- Home
- Cisco Certifications
- 300-420 Designing Cisco Enterprise Networks (ENSLD) Dumps
Pass Cisco ENSLD 300-420 Exam in First Attempt Guaranteed!
Get 100% Latest Exam Questions, Accurate & Verified Answers to Pass the Actual Exam!
30 Days Free Updates, Instant Download!


300-420 Premium Bundle
- Premium File 386 Questions & Answers. Last update: Jan 20, 2026
- Training Course 75 Video Lectures
- Study Guide 751 Pages
Last Week Results!

Includes question types found on the actual exam such as drag and drop, simulation, type-in and fill-in-the-blank.

Based on real-life scenarios similar to those encountered in the exam, allowing you to learn by working with real equipment.

Developed by IT experts who have passed the exam in the past. Covers in-depth knowledge required for exam preparation.
All Cisco ENSLD 300-420 certification exam dumps, study guide, training courses are Prepared by industry experts. PrepAway's ETE files povide the 300-420 Designing Cisco Enterprise Networks (ENSLD) practice test questions and answers & exam dumps, study guide and training courses help you study and pass hassle-free!
Cisco 300-420 ENSLD Exam Prep: Designing Cisco Enterprise Networks
An organization’s performance and success often rely heavily on the capability and cooperation of the professionals who form its workforce. Among these professionals, those in the field of Information Technology are uniquely tasked with ensuring that a business’s systems, networks, and data remain secure, efficient, and up to date. In this ever-evolving technological landscape, staying informed of the latest advancements is no longer optional—it is a requirement. Technology professionals must remain continually engaged with new tools, techniques, and certifications to maintain relevance and effectiveness.
In the IT industry, one of the most sought-after credentials is Cisco certification. Recognized globally, Cisco certifications signify a strong grasp of networking fundamentals and specialized expertise. Among these, the 300-420 ENSLD exam stands out as a critical requirement for those aiming to achieve the Cisco Certified Network Professional Enterprise certification. Known formally as the Designing Cisco Enterprise Networks exam, the 300-420 test is crafted for network professionals with at least three to five years of experience in designing complex network infrastructures. The certification validates their ability to effectively plan, design, implement, and optimize modern enterprise networks.
Achieving success in the 300-420 exam is not merely about rote learning. It involves a deep understanding of network topologies, routing protocols, infrastructure components, automation, and security design. For this reason, preparing for the exam often requires more than traditional study guides or instructor-led training. Practice exams and detailed exam dumps have emerged as popular tools that replicate the real exam experience, offering candidates a way to assess their readiness, identify weak areas, and reinforce key topics.
Value of Passing the 300-420 ENSLD Exam
Those who successfully pass the 300-420 exam demonstrate a comprehensive capability to design network solutions that are robust, scalable, and secure. Their skill set includes the selection of appropriate hardware and software components, planning for efficient connectivity, integrating security protocols, and aligning the network infrastructure with business goals. Such expertise is crucial for the smooth operation of enterprise networks, where the cost of downtime or performance issues can be significant.
As the need for skilled professionals continues to grow, the relevance of certifications like Cisco’s 300-420 becomes even more critical. Professionals seeking to elevate their careers find that achieving this certification opens doors to more advanced roles, better pay, and increased recognition within their organizations. However, understanding the true nature and expectations of the exam is the first step toward success.
A fundamental concept behind Cisco enterprise network design is the construction of a well-structured network that not only meets current demands but also accommodates future growth. This involves developing a design that supports high availability, scalability, manageability, and performance. To accomplish this, network designers must be adept at using network diagrams and topology maps that detail device connections, traffic flows, and configuration parameters.
Role of Enterprise Network Design in Business Success
The enterprise network is a broad concept referring to the IT framework used by medium to large businesses to connect employees, applications, devices, and services. This network acts as the backbone for all digital communications and transactions within the company. It must operate seamlessly across different locations, support a variety of devices, and remain secure from external threats. Cisco’s approach to enterprise network design integrates a wide range of technologies and design principles that address these requirements.
The Cisco 300-420 exam is designed to test not only theoretical knowledge but also the practical application of design principles in real-world scenarios. The exam covers areas such as advanced routing and addressing solutions, campus network design, wide-area network design, network services, and automation. Each of these areas represents a pillar of modern enterprise networking.
Routing and addressing design involves planning how data will move through the network. It includes choosing the correct routing protocols such as EIGRP, OSPF, IS-IS, and BGP, and creating structured IP addressing plans for both IPv4 and IPv6. A well-thought-out routing and addressing strategy ensures efficient data transmission and simplifies network management.
The campus network refers to the portion of the enterprise network that connects devices within a local area, such as within office buildings or campuses. Designing this layer requires attention to redundancy, scalability, and security. Cisco’s SD-Access fabric, which allows for automated provisioning and policy enforcement, plays a crucial role in modern campus design.
WAN design focuses on connecting geographically dispersed locations. Today’s WAN designs often leverage technologies like SD-WAN to provide secure, reliable connectivity while optimizing application performance and reducing costs. Site-to-site VPNs, MPLS alternatives, and redundant paths are among the critical components in this area.
Network Services and Automation in Modern Design
Network services include aspects like multicast routing, Quality of Service, and network management. These services ensure that the network can deliver the right performance levels to different applications and users. Understanding how to design for these services is vital for maintaining an optimal user experience.
Finally, automation is a growing area of focus. Network automation involves using tools and scripts to reduce manual configuration and improve consistency across devices. The Cisco 300-420 exam tests knowledge of automation frameworks such as YANG, model-driven telemetry, and configuration protocols like NETCONF and RESTCONF.
For professionals aiming to succeed in this exam, having access to accurate and high-quality study materials is crucial. Practice tests and simulated questions that mirror the structure and content of the actual exam can help candidates evaluate their readiness and refine their study approach. These tools also provide insight into time management, question formats, and complexity levels that may be encountered on test day.
The journey to certification is not just a technical endeavor. It is a professional commitment that demonstrates a willingness to grow, adapt, and excel in a competitive field. Candidates who invest the time and effort into preparing for the Cisco 300-420 ENSLD exam will find that the knowledge gained not only helps them pass the test but also equips them with skills that are highly valuable in the workplace.
As more businesses undergo digital transformation, the need for expertly designed enterprise networks continues to rise. From integrating cloud services and remote access to supporting mobile workforces and securing sensitive data, modern networks must do more than ever before. Cisco’s certifications are crafted to ensure that professionals are ready to meet these challenges head-on.
In summary, the Cisco 300-420 ENSLD exam is more than just a stepping stone to the CCNP Enterprise certification. It is a comprehensive evaluation of one’s ability to design and implement modern enterprise networks. Understanding its importance, structure, and content areas is the first phase in preparing for success. In the following sections, we will explore deeper into the domains covered by the exam, strategies for effective preparation, and the specific role of practice materials in boosting your chances of passing on the first attempt.
Core Domains of the Cisco 300-420 ENSLD Exam
Understanding the Cisco 300-420 ENSLD exam requires a thorough examination of the domains it covers. Each section represents a specialized area of network design that plays a vital role in the planning and deployment of enterprise infrastructures. Mastery of these domains is necessary not only for passing the exam but also for performing effectively in professional roles that involve enterprise network design.
The 300-420 ENSLD exam is structured around five main content areas. These are: advanced routing and addressing solutions, enterprise campus networks, enterprise WAN design, network services, and network automation. Each domain contributes a different percentage to the exam’s total weight, indicating its importance and the depth of understanding expected.
The most heavily weighted domains are advanced routing and addressing solutions and enterprise campus network design. Together, they represent fifty percent of the exam content. Candidates must also demonstrate significant knowledge of WAN technologies, network services, and emerging practices in automation. A clear understanding of these areas provides the foundational knowledge to address modern network challenges and ensures efficient design and deployment strategies.
Advanced Routing and Addressing Solutions
Advanced routing and addressing are essential components in the structure of any scalable and resilient enterprise network. This domain covers the design and implementation of routing protocols, address planning, and the integration of IPv4 and IPv6 within the same infrastructure. Candidates preparing for the exam must develop a strong understanding of the function and behavior of multiple routing protocols, including EIGRP, OSPF, IS-IS, and BGP.
The 300-420 exam focuses on the ability to design reliable and stable routing solutions that support organizational requirements. This includes selecting appropriate routing protocols based on business needs, designing route redistribution strategies, and ensuring loop prevention through technologies such as route maps and prefix lists. Furthermore, understanding the convergence behavior of routing protocols and the role of administrative distance and metrics is critical.
Addressing design includes planning hierarchical IP schemes that support summarization and route aggregation. Candidates are expected to know how to build structured address plans that align with business scalability goals and security policies. In networks that require dual-stack operations, effective IPv6 transition strategies such as tunneling, dual-stack, and translation mechanisms must be part of the design process.
This domain also evaluates the candidate’s capability to manage routing policies for external connectivity using BGP. They must understand BGP attributes, path selection, and policy controls, including community strings and route filtering. Given the centrality of routing to all network operations, this domain forms a substantial portion of the ENSLD certification process and sets the technical tone for the rest of the exam.
Designing Advanced Campus Networks
Campus network design involves constructing the local area network environment that connects all internal users and resources. This domain examines how to develop robust and efficient campus architectures using best practices and Cisco-recommended models, such as hierarchical design. The focus is on creating high-availability, fault-tolerant, and scalable systems that can accommodate growth and new technologies.
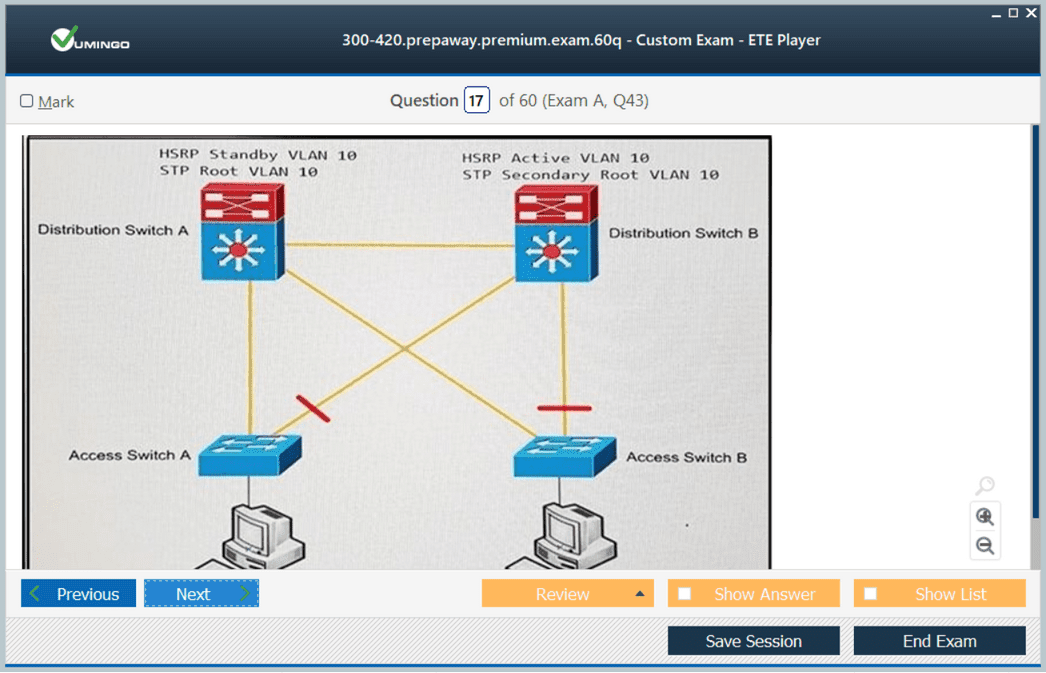
One of the key considerations in campus design is Layer 2 and Layer 3 architecture. Candidates must understand where to deploy Layer 2 switching and when to introduce Layer 3 routing to optimize traffic flow, enhance redundancy, and simplify troubleshooting. Redundancy mechanisms such as First Hop Redundancy Protocols and spanning tree enhancements are also central to this domain.
The domain also introduces software-defined access (SD-Access), Cisco’s solution for network segmentation, automation, and policy enforcement. Candidates should understand SD-Access components, including the control plane (LISP), data plane, and policy plane. They should also be able to describe the operation of fabric borders, fabric edges, and control nodes.
Wireless design considerations are another important component. The ability to integrate wireless access into the campus architecture using best practices is expected. This includes planning access point placement, wireless controller integration, roaming, and security in a dense user environment.
Understanding campus design extends beyond technology to include considerations for organizational needs, including departmental separation, application delivery, and support for multimedia services. By learning how to analyze business goals and translate them into network requirements, candidates can build solutions that are both technically sound and aligned with strategic priorities.
Enterprise WAN Design and Connectivity
Wide Area Network design is a critical part of connecting enterprise campuses, branch locations, data centers, and cloud resources. The 300-420 exam evaluates the candidate’s knowledge in designing scalable, secure, and efficient WAN topologies using modern technologies. This includes traditional WAN solutions as well as modern software-defined approaches.
Cisco’s SD-WAN solution is a major focus area. Candidates must understand its architecture, including control and data plane separation, central policy management, application-aware routing, and transport independence. The ability to design SD-WAN with redundancy, quality of service, and appropriate failover strategies is tested in the exam.
Another important concept in WAN design is connectivity choices. This includes evaluating the use of dedicated MPLS circuits, broadband internet, LTE, and satellite connections. Each transport option must be evaluated based on bandwidth, latency, cost, and reliability.
Security remains a core part of WAN planning. Candidates are expected to design secure site-to-site VPNs, remote user access, and encrypted tunnels for data-in-transit. Understanding IPsec, GRE, and DMVPN is essential when addressing secure communication across WAN links.
In WAN design, high availability is addressed by introducing redundancy in both physical links and routing protocols. Load balancing and backup paths should be carefully considered to avoid single points of failure. The exam emphasizes the ability to build resilient WAN architectures that support business continuity and remote work environments.
As more enterprises adopt cloud computing, the WAN becomes a strategic link between the enterprise network and public cloud services. Candidates must be able to plan connectivity to cloud service providers while ensuring predictable performance, compliance, and centralized management.
Network Services in Enterprise Environments
Enterprise networks rely on a wide range of services to support applications, users, and administrative functions. This domain evaluates a candidate’s ability to design services such as multicast routing, Quality of Service, and network management systems. Each service must be designed to integrate seamlessly into the network architecture without introducing security risks or bottlenecks.
Multicast design involves understanding protocols like PIM, IGMP, and Rendezvous Points. Candidates must demonstrate how to implement multicast efficiently across both Layer 2 and Layer 3, ensuring that traffic only reaches intended recipients without overloading links or devices.
Quality of Service design is another critical area. Candidates are required to understand traffic classification, marking, queuing, and shaping mechanisms. They must be able to select the right QoS policies to support different types of traffic, such as voice, video, and data. The goal is to ensure predictable performance across all applications while preserving bandwidth and user experience.
Network management includes designing systems that monitor, configure, and optimize network infrastructure. This includes using SNMP, Syslog, NetFlow, and telemetry for gathering operational data. Candidates must also know how to use management protocols to simplify operations and enforce compliance.
Service design often overlaps with security and policy considerations. For example, designing an effective QoS model requires knowledge of access control lists and policy maps. Similarly, monitoring tools must be deployed securely to avoid data leaks or unauthorized access.
This domain emphasizes not only technical implementation but also the alignment of network services with organizational goals. Designing a service-aware infrastructure allows enterprises to scale operations, reduce troubleshooting efforts, and ensure continuous performance improvement.
Understanding Network Automation in the Cisco 300-420 ENSLD Exam
Network automation has become a central component of modern enterprise network design. As networks grow in scale and complexity, manual configuration and monitoring become increasingly inefficient and error-prone. Automation provides a means to manage repetitive tasks, enforce configuration standards, and improve operational consistency. For these reasons, the Cisco 300-420 ENSLD exam includes a dedicated domain focused on automation concepts, frameworks, and design principles.
Candidates are expected to understand how network automation can be integrated into design decisions. This involves not only technical awareness of protocols and models but also recognizing the broader benefits, including faster deployment, reduced operational costs, and improved accuracy. The exam does not focus on scripting or coding skills but emphasizes design-level decisions regarding automation tools and technologies.
One of the primary concepts evaluated is the use of data models such as YANG, which define how configuration and state data are structured within a network device. Candidates should be able to select the appropriate YANG model set based on the use case and explain how these models support automated workflows.
Candidates must also understand the differences between telemetry models. Model-driven telemetry enables the continuous streaming of data from devices to collectors, offering a real-time view of network health and performance. The exam tests knowledge of the advantages and use cases for model-driven telemetry compared to traditional polling-based monitoring methods.
Familiarity with different types of data models—Cisco native, OpenConfig, and IETF—is also required. Each model has different levels of vendor support and customization. Knowing when to apply each model is essential for designing a solution that supports current and future automation needs.
Additionally, the exam includes conceptual understanding of configuration protocols such as NETCONF and RESTCONF. These are APIs that enable external systems to interact with network devices using structured data. Candidates must understand the operational flow, advantages, and differences between these protocols and how they influence device manageability.
By integrating automation into the network design, organizations can reduce the mean time to deploy, accelerate troubleshooting, and gain better insight into device behavior. The Cisco 300-420 exam tests the ability to recognize automation as a design enabler rather than an operational add-on.
Strategic Preparation for the 300-420 ENSLD Exam
Preparing for the Cisco 300-420 ENSLD exam requires a structured approach that addresses each domain comprehensively. Success in this exam comes from more than just technical knowledge; it involves understanding design principles, network behavior, and how to apply concepts in practical scenarios. Developing a strategic preparation plan is essential for navigating the diverse range of topics and question types that the exam includes.
The first step in preparation is to become thoroughly familiar with the exam blueprint. This official document outlines the topic areas, objectives, and expected knowledge for each domain. By using the blueprint as a study guide, candidates can ensure their efforts are aligned with the content that will appear on the test.
Next, building a strong foundational knowledge of network design is essential. Candidates should review Cisco’s recommended design models and principles, such as hierarchical network design, modularity, redundancy, and fault isolation. These principles form the foundation for many design-related decisions and are frequently referenced throughout the exam.
Candidates are also encouraged to use official study materials and participate in training courses when available. These resources typically provide both theoretical explanations and practical examples that reinforce understanding. However, relying solely on books or courses may not provide the level of readiness required to face real exam questions, especially those that test the practical application of design logic.
Hands-on experience with network design tools and platforms is highly recommended. This includes drawing network topologies, planning addressing schemes, evaluating routing strategies, and simulating WAN connectivity models. Using tools such as Cisco Packet Tracer, EVE-NG, or physical lab equipment can greatly enhance your understanding of real-world network behavior.
Concept reinforcement is another important strategy. This means regularly revisiting previously studied material, especially areas where initial understanding was weak. Using summaries, flashcards, and diagram-based review techniques can help retain complex information over a longer period.
Role of Practice Tests and Simulation Materials
One of the most effective ways to solidify your understanding and assess your readiness is by taking practice exams that reflect the format and difficulty of the actual Cisco 300-420 test. Practice questions are not simply for memorization—they serve as a diagnostic tool that reveals strengths and highlights knowledge gaps.
High-quality practice exams replicate the time constraints, question types, and structure of the real test. This allows candidates to become comfortable with navigating through scenario-based questions, drag-and-drop exercises, and multiple-choice formats. By simulating the test environment, candidates can also learn how to manage time effectively during the actual exam.
Practice exams also provide insight into how questions are worded and how answer choices are designed. Many questions on the real exam may include distractors—plausible but incorrect answers designed to test your depth of knowledge. Familiarity with this type of questioning helps develop critical thinking and decision-making skills.
An additional benefit of practice exams is building exam stamina. The Cisco 300-420 exam lasts ninety minutes and includes a wide range of challenging topics. Being able to stay focused and make informed decisions under pressure is just as important as having technical knowledge. Regular exposure to timed practice builds confidence and improves mental performance.
After completing each practice session, it’s important to thoroughly review incorrect answers. Understand not just what the right answer is, but why the wrong options are incorrect. This approach leads to a deeper understanding of concepts and helps prevent similar mistakes in the future.
Some practice platforms also include performance analytics that allow you to track your progress over time. These insights help identify trends, such as consistently weak domains, and offer guidance on how to adjust your study plan accordingly.
Designing a Realistic Study Plan for the Exam
A realistic and consistent study plan is one of the most critical elements in preparing for the Cisco 300-420 ENSLD exam. Attempting to master the entire blueprint without a schedule can lead to burnout, missed topics, and shallow learning. A well-structured plan includes time for reading, practicing, reviewing, and resting.
Start by identifying how much time you can dedicate each day or week toward exam preparation. Be honest about your other commitments, work responsibilities, and personal limitations. Then, divide the exam domains into weekly or bi-weekly segments, assigning time based on their weight in the exam and your comfort level with each topic.
Use a study calendar to set milestones and goals. For example, allocate specific days to routing and addressing, others to campus design, and so on. Mix passive study (reading and watching videos) with active engagement (drawing topologies, solving questions, and lab work).
Make room in your schedule for comprehensive reviews. As you approach the exam date, shift focus from learning new material to reinforcing previously studied content. Repetition plays a key role in long-term retention, particularly with complex topics like multicast design or SD-Access architecture.
Incorporating rest periods into your study plan is also vital. Fatigue can lead to diminished retention and poor performance. Taking short breaks during study sessions and scheduling rest days in your weekly routine allows your brain to process information and reset focus.
Finally, as your confidence builds and your practice scores improve, consider taking a full-length mock exam under realistic conditions. This final rehearsal prepares you mentally and emotionally for the actual test and helps you fine-tune your time management and pacing.
By designing a study plan that fits your life and accommodates your learning style, you can approach the Cisco 300-420 exam with confidence, clarity, and control. Consistency, discipline, and adaptability are the keys to mastering both the content and the pressure of the exam environment.
Long-Term Career Value of the Cisco 300-420 ENSLD Certification
Achieving the Cisco 300-420 ENSLD certification does more than just prove your technical knowledge—it positions you for long-term success in the IT industry. As networks become more complex and organizations demand faster, more reliable, and secure communication between locations, the need for qualified network designers continues to grow. Employers increasingly seek individuals who not only understand how to configure devices but who can also architect and maintain robust infrastructures aligned with business goals.
Holding the 300-420 certification means you have demonstrated your ability to design enterprise networks that are efficient, scalable, and secure. It also confirms that you understand the real-world considerations of designing systems for large organizations, such as redundancy, traffic management, security architecture, cloud integration, and automation. These are the skills companies need to remain agile and competitive.
Certified professionals often find themselves eligible for senior-level roles, such as network architects, design engineers, and infrastructure specialists. These roles come with higher salaries, greater responsibilities, and broader influence in organizational decision-making. Hiring managers recognize that those who pass Cisco’s advanced exams have made a serious investment in their professional development and possess the kind of critical thinking that modern network design demands.
Over time, the value of the certification increases as your experience deepens and your responsibilities grow. Rather than becoming outdated, the foundational knowledge acquired through preparing for the 300-420 exam can evolve with technological advancements. As Cisco updates its certification tracks to reflect changes in networking technologies, certified individuals can remain aligned by renewing or upgrading their credentials through continuing education.
This certification also serves as a stepping stone toward more advanced paths. Those who complete the 300-420 ENSLD as part of the CCNP Enterprise track are already on their way to Cisco Certified Design Expert or network security specializations. Each new credential builds upon the knowledge and recognition gained from previous achievements, helping you build a solid and respected career profile.
Industry Demand for Network Design Expertise
As businesses continue to embrace digital transformation, the demand for professionals who can design reliable and flexible network architectures has reached new heights. From expanding into cloud-based services to supporting hybrid workforces and integrating emerging technologies like IoT and edge computing, organizations rely on their networks more than ever before. Poor design can lead to costly downtime, performance issues, security breaches, and scalability problems.
Enterprise networks are no longer limited to routers and switches. They now include virtual infrastructure, security policies, automation workflows, and integration with third-party services. This creates a new layer of complexity that requires not just technical skill, but also design intuition and strategic thinking.
Professionals with the Cisco 300-420 certification are uniquely equipped to meet this demand. They understand not just how networks function, but how to design systems that align with business objectives. Whether an organization is rolling out a new branch location, migrating to the cloud, or deploying a secure wireless infrastructure, certified designers are essential in translating business needs into technical realities.
Companies recognize this and reward certified individuals with better job offers, increased trust, and more project leadership opportunities. In consulting and client-facing roles, having a Cisco design certification adds credibility to your expertise, allowing you to influence architectural decisions and offer solutions that are both technically sound and strategically aligned.
For those working in managed service environments or vendor support roles, the certification provides a framework for evaluating client requirements and proposing standardized, effective solutions. It also makes it easier to troubleshoot existing environments by providing a comprehensive understanding of network behavior, device interaction, and protocol dependencies.
Benefits Beyond the Certification
While the 300-420 ENSLD certification opens doors professionally, the benefits go beyond job titles and salaries. The process of preparing for the exam itself brings substantial rewards. The structured learning path helps you organize your knowledge in a more meaningful way, allowing you to connect concepts across different domains. It reinforces best practices and exposes you to industry standards that may not be part of your daily work.
Through studying, you develop a deeper understanding of why certain designs work better than others, how network protocols interact under different conditions, and how to evaluate trade-offs between performance, cost, and manageability. This not only helps you in the exam but also enhances your ability to make informed decisions in your job.
The discipline, focus, and consistency required to prepare for the 300-420 exam also foster personal growth. You build a stronger work ethic, develop better study habits, and improve your problem-solving skills. These qualities are valuable in any professional context and help you take on challenges with confidence.
Being part of the Cisco-certified community also provides access to global networking opportunities. Whether attending events, joining online forums, or contributing to collaborative projects, you are part of a peer group that shares your commitment to professional excellence. This exposure can lead to mentorships, job referrals, and access to advanced learning resources.
Another overlooked benefit is the ability to mentor others. Once certified, many professionals choose to support junior colleagues or those pursuing their first Cisco exams. Teaching others reinforces your understanding, helps build team capacity, and earns you recognition as a knowledgeable and supportive leader.
Sustaining Your Certification and Career Growth
Like all professional certifications, the Cisco 300-420 ENSLD requires renewal after a certain period to remain valid. This is not just an administrative requirement; it’s an opportunity to stay relevant and continue growing. Cisco provides multiple pathways for recertification, including taking new exams, completing continuing education credits, or pursuing more advanced certifications.
Staying current with new technologies and evolving best practices ensures that your knowledge remains useful in changing environments. It also shows employers and clients that you are committed to lifelong learning and capable of adapting to industry trends.
To make the most of your certification, consider aligning it with your career goals. For example, if your interest lies in automation, cloud networking, or network security, you can pursue specialized learning tracks that build on your ENSLD foundation. Cisco offers other concentration exams that complement the 300-420 content, allowing you to deepen your expertise or pivot toward adjacent domains.
Keeping a professional portfolio of your certifications, projects, and continuing education achievements is also helpful. This not only helps with job applications and promotions but also provides a sense of direction for your career development. Having a clear record of your accomplishments and goals keeps you focused and motivated.
Your career path may also benefit from joining professional associations, attending industry conferences, and participating in certification study groups. These activities help you build relationships, share knowledge, and stay informed about emerging trends and opportunities in network design and architecture.
In conclusion, the Cisco 300-420 ENSLD certification is not just a credential—it is a catalyst for professional development, career advancement, and lifelong learning. Whether you’re seeking a new role, aiming for a promotion, or simply wanting to grow your technical knowledge, this certification provides a structured, respected, and meaningful path forward. The knowledge you gain and the reputation you build through this process will continue to serve you long after the exam is over.
Final Thoughts
The journey to earning the Cisco 300-420 ENSLD certification is both challenging and rewarding. It goes far beyond memorizing terms or passing a timed exam—it is a deliberate investment in your professional future. As enterprise networks become more complex and integral to organizational success, the demand for skilled network designers continues to rise. This certification validates that you not only understand how networks operate, but that you can design them with foresight, precision, and purpose.
Preparing for the exam requires discipline, strategy, and commitment. It involves learning key concepts in routing, campus and WAN design, network services, and automation. But it also teaches you how to think critically, solve real-world design problems, and apply principles that are directly transferable to your day-to-day role.
The tools you choose—whether study guides, hands-on labs, or practice tests—can play a significant role in how efficiently and confidently you prepare. Using accurate and comprehensive preparation materials helps you identify your strengths, overcome weaknesses, and ultimately face the exam with clarity and assurance.
More importantly, the value of this certification extends beyond exam day. It reinforces your credibility in the industry, opens up higher-level career opportunities, and keeps you aligned with the evolving demands of modern networking. Whether you’re advancing within your current role, exploring new opportunities, or simply looking to deepen your technical knowledge, the 300-420 ENSLD certification marks a milestone of genuine achievement.
As you move forward, let this certification be a foundation, not a finish line. Continue learning, stay curious, and remain adaptable. The landscape of enterprise networking will keep changing, and your ability to grow with it will define your long-term success. Use this accomplishment as a launching point to take on even more complex challenges and elevate your impact in the world of IT.
Cisco ENSLD 300-420 practice test questions and answers, training course, study guide are uploaded in ETE Files format by real users. Study and Pass 300-420 Designing Cisco Enterprise Networks (ENSLD) certification exam dumps & practice test questions and answers are to help students.
- 200-301 - Cisco Certified Network Associate (CCNA)
- 350-401 - Implementing Cisco Enterprise Network Core Technologies (ENCOR)
- 350-701 - Implementing and Operating Cisco Security Core Technologies
- 300-410 - Implementing Cisco Enterprise Advanced Routing and Services (ENARSI)
- 300-715 - Implementing and Configuring Cisco Identity Services Engine (300-715 SISE)
- 350-601 - Implementing and Operating Cisco Data Center Core Technologies (DCCOR)
- 350-801 - Implementing Cisco Collaboration Core Technologies (CLCOR)
- 300-420 - Designing Cisco Enterprise Networks (ENSLD)
- 820-605 - Cisco Customer Success Manager (CSM)
- 200-901 - DevNet Associate (DEVASC)
- 300-425 - Designing Cisco Enterprise Wireless Networks (300-425 ENWLSD)
- 200-201 - Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- 300-710 - Securing Networks with Cisco Firewalls
- 300-415 - Implementing Cisco SD-WAN Solutions (ENSDWI)
- 350-901 - Developing Applications using Cisco Core Platforms and APIs (DEVCOR)
- 300-620 - Implementing Cisco Application Centric Infrastructure (DCACI)
- 350-501 - Implementing and Operating Cisco Service Provider Network Core Technologies (SPCOR)
- 400-007 - Cisco Certified Design Expert
- 300-430 - Implementing Cisco Enterprise Wireless Networks (300-430 ENWLSI)
- 700-805 - Cisco Renewals Manager (CRM)
- 350-201 - Performing CyberOps Using Core Security Technologies (CBRCOR)
- 500-220 - Cisco Meraki Solutions Specialist
- 300-730 - Implementing Secure Solutions with Virtual Private Networks (SVPN 300-730)
- 300-810 - Implementing Cisco Collaboration Applications (CLICA)
- 300-815 - Implementing Cisco Advanced Call Control and Mobility Services (CLASSM)
- 300-435 - Automating Cisco Enterprise Solutions (ENAUTO)
- 300-820 - Implementing Cisco Collaboration Cloud and Edge Solutions
- 300-610 - Designing Cisco Data Center Infrastructure for Traditional and AI Workloads
- 300-735 - Automating Cisco Security Solutions (SAUTO)
- 100-150 - Cisco Certified Support Technician (CCST) Networking
- 300-510 - Implementing Cisco Service Provider Advanced Routing Solutions (SPRI)
- 300-745 - Designing Cisco Security Infrastructure
- 300-440 - Designing and Implementing Cloud Connectivity (ENCC)
- 300-215 - Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR)
- 300-515 - Implementing Cisco Service Provider VPN Services (SPVI)
- 100-140 - Cisco Certified Support Technician (CCST) IT Support
- 300-910 - Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)
- 300-720 - Securing Email with Cisco Email Security Appliance (300-720 SESA)
- 300-725 - Securing the Web with Cisco Web Security Appliance (300-725 SWSA)
- 700-250 - Cisco Small and Medium Business Sales
- 300-835 - Automating Cisco Collaboration Solutions (CLAUTO)
- 700-150 - Introduction to Cisco Sales (ICS)
- 100-490 - Cisco Certified Technician Routing & Switching (RSTECH)
- 300-445 - Designing and Implementing Enterprise Network Assurance
- 300-615 - Troubleshooting Cisco Data Center Infrastructure (DCIT)
- 500-560 - Cisco Networking: On-Premise and Cloud Solutions (OCSE)
- 300-635 - Automating Cisco Data Center Solutions (DCAUTO)
- 500-442 - Administering Cisco Contact Center Enterprise
- 500-443 - Advanced Administration and Reporting of Contact Center Enterprise
- 700-750 - Cisco Small and Medium Business Engineer
- 700-240 - Cisco Environmental Sustainability Overview
- 700-245 - Environmental Sustainability Practice-Building
- 800-150 - Supporting Cisco Devices for Field Technicians
Purchase 300-420 Exam Training Products Individually



Why customers love us?
What do our customers say?
The resources provided for the Cisco certification exam were exceptional. The exam dumps and video courses offered clear and concise explanations of each topic. I felt thoroughly prepared for the 300-420 test and passed with ease.
Studying for the Cisco certification exam was a breeze with the comprehensive materials from this site. The detailed study guides and accurate exam dumps helped me understand every concept. I aced the 300-420 exam on my first try!
I was impressed with the quality of the 300-420 preparation materials for the Cisco certification exam. The video courses were engaging, and the study guides covered all the essential topics. These resources made a significant difference in my study routine and overall performance. I went into the exam feeling confident and well-prepared.
The 300-420 materials for the Cisco certification exam were invaluable. They provided detailed, concise explanations for each topic, helping me grasp the entire syllabus. After studying with these resources, I was able to tackle the final test questions confidently and successfully.
Thanks to the comprehensive study guides and video courses, I aced the 300-420 exam. The exam dumps were spot on and helped me understand the types of questions to expect. The certification exam was much less intimidating thanks to their excellent prep materials. So, I highly recommend their services for anyone preparing for this certification exam.
Achieving my Cisco certification was a seamless experience. The detailed study guide and practice questions ensured I was fully prepared for 300-420. The customer support was responsive and helpful throughout my journey. Highly recommend their services for anyone preparing for their certification test.
I couldn't be happier with my certification results! The study materials were comprehensive and easy to understand, making my preparation for the 300-420 stress-free. Using these resources, I was able to pass my exam on the first attempt. They are a must-have for anyone serious about advancing their career.
The practice exams were incredibly helpful in familiarizing me with the actual test format. I felt confident and well-prepared going into my 300-420 certification exam. The support and guidance provided were top-notch. I couldn't have obtained my Cisco certification without these amazing tools!
The materials provided for the 300-420 were comprehensive and very well-structured. The practice tests were particularly useful in building my confidence and understanding the exam format. After using these materials, I felt well-prepared and was able to solve all the questions on the final test with ease. Passing the certification exam was a huge relief! I feel much more competent in my role. Thank you!
The certification prep was excellent. The content was up-to-date and aligned perfectly with the exam requirements. I appreciated the clear explanations and real-world examples that made complex topics easier to grasp. I passed 300-420 successfully. It was a game-changer for my career in IT!