in ethical hacking, penetration testing, risk assessment, and incident response. They are equipped to handle complex enterprise security challenges, including securing networks, applications, systems, and user environments. Employers recognize the certification as evidence of practical skills, strategic thinking, and professional integrity
Certified professionals are often positioned for advanced roles such as senior security analyst, penetration tester, security consultant, cybersecurity manager, or security engineer. Their ability to integrate technical knowledge with strategic decision-making enhances their value to organizations, supporting the development of robust security programs, risk mitigation strategies, and compliance initiatives
Enterprise organizations benefit from employing 312-50v10 certified professionals. Their expertise in identifying vulnerabilities, assessing risks, and implementing defenses contributes to overall resilience, protects sensitive data, and ensures operational continuity. Certified ethical hackers also support organizational preparedness, helping anticipate emerging threats and implement proactive measures to reduce exposure and improve security outcomes
Leveraging Certification for Long-Term Professional Growth
Achieving the 312-50v10 certification is not only an immediate demonstration of skills but also a foundation for long-term professional growth. Certified professionals continue to develop expertise in advanced attack techniques, defensive measures, and risk management. They engage in scenario-based exercises, continuous learning, and professional development activities that expand their knowledge and capabilities
Leveraging certification involves applying skills to complex enterprise environments, leading security assessments, and mentoring junior professionals. Ethical hackers contribute to organizational strategy, influence policy, and provide guidance on emerging threats and security technologies. By maintaining a commitment to continuous improvement, certified professionals ensure that their expertise remains relevant, adaptable, and valuable to employers
Consolidating Knowledge Across Domains
The 312-50v10 exam emphasizes the integration of skills across multiple domains, reinforcing the ability to view security holistically. Candidates combine technical proficiency in penetration testing, malware analysis, web and wireless security, social engineering, and risk assessment with strategic understanding of enterprise operations. This consolidated knowledge allows professionals to identify systemic weaknesses, anticipate attack paths, and implement comprehensive mitigation strategies
Scenario-based labs and simulations continue to play a critical role in consolidating knowledge. Candidates practice multi-step assessments that span domains, integrating reconnaissance, scanning, exploitation, remediation, and reporting. By mastering these interconnected skills, professionals demonstrate their ability to handle complex security challenges and provide actionable insights to organizations
Final Words
The 312-50v10 certification validates advanced knowledge and practical expertise in ethical hacking and enterprise security. Professionals who achieve this credential demonstrate proficiency in multiple domains, including network and system penetration testing, web and wireless security, malware analysis, social engineering, and risk assessment. Mastery of these areas enables candidates to identify vulnerabilities, assess threats, and implement effective mitigation strategies in complex enterprise environments. The certification emphasizes both technical execution and strategic thinking, ensuring that ethical hackers can contribute meaningfully to organizational security initiatives
Preparation for the 312-50v10 exam encourages a combination of theoretical learning, hands-on lab practice, and scenario-based exercises. Candidates develop the ability to simulate multi-layered attacks, analyze system weaknesses, and prioritize vulnerabilities based on potential impact. Continuous practice strengthens procedural skills, tool proficiency, and analytical capabilities, which are essential for professional application. By incorporating scenario-based learning, candidates gain experience in realistic enterprise settings, improving decision-making under pressure and enhancing confidence in executing complex security operations
Achieving this certification also enhances career opportunities and professional recognition. Certified professionals are positioned for roles such as security analyst, penetration tester, security consultant, cybersecurity manager, and security engineer. Their ability to integrate technical expertise with strategic risk assessment makes them valuable assets to organizations seeking to strengthen security posture, protect sensitive data, and maintain operational continuity. Furthermore, ongoing engagement with emerging threats, advanced attack techniques, and evolving security technologies ensures that 312-50v10 certified professionals maintain proficiency and adaptability in a constantly changing cybersecurity landscape
Overall, the 312-50v10 certification represents a comprehensive validation of ethical hacking and enterprise security skills. It equips professionals to tackle complex security challenges, supports strategic decision-making, and contributes to long-term career growth, making it a meaningful credential for those seeking to advance in the cybersecurity field
ECCouncil CEH 312-50v10 practice test questions and answers, training course, study guide are uploaded in ETE Files format by real users. Study and Pass 312-50v10 Certified Ethical Hacker v10 Exam certification exam dumps & practice test questions and answers are to help students.
Exam Comments * The most recent comment are on top
Purchase 312-50v10 Exam Training Products Individually



Why customers love us?
What do our customers say?
The resources provided for the ECCouncil certification exam were exceptional. The exam dumps and video courses offered clear and concise explanations of each topic. I felt thoroughly prepared for the 312-50v10 test and passed with ease.
Studying for the ECCouncil certification exam was a breeze with the comprehensive materials from this site. The detailed study guides and accurate exam dumps helped me understand every concept. I aced the 312-50v10 exam on my first try!
I was impressed with the quality of the 312-50v10 preparation materials for the ECCouncil certification exam. The video courses were engaging, and the study guides covered all the essential topics. These resources made a significant difference in my study routine and overall performance. I went into the exam feeling confident and well-prepared.
The 312-50v10 materials for the ECCouncil certification exam were invaluable. They provided detailed, concise explanations for each topic, helping me grasp the entire syllabus. After studying with these resources, I was able to tackle the final test questions confidently and successfully.
Thanks to the comprehensive study guides and video courses, I aced the 312-50v10 exam. The exam dumps were spot on and helped me understand the types of questions to expect. The certification exam was much less intimidating thanks to their excellent prep materials. So, I highly recommend their services for anyone preparing for this certification exam.
Achieving my ECCouncil certification was a seamless experience. The detailed study guide and practice questions ensured I was fully prepared for 312-50v10. The customer support was responsive and helpful throughout my journey. Highly recommend their services for anyone preparing for their certification test.
I couldn't be happier with my certification results! The study materials were comprehensive and easy to understand, making my preparation for the 312-50v10 stress-free. Using these resources, I was able to pass my exam on the first attempt. They are a must-have for anyone serious about advancing their career.
The practice exams were incredibly helpful in familiarizing me with the actual test format. I felt confident and well-prepared going into my 312-50v10 certification exam. The support and guidance provided were top-notch. I couldn't have obtained my ECCouncil certification without these amazing tools!
The materials provided for the 312-50v10 were comprehensive and very well-structured. The practice tests were particularly useful in building my confidence and understanding the exam format. After using these materials, I felt well-prepared and was able to solve all the questions on the final test with ease. Passing the certification exam was a huge relief! I feel much more competent in my role. Thank you!
The certification prep was excellent. The content was up-to-date and aligned perfectly with the exam requirements. I appreciated the clear explanations and real-world examples that made complex topics easier to grasp. I passed 312-50v10 successfully. It was a game-changer for my career in IT!

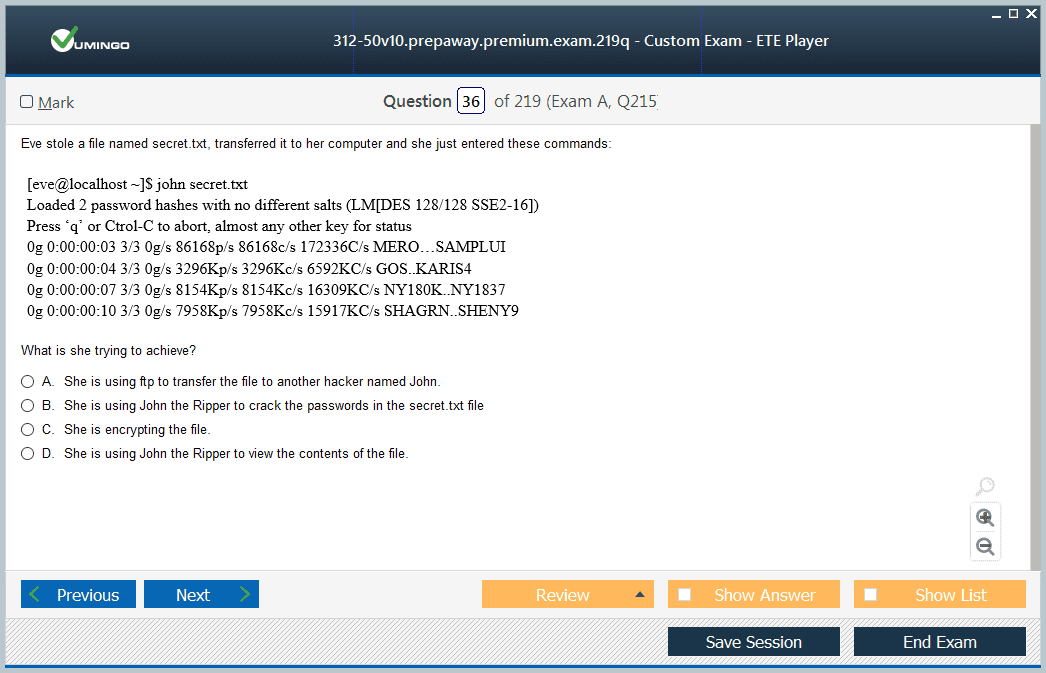
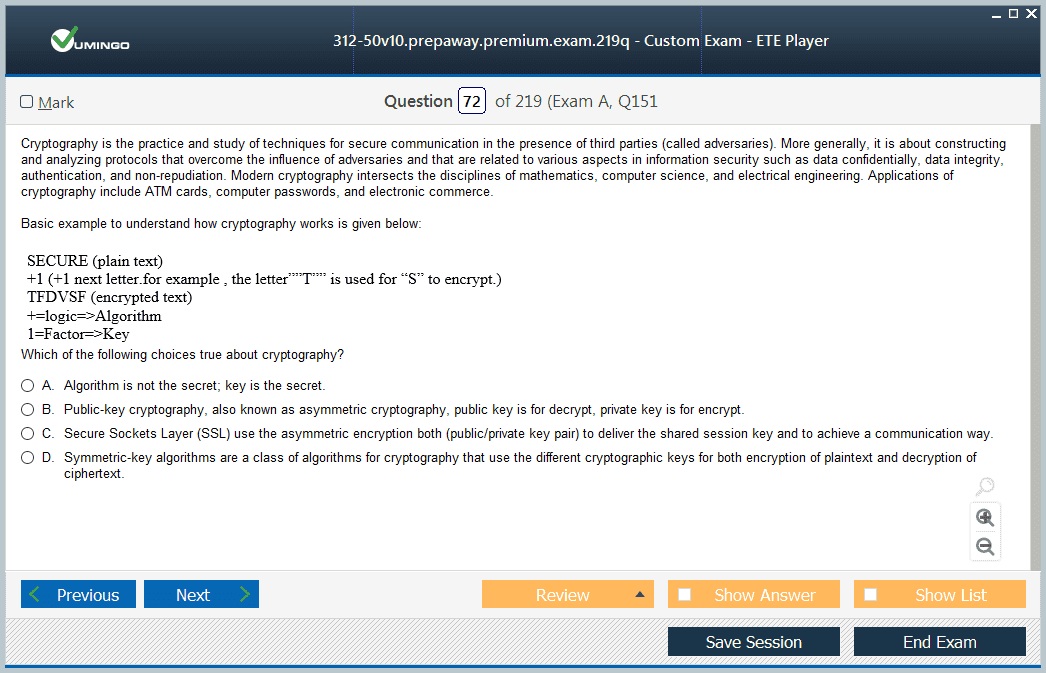
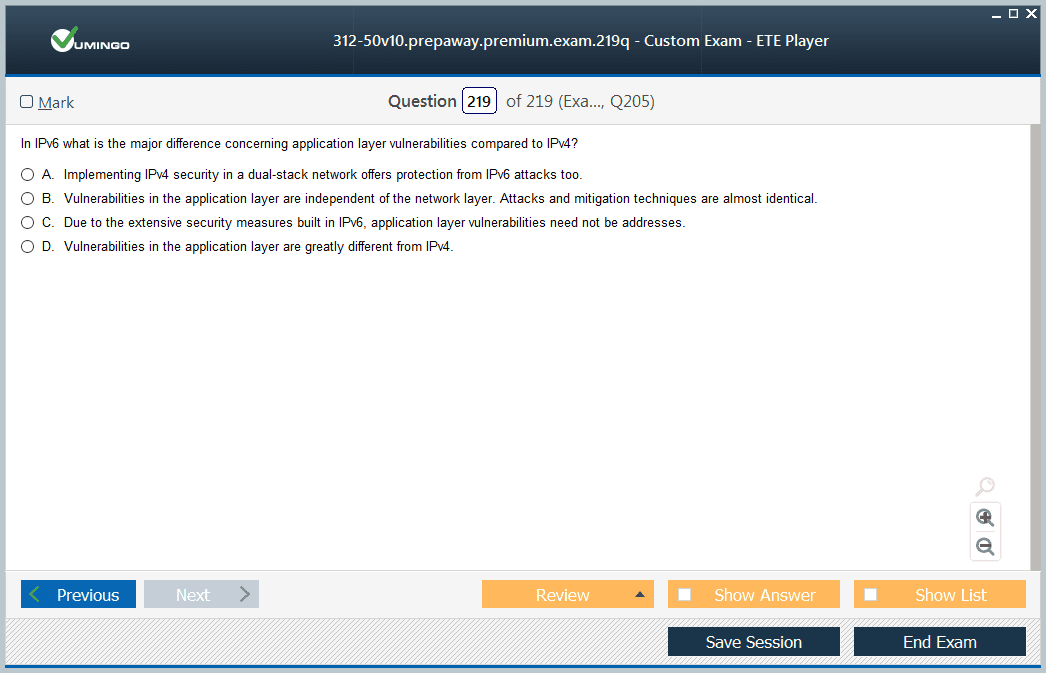
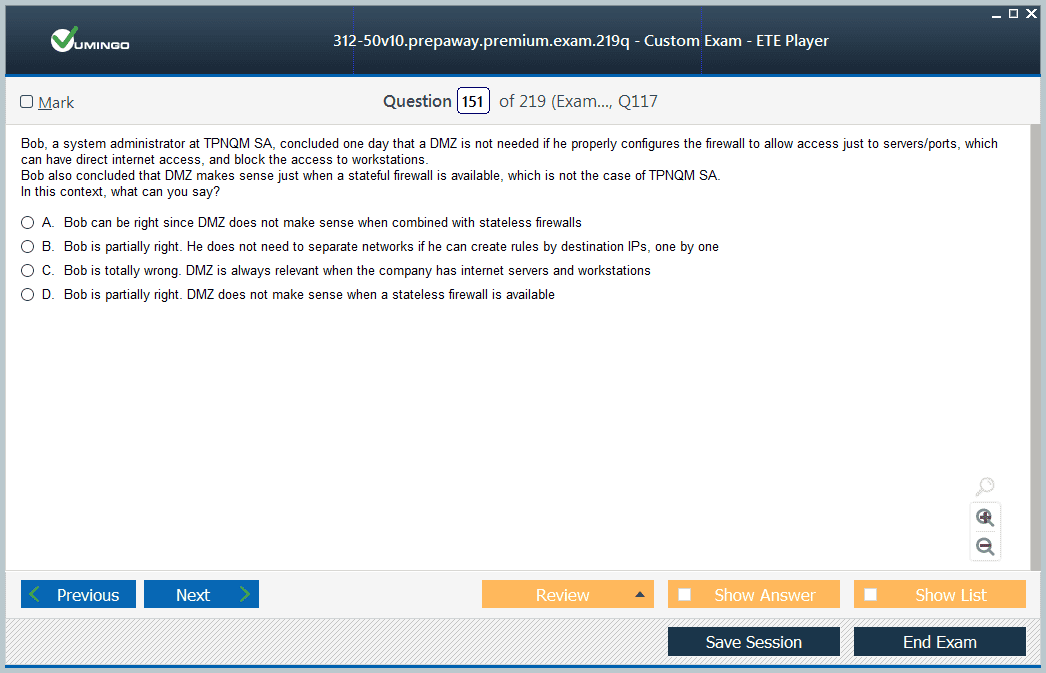








preparing to sit for CEH v10... am using these free practice tests and find them useful... so many questions and very good practice to manage the limited time... recommend